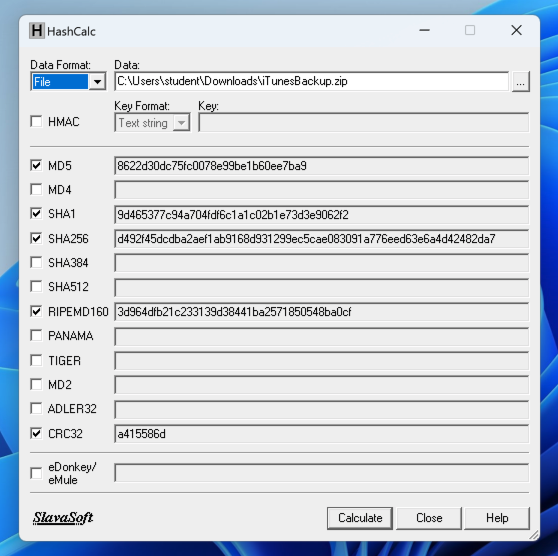
https://www.slavasoft.com/download.htm

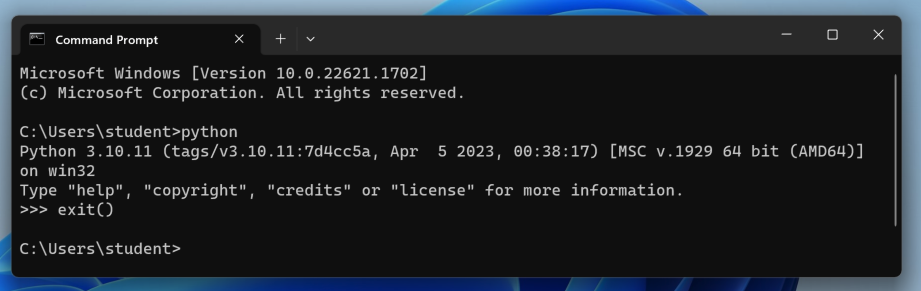
Execute this command:
python
If you have Python installed, it will open, as shown below.
Execute this command to exit from Python:
exit()
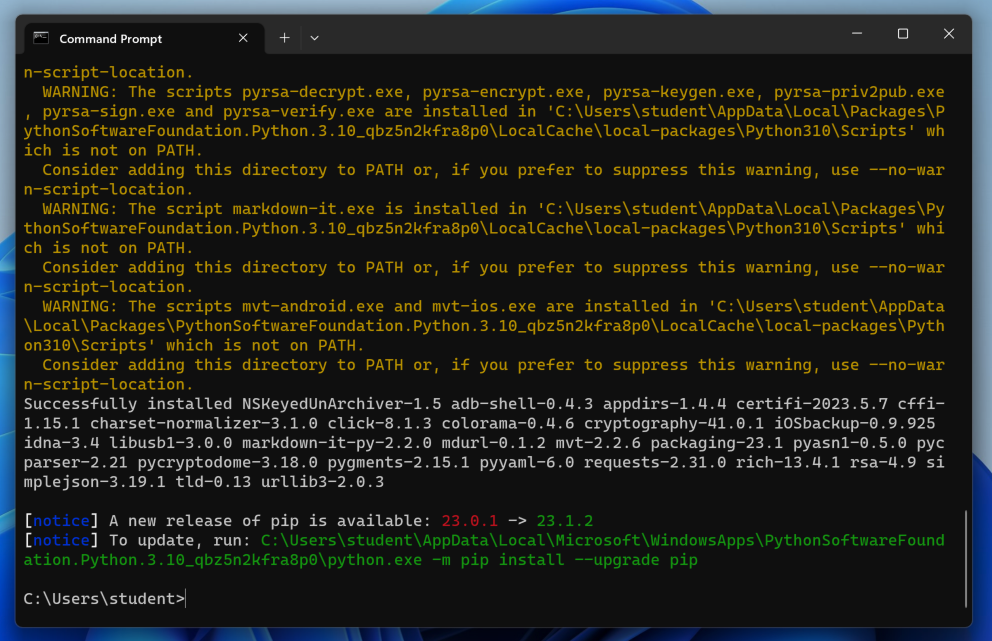
pip install mvt
To test your installation, execute this command:
mvt-ios
If that happens, execute this command:
pip show mvt
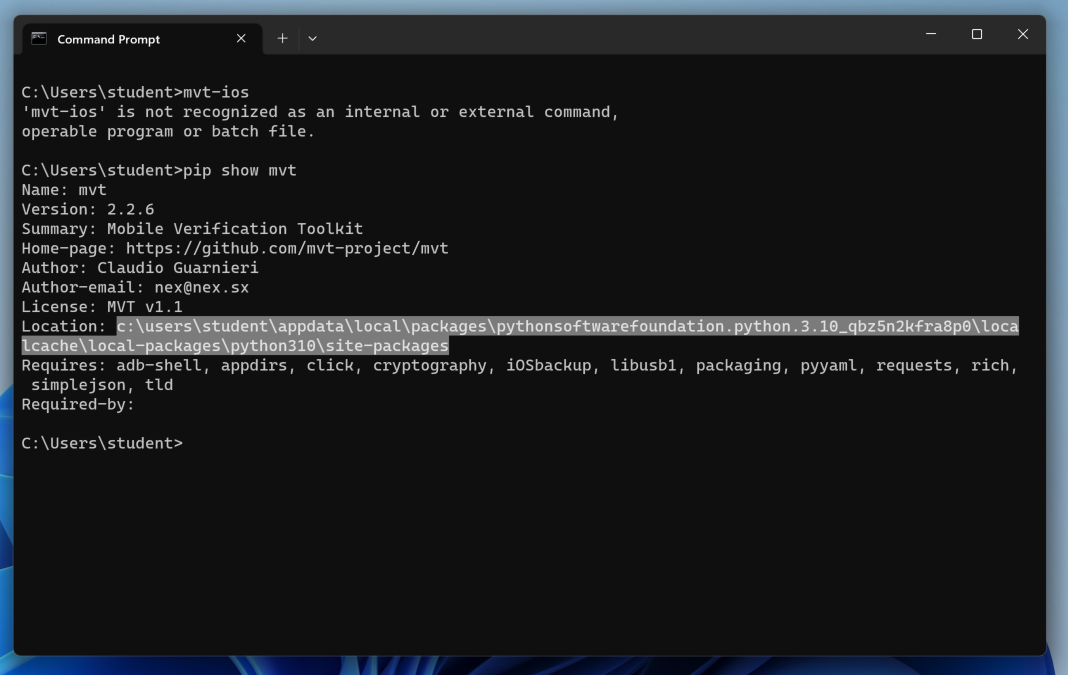
To copy the path, carefully highlight the whole thing, as shown above, and then press the Enter key.
Click Start. Type ENVIRONMENT. In the search results, click "Edit environment variables for your account".
In the top pane, click Path. Then click the Edit... button, as shown below.
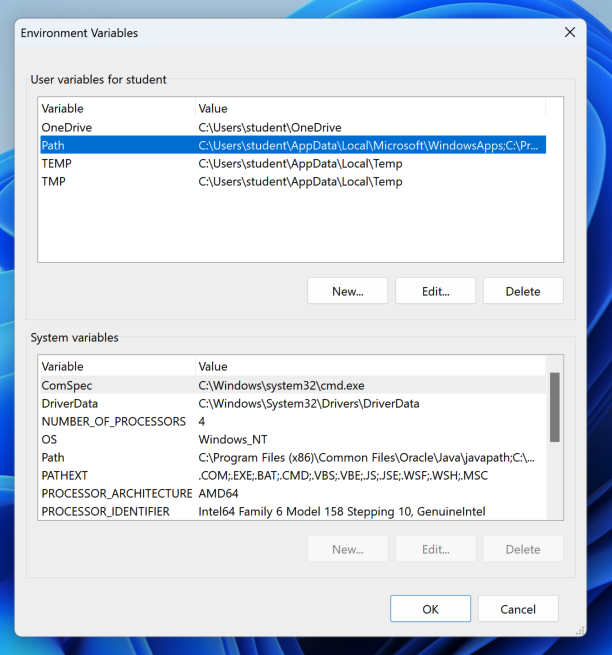
In the "Edit environment variable" box, click the New. button.
Paste in the long path you copied earlier, as shown below.
At the right end of that long path, delete "site-packages" and add
Scripts
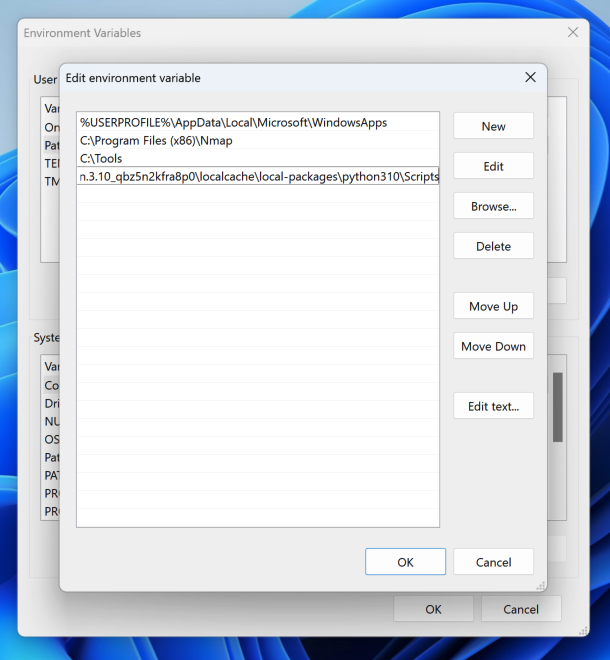
Click OK. Click OK.
Close the Command Prompt window. Open a new Command Prompt window.
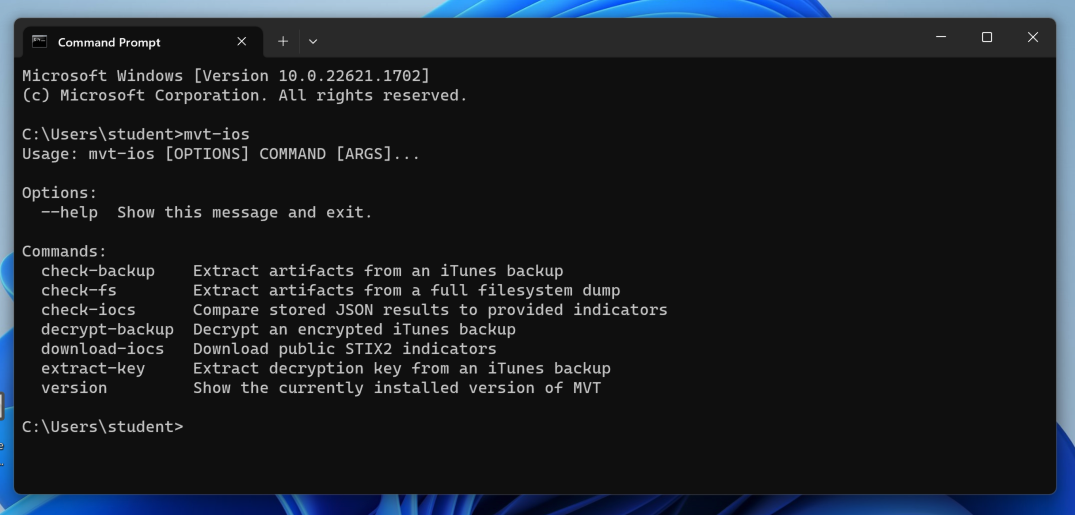
Execute this command:
mvt-ios
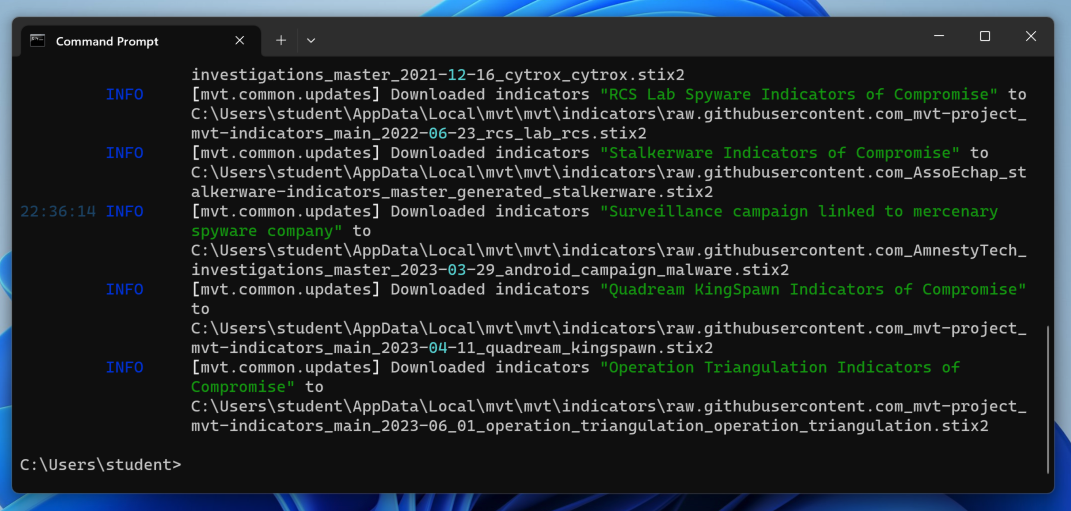
mvt-ios download-iocs
cd Downloads\iTunesBackup
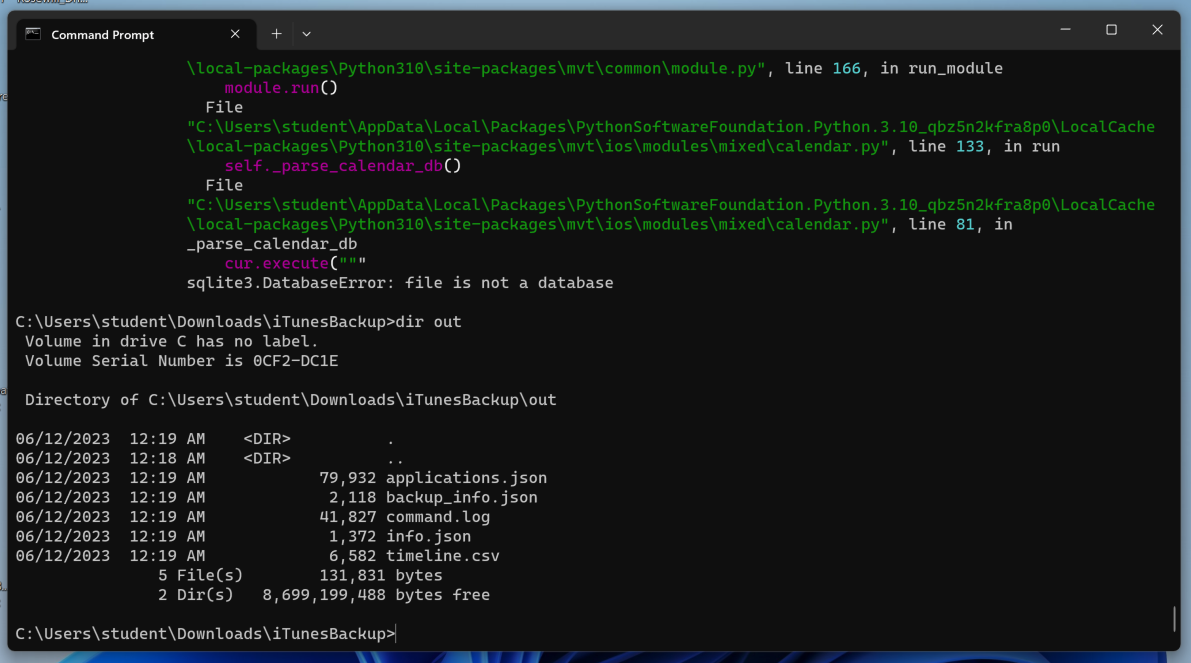
mvt-ios check-backup --output out iTunesBackup
dir out
F 231.1: Timeline (15 pts)
To find the latest threat, named "Triangulation", search the timeline.csv file for "BackupAgent".To search for all lines containing "ba", execute this command:
The flag is covered by a green rectangle in the image below.
Posted 6-12-23