In your Kali64 machine, in a Terminal window, execute these commands:
cd /etc/snort
nano snort-test.conf
include /etc/snort/icmp-test.rules
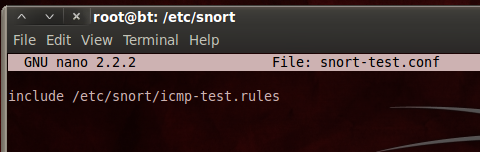
Save the file with Ctrl+X, Y, Enter.
In your Kali64 machine, in a Terminal window, execute this command:
nano icmp-test.rules
alert icmp any any -> any any (msg:"ICMP Packet"; sid:477; rev:3;)
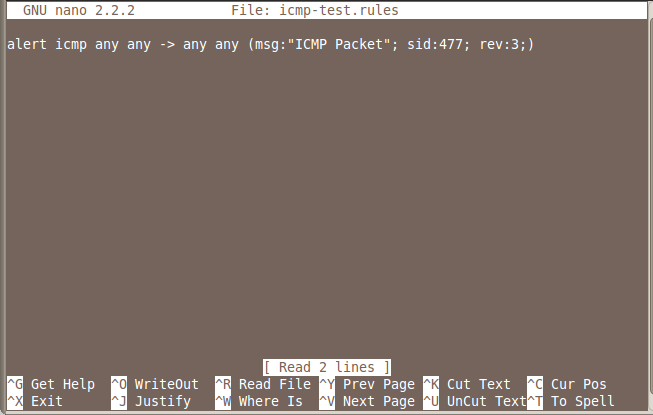
Save the file with Ctrl+X, Y, Enter.
This is the structure of an alert:
<Rule Actions> <Protocol> <Source IP Address> <Source Port> <Direction Operator> <Destination IP Address> <Destination > (rule options)
| Structure | Example |
|---|---|
| Rule Actions | alert |
| Protocol | icmp |
| Source IP Address | any |
| Source Port | any |
| Direction Operator | -> |
| Destination IP Address | any |
| Destination Port | any |
| (rule options) | (msg:”ICMP Packet”; sid:477; rev:3;) |
In your Kali64 machine, in a Terminal window, execute this command:
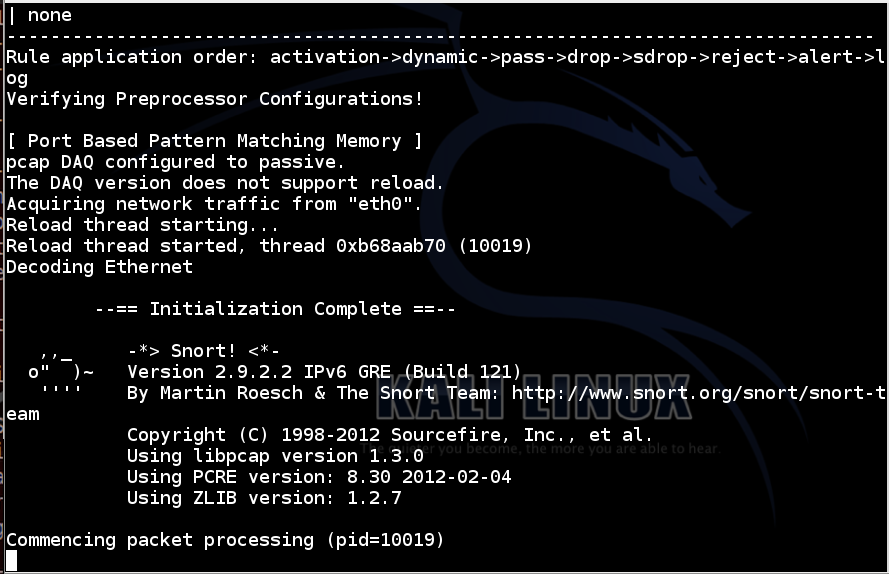
snort -i eth0 -c /etc/snort/snort-test.conf -l /var/log/snort
Your interface name may be different from eth0.
Snort starts, showing an "Initialization Complete" message, as shown below:

Click File, "Open Terminal" to open another Terminal window and execute this command:
ping -c 1 samsclass.info
cat /var/log/snort/alert
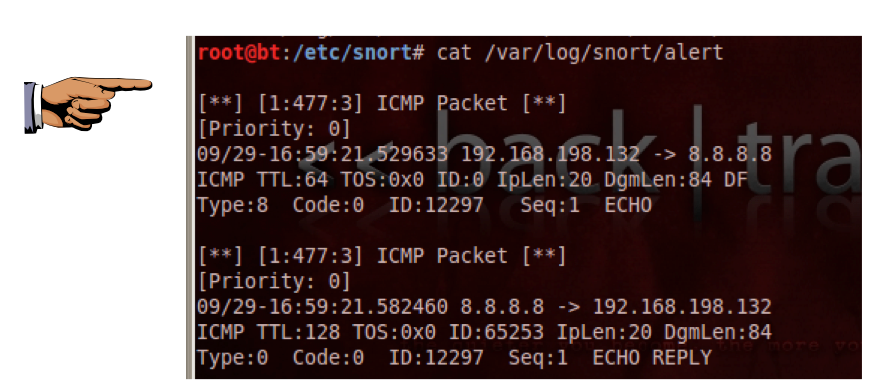
Snort prints out a page of statistics about the packets it saw, as shown below:
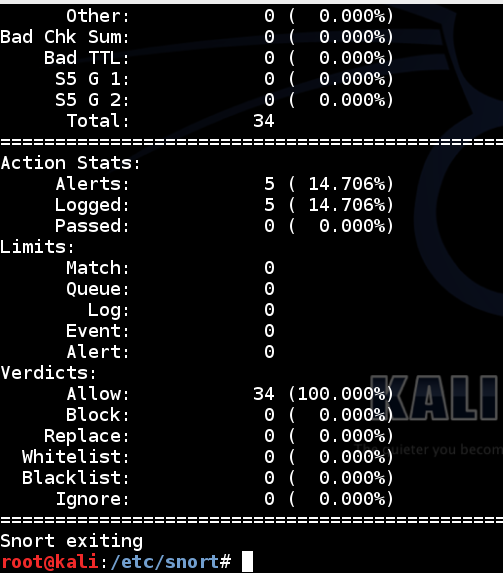
snort -i eth0 -l /var/log/snort -c /etc/snort/snort.conf
Snort starts, showing an "Commencing packet processing" message.
In the other Terminal window, execute this command:
tail -f /var/log/snort/alert
Open a Terminal window and execute this command, to run an Nmap scan of your Kali64 machine, as shown below.
nmap 172.16.1.202
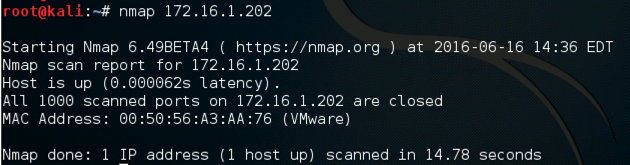
You should see messages scroll by on the Kali64 machine as snort sends alerts about the scans.
When the scan is complete, the Kali64 machine shows alerts, as shown below.
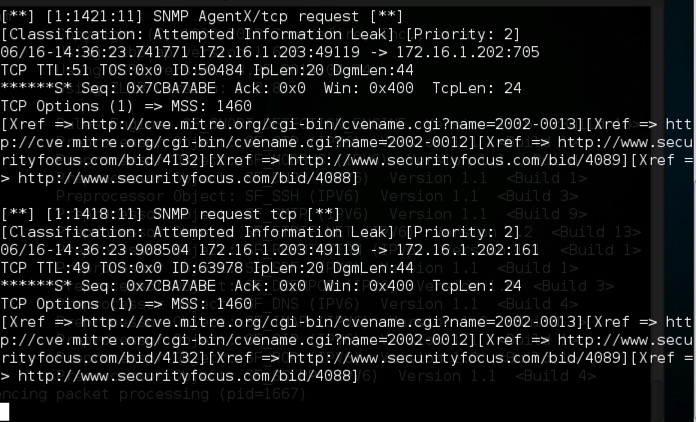
http://people.umass.edu/cs415/labs/lab2/415-lab2-Snort.pdf
Last modified 4-26-16
Modified 6-16-16 for NETLAB