dpkg-reconfigure mysql-server-5.5
Type in a password of
password
In the next box, type in a password of
password
This is obviously an insecure password, but use it anyway for this project, to match the password SQLol expects.
In a Terminal window, enter these commands:
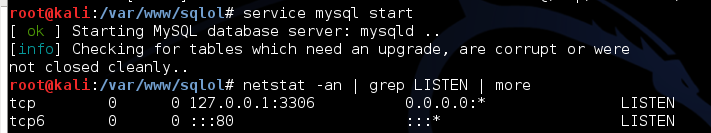
service mysql start
netstat -an | grep LISTEN | more

service apache2 restart
In your Linux machine, in a Terminal window, enter these commands:
cd /var/www
curl https://samsclass.info/124/proj11/sqlol-sbowne.tgz >sqlol-sbowne.tgz
tar xzf sqlol-sbowne.tgz
In IceWeasel, go to
SQLol opens, as shown below:
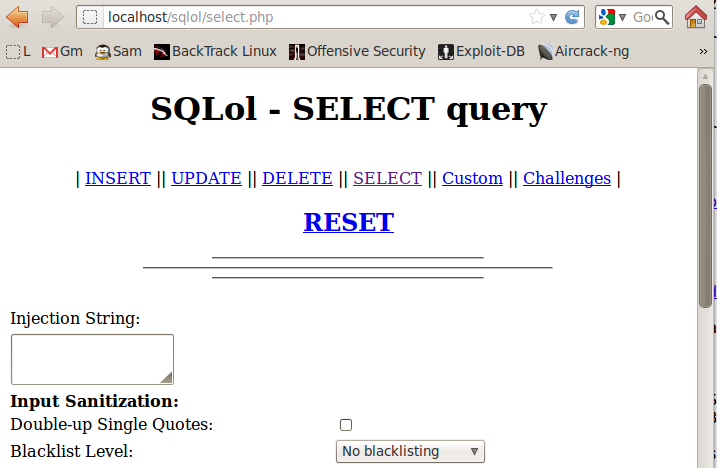
Click RESET
A message appears saying "Done!"
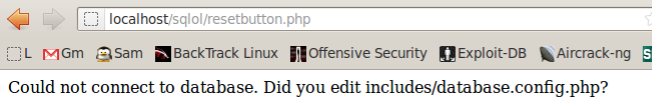
If you see the "Could not connect..." message shown below, restart mySQL with this command:
service mysql restart
In IceWeasel, click the Back button.
A list of challenges appears, as shown below:
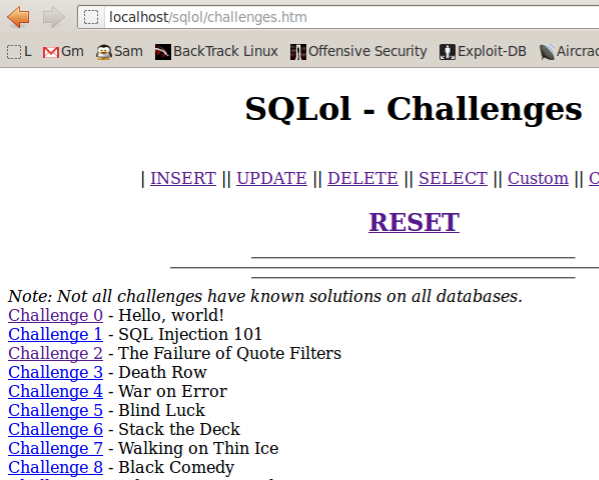
Click the "Challenge 0" link.
Scroll to the bottom of the next page to see the result of your injection, as shown below:

The SQL statement is shown--you have searched for records with username = 'Student'. Since there is no such user, there are no results.
Enter a single asterisk in the "Injection String" field, and click the Inject! button.
Scroll to the bottom of the next page to see the result of your injection, as shown below:

This searched for username = '*', which doesn't exist, so it again returns no results.
Enter a single apostrophe in the "Injection String" field, and click the Inject! button.
Scroll to the bottom of the next page to see the result of your injection, as shown below:

Note the message saying "Error: You have an error in your SQL syntax" -- that indicates a SQL injection vulnerability.
With a more carefully crafted injection, you can get the whole list of usernames to diplay.
Try to figure it out yourself. If you need help, see the tutorial here:
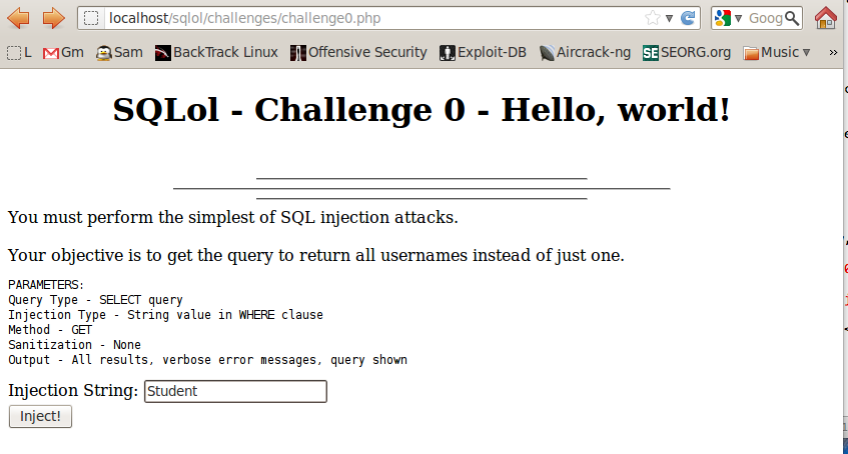
When you succeed, you will see a list of five records as shown below:
Make sure you can see the five records, as shown in the image above on this page, but without the gray box obscuring the data.
Save a screen image with the filename Proj 19a from Your Name.
Click the "Challenge 1" link.
This time your goal is to find SSNs.
Try to figure it out yourself. If you need help, see the tutorial here:
When you succeed, you will see a list of five records as shown below:

Make sure you can see the five records, as shown in the image above on this page, but without the gray box obscuring the data.
Save a screen image with the filename Proj 19b from Your Name.
Click the "Challenge 2" link.
Once again, your goal is to find SSNs. The new feature is that you are injecting into a numeric field, not a text field, so you won't need apostrophes.
Try to figure it out yourself. If you need help, see the tutorial here:
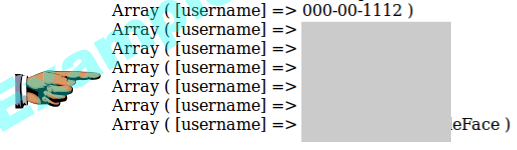
Make sure you can see the seven records, as shown in the image above on this page, but without the gray box obscuring the data.
Save a screen image with the filename Proj 19c from Your Name.
Email the images to cnit.123@gmail.com with a Subject line of Proj 19 from Your Name.
http://www.unixmen.com/how-to-enable-and-disable-apache-modules/
Last modified: 4-18-15