Note: I just tested it with a time delay, and the stolen cookie stops working after ten minutes of inactivity, so that lowers the risk to some extent. -- Added 11:19 am 7-23-13
Note: I just tested it with a time delay, and the stolen cookie stops working after ten minutes of inactivity, so that lowers the risk to some extent. -- Added 2:07 pm 7-23-13
So the "Log off" feature is the opposite of security--blocking the authorized user but not blocking attackers.
Why doesn't logging off cancel the cookie? That is obviously the intent of the user who clicks it. This seems like a bug to me. However, Microsoft was notified last year and decided they like it this way, as detailed in the Hacker News article.
Click here for step-by-step instructions.
Here is the list of sites I and others have tested so far.
BAD
|
GOOD
|
Financial | |
|
American Express (E) Chase (E) |
Discover Card (J) @askRegions Bank (I) TDbank (G) Bank of America (L) Arizona Federal Credit Union (L) @BECU (O) |
Shopping | |
|
Amazon (A C) IBM (including Many Eyes) NetFlix (F) TigerDirect (A C) Woot (M) |
Adobe Craigslist Travelocity Newegg (N) |
Email & Social | |
|
Chrome App Store (A C G H) Flickr iCloud (C K) Live.com Office 365 (A B) Soundcloud (G) Stumbleupon Twitter (C K) Wordpress Yahoo mail YouTube (D G H) |
Facebook Gmail Tweetdeck |
News | |
|
Forbes The Guardian Huffington Post The New York Times The Register |
Ars Technica Slashdot |
Security | |
|
Packet Storm (G) |
Cloudflare (Fixed on 7-25-13) (ISC)^2 LastPass Mitto My1Login Need My Password Passpack |
Others | |
|
CourseSmart Github NameCheap (I) Vimeo Waze WHMCS (G) |
alpha.app.net (tested by @nicoduck) Dropbox Godaddy Insight (CCSF's Online Course System) |
NotesA Cookie still works after password reset! (ty @dakami for asking this question)B Cookie still works when copied to another machine (ty @0x90NOP and @winremes for asking this question) C Cookie still worked after 12 hours logged out D Cookie no longer worked after 12 hours logged out E Cookie expires after 10 minutes F Tested by @privacyfanatic G Tested by @_KrypTiK H Verified by @sambowne I Tested by @jTizYl J Tested by Julie Hietschold K Password reset invalidates old cookie L Tested by Hector Acencio M Tested by @NDRoughneck N Tested by @splint3rz O Tested by @vaha | |
"Re: the ineffective logout mechanisms you were talking about...ASP.NET's forms authentication function exhibits the behaviour you were describing (i.e. only invalidating the cookie on the client side at logout). This is definitely a bad idea (which is of course the point you were making) but I guess it is part of the reason why so many sites have this issue (in particular I remember seeing Office365 and another Microsoft site on your list - they may well be using ASP.NET).We often report this issue when doing web application assessments for our clients, but without any real expectation that they'll do anything about it (because they'd either have to stop using ASP.NET forms auth or somehow persuade Microsoft to fix it!)"
From: Richard Turnbull, Principal Security Consultant, NCC Group
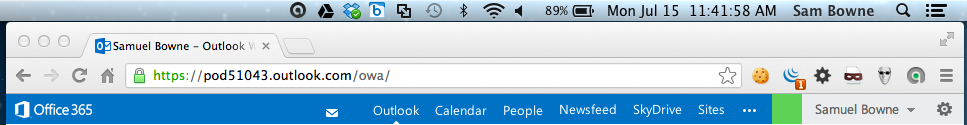
Your name appears in the upper right corner, as shown below, and your emails are visible.
Add this page to your Favorites, or make some other record of its URL.

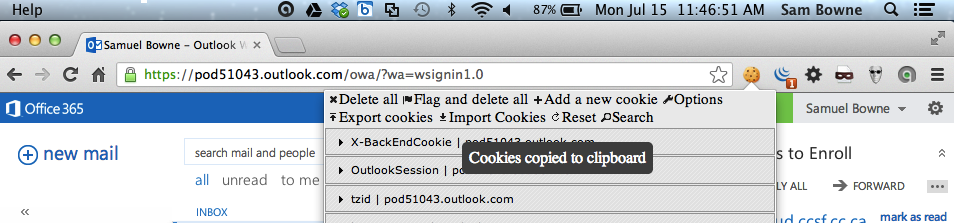
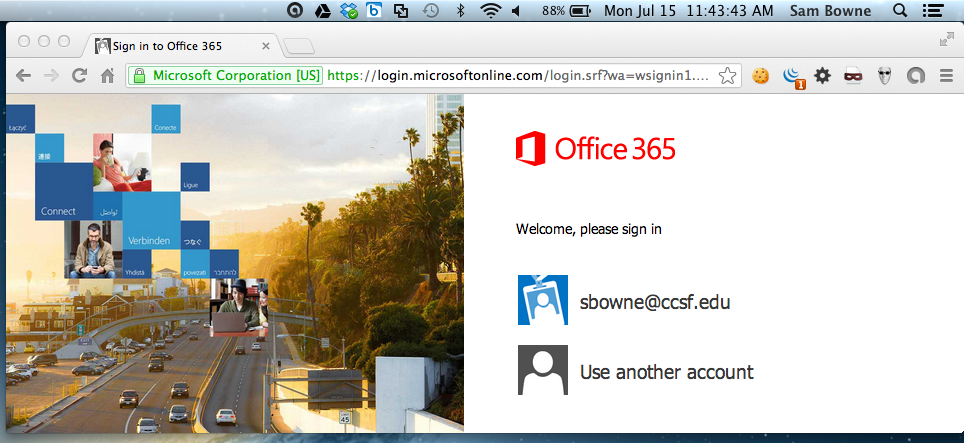
A box appears saying "Paste here the cookies to import". Paste the cookies there, as shown below (I redacted the image, since anyone with this data can apparently get into my Office 365 account.)
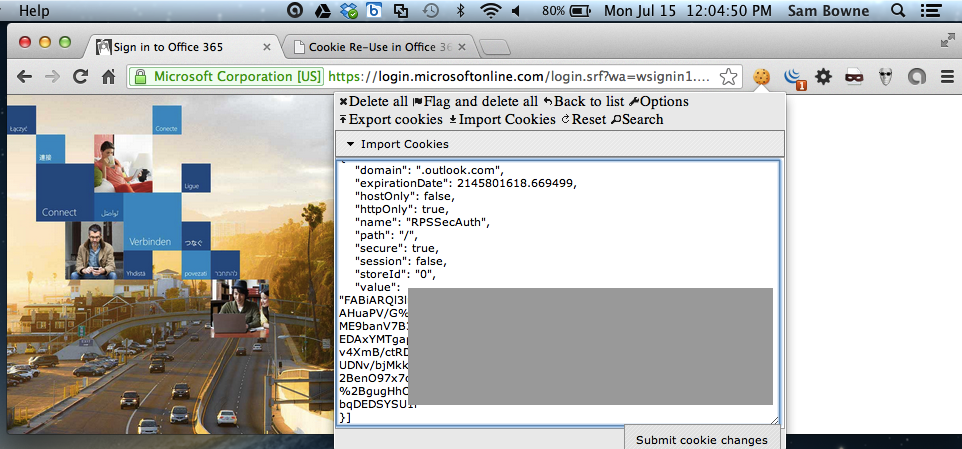
Then click the "Submit cookie changes" button.
If the site is not vulnerable, you will see a logon page.

This issue has been published by @privacyfanatic in Network World!