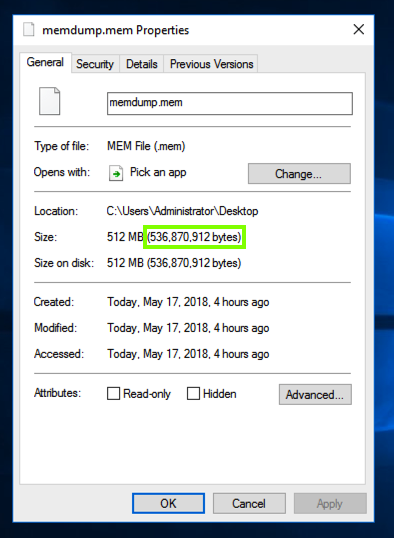
Find the memdump.mem file on your Windows server's desktop. Right-click it and click Properties. Make a note of its exact size in bytes, as shown in the image below.

Drag it out of the virtual machine and drop it on the host machine's desktop.
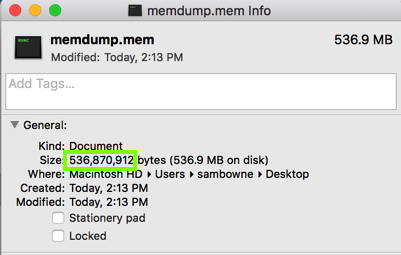
When the copy finishes, check the size of the file on your host system. It should match, as shown below. (This image is from a Mac host.)
Close the Windows virtual machine.
Launch your Kali Linux machine. If necessary, log in as root with the password toor
Drag the memdump.mem file from your Windows 7 host machine's desktop and drop it on your Kali Linux desktop.
Note: the VMware Tools copy process is buggy and sometimes fails to copy the entire file.
You may see an error message and have to click "Retry".
When the copy finishes, on your Kali desktop, right-click the memdump.mem file and click Properties, as shown below.
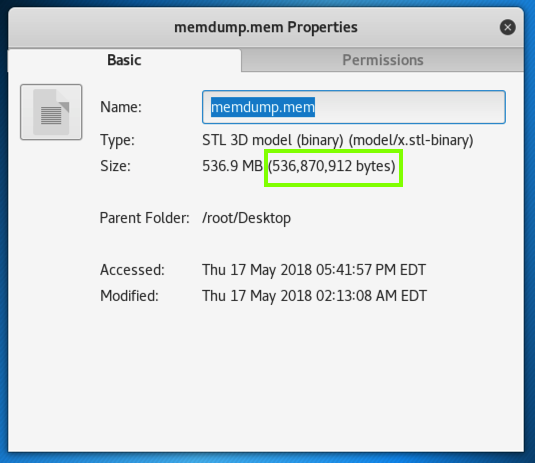
The size should match the size of the original file, as shown below.
cd
cd Desktop
ls -l
You should see the memdump.mem file as shown below.
In your Kali Linux machine, in the Terminal window, execute this command:
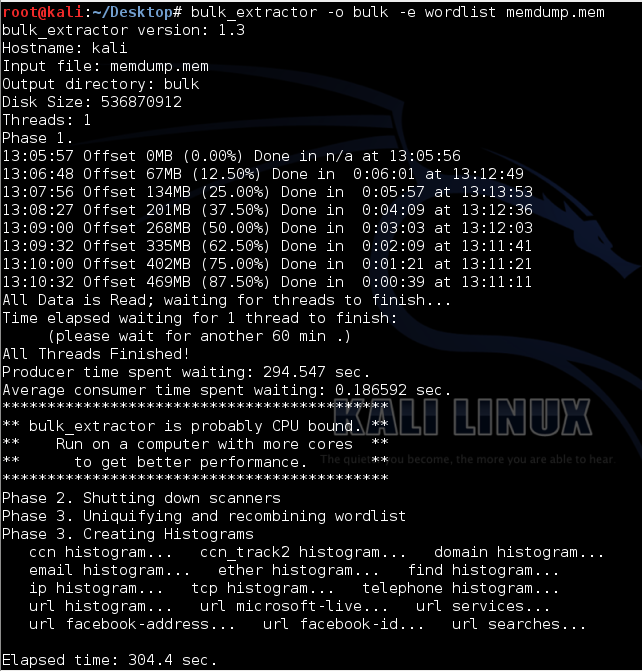
bulk_extractor -o bulk -e wordlist memdump.mem
To fix it, replace "-o bulk" with "-o bulk2".
This tells Bulk Extractor to gather data from the memdump file, put the results in a folder named "bulk", and compile a wordlist of all readable strings.
Bulk Extractor will take several minutes to run and output progress messages, as shown below:
cd bulk
ls -l
nano domain_histogram.txt
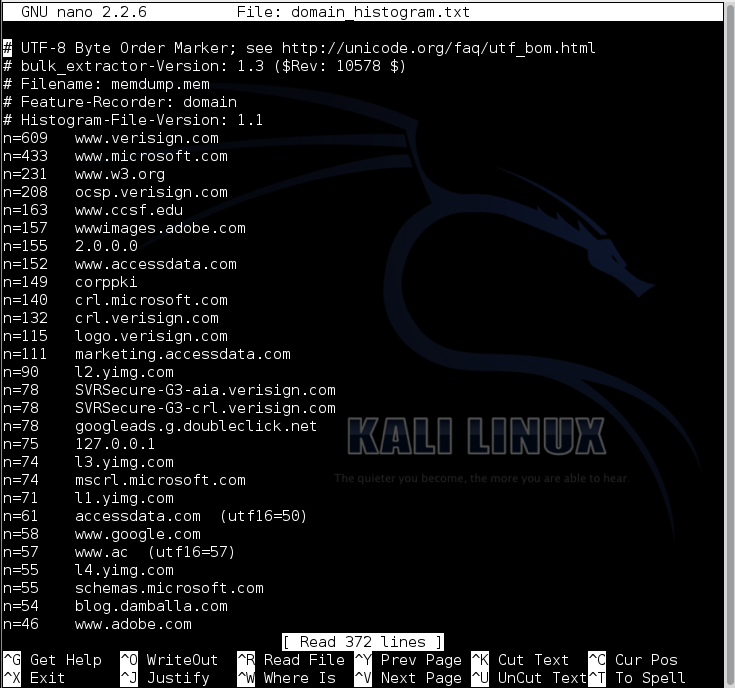
Press Ctrl+W, enter the search term ccsf, and press Enter.
ccsf.edu is found, as shown below:
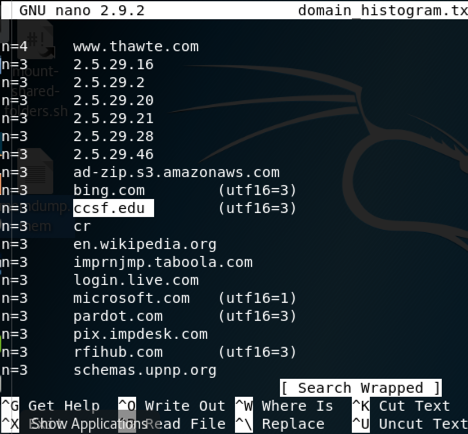
Press Ctrl+X to close nano.
nano ccn_histogram.txt
nano wordlist.txt
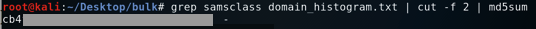
grep samsclass domain_histogram.txt | head -n 1 | cut -f 2 | md5sum
Use the form below to put your name on the WINNERS PAGE.
The file is 151,799,629 bytes in size, and its MD5 hash is aa1095f89a2992adeb6b5d2bb519e1ee.
That memory dump contains an email address ending in "@wazuh.com". Find it and use the form below to put your name on the WINNERS PAGE.
The file is 130,398,701 bytes in size, and its MD5 hash is 364fed484bcdd1a1f81a3538a4b1cd9a.
To unzip a .7z file in Kali, use "7z x filename"
That memory dump contains a credit card number beginning with 3728. Find it and use the form below to put your name on the WINNERS PAGE.