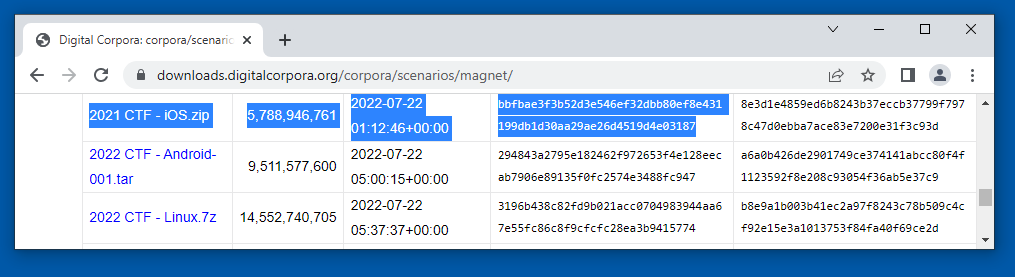
https://downloads.digitalcorpora.org/corpora/scenarios/magnet/
Download the "2021 CTF - iOS.zip" file, highlighted in the image below.
cd Downloads
Get-FileHash -Algorithm SHA256 "2021 CTF - iOS.zip"
Enter a Case Name of iPhone.
Click the Next button.
Click the Finish button.
At step 2. Select Data Source Type, click "Logical Files".
Click the Next button.
At step 3. Select Data Source, click the Add button. Navigate to your desktop. Click the "2021 CTF - iOS" folder and click Select.
Click the Next button.
At step 4. Configure Ingest, clear all the boxes except "iOS Analyzer (aLEAPP)", as shown below.
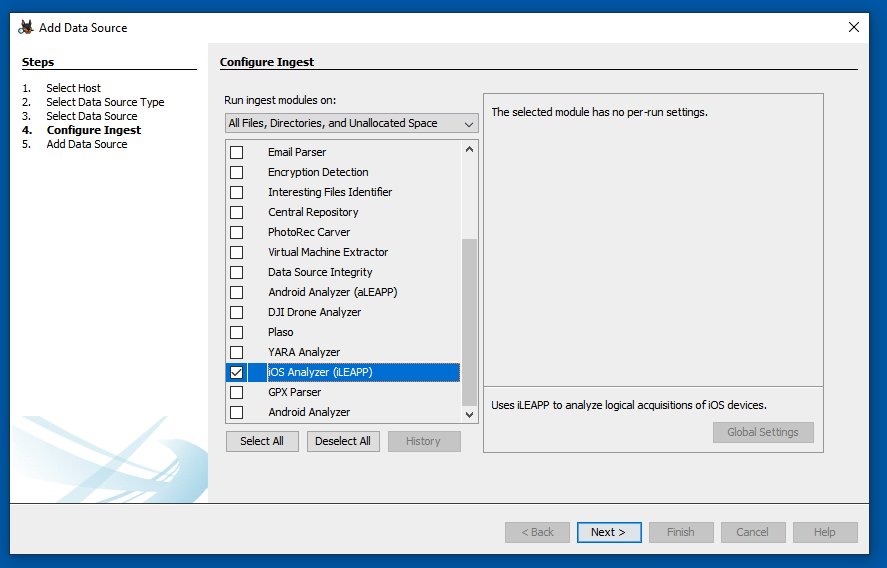
Click the Next button.
At step 5. Add Data Source, click the Finish button.
F 230.1: Phone Number (5 pts)
If you are using Autopsy v. 4.21, find the name of the device paired via Bluetooth, covered by a green rectangle in the image below. That's the flag.
If you are using Autopsy v. 4.20, find the phone number in the 541 area code, covered by a green rectangle in the image below. That's the flag.
F 230.2: Latitude (5 pts)
Examining the GPS data, what was the most northern latitude of the phone?If your version of Autopsy doesn't show "GPS Last Known Location" values, look in "Wireless Networks".
F 230.3: SMS (5 pts)
Examining the Messages, what code did SIGNAL send the phone?
F 230.4: Signal Contact (5 pts)
Examining the Program Notifications, find the person named Johnathan who sent Snapchat (also called pikaboo) messages to this phone.What is that person's last name? That's the flag.
Posted 10-7-22
F 230.4 description fixed 11-5-22
References to Android removed 11-12-22
Alternate value for Flag 1 added 10-24-23
Hint added to flag 2 11-12-23
Hashcalc reference replaced with PowerShell 4-16-24