Unless you have a real attacker at that IP address, running this file won't do any harm. But it WILL set off antivirus software, which will prevent you completing the project.
So disable your antivirus, or use a virtual machine without any antivirus installed.
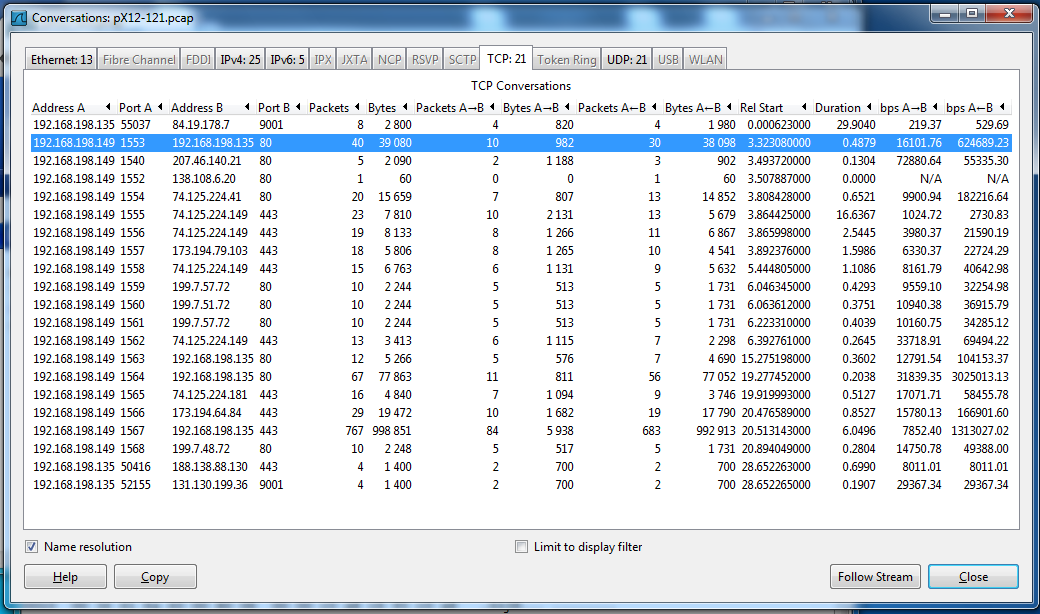
From the Wireshark menu bar, click Statistics, Conversations. In the "Conversations: pX12-121.pcap" window, click the TCP:21 tab. You see the 21 conversations in the capture, as shown below:

Click the second conversation, the one that exchanges 40 packets with 192.168.198.135 on port 80, as shown above. Click the Follow Stream button.
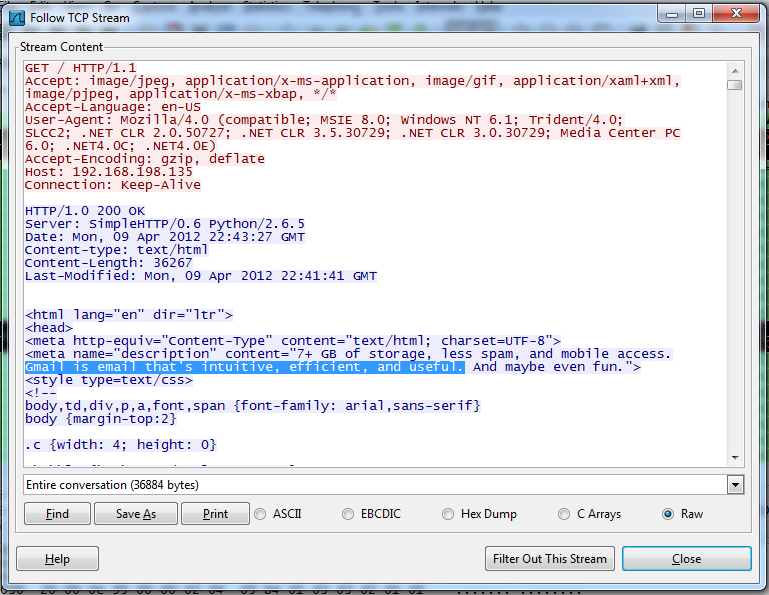
A "Follow TCP Stream" box pops up, as shown below. You can see the outgoing data in red--an HTTP GET request. The reply is in blue. This is a Gmail login page--you can see the description of the page highlighted in the image below.
You can already see that this looks suspicious--why is a Gmail login page coming from a private address like that, and not from Google?
In the "Follow TCP Stream" box, click the Close button.
Click the "Conversations: pX12-121.pcap" window to bring it to the front.
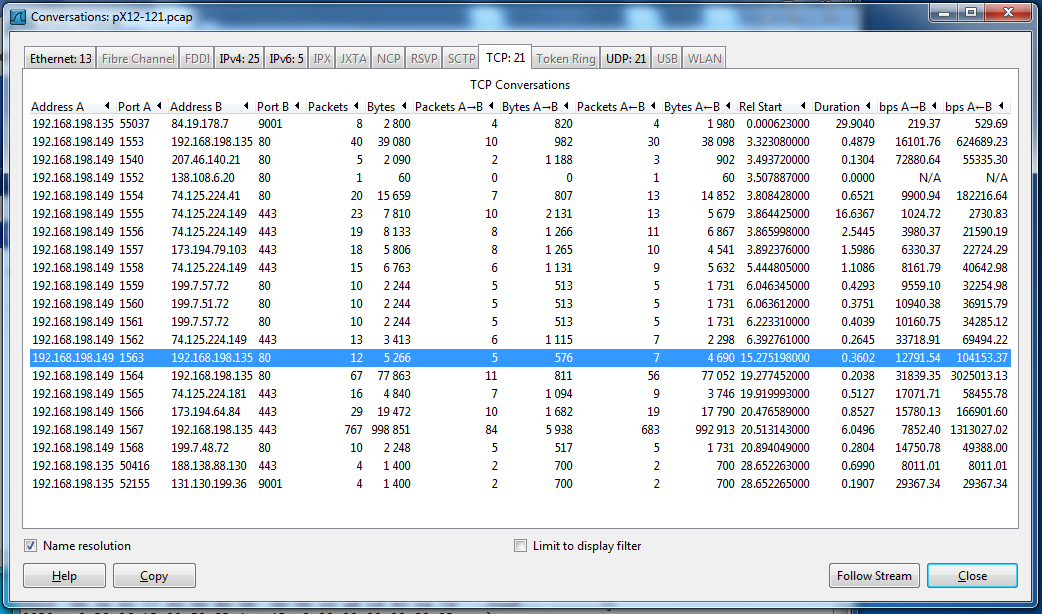
Click the conversation that exchanges 12 packets with 192.168.198.135 on port 80. It's near the end of the list, as shown below. Click the Follow Stream button.
The "Follow TCP Stream" box shows a request for a file named "Signed_update.jar", as highlighted in the image below.
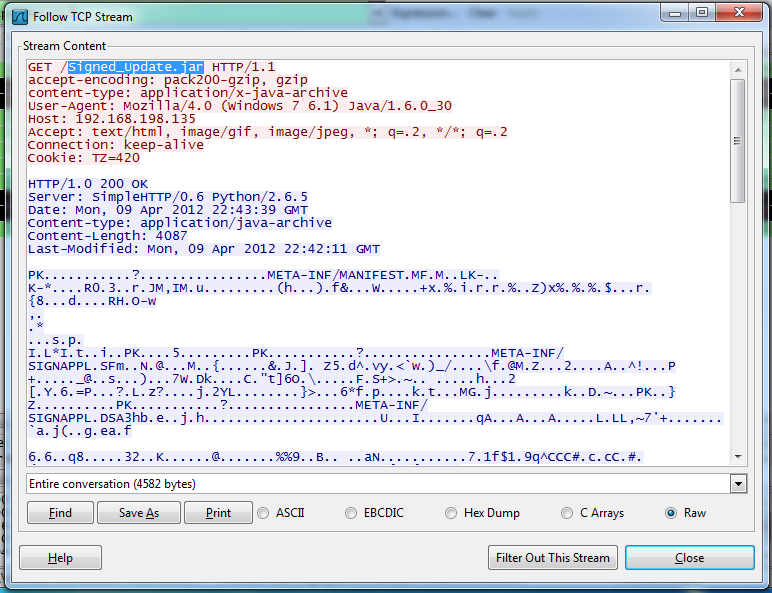
This is a Java archive. And the real Gmail page doesn't use Java. Also, if it is really a Java Update, it should be coming from Oracle, not from the same server that delivered the Gmail login page.
You can see the file contents in blue in the image above--it's a binary file so it's unreadable.
You can, however, save the file in its binary form.
In the "Follow TCP Stream" box, click the Save As button. Save the file on your desktop as "Java-malware.jar"
The file size should be exactly 4,582 bytes, as shown below:
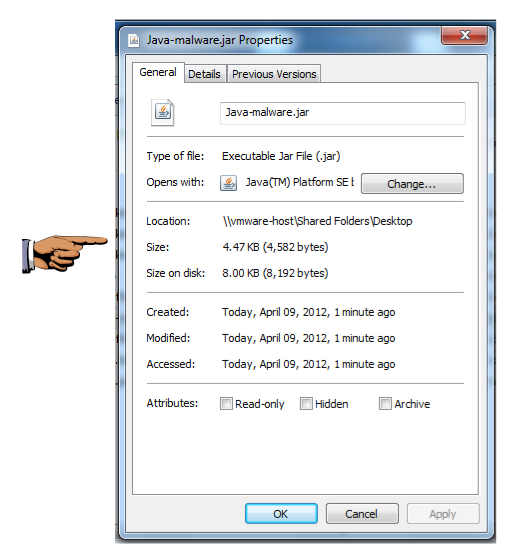
Make sure the file size of 4,582 bytes is visible.
Save this image with the filename Proj X12a from YOUR NAME
In the "Follow TCP Stream" box, click the Close button.
Click the "Conversations: pX12-121.pcap" window to bring it to the front.
Click the conversation that exchanges 67 packets with 192.168.198.135 on port 80. It's near the end of the list, as shown below.
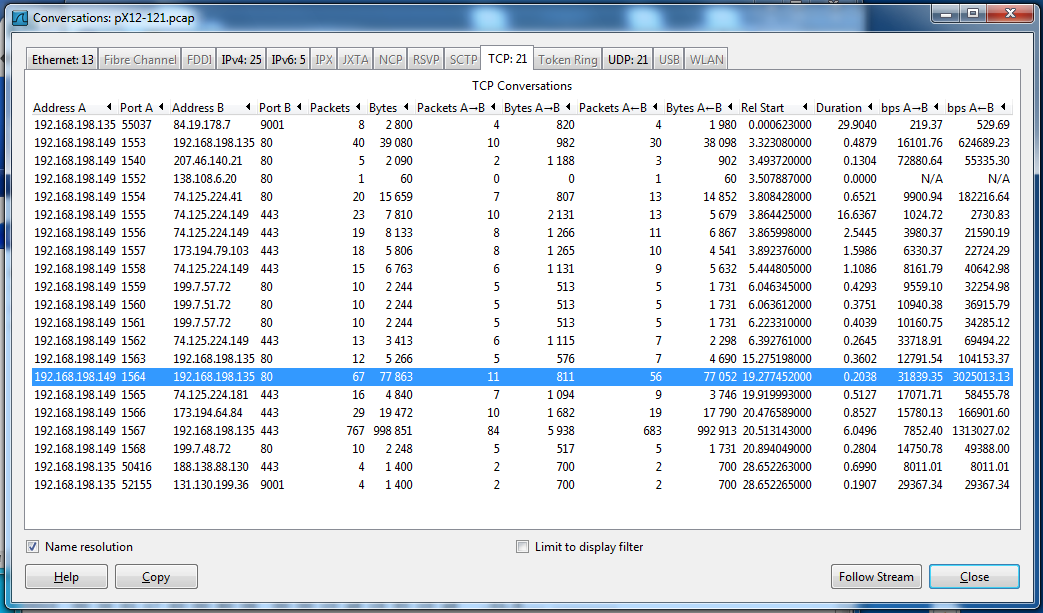
Click the Follow Stream button.
This conversation requests a file named "77S1wJh" -- it's not obvious what it is. But the blue response shows a clue--the text "This program cannot be run on DOS mode" is readable, as highlighted in the image below.
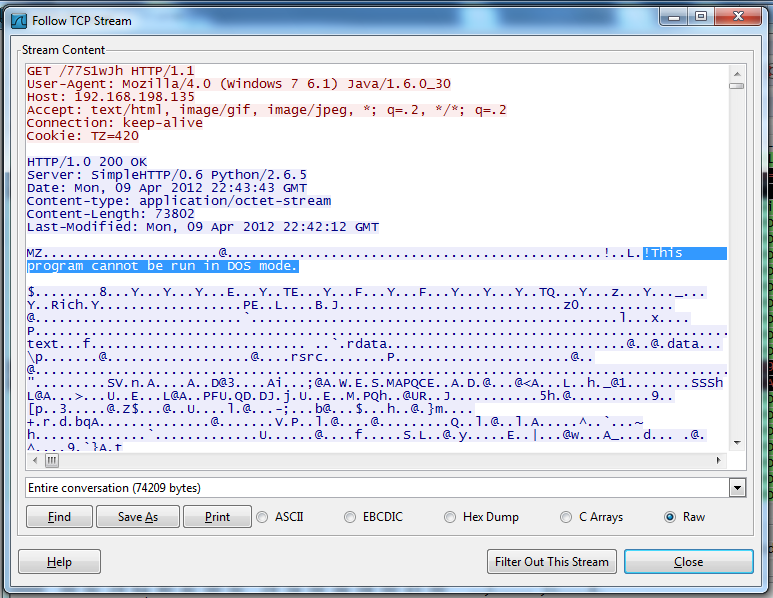
This is a Windows executable file.
In the "Follow TCP Stream" box, click the Save As button. Save the file on your desktop as "malware.exe"
The file size should be exactly 74,209 bytes, as shown below:
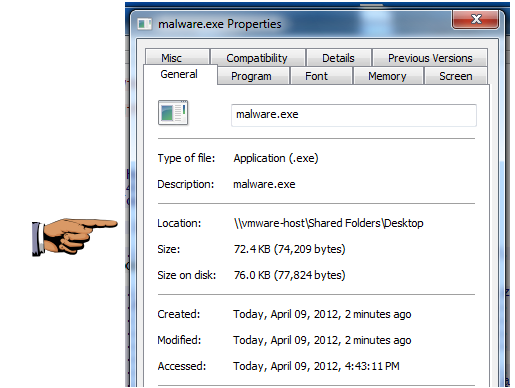
Make sure the file size of 74,209 bytes is visible.
Save this image with the filename Proj X12b from YOUR NAME
In the "Follow TCP Stream" box, click the Close button.
Click the "Conversations: pX12-121.pcap" window to bring it to the front.
Click the conversation that exchanges 767 packets with 192.168.198.135 on port 443. It's near the end of the list, as shown below.
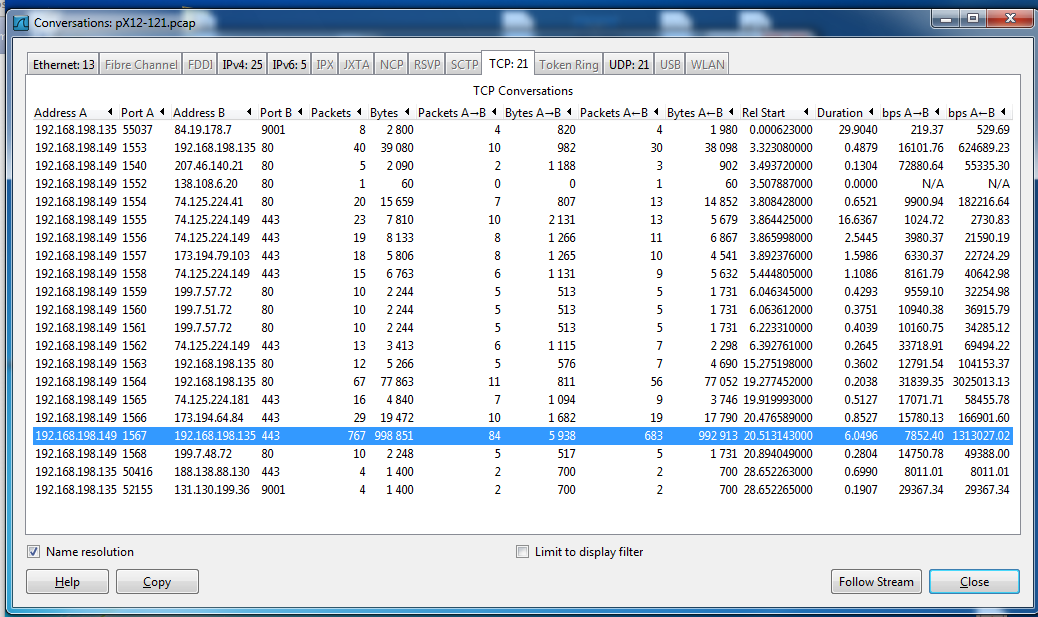
Click the Follow Stream button.
The target machine was under hostile control by this time, so it was sent a file without needing to send an HTTP request first.
And, as you can see below, even though this traffic is coming in from port 443, it is not encrypted--you can read the usual message that indicates a Windows executable file, as shown below:
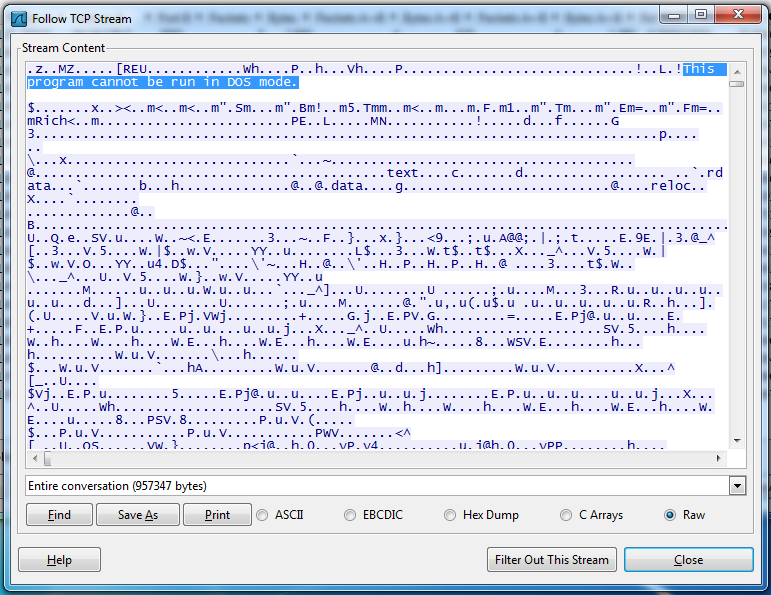
In the "Follow TCP Stream" box, click the Save As button. Save the file on your desktop as "malware2.exe"
The file size should be exactly 957,347 bytes, as shown below:
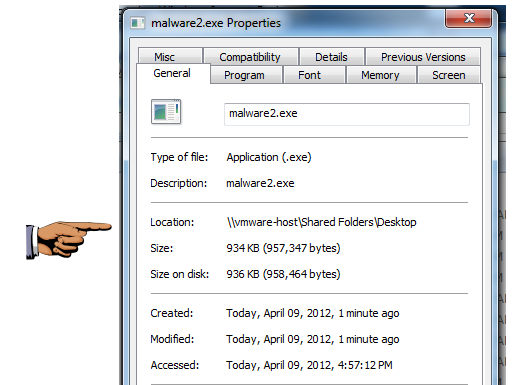
Make sure the file size of 957,347 bytes is visible.
Save this image with the filename Proj X12c from YOUR NAME