27bslash6.com
Press Enter to open the page.
Note: Make sure you type in the URL directly, and do not use a search engine to find the page.
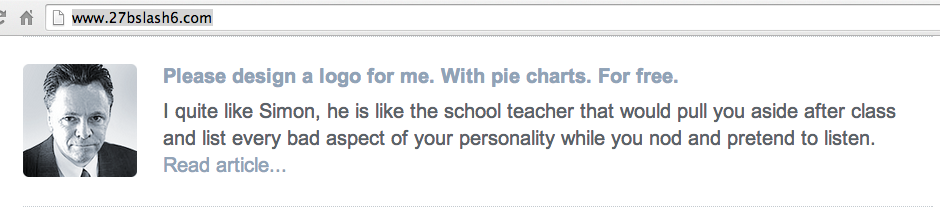
Scroll down and find the "Please design a logo for me" story, as shown below:

Right-click on the photo of the man there and click "Save picture as...""
Save the picture on your desktop with its default filename, which is "photo_simon_graphs".
Close Internet Explorer.
On your Desktop, double-click photo_simon_graphs.
The photo opens in your default image viewer. When I did it, it opened in Internet Explorer.
Close the viewer window.
If a "User Account Control" box pops up, click Yes.
In Registry Editor, navigate to this key:
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TypedURLs
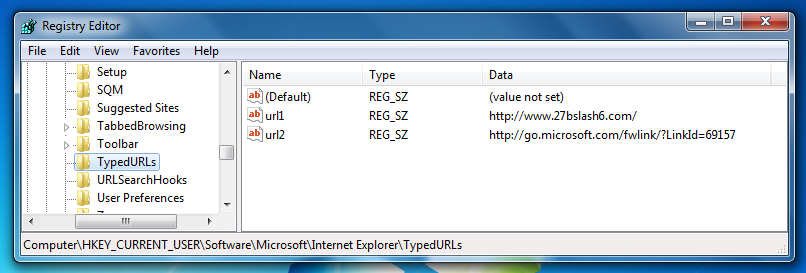
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist
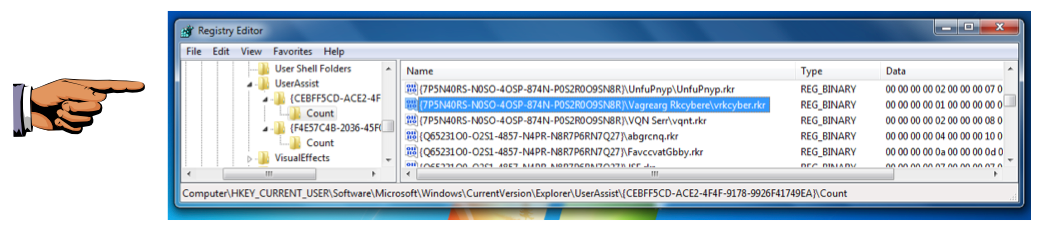
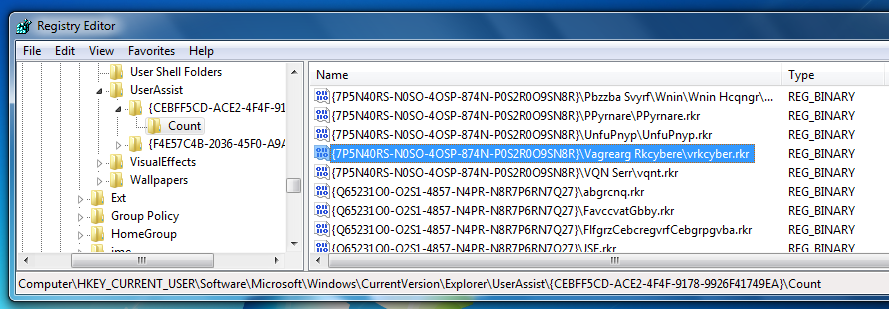
Hunt through the entries in the right pane, until you find a Name ending in vrkcyber.rkr
Highlight that name, as shown below.
"vrkcyber.rkr" is the ROT-13 obfuscated text "iexplore.exe", as you can verify at
This registry value is another artifact showing that you opened Internet Explorer.
Click on the host system's taskbar, at the bottom of the screen.
Press the PrntScrn key to capture the whole desktop. Open Paint and paste in the image.
Save the image as "Proj 18a from YOUR NAME".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Instead of waiting a week, we'll create a restore point manually.
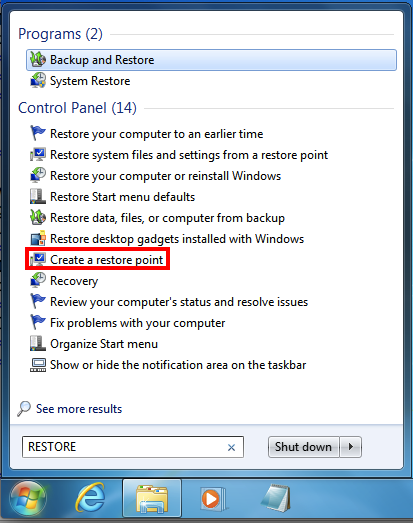
Click Start. In the Search box, type RESTORE
In the search results, click "Create a restore point", as shown below.
A "System Properties" box pops up. Click Create.
In the "System Protection" box, type a name of
YOURNAME Before CCleaner
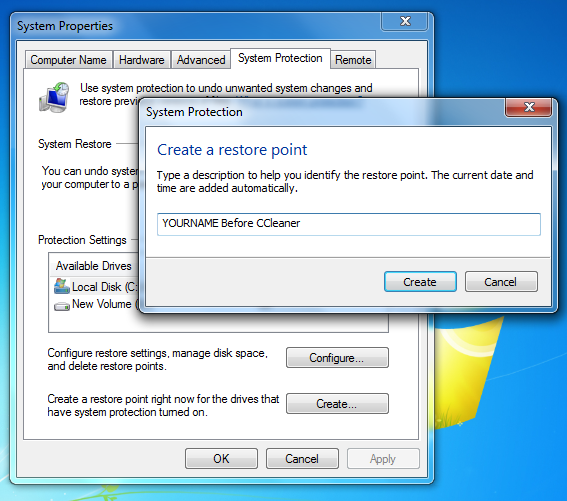
Note the time when you made your restore point. You'll need it later.
In the "System Protection" box, click Create.
A box pops up saying "The restore point was created successfully".
Click Close.
In the "System Properties" box, click OK.
http://www.piriform.com/ccleaner
Click the green Download button.
Scroll down and click the leftmost green Download button to get the free version.
Run the installer. Install the software.
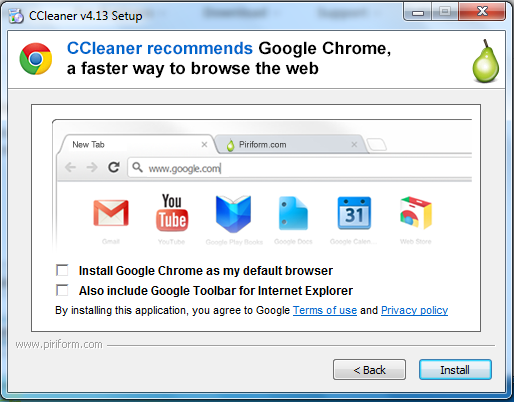
When you see the screen below, Google will attempt to install spyware on your machine. I recommend clearing both check boxes, although it doesn't really matter for this project. It's worth noticing, however, how far Google has moved from their old motto "Do No Evil", which they abandoned when they incorporated.
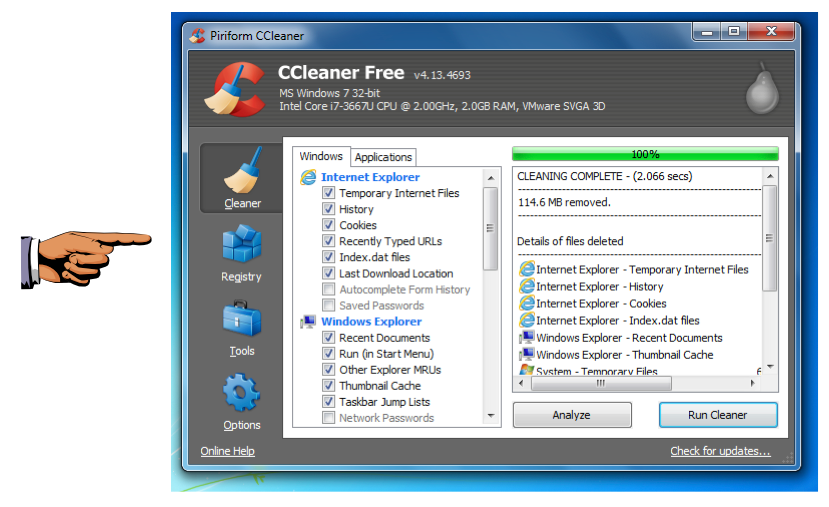
Click the "Run Cleaner" button.
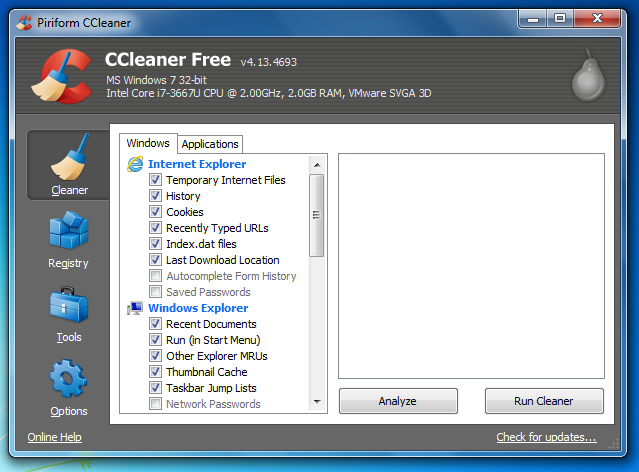
A box pops up saying "This process will permanently delete files from your system", as shown below.
That is a very interesting claim, and we shall see to what extent it is true. CCleaner does delete some files, but it doesn't get all the evidence left behind.
In the box, click OK.
In a few seconds, CCleaner says "CLEANING COMPLETE", as shown below.
Click on the host system's taskbar, at the bottom of the screen.
Press the PrntScrn key to capture the whole desktop. Open Paint and paste in the image.
Save the image as "Proj 18b from YOUR NAME".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
If a "User Account Control" box pops up, click Yes.
In Registry Editor, navigate to this key:
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TypedURLs

HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist
Hunt through the entries in the right pane, until you find a Name ending in vrkcyber.rkr as shown below. CCleaner did not erase it!
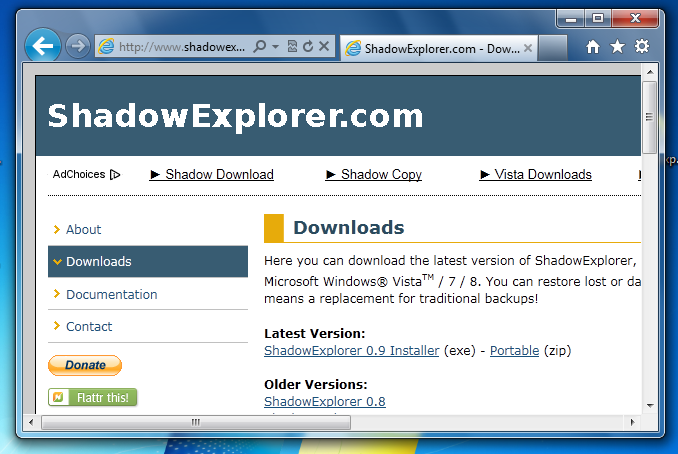
http://www.shadowexplorer.com/downloads.html
In the "Downloads" section, under the "Latest Version:" heading, click "ShadowExplorer0.9 Installer (exe)", as shown below:
Install the software with the default options.
At the top left, select C: and the time at which you made your restore point, as shown below.
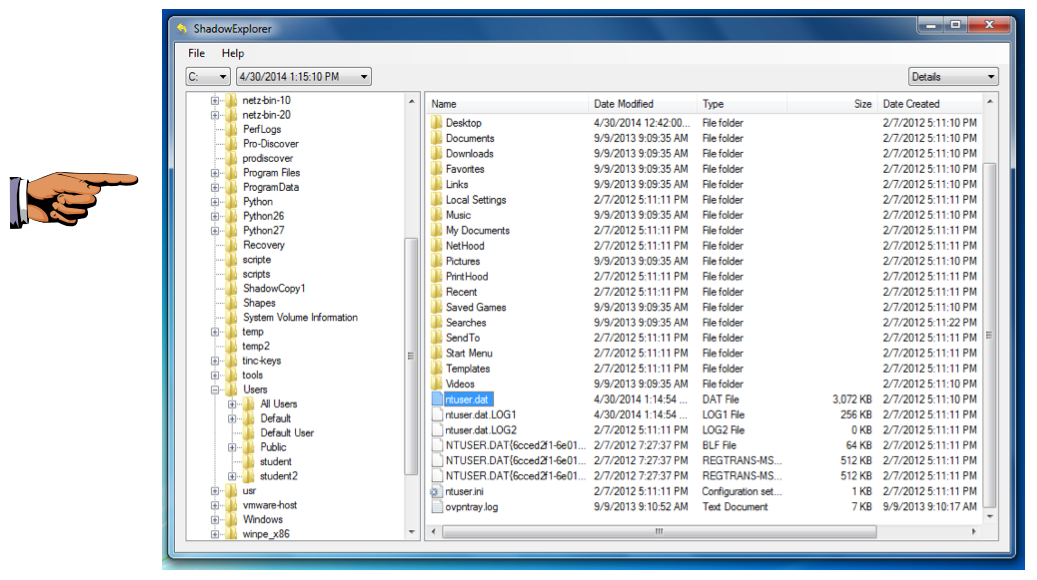
Navigate to your profile folder, which is like this, replacing "student" with your username:
C:\Users\student
Click on the host system's taskbar, at the bottom of the screen.
Press the PrntScrn key to capture the whole desktop. Open Paint and paste in the image.
Save the image as "Proj 18c from YOUR NAME".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT
Click Desktop, and click OK.
The file is placed on your desktop, but it is probably invisible because it's a hidden system file.
Open a Web browser and go toOn the upper right of the page, point to SUPPORT. Click "Product Downloads".
In the "Current Releases" section, expand the "Registry Viewer" section. On the "Registry Viewer 1.7.4" line, click Download.
Download and install the software with the default options.
In Registry Viewer, click File, Open.
Navigate to your desktop.
The Ntuser.dat file is not visible. However, just type its name into the Filename box anyway, as shown below:
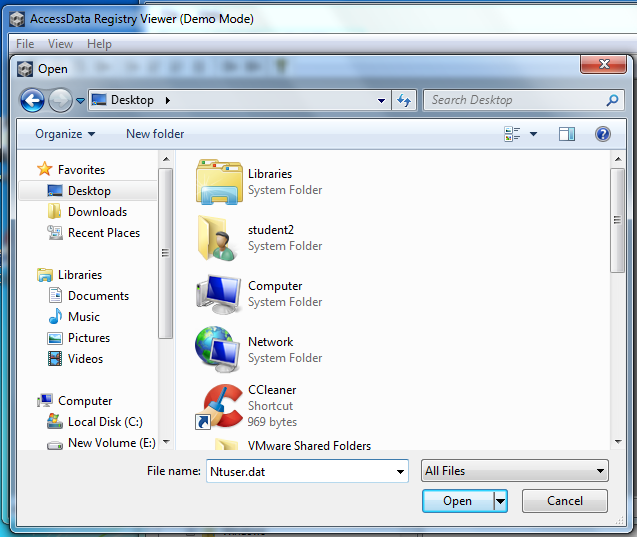
In the Open box, click Open.
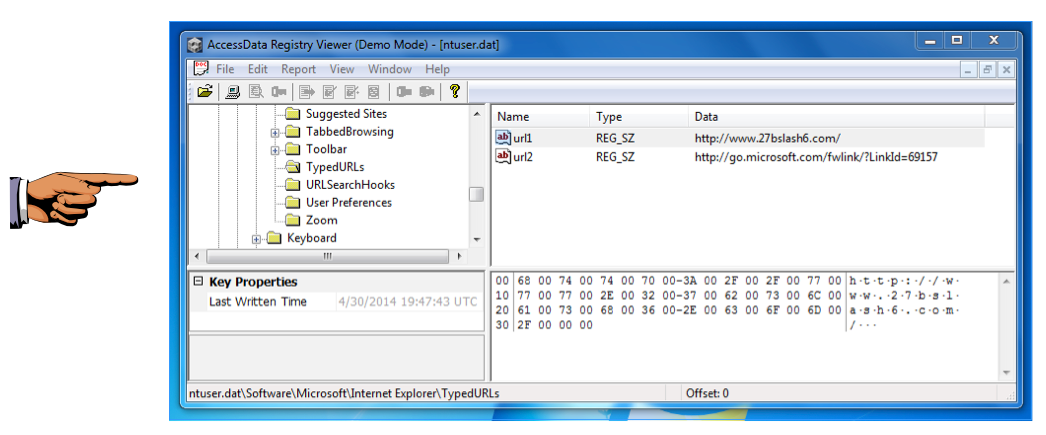
ntuser.dat\Software\Microsoft\Internet Explorer\TypedURLs
Find the url http://www.27bslash6.com/ and highlight it, as shown below:
Click on the host system's taskbar, at the bottom of the screen.
Press the PrntScrn key to capture the whole desktop. Open Paint and paste in the image.
Save the image as "Proj 18d from YOUR NAME".
YOU MUST SEND IN A WHOLE-DESKTOP IMAGE FOR FULL CREDIT