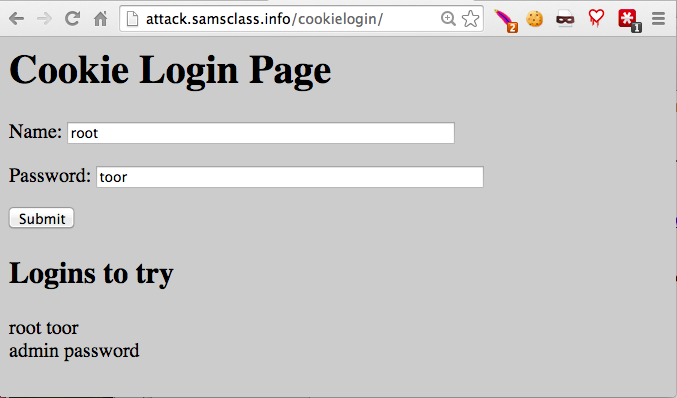
http://attack.samsclass.info/cookieloginLog in with a Name of root and a Password of toor, as shown below.

A Message Board opens, as shown below. Notice the "Welcome" message, showing that you are logged in.
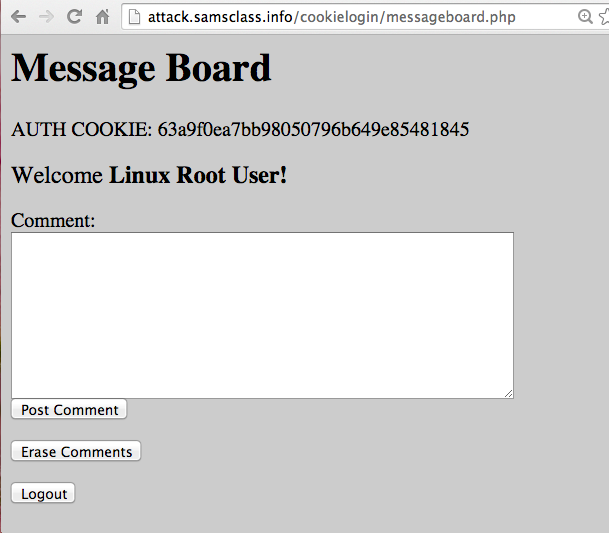
Notice the "AUTH COOKIE" value--a long string of random-looking numbers and letters.
Log out and log in again with the other credentials--"admin" and "password". Examine the cookie.
Log in and out a few times to see what cookies you see.
Try to figure out how the cookie is constructed. When you get it, figure out the cookie for this account:
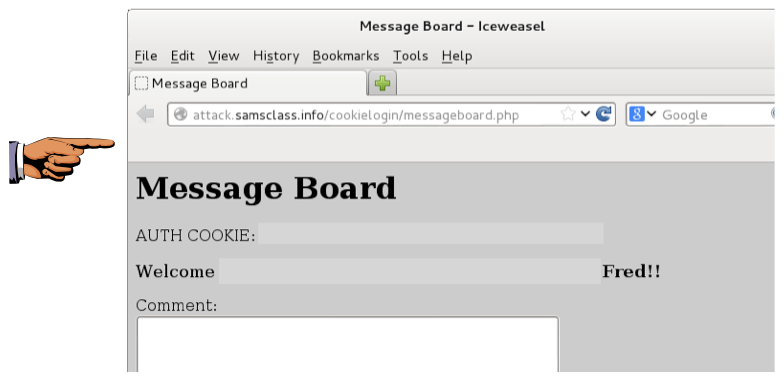
Username: fredWhen you get in, you'll see the page below (with the grayed-out sections visible).
https://hashcat.net/wiki/doku.php?id=example_hashes
Save a FULL DESKTOP image with the filename Proj X6 from Your Name.