http://samlol.samsclass.info/VP/VP230.php
Open Wireshark and start sniffing traffic. In the Filter bar, enter
http
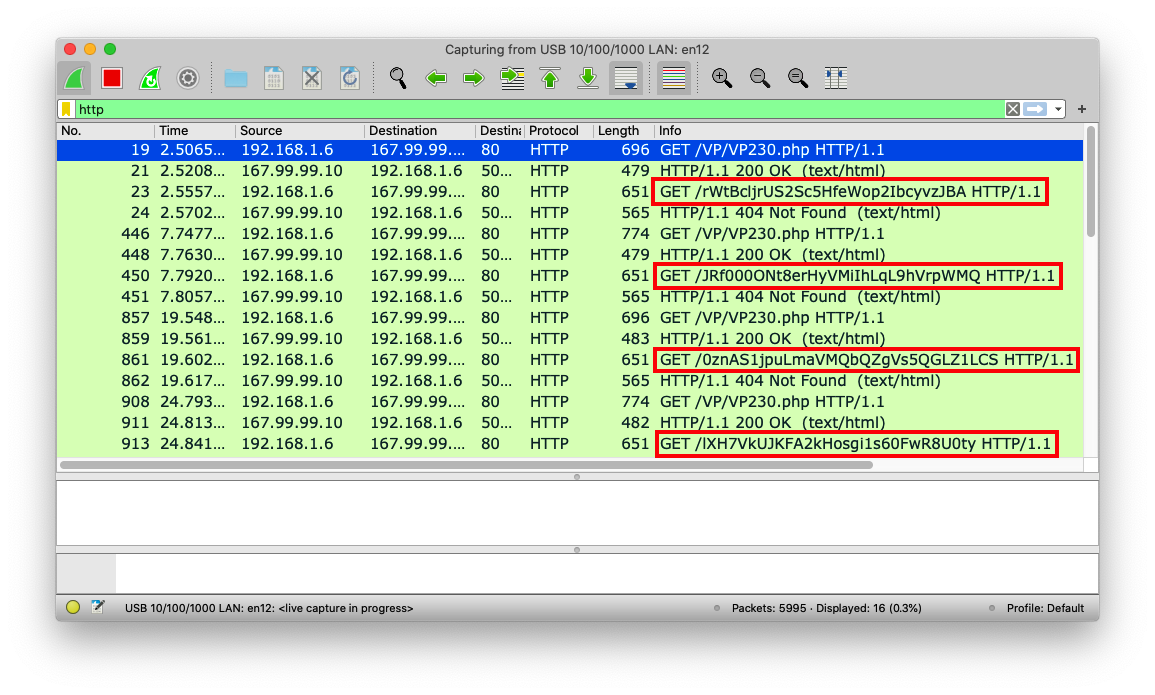
Notice the long folder names, outlined in red in the image below.

In this project, you'll write scripts to harvest the HTTP traffic and find the concealed data in it.
Execute this command to download and install the Scapy library:
python3 -m pip install scapy
from scapy.all import *
def findHTTP(p):
if p.haslayer(TCP):
if p[TCP].dport == 80:
print(p.summary())
print(p.display())
sniff(prn=findHTTP)
You see a lot of data about the HTTP requests scroll by, as shown below.
Press Ctrl+C to stop the program.
from scapy.all import *
def findHTTP(p):
if p.haslayer(TCP):
if p[TCP].dport == 80:
if p.haslayer(Raw):
print(p[Raw].load)
sniff(prn=findHTTP)
Press Ctrl+C to stop the program.
Flag VP 230.1: Directory Name (10 pts)
In a Web browser, open this page:http://samlol.samsclass.info/VP/VP230-1.php
Monitor the HTTP requests. After a while you'll find the flag, as shown below.
Flag VP 230.2: Hex Encoding (10 pts)
In a Web browser, open this page:http://samlol.samsclass.info/VP/VP230-2.php
Monitor the HTTP requests. Some of the requests contain the flag, but they are encoded.
Hints
Flag VP 230.3: Binary Encoding (10 pts)
In a Web browser, open this page:http://samlol.samsclass.info/VP/VP230-3.php
Monitor the HTTP requests. Some of the requests contain the flag, but they are encoded.
Flag VP 230.4: Base64 Encoding (10 pts)
In a Web browser, open this page:http://samlol.samsclass.info/VP/VP230-4.php
Monitor the HTTP requests. Some of the requests contain the flag, but they are encoded.
Flag VP 230.5: Base58 Encoding (10 pts)
In a Web browser, open this page:http://samlol.samsclass.info/VP/VP230-5.php
Monitor the HTTP requests. Some of the requests contain the flag, but they are encoded.
Hint: Base58Check encoding