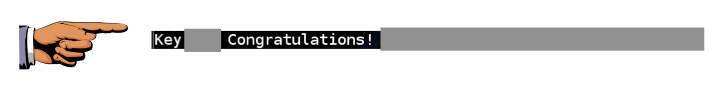
To get the ciphertext, execute this command:
wget https://samsclass.info/124/proj14/xorchal1-cipher --no-check-certificate

Save the image as "Proj 13xa from YOUR NAME".
To get the ciphertext, execute this command:
wget https://samsclass.info/124/proj14/xorchal2-cipher --no-check-certificate
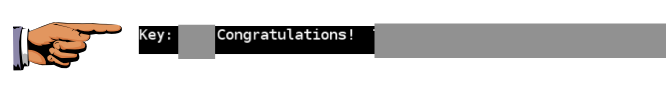
Save the image as "Proj 13xb from YOUR NAME".
To get the ciphertext, execute this command:
wget https://samsclass.info/124/proj14/xorchal3-cipher --no-check-certificate
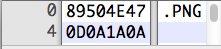
Notice that the first 4 bytes are 89, 50, 4E, 47; the 2nd through 4th byte spell out PNG in ASCII.
Decrypt the file. When you get it, change its filename extension to PNG and open it in an image viewer or Web browser.
Capture a whole-desktop image showing the visible image.
Save the image as "Proj 13xc from YOUR NAME".
To get the ciphertext, execute this command:
wget https://samsclass.info/124/proj14/xorchal4-cipher --no-check-certificate
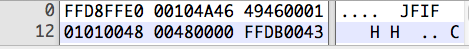
Notice that the first 2 bytes are FFD8, and some later bytes contain the ASCII characters JFIF.
Decrypt the file. When you get it, change its filename extension to JPG and open it in an image viewer or Web browser.
Capture a whole-desktop image showing the visible image.
Save the image as "Proj 13xd from YOUR NAME".