ProDiscover Notes Day 1
Types of Tools
In forensics, there are four processes:
- Data acquisition
- Data preservation
- Analysis
- Presentation
There are Tier 1 tools, which give you
all four processes, and Tier 2 tools which
do only specialized things.
ProDiscover, EnCase, and FTK are Tier 1 Tools.
Versions
There are three versions of ProDiscover.
The free version has no restrictions--it can
even be used in court. But it lacks advanced
features like indexed searches.
The Forensic version
has more features, and the
Incident Response version can
do everything the Forensic version does,
plus network acquisitions.
The Forensics
version costs $2500/yr. for 21 stations in a
school, but you can't use that academic version in
court.
If you want to use it in court, it cost
approximately $2500 for one machine for
the Forensic version, and $9000 for the
Incident Response version.
Host Protected Area
ProDiscover is the only product that can access the
Host Protected Area of a hard disk. At first, the
developer wanted to patent this feature, but he has
abandoned that idea because only one known case so far actually
involved data hidden there. Although it is a good place to
hide things, it never became popular, and now encryption
offers a much simpler way to hide data. So this feature
is essentially obsolete. It will be removed from the product
within the next two years, because it's not worth the
development effort to update it for Windows 7.
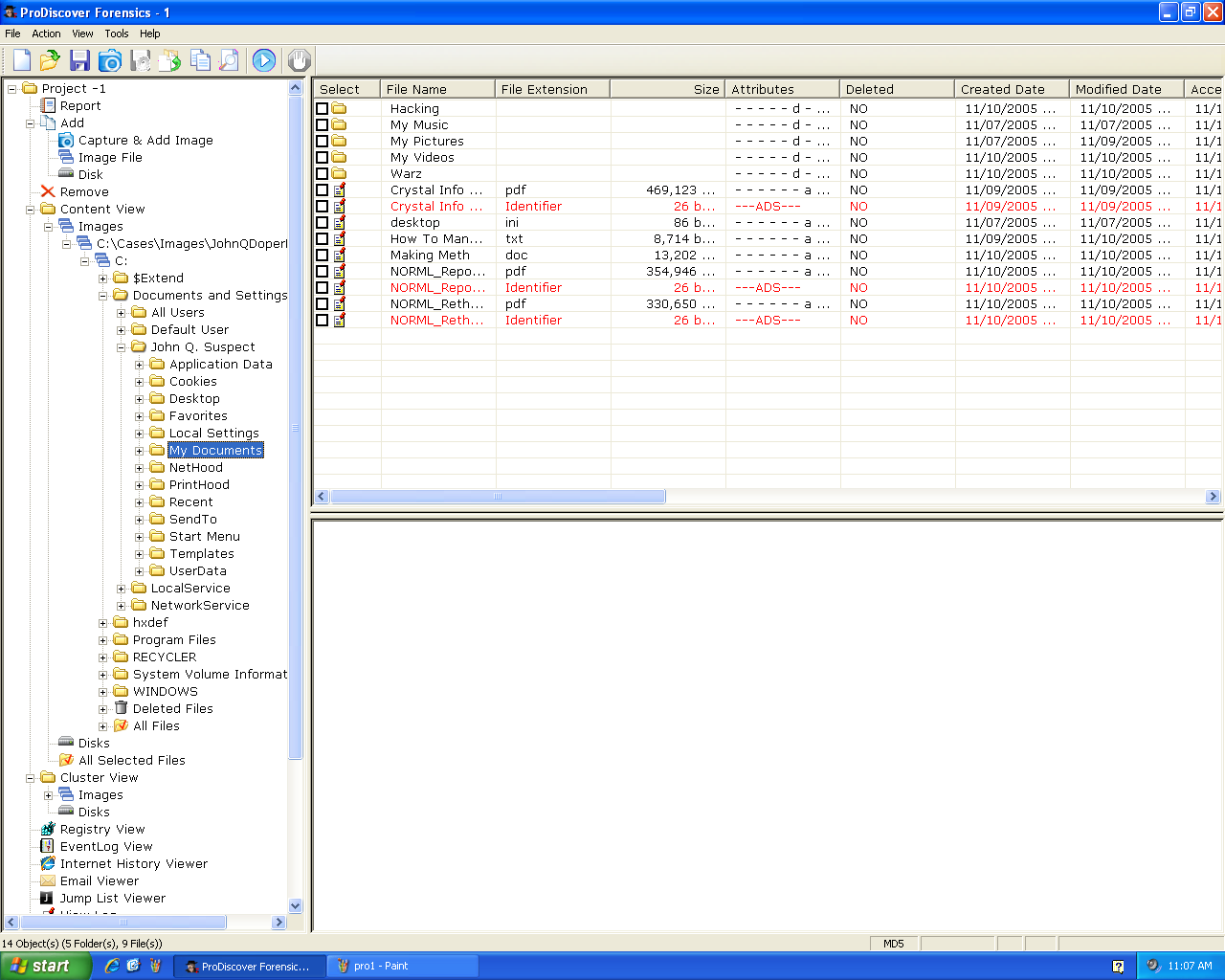
A Sample Case
Here's ProDiscover opening one of the sample cases.
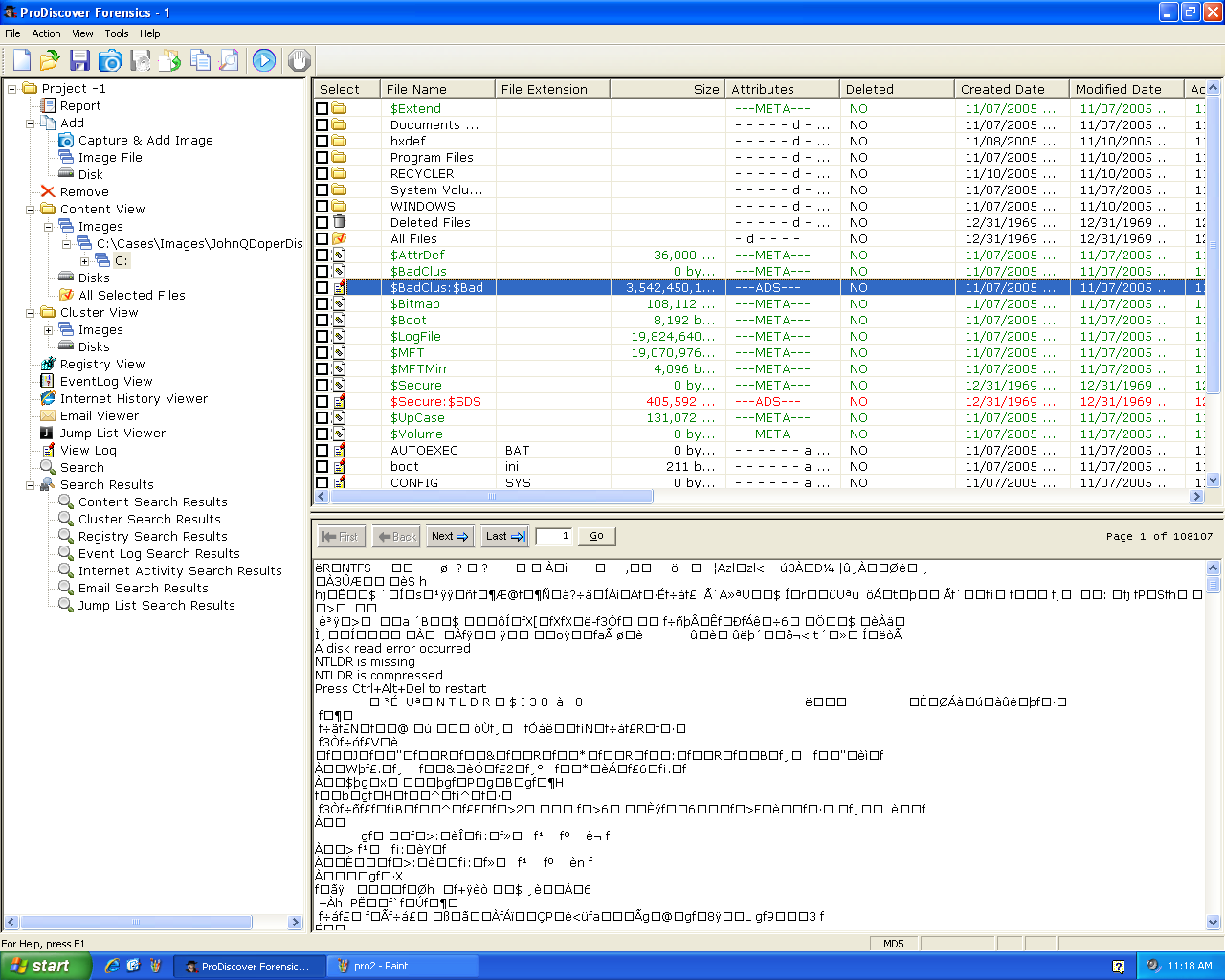
Here's a Bad Cluster
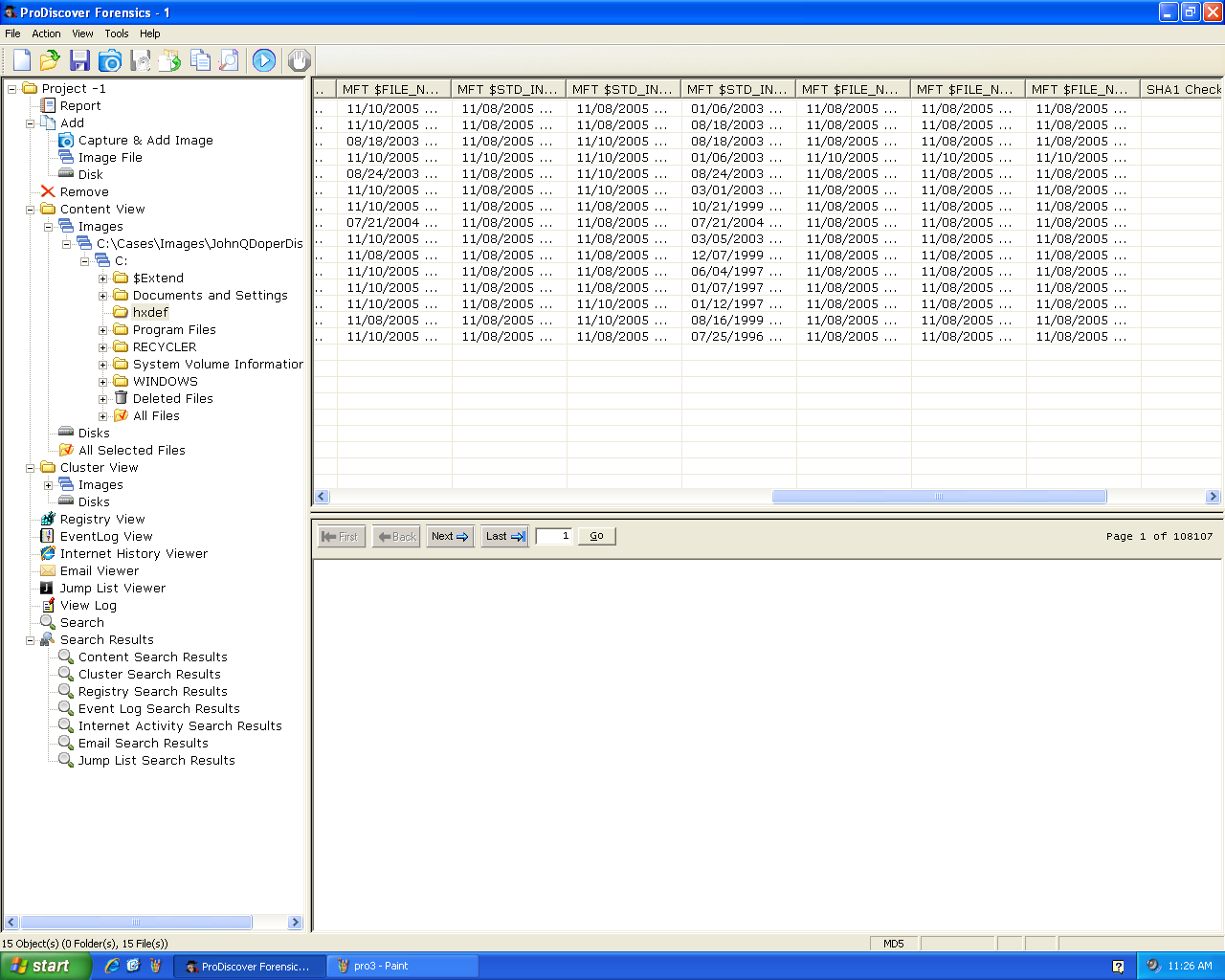
Timestamps
ProDiscover shows a lot of timestamps beyond the
usual ones. These are explained in
Brian Carrier's book
Cluster View
Cluster View shows the raw clusters on disk.
You can right-click a cluster and see the file
that contains it.
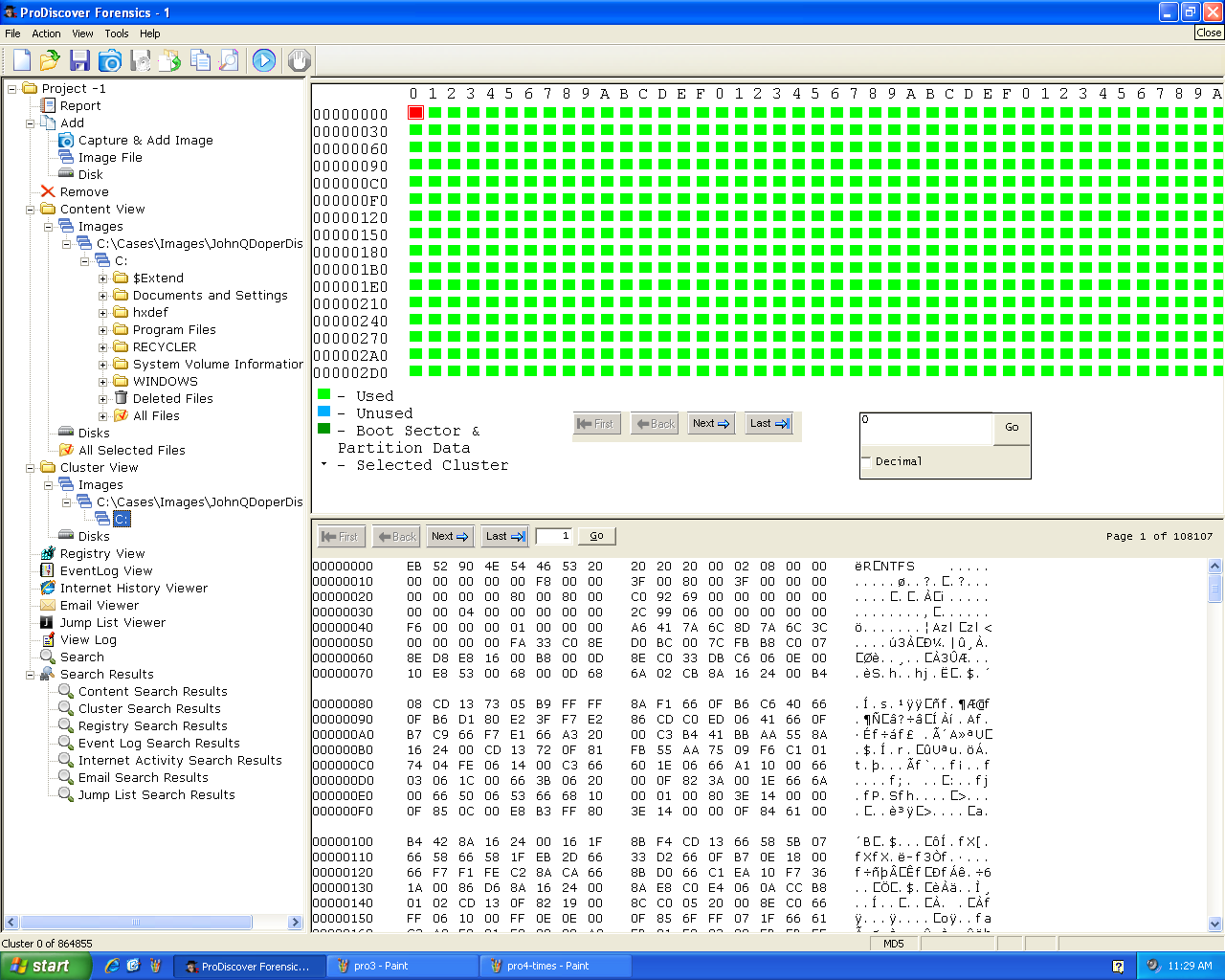
Report
Check a file to include it in the Report.
It will prompt you for a comment.
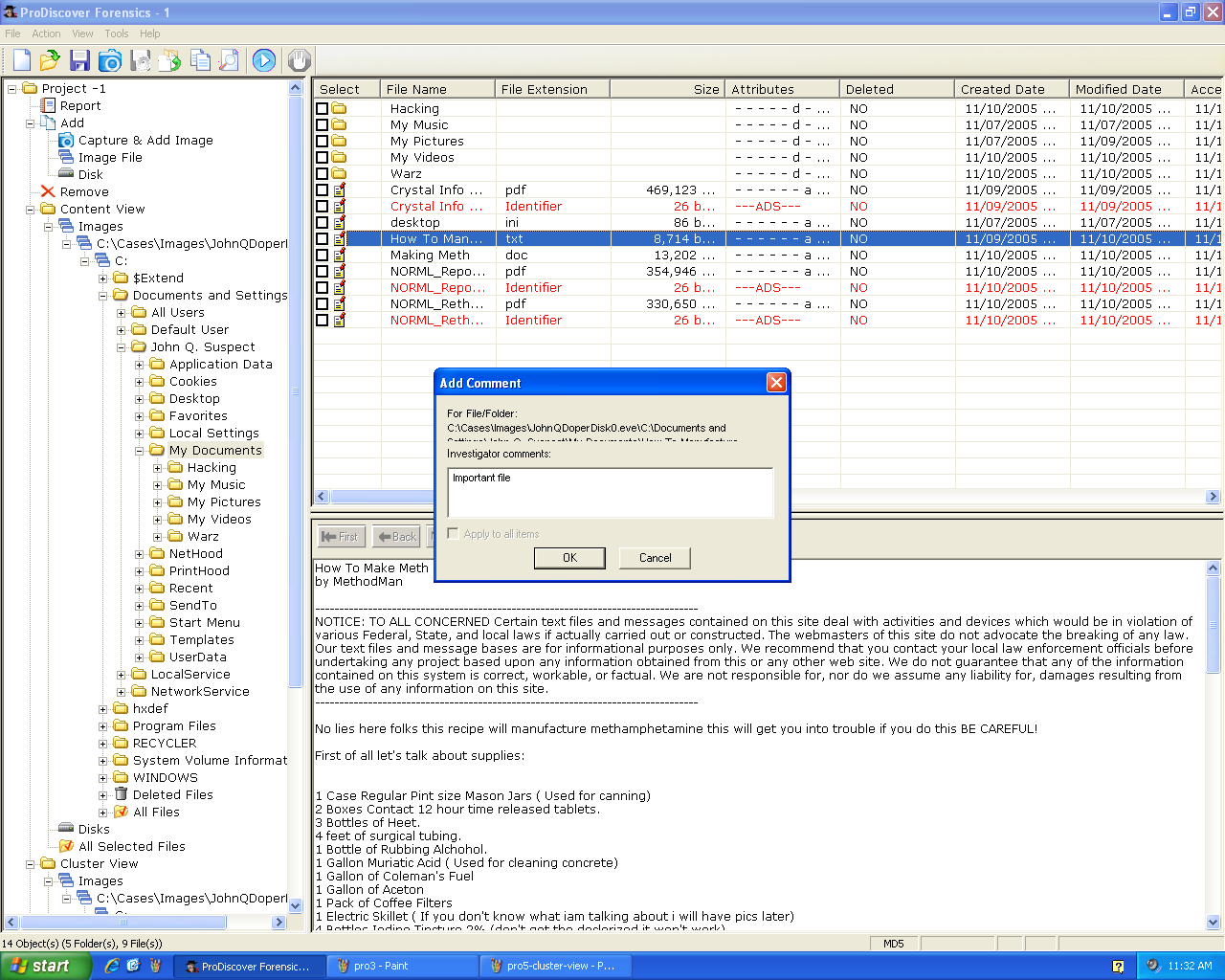
Here's the Report:
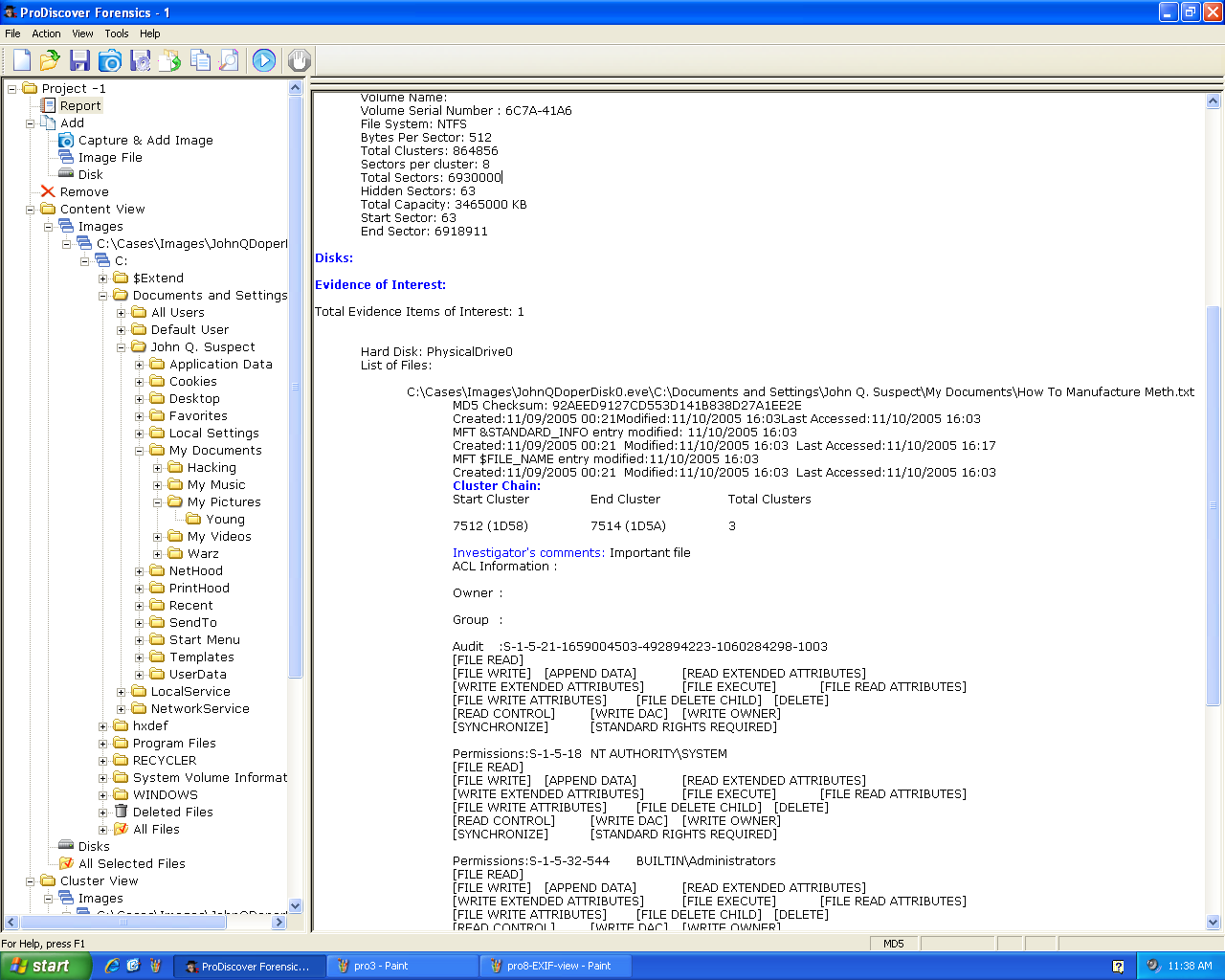
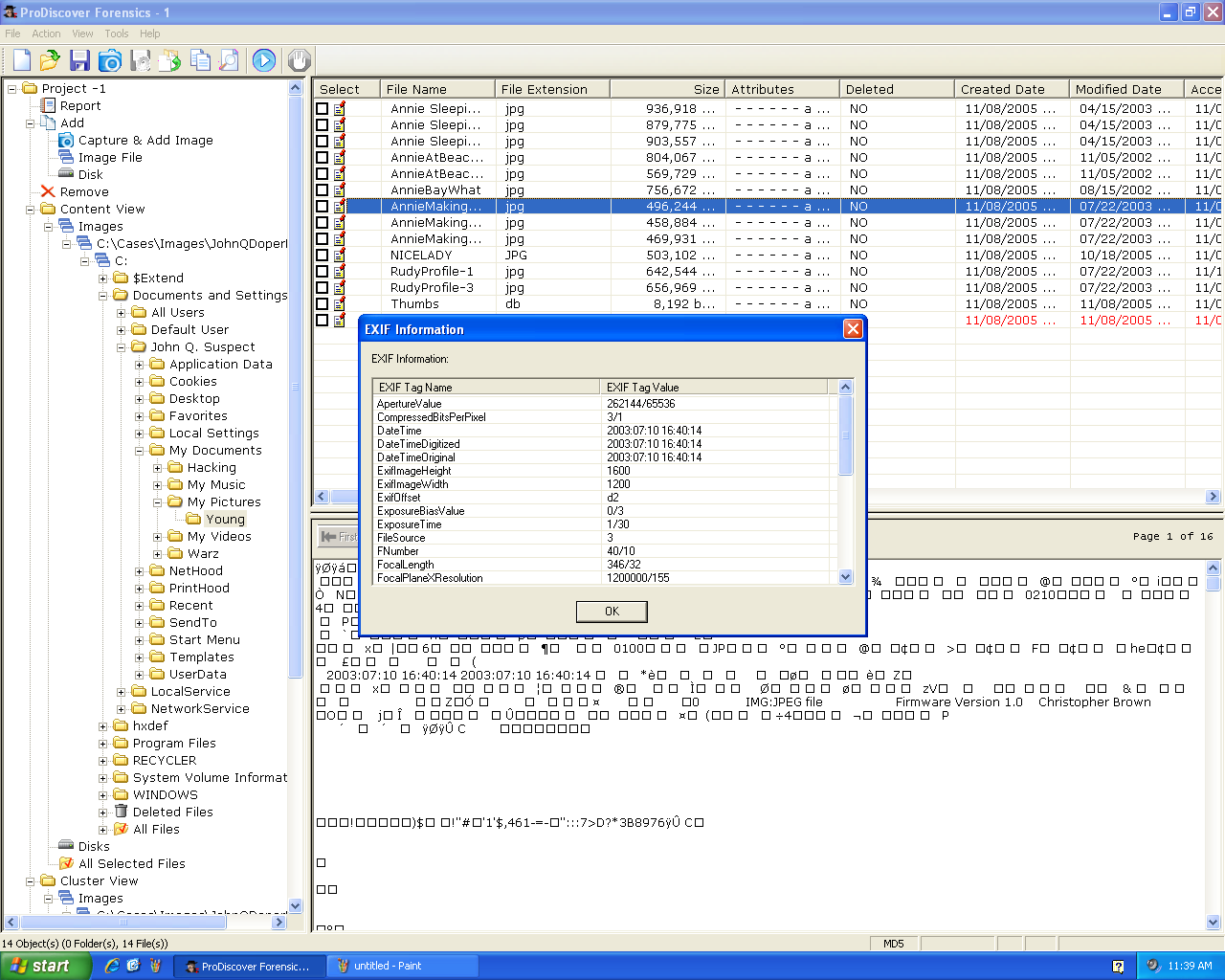
EXIF Data
Right-click an image and click
"View EXIF Data" to see the EXIF
metadata:
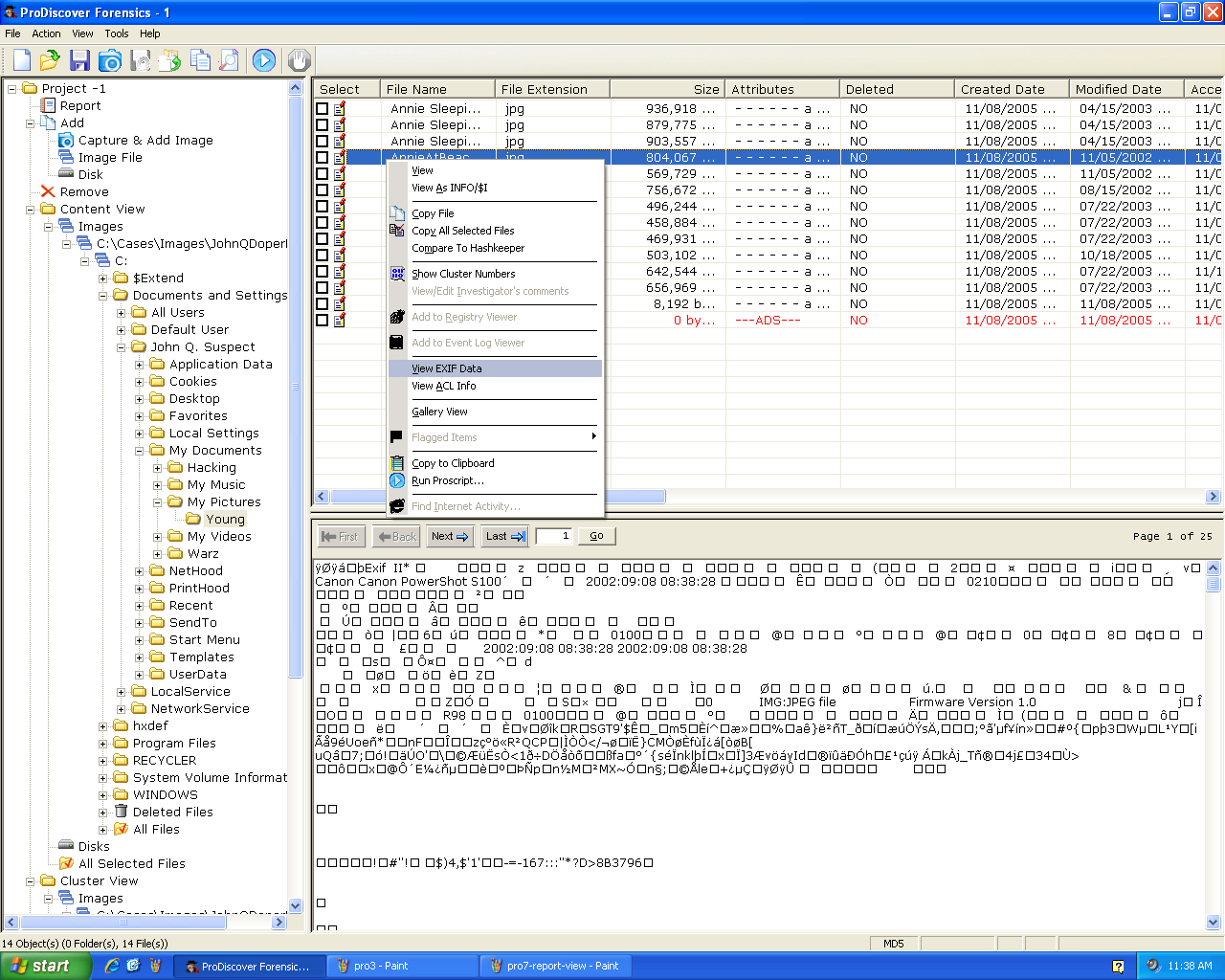
Here's the EXIF data:
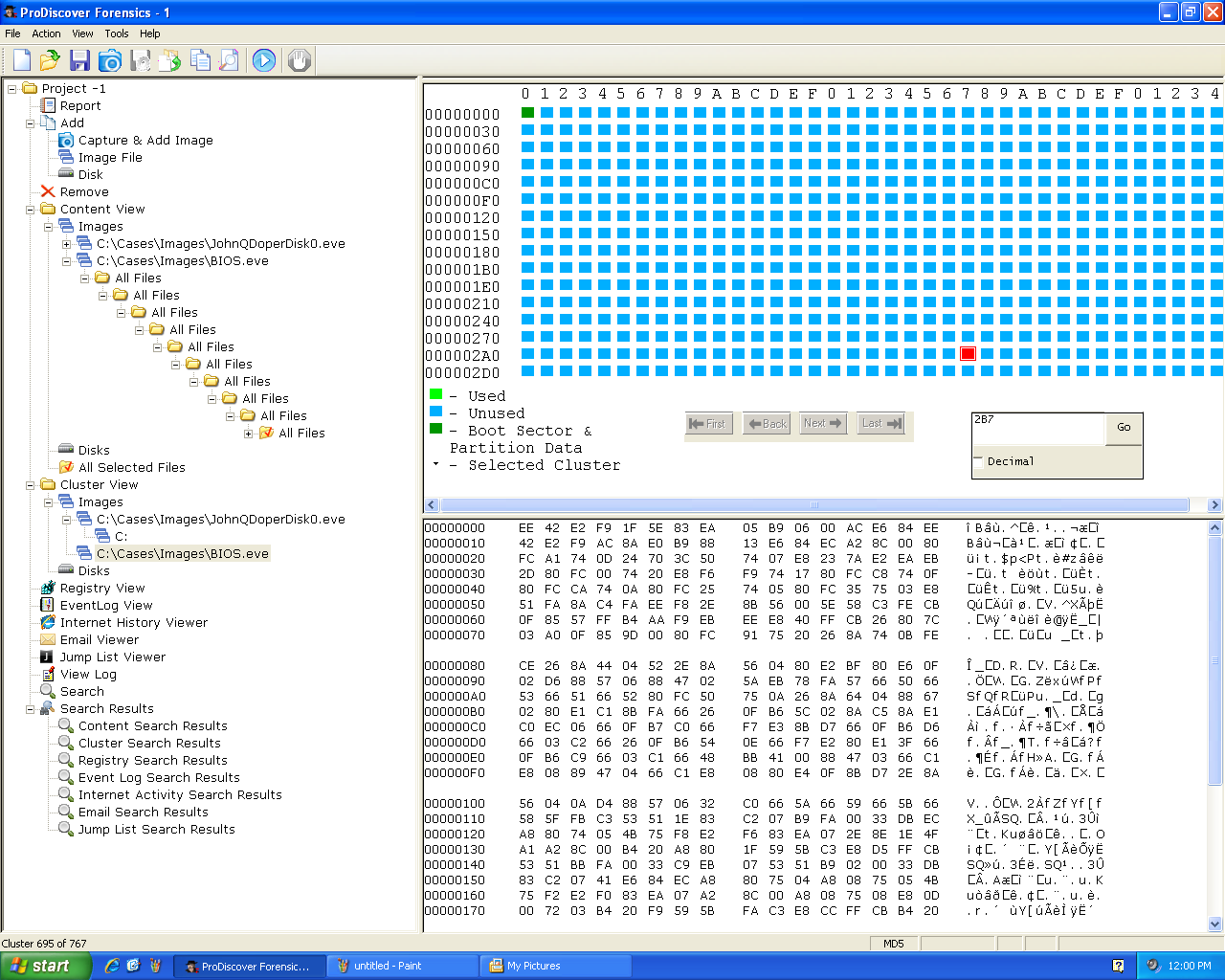
BIOS
ProDiscover can image the BIOS. However,
you need other tools to parse this data.
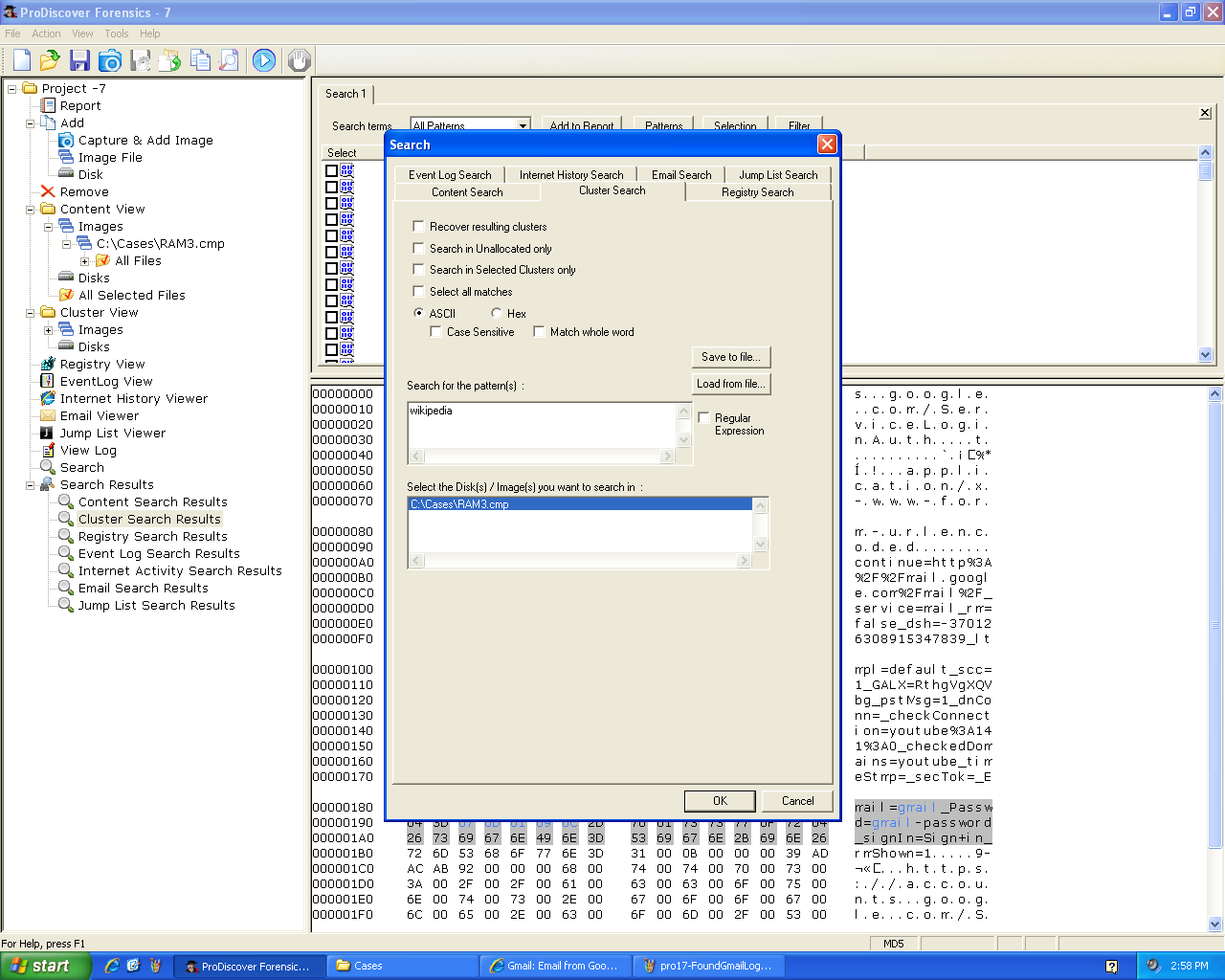
HTTP Password
I opened Internet Explorer and sent a
username of "wikipedia" and a password
of "wikipedia-password" to its login page.
Then I dumped the RAM with ProDiscover
and searched it for the string
"wikipedia".
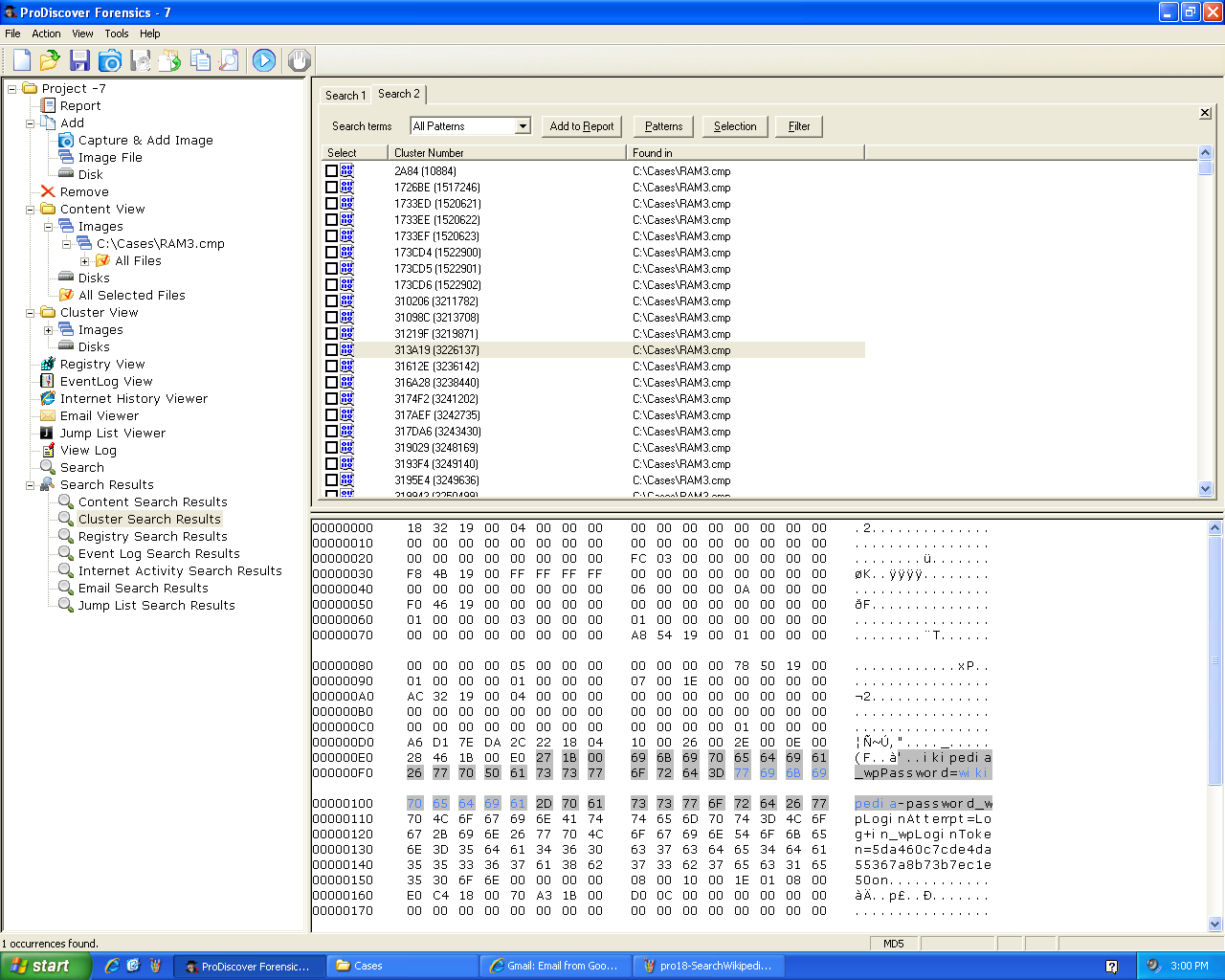
Among the hits I
found the password:
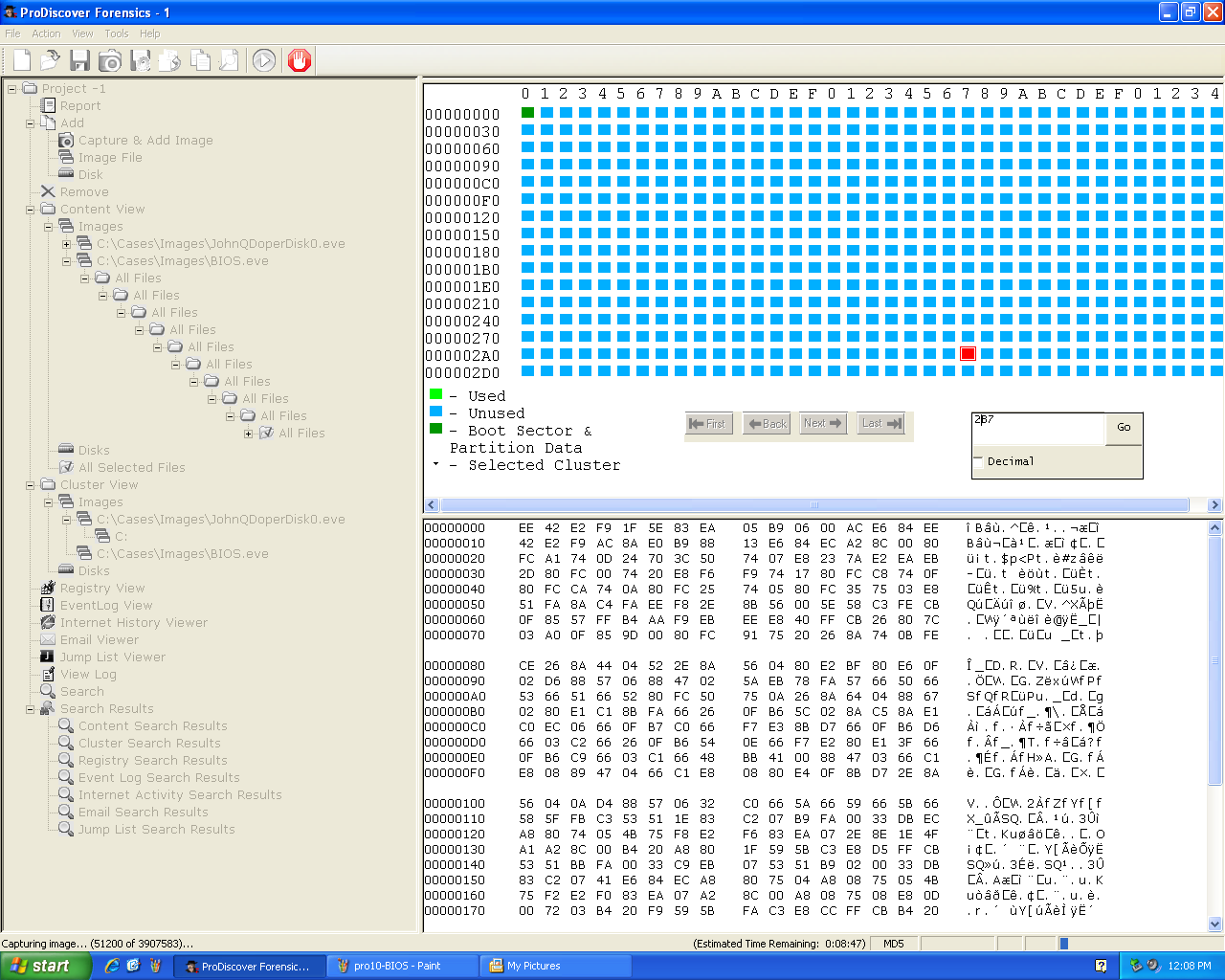
Split Image
Here's ProDiscover acquiring an image of a USB
drive. Notice the progress indicator in the
lower left corner:
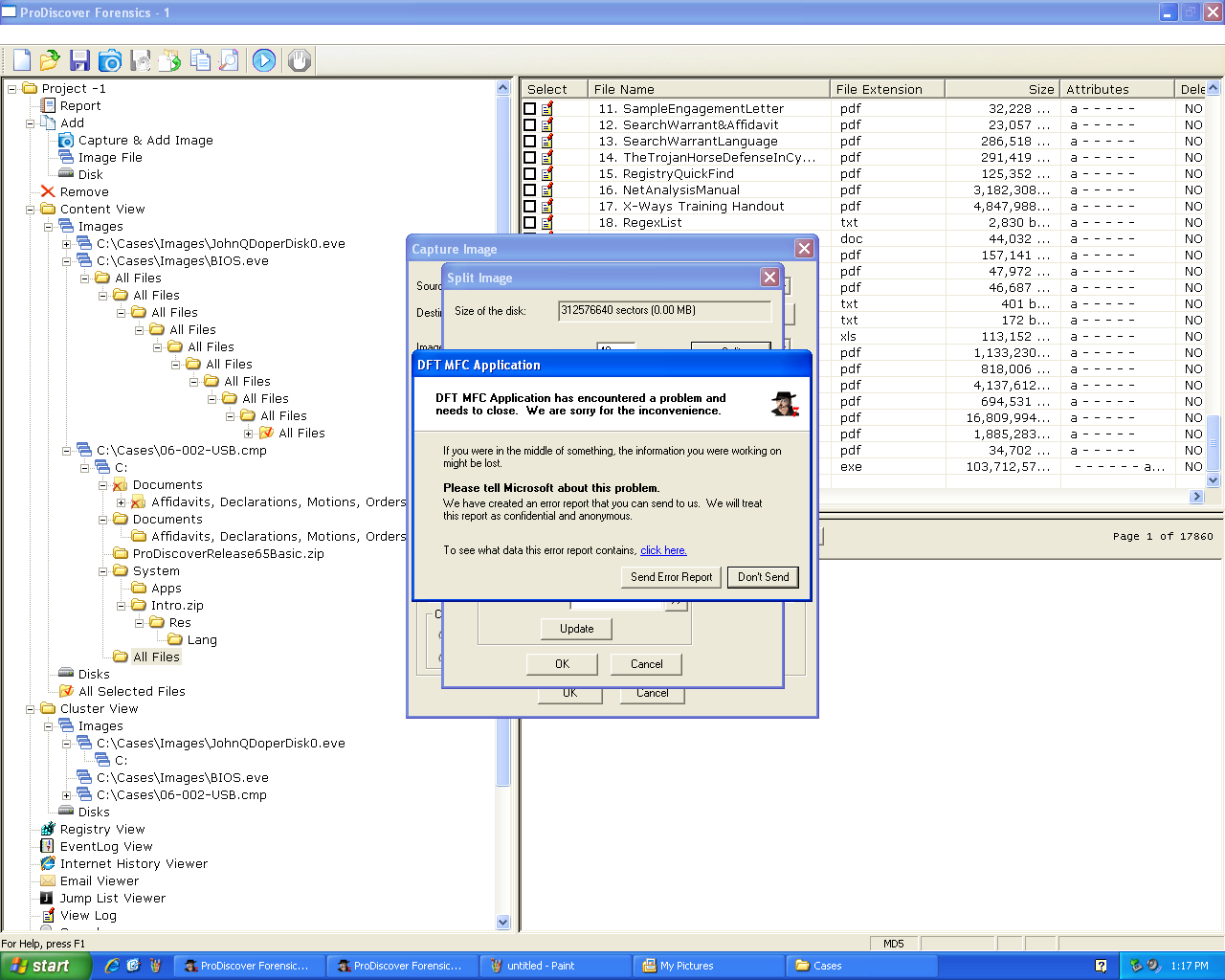
I tried to make a "Split" image of the USB
drive--splitting the file into many small
pieces. It failed and eventually crashed:
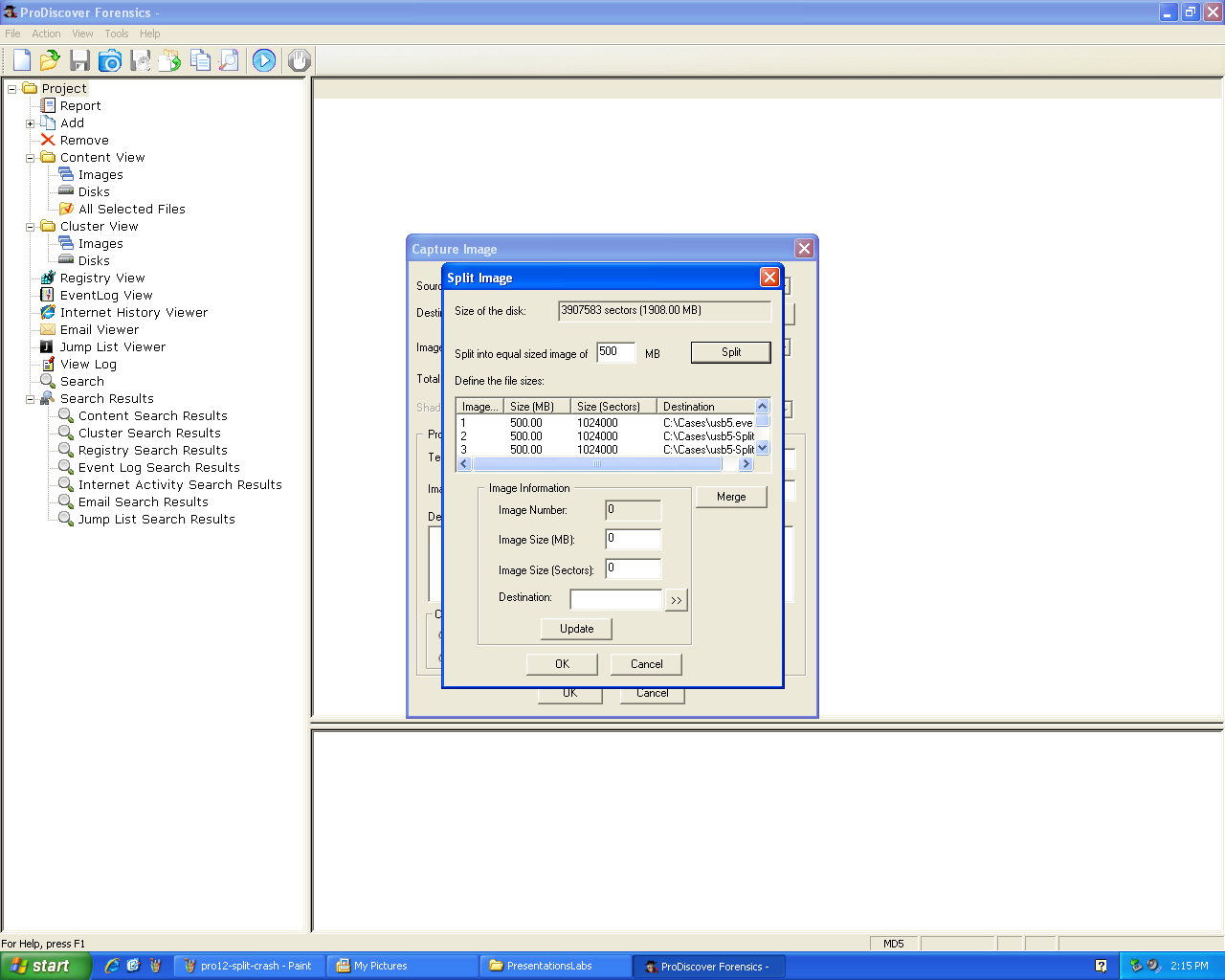
I asked for help making the split image.
After opening the "Split Image" box, I specified
the size and clicked the "Split" button.
Then it prepares all the image names in the list
shown in the middle of this box:
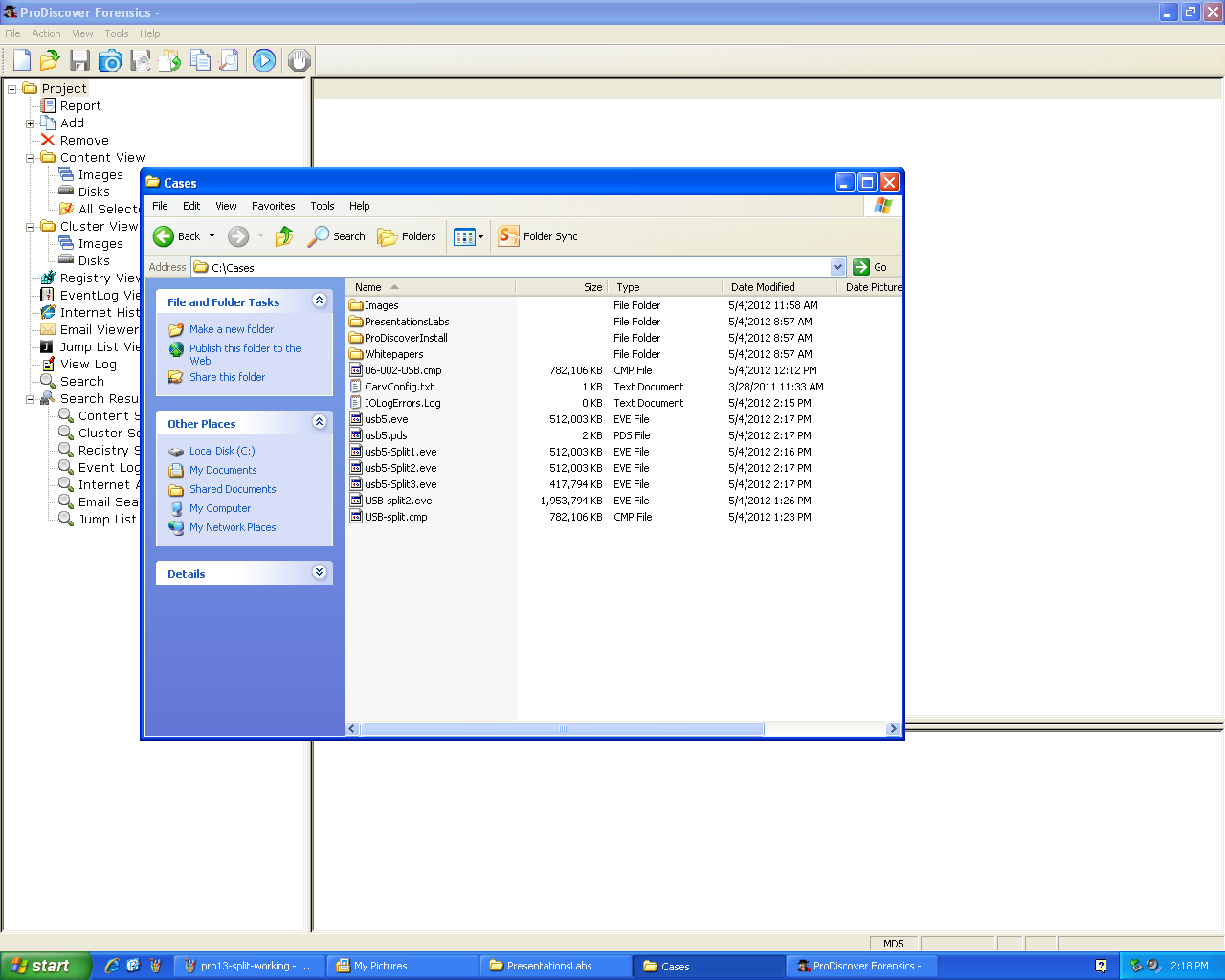
This was a successful split, breaking the image into
several files:
HTTPS Password
I wondered if HTTPS web passwords were stored
in plaintext.
So I opened Internet Explorer and sent a
username of "gmail" and a password
of "gmail-password" to its login page.
Then I dumped the RAM with ProDiscover:
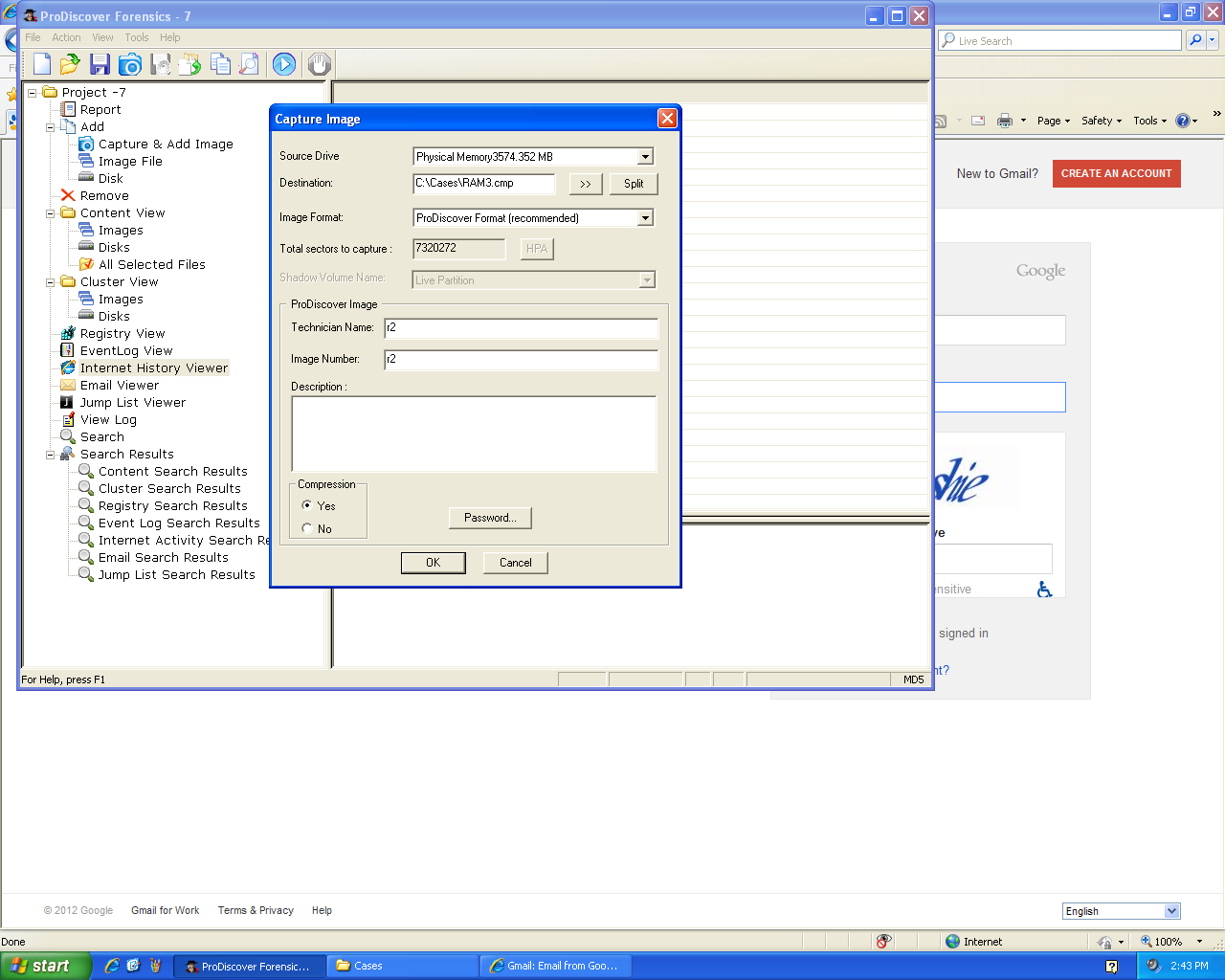
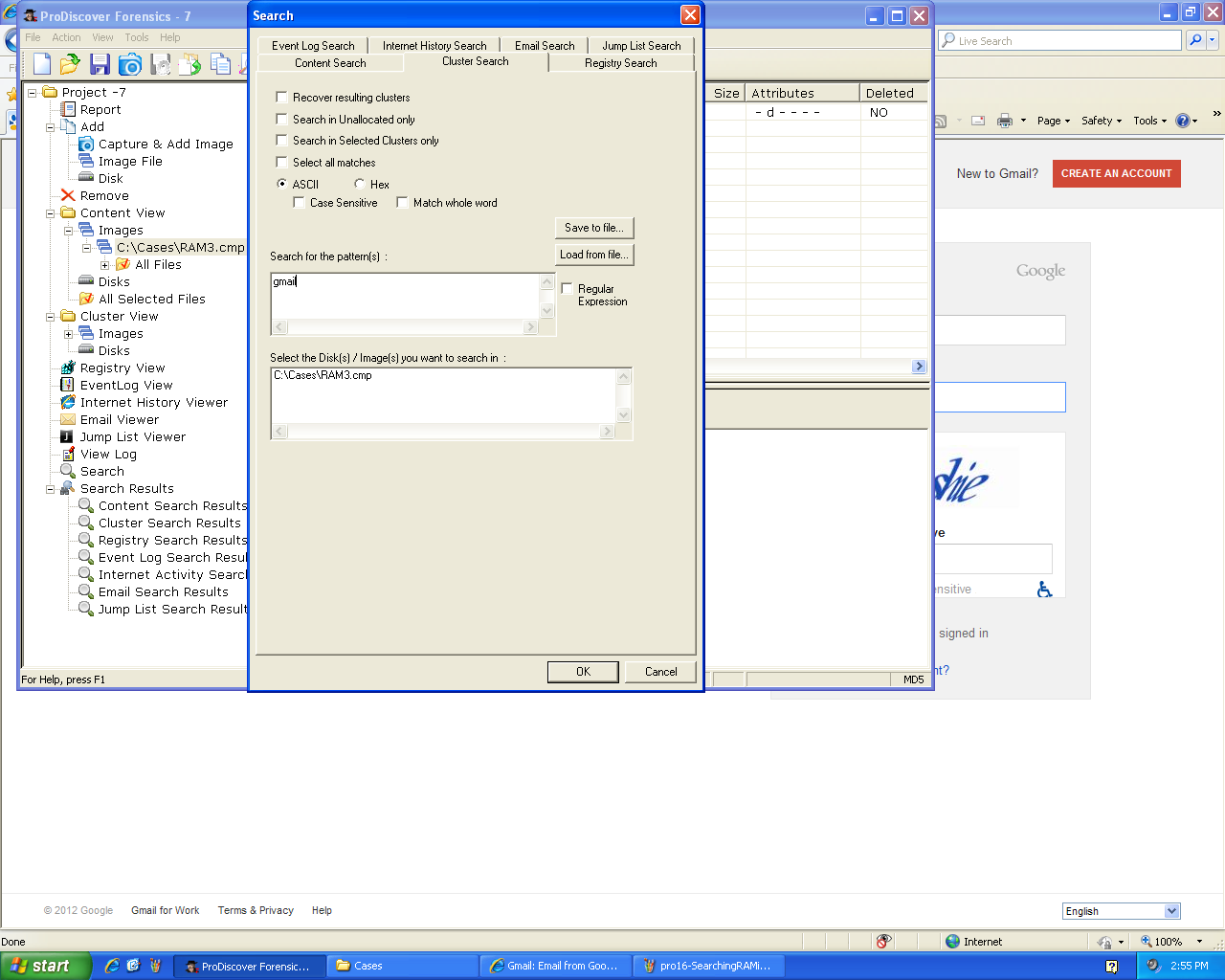
I searched it for the string
"gmail":
Among the hits I
found the password:
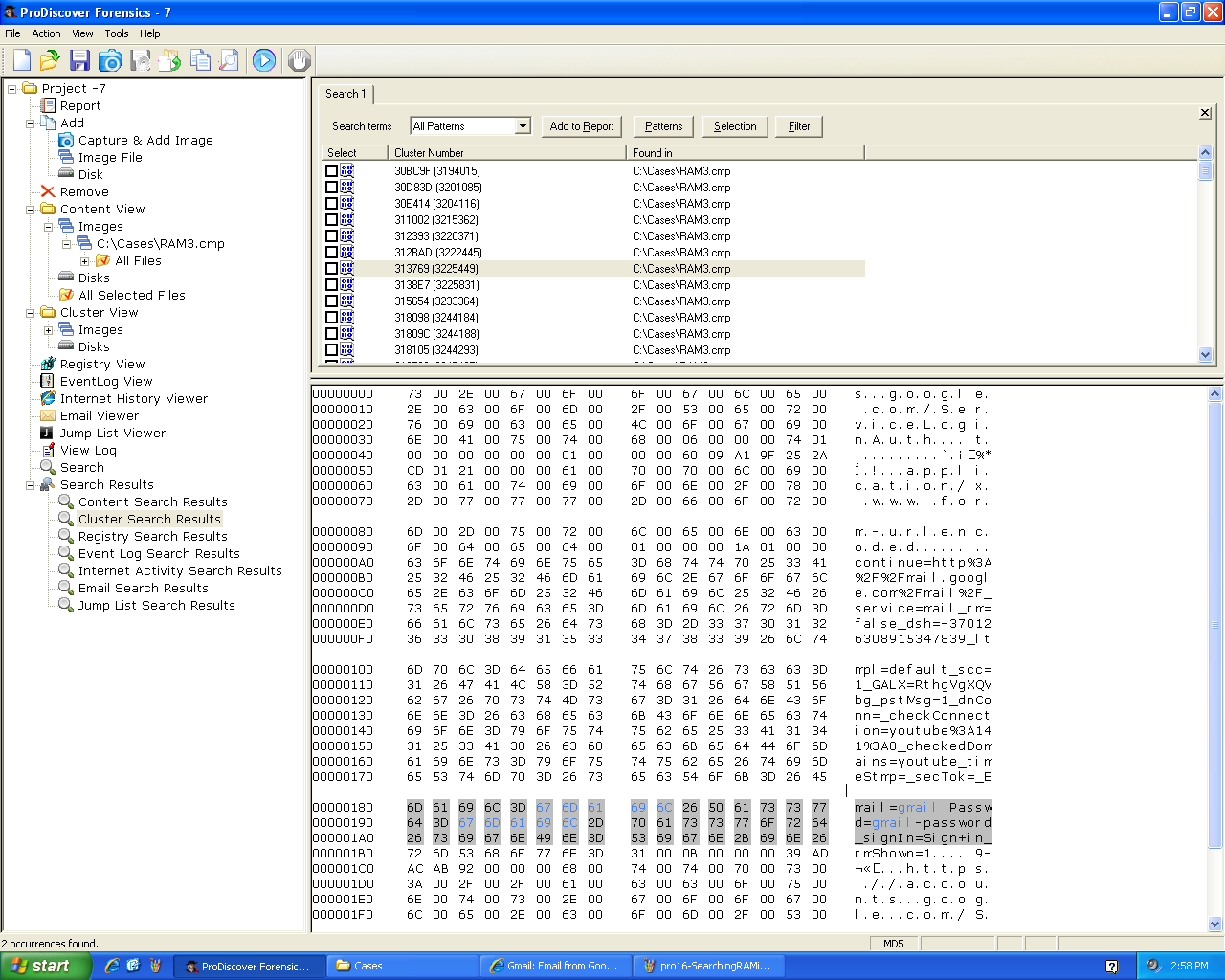
Logon Password
I wondered if Windows login passwords were
stored in RAM in plaintext. So I made an account
with a user name of "Sam" and a password of
"supersecretlongpassword". Then I acquired the
RAM and searched it for the string "supersecret":
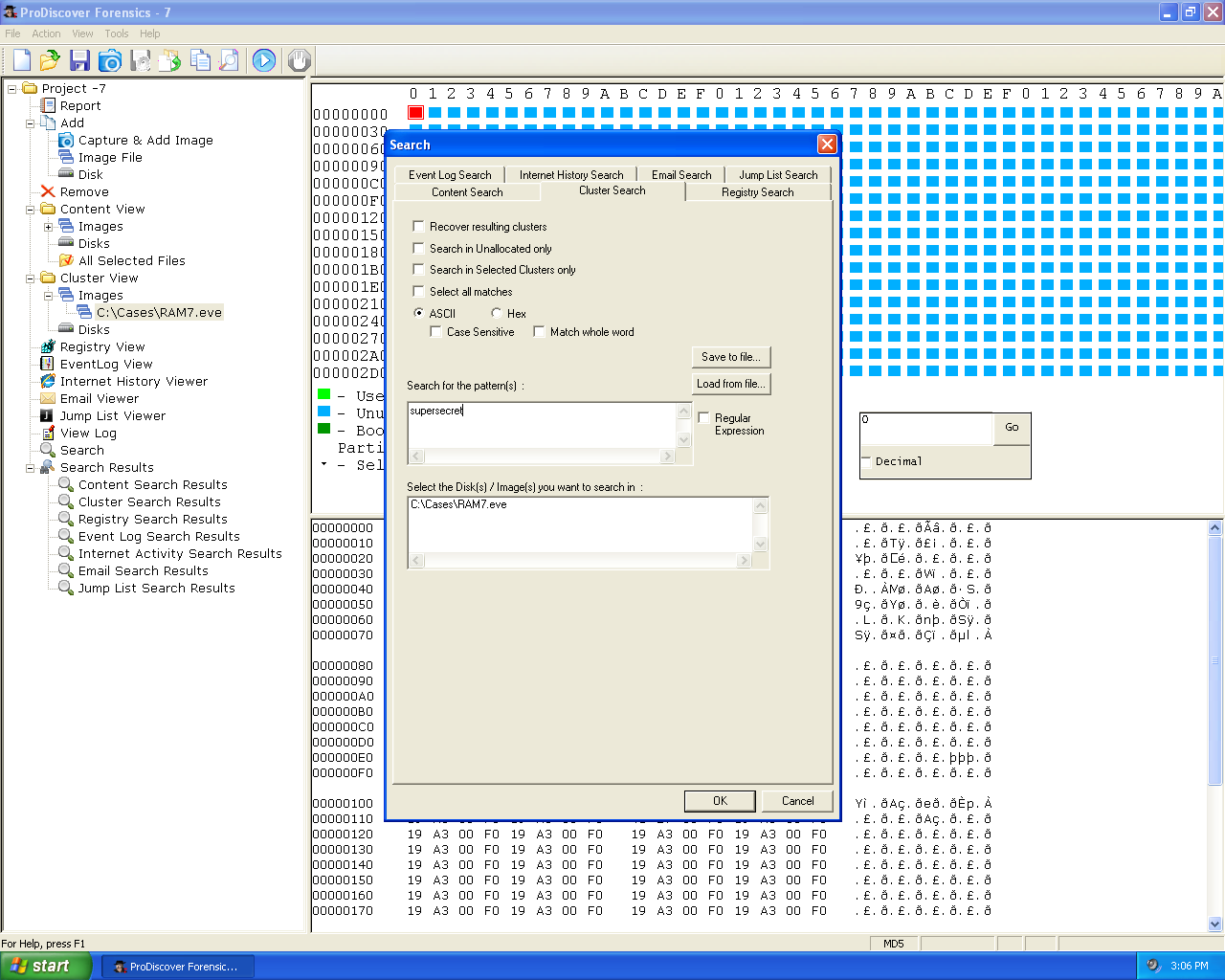
There were no hits. Windows does not store
passwords in RAM in cleartext:
I know you can steal Windows login passwords
from RAM with Windows Credential Editor. I found
an explanation of its operations
here.
As explained there, Windows does encrypt the credentials
it stores in RAM. But those researchers were able to
open the encryption.
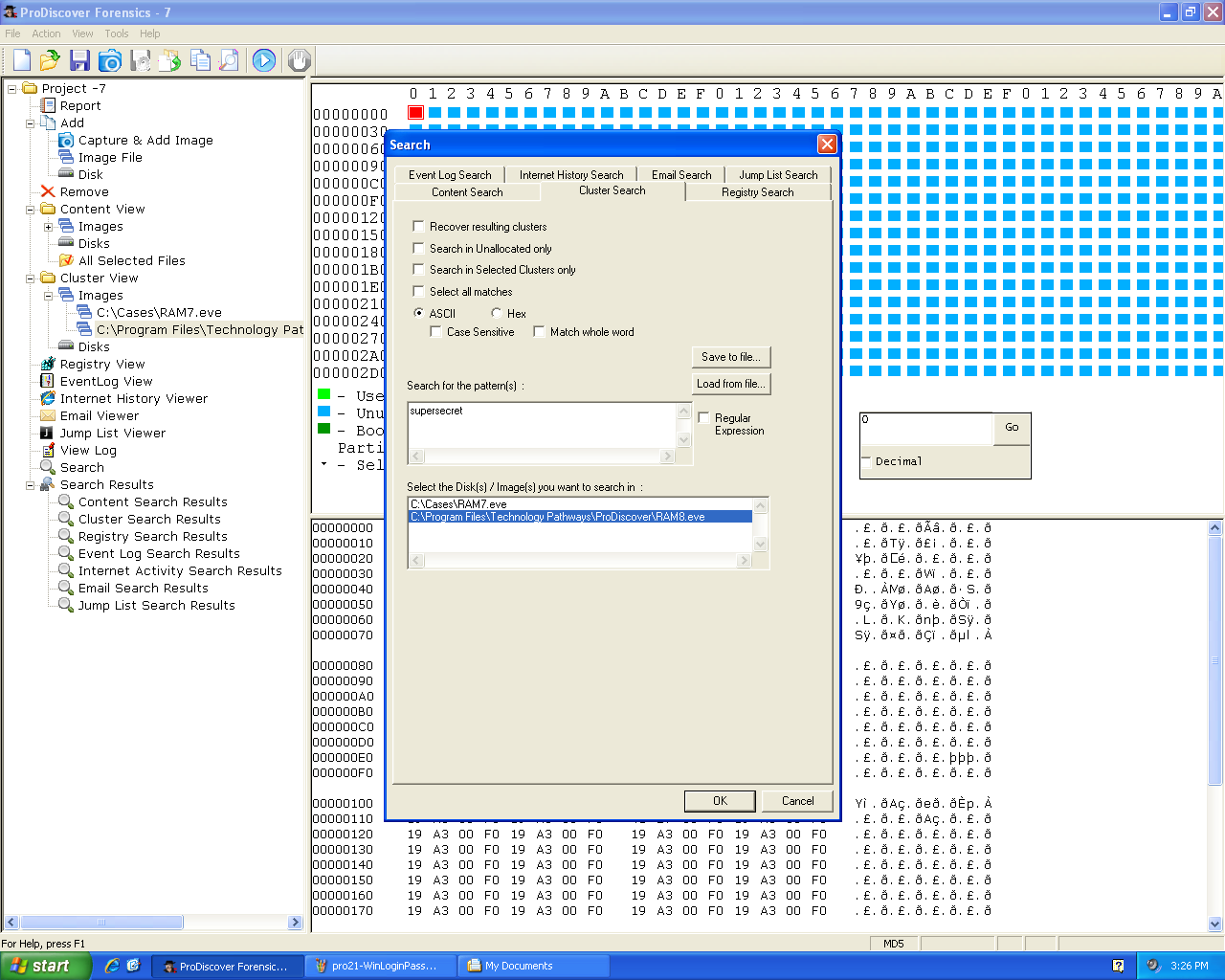
Word Password
I tried adding Microsoft Word 2010 password to a document.
Then I opened the document with the password.
Then I acquired the RAM and searched for the password:
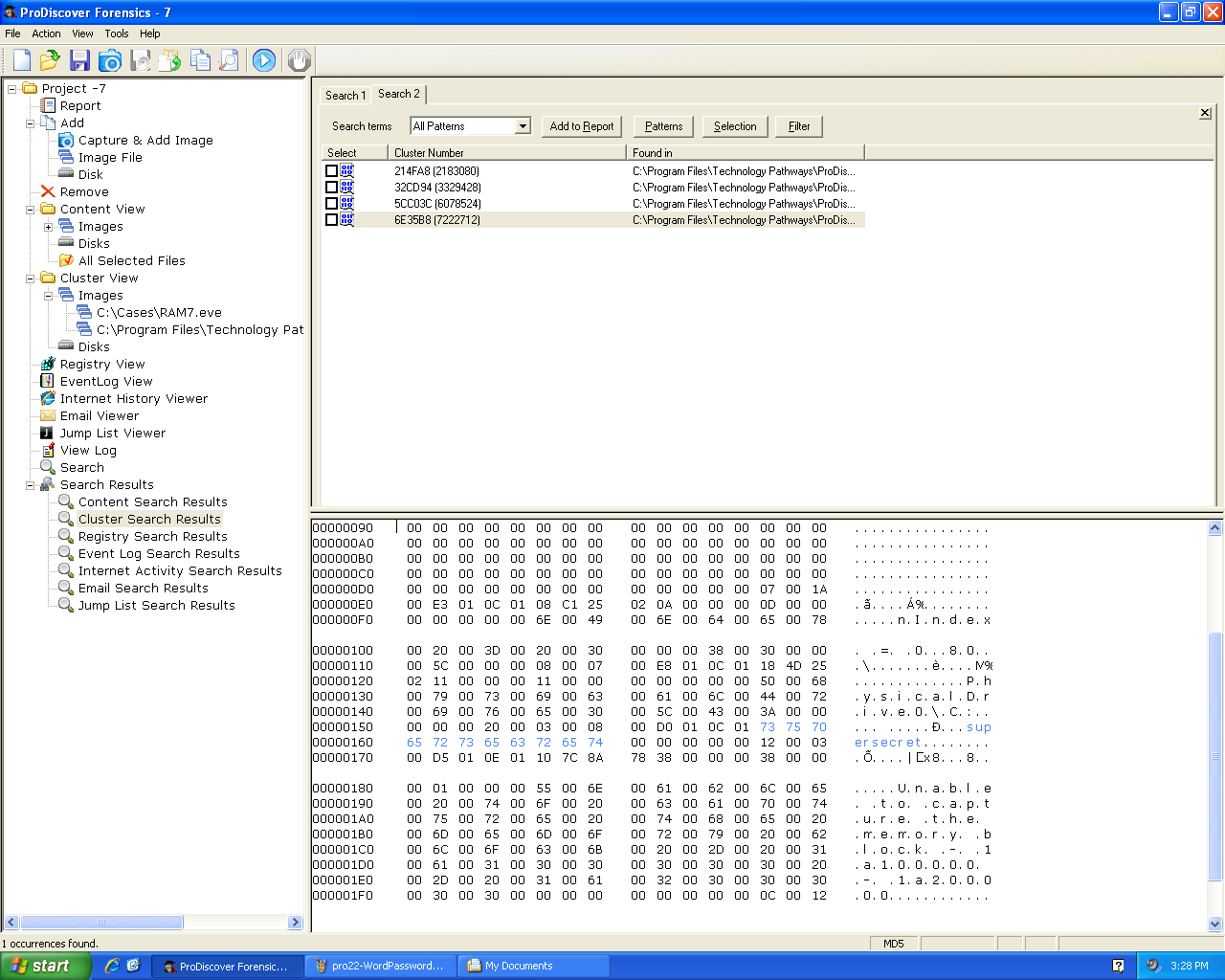
The password was not found--Windows XP doesn't store
Word passwords in RAM in plaintext:
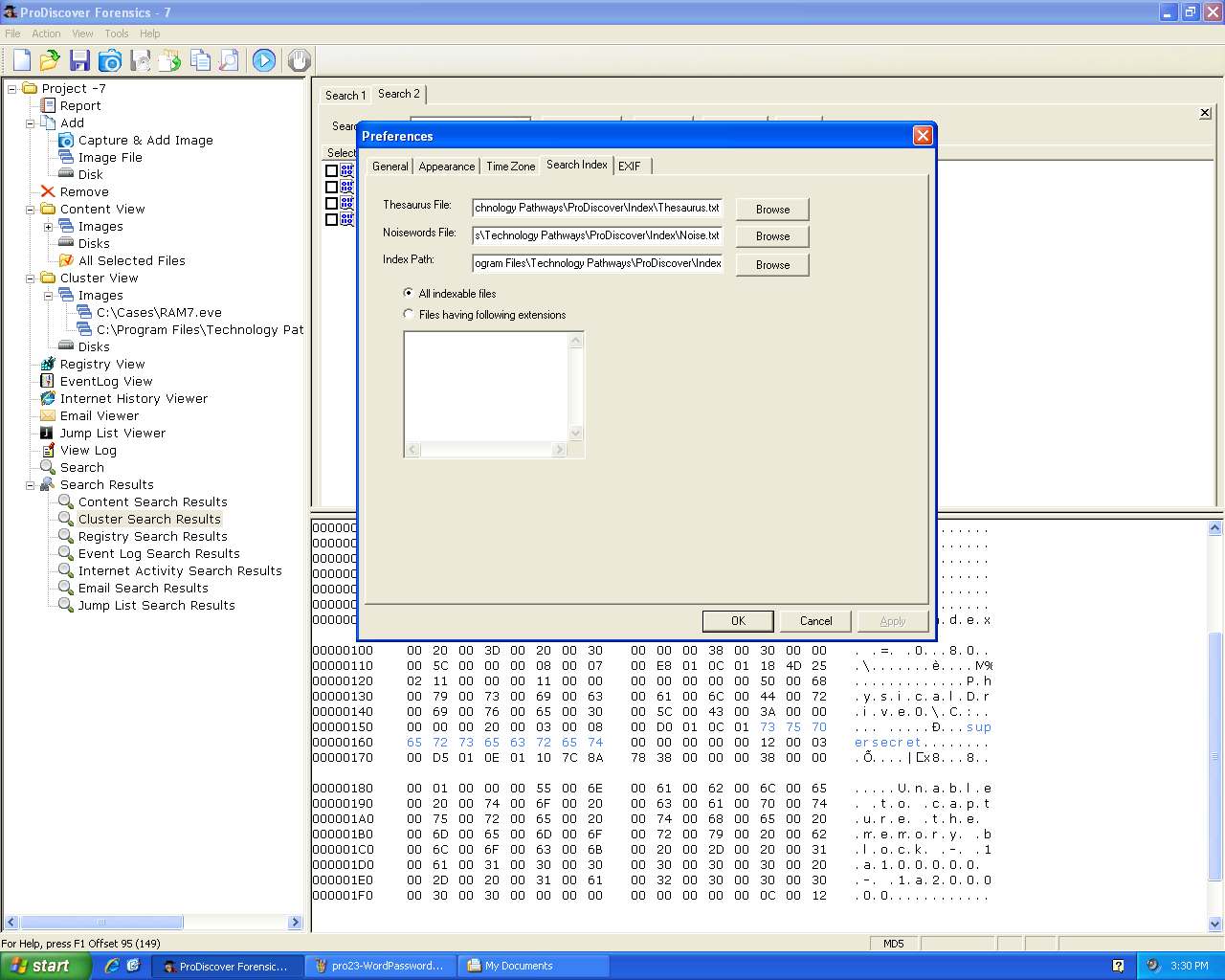
Indexed Searches
To make indexing faster, it is recommended to
configure a "Thesaurus" and "Noise" list in
ProDiscover before building an index:
Last updated 5-4-12 Sam Bowne