Theory If you just want to do the hands-on projects, skip this section.
Background
Read this article (you can skip sections 3.2 - 6.3):Argon2: the memory-hard function for password hashing and other applicationsThen answer the questions below.
Flags VP 330.1: Hash System (2 pts)
What hashing system uses SMix and ROMix?
Flags VP 330.2: Hash Type (2 pts)
What is the technical term for a hash function with this property:D(α) > 1/α as α → 0
Flags VP 330.3: Side-Channel (2 pts)
Which flavor of Argon2 is vulnerable to side-channel attacks?
Flags VP 330.4: Chains (2 pts)
What parameter determines how many independent computational chains can be run?
Flags VP 330.5: Cold Boot (2 pts)
Which flavor of Argon2 resists cold-boot attacks?
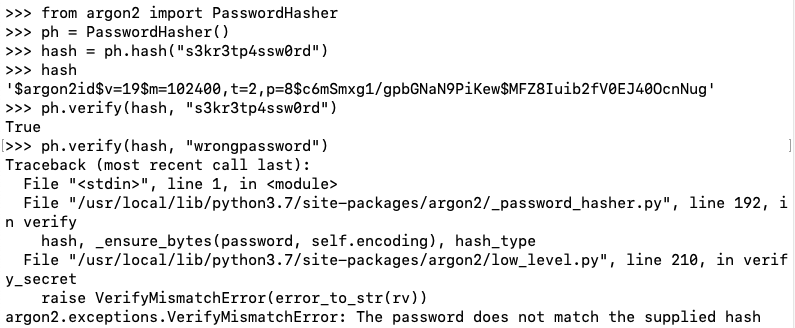
argon2-cffiExecute this command:
python3 -m pip install argon2-cffi
python3
from argon2 import PasswordHasher
ph = PasswordHasher()
hash = ph.hash("s3kr3tp4ssw0rd")
hash
ph.verify(hash, "s3kr3tp4ssw0rd")
ph.verify(hash, "wrongpassword")
Execute these commands to see the attributes of the password hash object you created in the previous steps, and display the value of the __class__ attribute:
dir(ph)
ph.__class__
Flags VP 330.6: Salt Length (2 pts)
How many bytes long is the salt used in the password hash you computed in the previous steps?
Flags VP 330.7: Password (10 pts)
The password is passwordNN, where NN is a two digit number, like password11.Find the password matching the hash below. That password is the flag.
Flags VP 330.8: Hash (10 pts)
Calculate a hash of password using these parameters:The flag is covered by a green rectangle in the image below.
- Time cost: 100
- Memory cost: 102400
- Parallelism: 8
- Hash length: 8 bytes
- Salt length: 8 bytes
- Encoding: utf-8
- Type: Argon2id
Flags VP 330.9: Password (10 pts)
The password is passwordNN, where NN is a two digit number, like password11.Find the password matching the hash below. That password is the flag.
Part of the hash has been redacted and replaced with underscores.
Flags VP 330.10: Salt (5 pts)
Find the salt for this hash. That salt, as eight ASCII characters, is the flag.