ifconfig
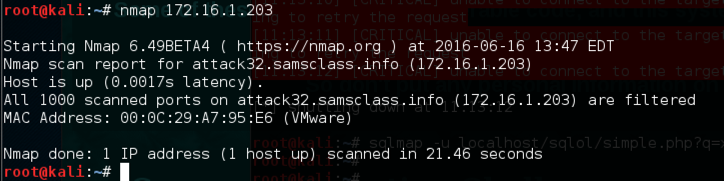
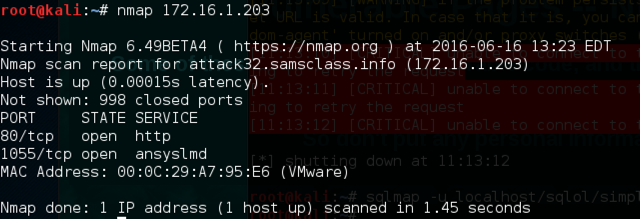
nmap 172.16.1.203

Kali includes the iptables firewall, which is very powerful, but difficult to use.
However, for this project, we'll use "ufw" -- the Uncomplicated Firewall.
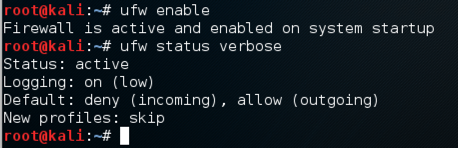
In your Kali32 machine, in a Terminal window, execute these commands:
ufw enable
ufw status verbose
This makes your Kali32 machine a client, but never a server, which is the same thing the Windows firewall does by default on public networks.
nmap 172.16.1.203