
Fill out the form with your name and email address and click the Register button.
On the next page, click the Download button.
Click the appropriate download link, as shown below.
Agree to the agreement.
A Web page opens, as shown below.
Click the "Connect via SSL" button.

On the next page, approve the SSL exception. If you are using Internet Explorer, that's done by clicking "Continue to this website (not recommended)".
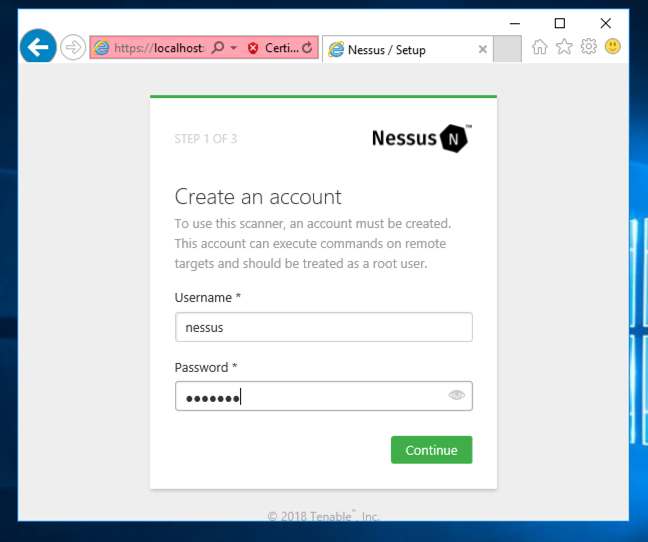
On the next page, enter a username and password you can remember, as shown below. I used nessus and Nessus!, which are obviously not very secure choices, appropriate only for testing purposes.
Click Continue.
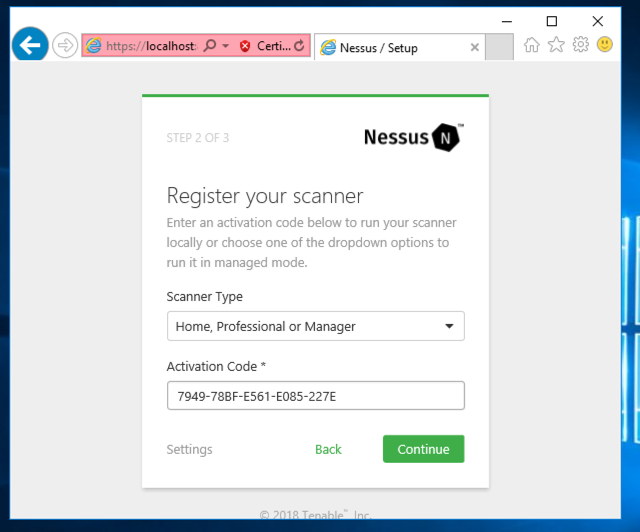
The next page asks for your Activation Code, as shown below. Check your email to get it.
Enter it and click Continue.
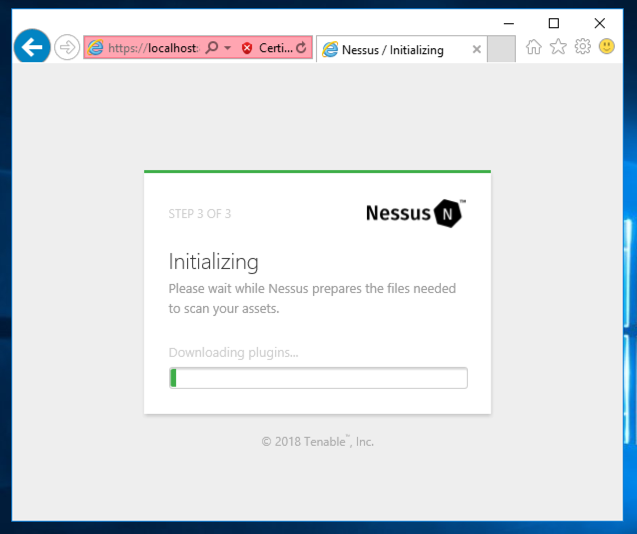
Wait while software downloads and installs, as shown below.
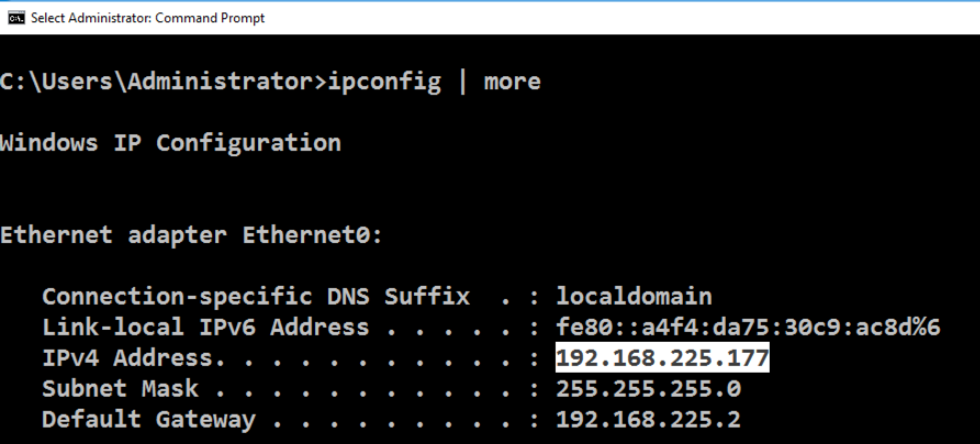
IPCONFIG
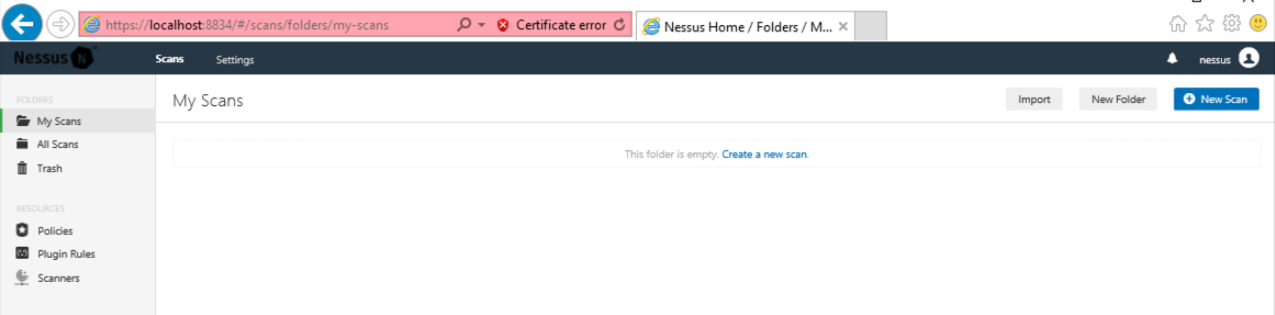
At the top right, click the "New Scan" button.
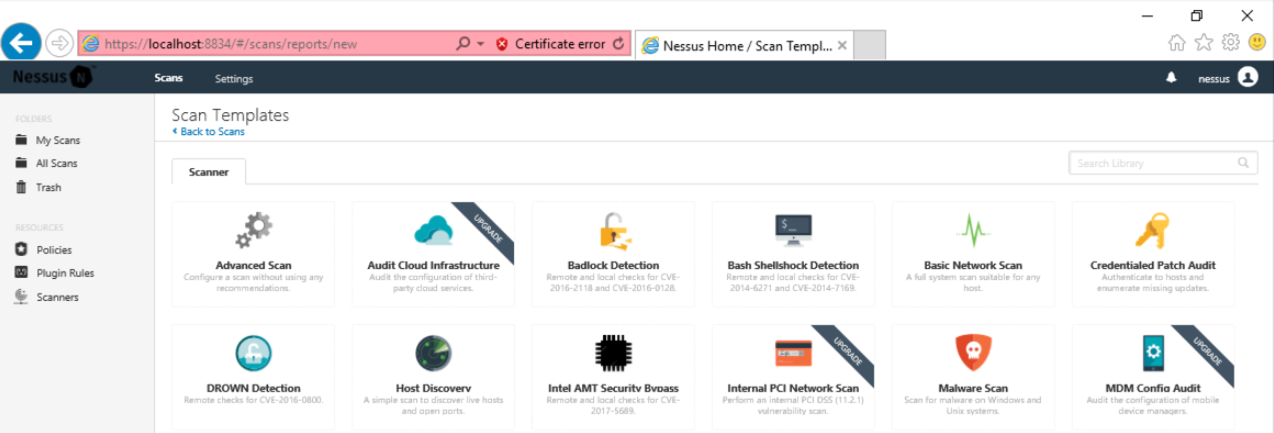
In the "Scan Templates" page, click "Basic Network Scan", as shown below.
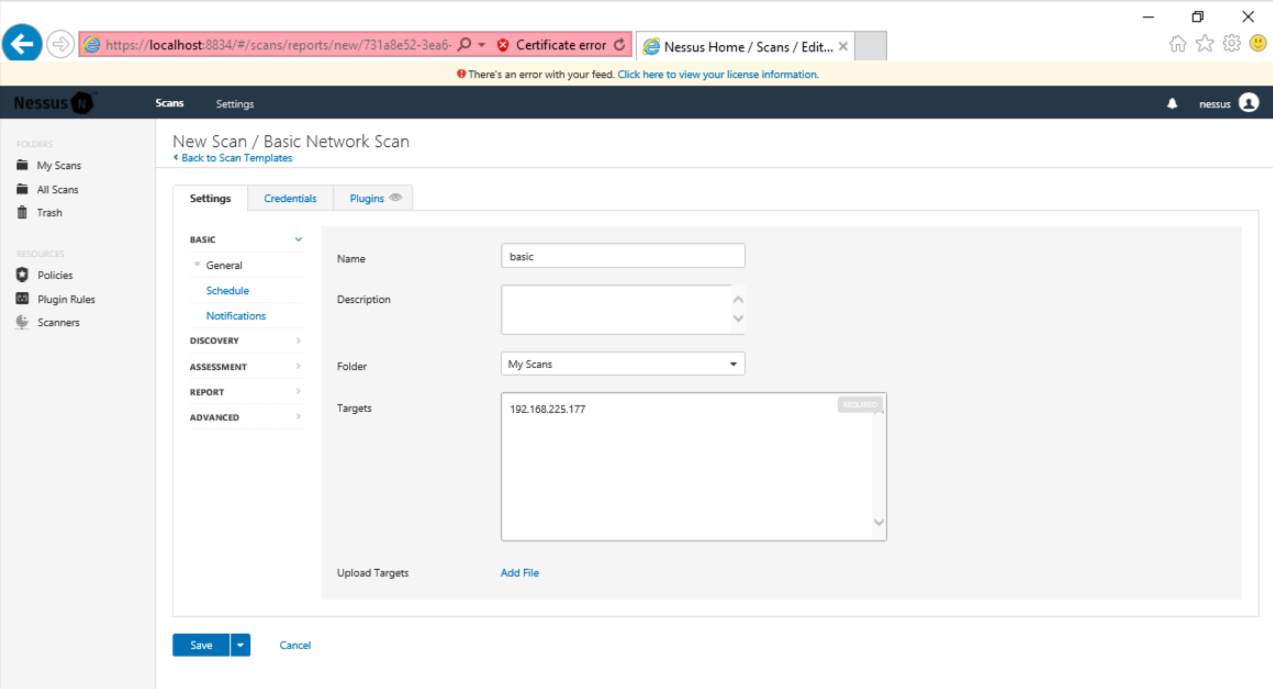
Enter a Name of "basic" and a Target of your IP address, as shown below.
At the lower left, click the Save button.
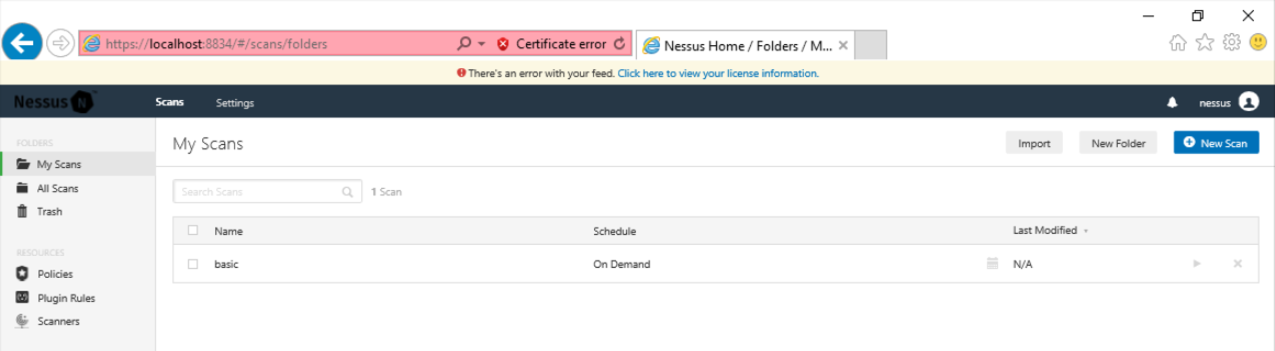
In the "My Scans" page, on the "basic" line, on the right side, click the right-arrow to launch your scan, as shown below.
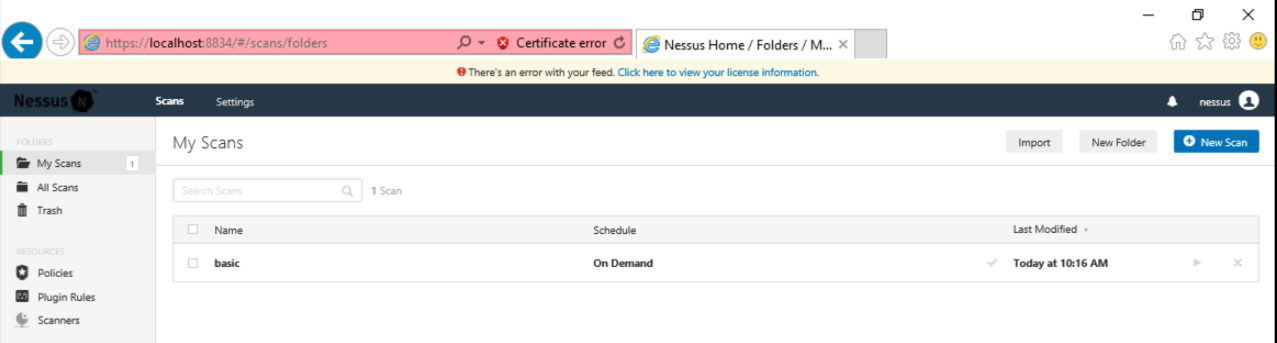
When the scan finishes, a gray check mark will appear in its line, as shown below.
Click "On Demand".
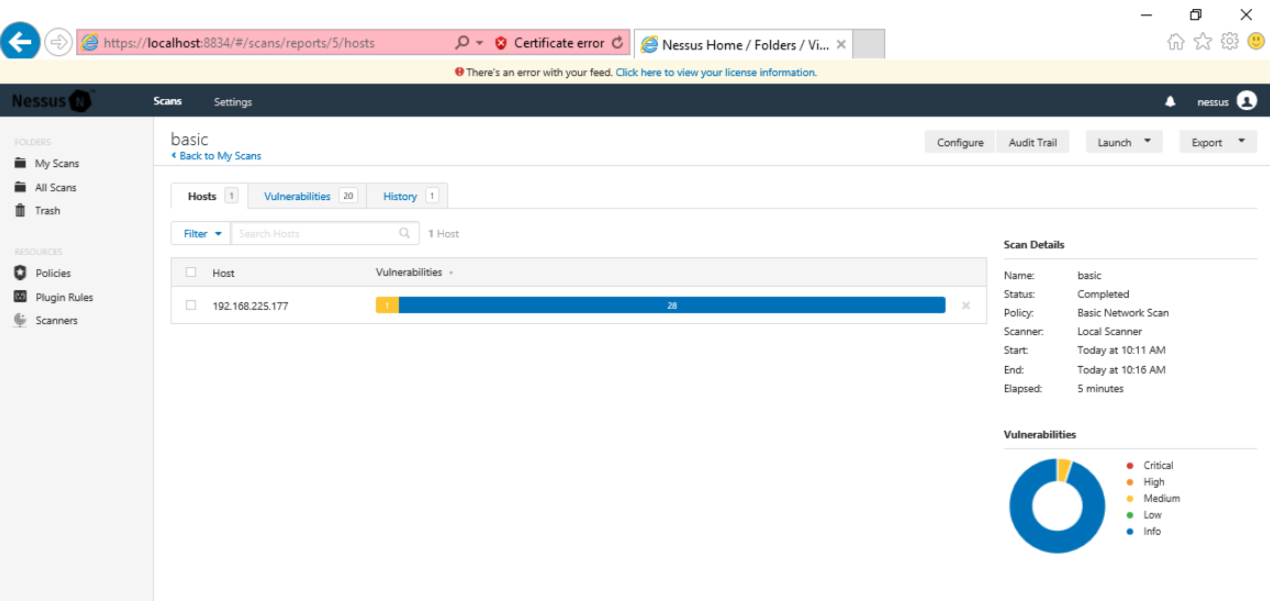
The results appear, as shown below.
They are color-coded.
Click the Vulnerabilities tab to see details, as shown below.
Click "SMB Signing not required".
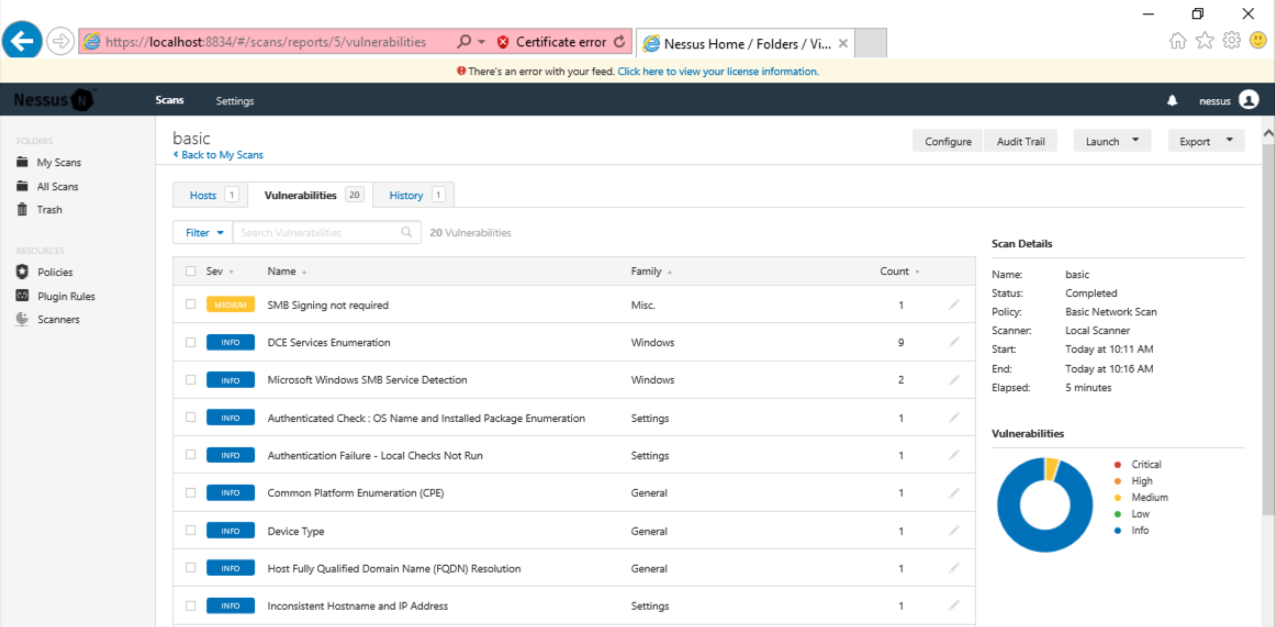
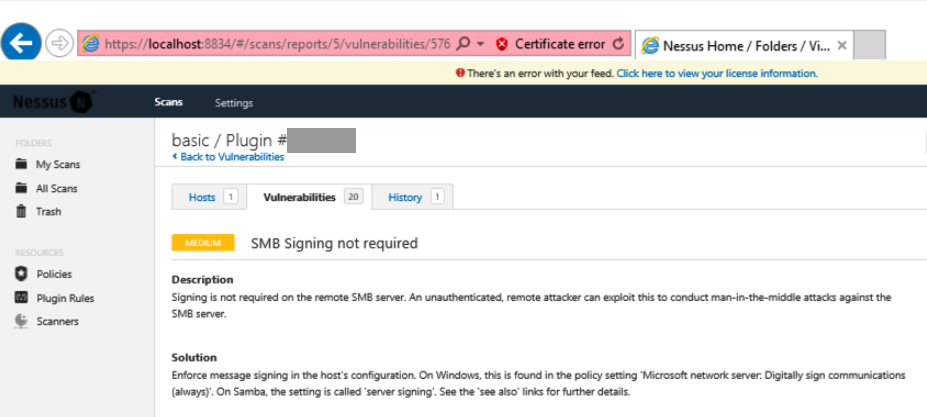
On the next page, find the Plugin #, which is covered by a gray box in the image below.
If you don't have a Canvas account, see the instructions here.
In the results, click the Vulnerabilities tab. Click "Nessus SYN scanner", as shown below.
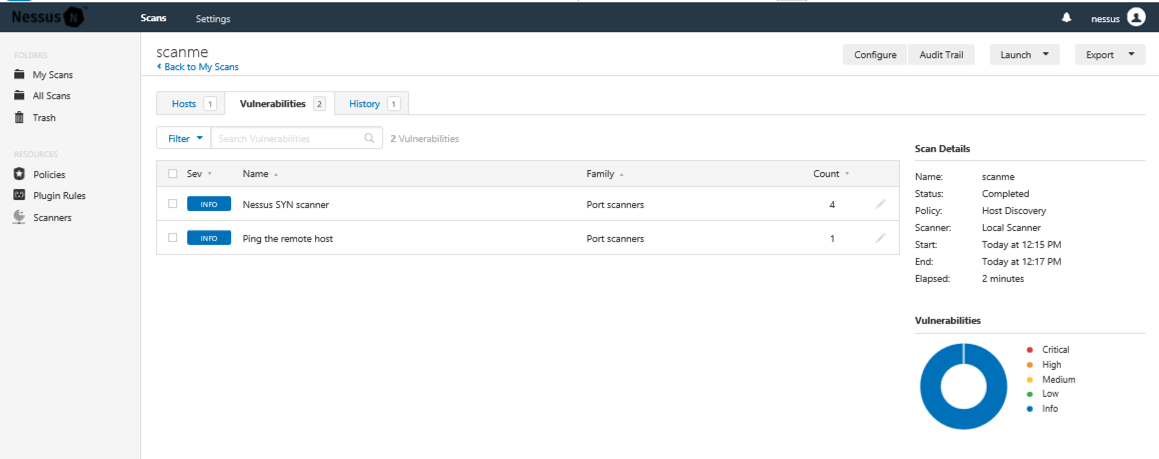
Four ports are open. Find the port number of the highest open port and enter it into the form below.
If you don't have a Canvas account, see the instructions here.
https://samsclass.info/126/PMA.shtml
Scan that machine with these steps:
The scan should find three critical vulnerabilities, as shown below.
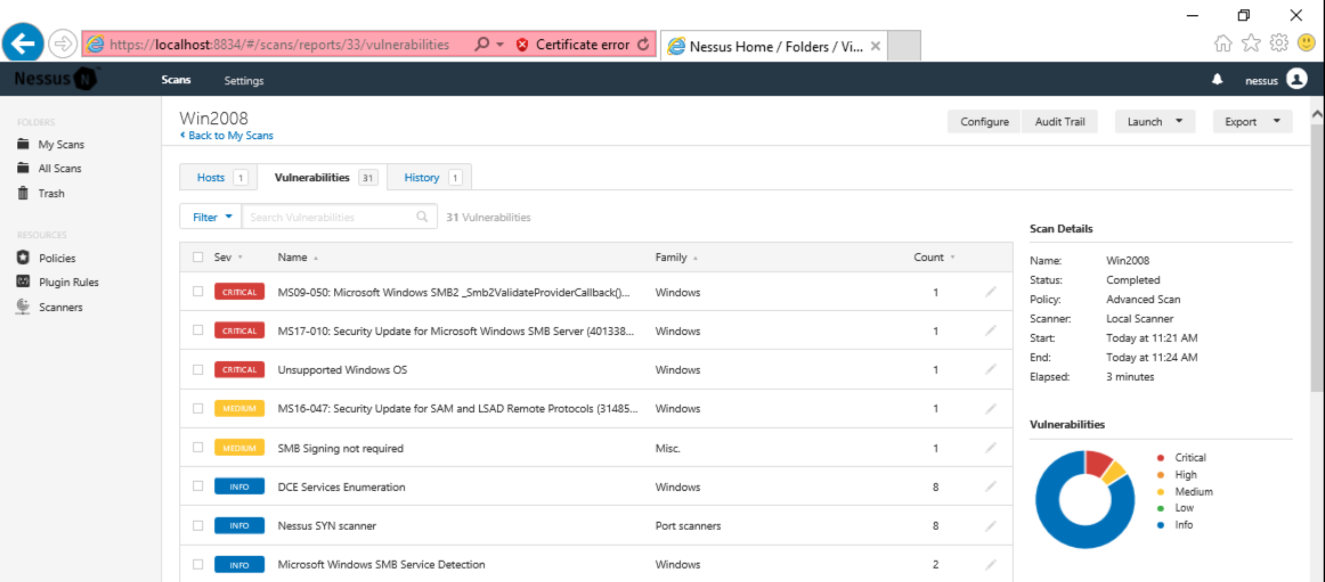
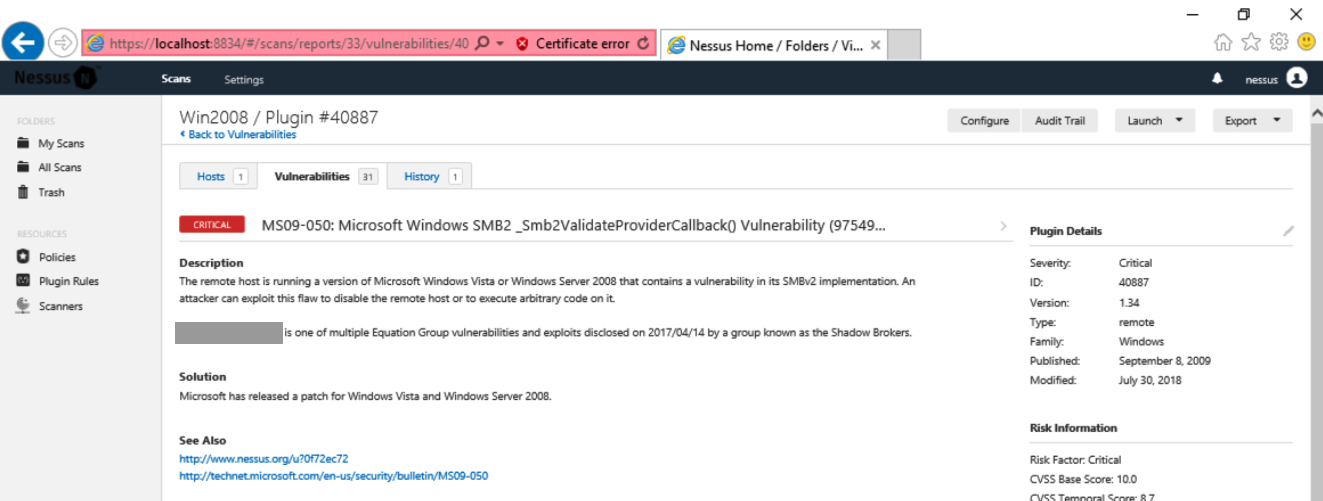
Click the first one. This is one of the Equation Group vulnerabilities, leaked from the NSA. Find the US military code name for this exploit, which is covered by a gray box in the image below.
If you don't have a Canvas account, see the instructions here.
Posted 9-6-18
Added installation of dirmngr 10-10-18
Removed reference to Debian 11-6-18