It is claimed that Rekall has more operating system images, and the ability to analyze live memory, so it's useful for fast incident response.
I spent a few days figuring out how to use it, and I couldn't get it to do anything useful for quick IR. My goal is to quickly detect nasty things like reverse shells and rootkits that are controlling the machine right now, on Windows.
But I couldn't get anything useful accomplished with Rekall. If I am just using it incorrectly, I'd appreciate advice from anyone. I based my procedure on the References listed at the end of this page.
https://github.com/google/rekall/releases
cd \Program Files\Rekall
rekal --help
Execute this command:
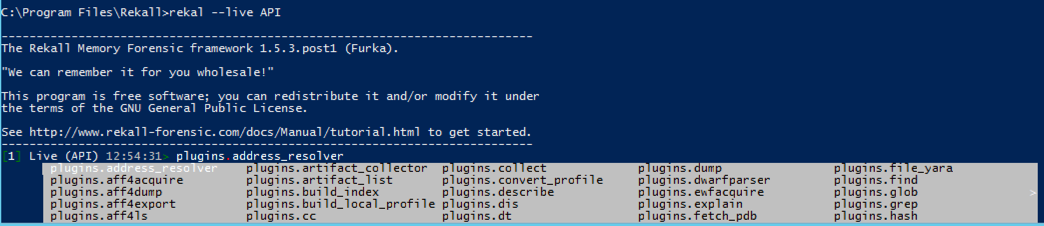
rekal --live API
To see the available modules, type this, and then hit the Tab key:
plugins.

You can Tab through the plugins and see all their names. To learn more about a plugin, type "plugins." followed by the plugin name and a question mark, like this. Press Enter to see more information, with the important portions colored dark red so you can't read them, as shown below.
plugins.address_resolver?
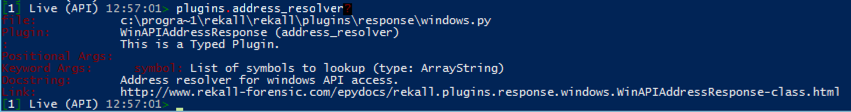
One plugin that works in API mode is "pslist", showing running processes as shown below.
However, since it's using the API, I don't see how it's better than just using Task Manager.
As far as I can tell, there are no plugins in API mode that show the network connections, so you're better off using normal Windows utilities like netstat and downloads like CurrPorts or TCPView.
The only problem is it doesn't work on any system I tried.
Here, for example, is a Windows 2012 R2 x64 server.
Execute this command:
rekal --live Memory
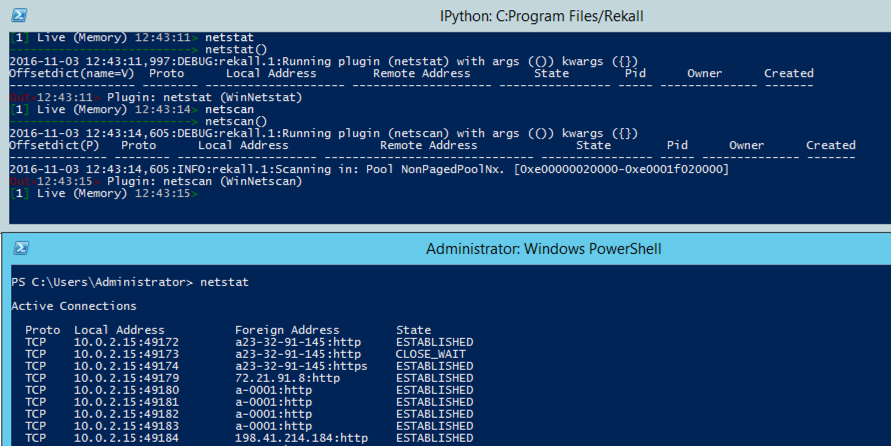
I tested all the Windows systems readily available to me. Rekall can't do a useful live memory analysis on any of them. I think this is because the online repositories don't have the necessary profiles, and Rekall can't find the required information from Microsft to construct them.
Perhaps Rekall works on Windows 7 or 8. I didn't test those.
Nothing works in Live Memory mode. "pslist" seems to run but finds nothing. "netstat" and "netscan" don't exist.Live API mode works.
Nothing works in Live Memory mode. When I attempt to execute "pslist", it attempts to download a profile from Microsoft, shows several "Error 403: Forbidden" messages, and crashes. Even Ctrl+C does nothing."netscan" does the same thing.
"netstat" runs around in an endless loop, downloading things from Microsoft that are only 2 bytes in size over and over.
Live API mode works.
In Live Memory mode, "pslist" works, but neither "netstat" nor "netscan" do.Live API mode works.
In Live Memory mode, "pslist" works, but neither "netstat" nor "netscan" do.Live API mode works.
Nothing works in Live Memory mode: "pslist", "netstat", and "netscan" all crash.Live API mode works.
The Rekall Profile Repository and Profile Auto-selection
YARA: Simple and Effective Way of Dissecting Malware
Triaging PowerShell Exploitation with Rekall