

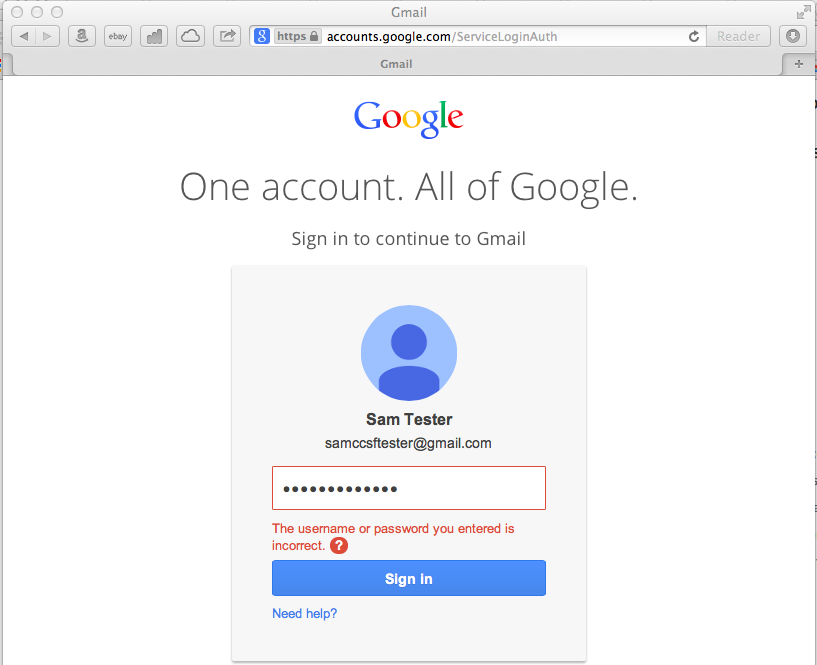
I attempted to log in to Gmail using a password of test_password (which is incorrect and rejected by Gmail):
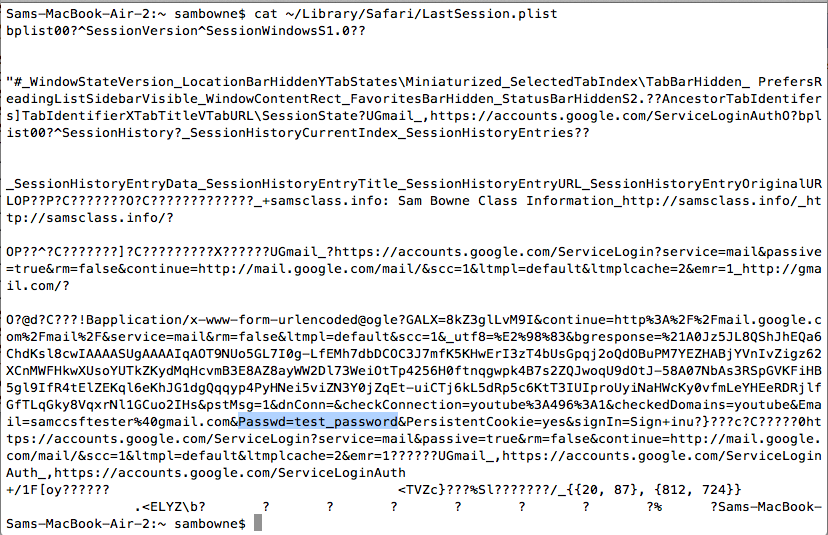
Then, in a Terminal, I executed this command:
cat ~/Library/Safari/LastSession.plist
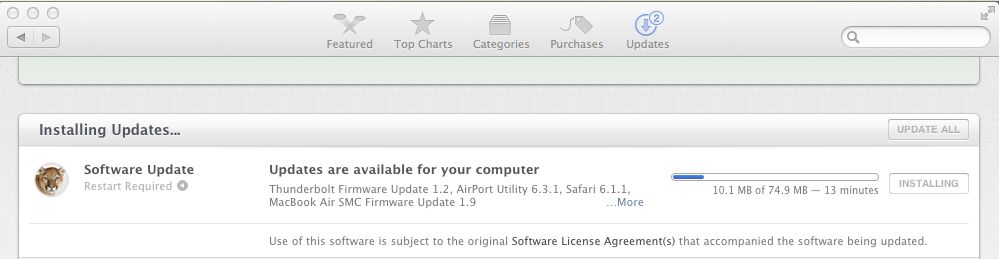
Now I went to the Apple Store and installed the Software Updates, including Safari 6.1.1:
I could have updated to Mavericks, but I didn't, I am still using Mt. Lion:

After the update, I have Safari 6.1.1:

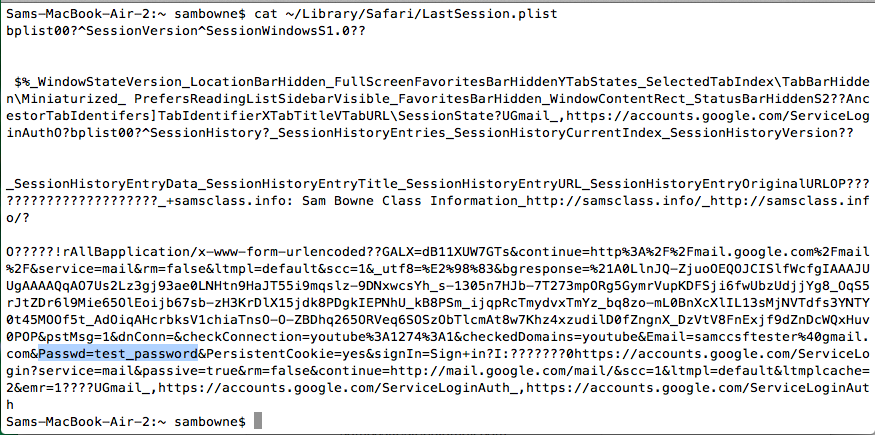
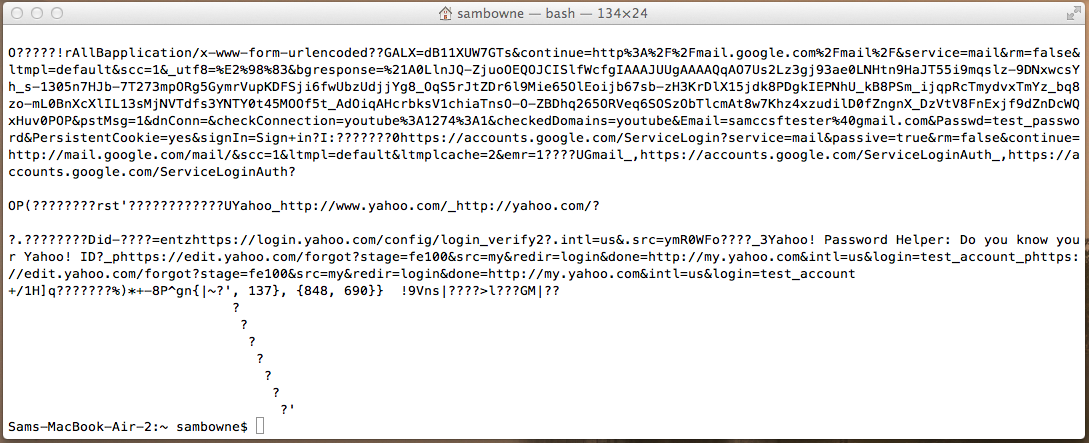
I attempted to log in to Gmail again, with the same password, and it's still visible in the plist file!
I attempted to log in to Yahoo then, with a password of topsecretpassword2:

Although the old Gmail credentials are still there, the Yahoo credentials no longer include the password in plaintext:
In hex, the Yahoo session storage clearly no longer includes the password in plaintext:
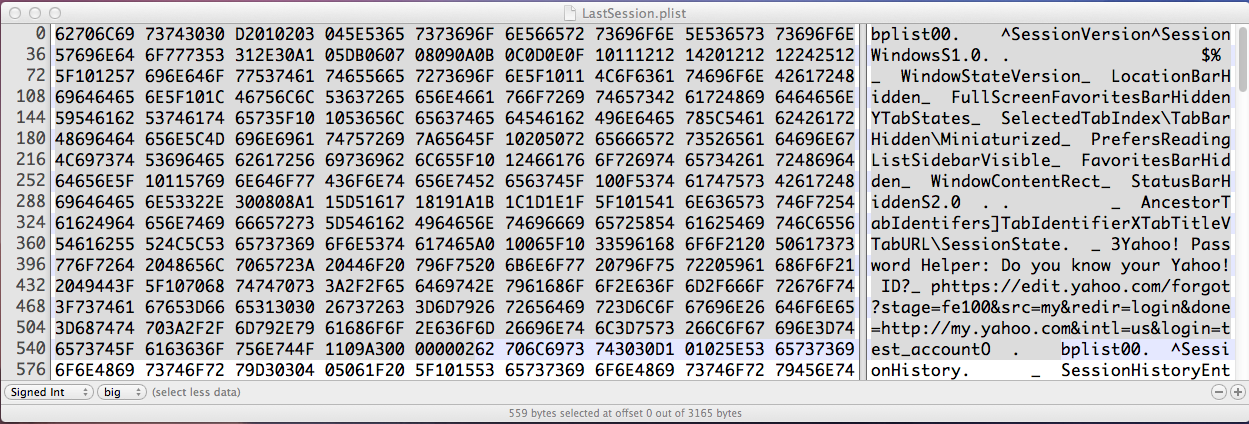
So the patch is OK, although it would have been nice to re-encode old sessions on upgrade.
Posted by Sam Bowne 11:09 am 1-2-14