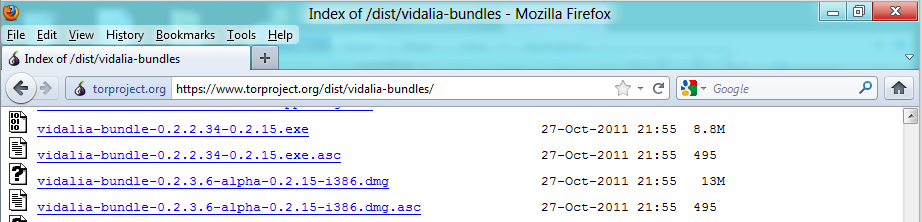
https://www.torproject.org/dist/vidalia-bundles
Scroll down and find the vidalia-bundle-0.2.2.34-0.2.15.exe link, as shown below:

Download and install the software with the default options.
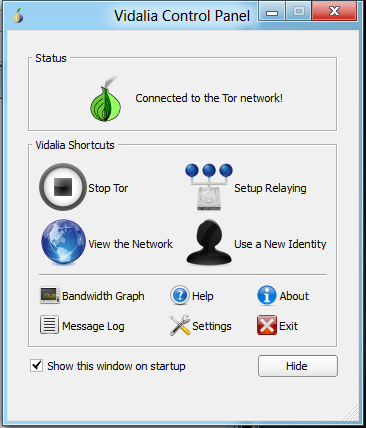
If it does not open, right-click the little icon in the Notification Area at the lower right of the desktop and click "Control Panel," as shown below:
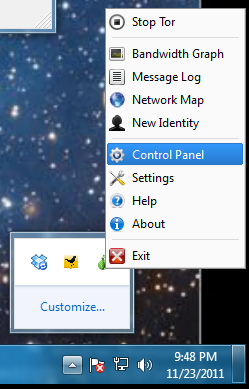
Click the Advanced tab. Clear the "Randomly Generate" box and type in a password of password as shown below:
Click OK.
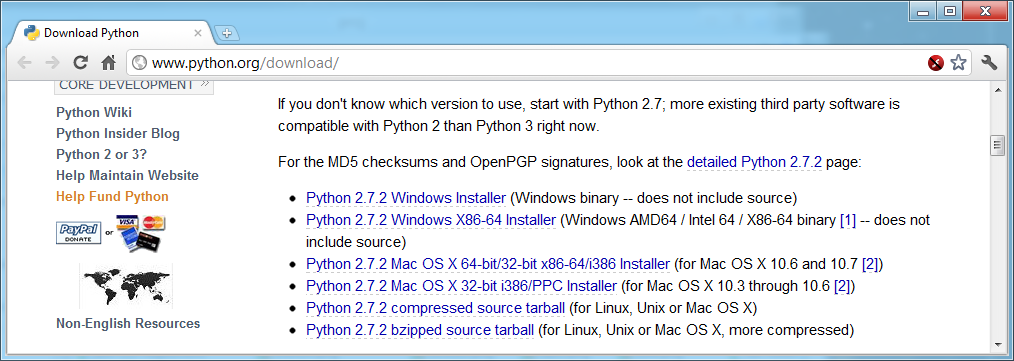
http://www.python.org/download/
Download the "Python 2.7.2 Windows Installer" as shown below:
Install Python with the default options.
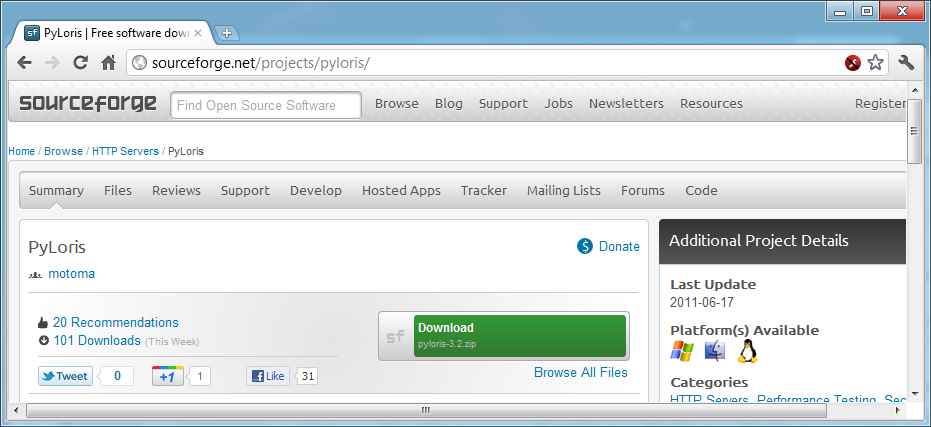
http://sourceforge.net/projects/pyloris/
Click the green "Download" button, as shown below:
Save the file, and unzip it. Open the "pyloris-3.2" folder to see the .py files, as shown below:

Two windows open. One is large and black, titled "C:\Python27\python.exe"--leave that one open but ignore it.
In the "TOR Switcher" window, type password in the password box, and change the Interval to 1, as shown below:
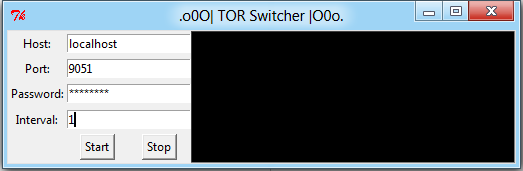
This will change your Tor relays every second.
You will be attacking one of my servers. If too many people bring it down all the time, I may have to take it offline, but hopefully people will leave it up long enough for students to do this project. It doesn't have anything essential on it.
In the "pyloris-3.2" window, double-click pyloris.py
As before, ignore the big black window and leave it open.
In the "PyLoris" window, make these changes:
Your window should look like the image below:
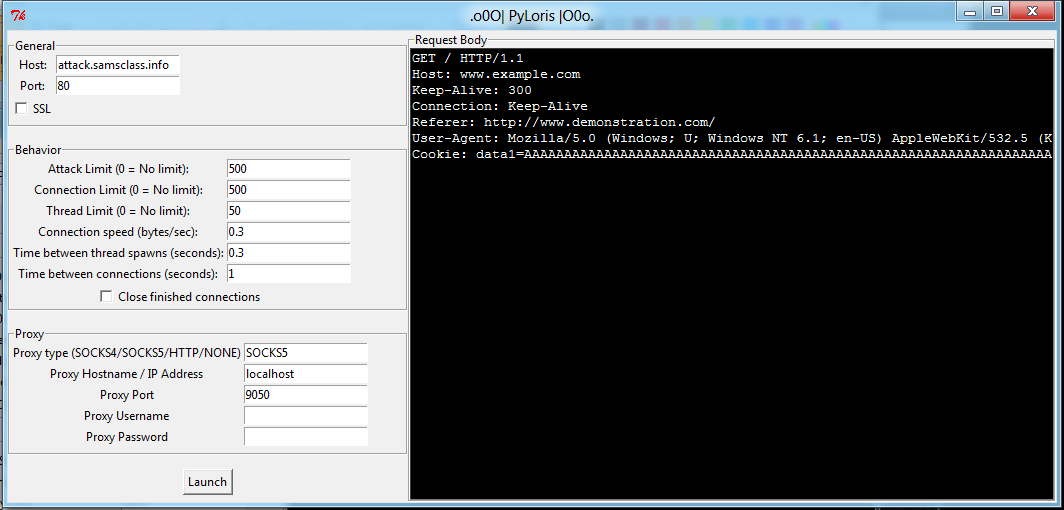
Don';t start the attack yet, because you need to start the server sniffing packets so you can tell that it is working.
A simple page opens, as shown below:
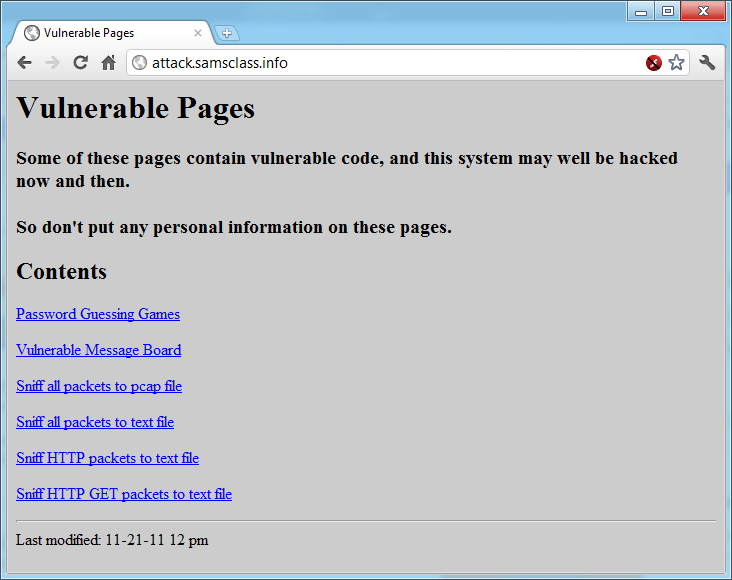
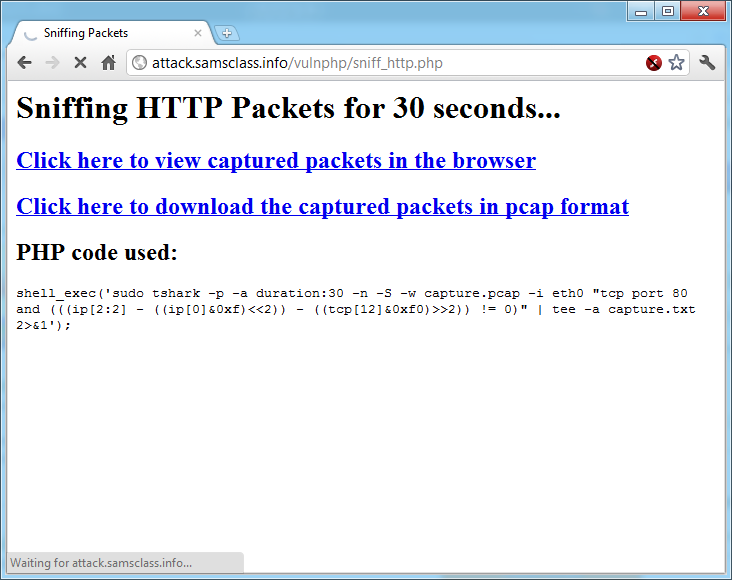
Click the "Sniff HTTP packets to text file" link. This starts the sniffer. It will run for 30 seconds--and during that time the status bar will show "Waiting for attack.samsclass.info", as shown below:
In the "PyLoris" window, click the Launch button. The attack starts, as shown below:
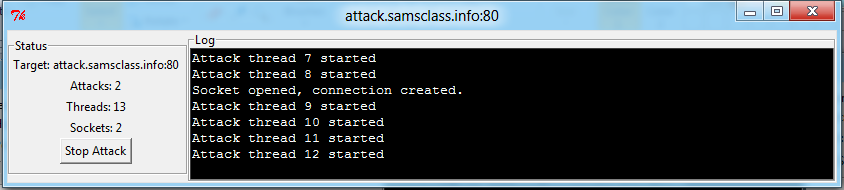
Wait for 30 seconds, until the sniffer stops running. Then click the "Stop Attack" button.
You should see at least two different source IP addresses sending packets, as shown below:
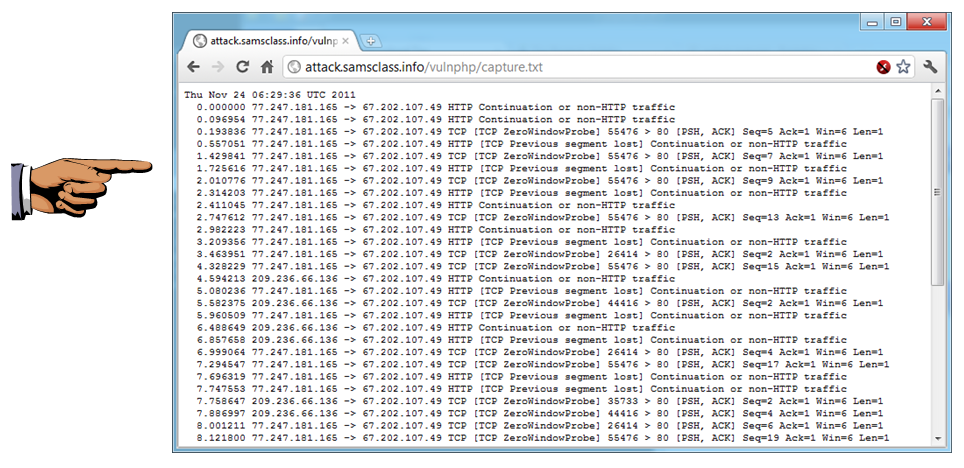
Save a screen capture with a filename of "Proj 5xa from YOUR NAME".
You see a message confirming that the address is a Tor exit router, as shown below:
Save a screen capture with a filename of "Proj 5xb from YOUR NAME".
Email the images to cnit.122sam@gmail.com with a subject of "Project 5x from YOUR NAME".
http://motomastyle.com/pyloris/
Thanks to @BreezySeas for telling me about PyLoris!
Last modified 11-23-11 10:30 pm