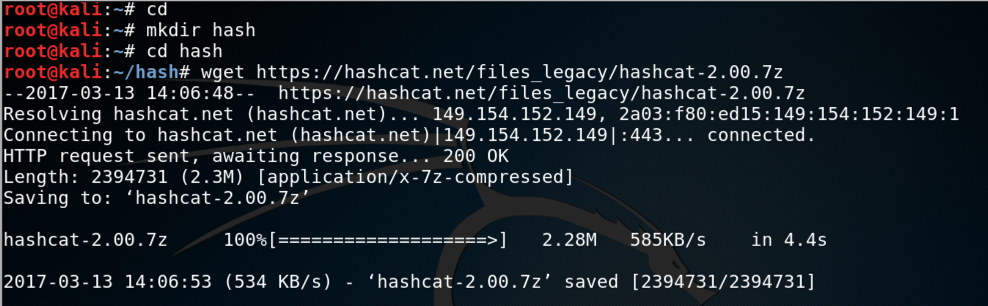
In a Terminal window, execute these commands:
cd
mkdir hash
cd hash
wget https://hashcat.net/files_legacy/hashcat-2.00.7z
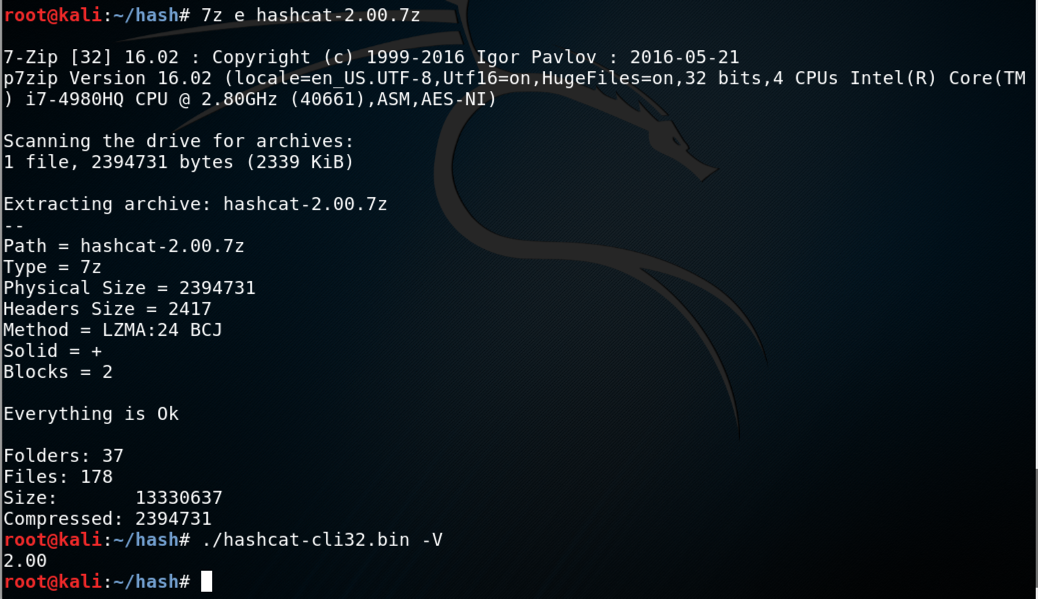
7z e hashcat-2.00.7z
./hashcat-cli32.bin -V

Troubleshooting
If that link doesn't work, use this one:wget https://samsclass.info/123/proj10/hashcat-2.00.7z
Troubleshooting
If you see an "No such file or directory" error message when launching hashcat-cli32.bin, you may be using a 64-bit Kali system. Try using hashcat-cli64.bin instead.
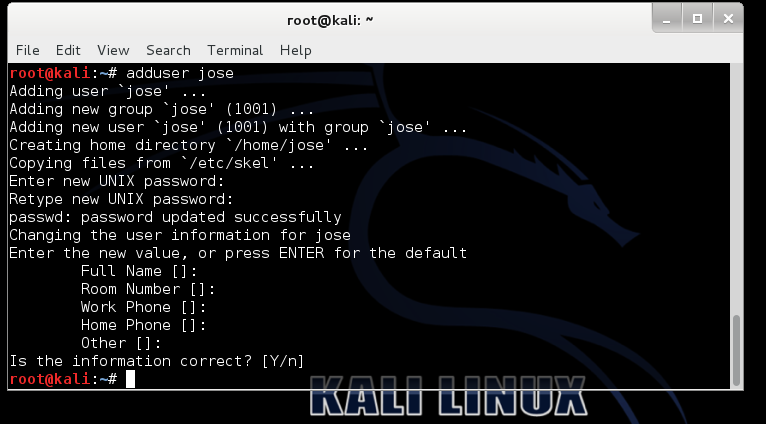
adduser jose
At the "Retype new UNIX password" enter a password of password
Press Enter to accept defaults for the other options, as shown below:
tail /etc/shadow
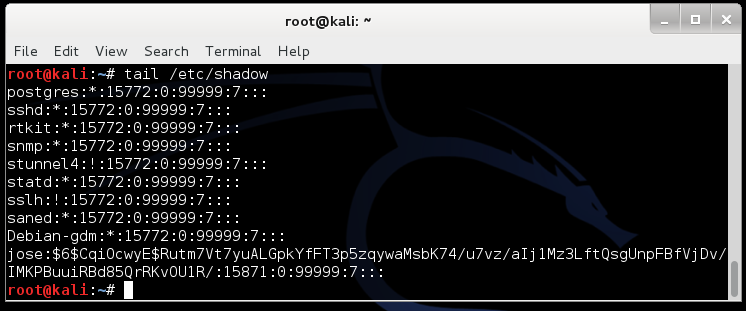
In my example, the SALT is CqiOcwyE
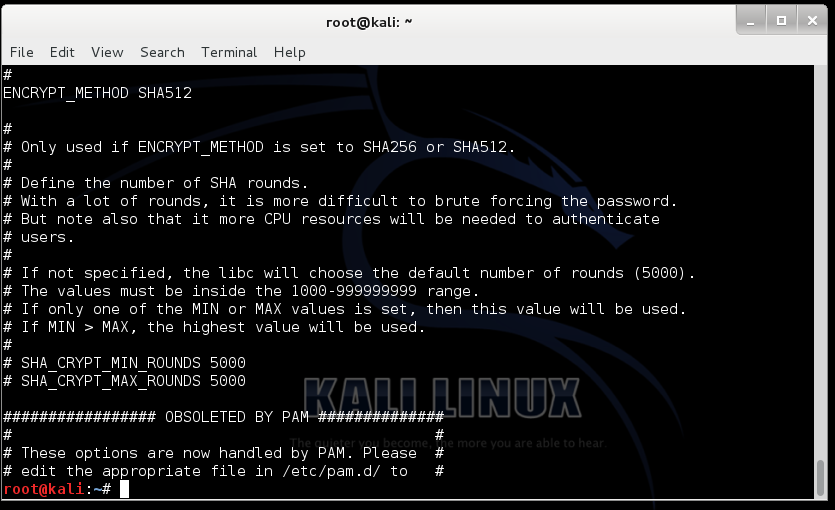
grep -A 18 ENCRYPT_METHOD /etc/login.defs
tail -n 1 /etc/shadow > crack1.hash
nano crack1.hash
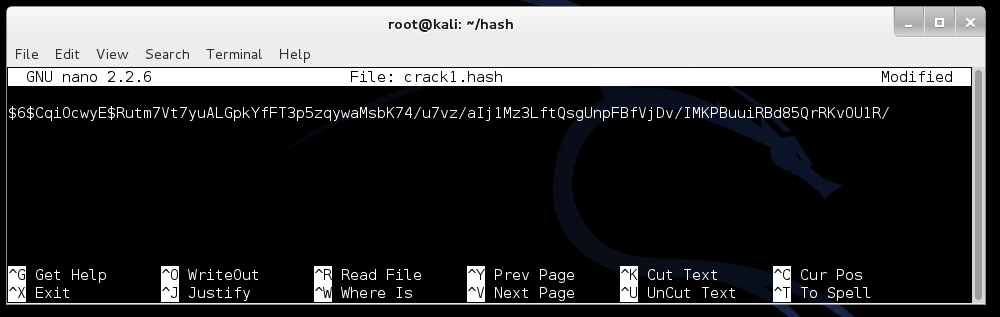
Press Ctrl+X, Y, Enter to save the file.
In a Terminal window, execute these commands:
curl http://www.scovetta.com/download/500_passwords.txt > 500_passwords.txt
head 500_passwords.txt
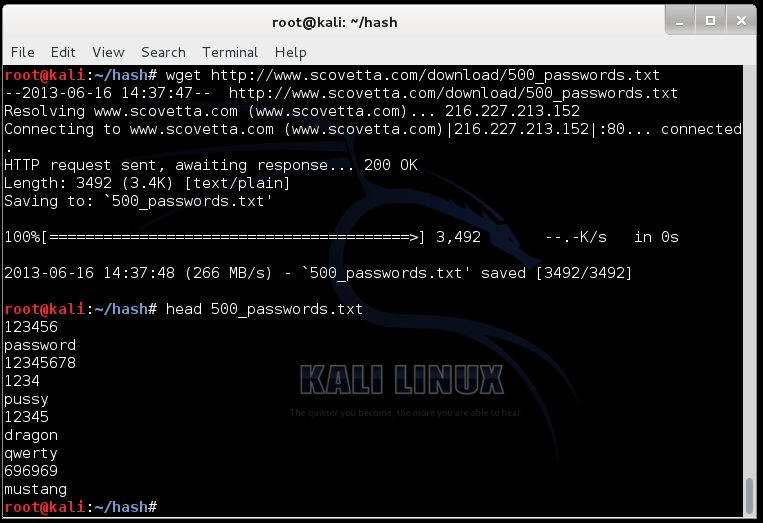
Troubleshooting
If that link doesn't work, use this one:curl https://samsclass.info/123/proj10/500_passwords.txt > 500_passwords.txt
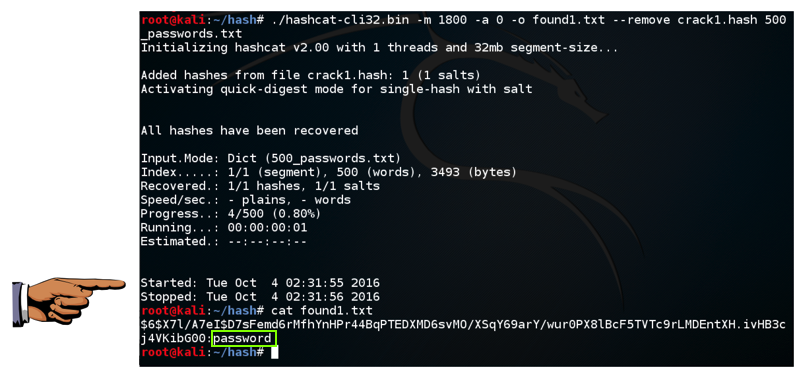
./hashcat-cli32.bin -m 1800 -a 0 -o found1.txt --remove crack1.hash 500_passwords.txt
cat found1.txt
You should see the hash, with the cracked password of "password" at the end, as shown below:
Click on the host machine's desktop, outside the virtual machine to make the host machine's desktop active.
Press the PrintScrn key to copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT.
In the host machine, open Paint and paste in the captured image. Save it as "Your Name Proj12a".
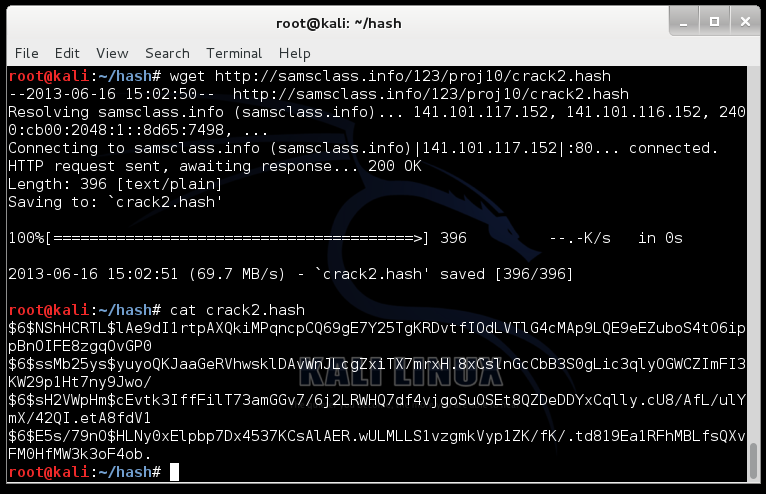
curl https://samsclass.info/123/proj10/crack2.hash > crack2.hash
cat crack2.hash
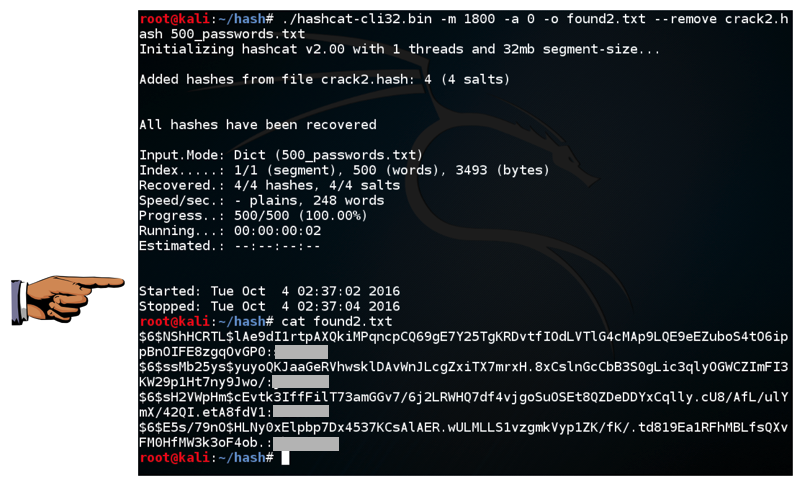
./hashcat-cli32.bin -m 1800 -a 0 -o found2.txt --remove crack2.hash 500_passwords.txt
cat found2.txt
Click on the host machine's desktop, outside the virtual machine to make the host machine's desktop active.
Press the PrintScrn key to copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT.
In the host machine, open Paint and paste in the captured image. Save it as "Your Name Proj12b".
http://hashcat.net/files/hashcat_user_manual.pdf
http://contest-2010.korelogic.com/wordlists.html
http://www.scovetta.com/article-2.html