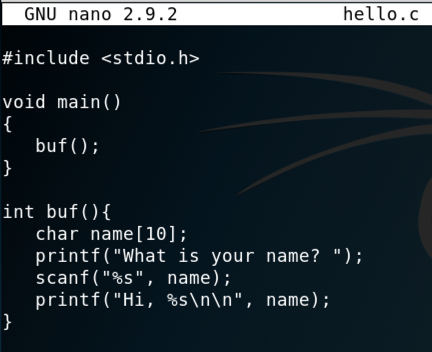
nano hello.c
#include <stdio.h>
void main()
{
buf();
}
int buf(){
char name[10];
printf("What is your name? ");
scanf("%s", name);
printf("Hi, %s\n\n", name);
}

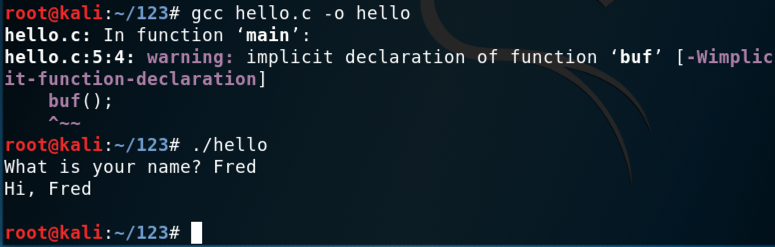
gcc hello.c -o hello
./hello
It should ask you for your name. When you type in your name (no longer than 10 characters), you should be greeted by name, as shown below.
./hello
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
In a Terminal window, execute this command, which loads the "hello" program into the "gdb" debugger:
gdb -q hello
run
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
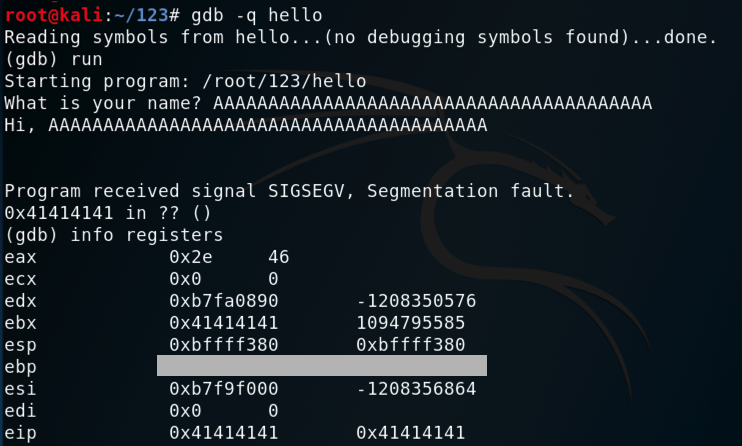
info registers
Troubleshooting
If you see longer register values with names like rax and rip, you are using a 64-bit machine. Download a 32-bit Kali machine and start over.
Use the form below to record your score in Canvas.
If you don't have a Canvas account, see the instructions here.
#include <stdio.h>
void main()
{
buf();
}
int buf(){
char name[3];
printf("What is your name? ");
scanf("%s", name);
printf("Yo, %s\n\n", name);
}
Run the program for a short name. The program runs properly, as shown below.
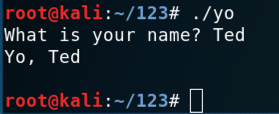
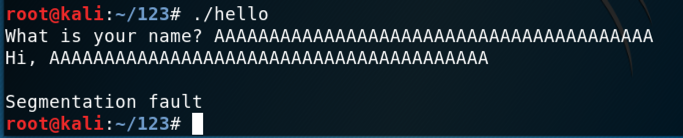
Try longer names until the program crashes, as shown below. This process is called "fuzzing" and it's an essential part of vulnerability discovery.
Use the form below to record your score in Canvas.
If you don't have a Canvas account, see the instructions here.
Use the form below to record your score in Canvas.
If you don't have a Canvas account, see the instructions here.