This project just follows this excellent write-up from MDSec: Analysing LastPass, Part 1.
https://www.google.com/chrome/
https://learn.microsoft.com/en-us/sysinternals/downloads/process-explorer
https://mh-nexus.de/en/hxd/
https://www.lastpass.com/Click the "Get LastPass Free" button.
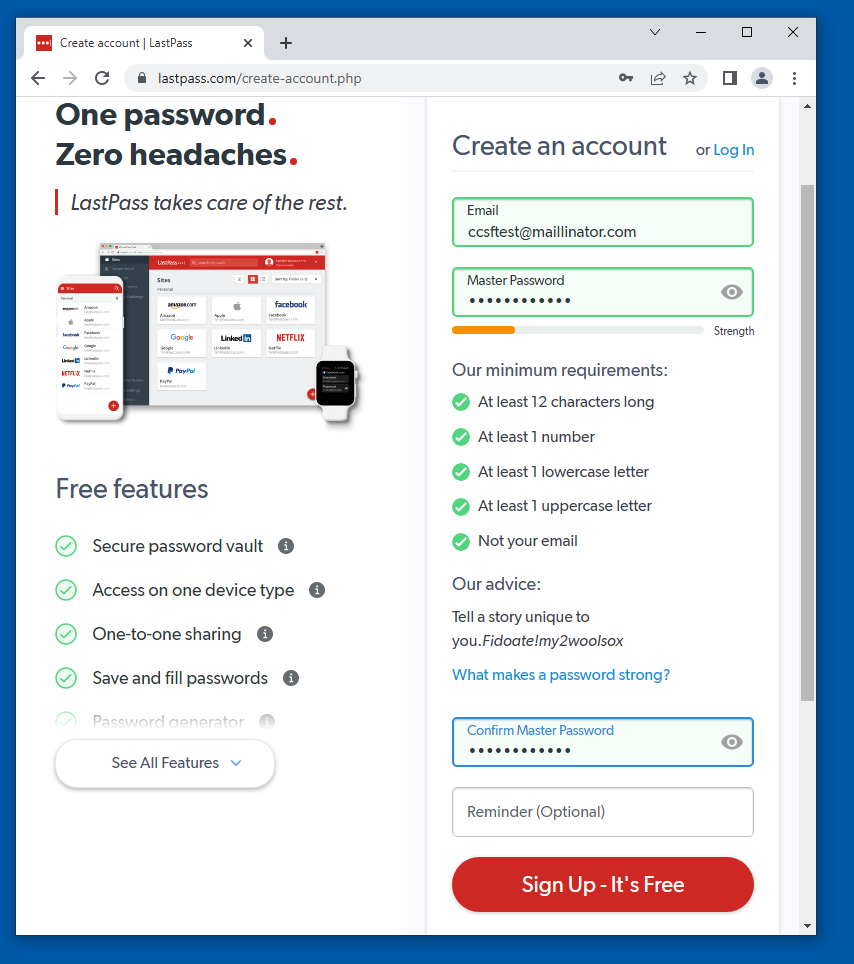
Fill in the form, as shown below.
Use a disposable email address, such as YOURNAME@mailinator.com.
Click the "Sign Up-It's Free" button.

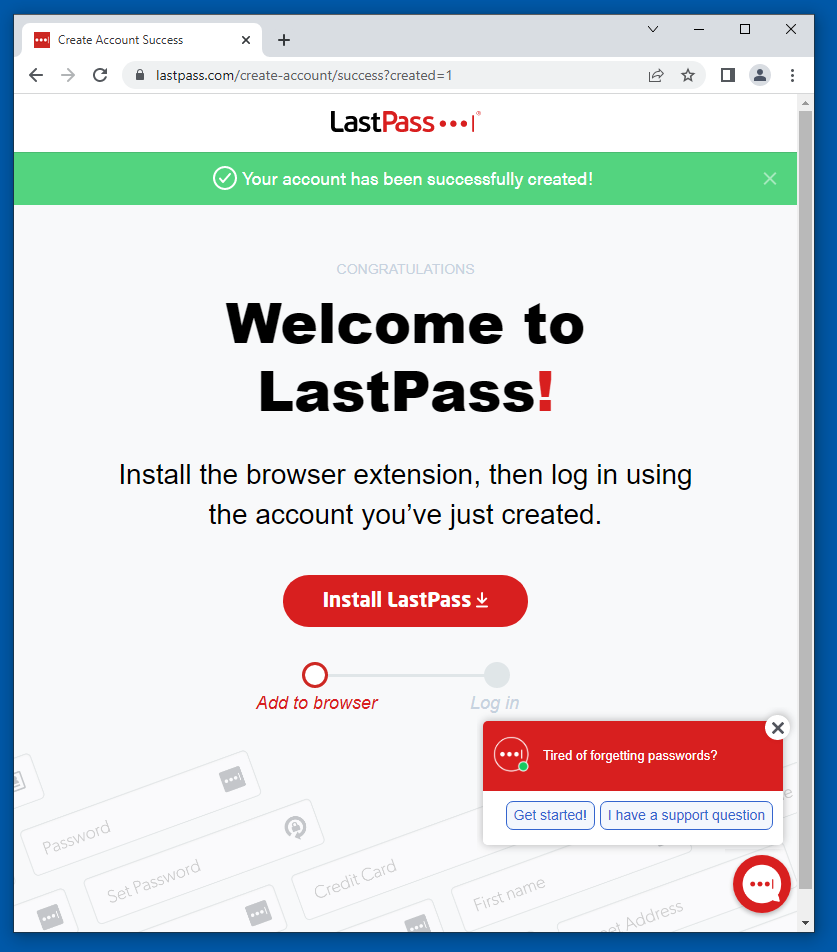
A Lastpass screen opens, as shown below.
At the bottom center, click "Add items one-by-one".
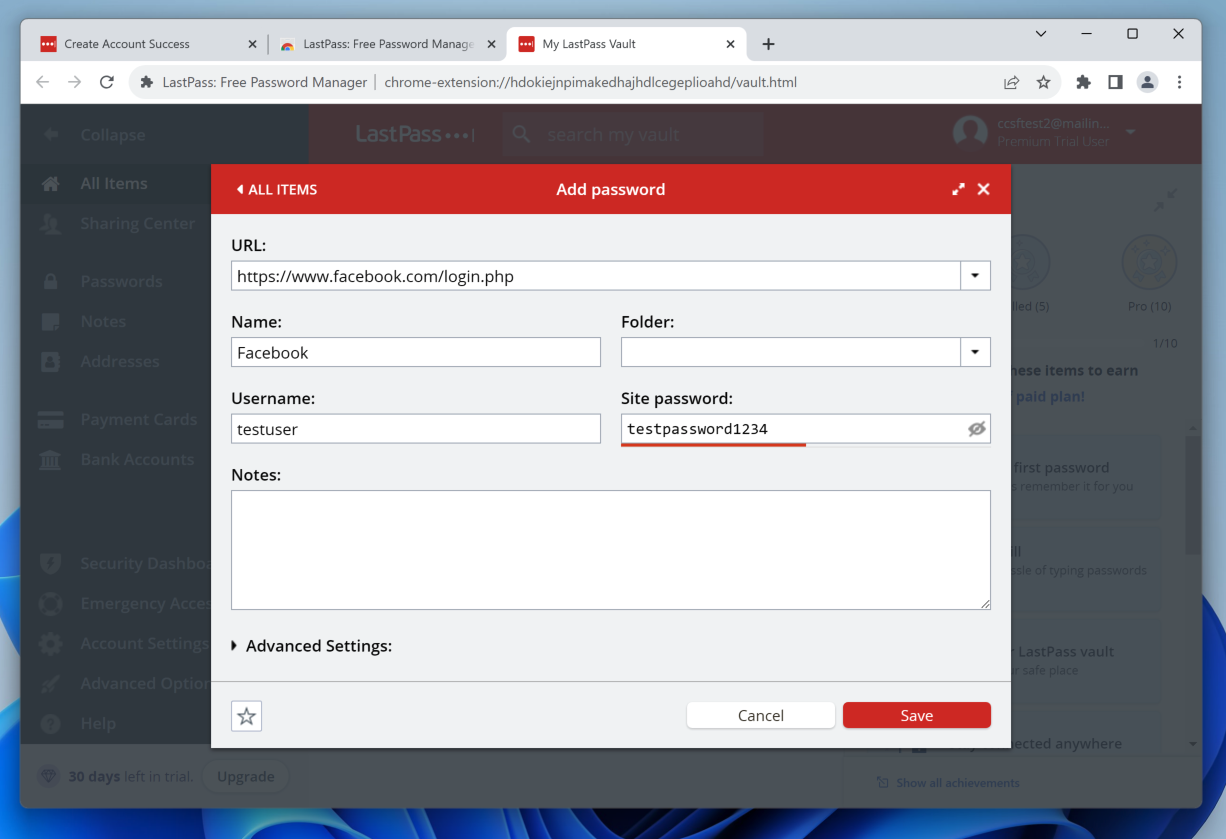
Add a fake password with these values, as shown below:
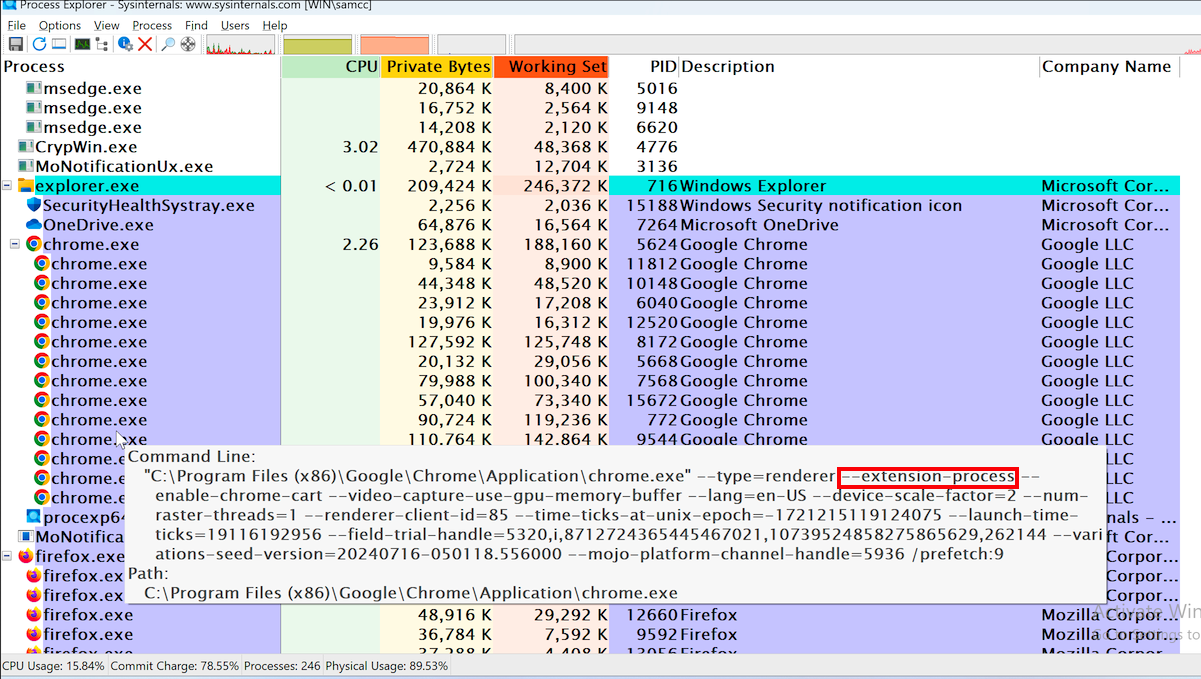
There are several Chrome processes, as shown below.
Hover the mouse over a Chrome process to see its command line.
Find the process with this switch, outlined in red in the image below:
-- extension-processMake a note of the PID of that process. In the image below, it's 3400.
Check to see if there is a second process with the "-- extension-process" switch. When I did it there were two. Note both PID values.
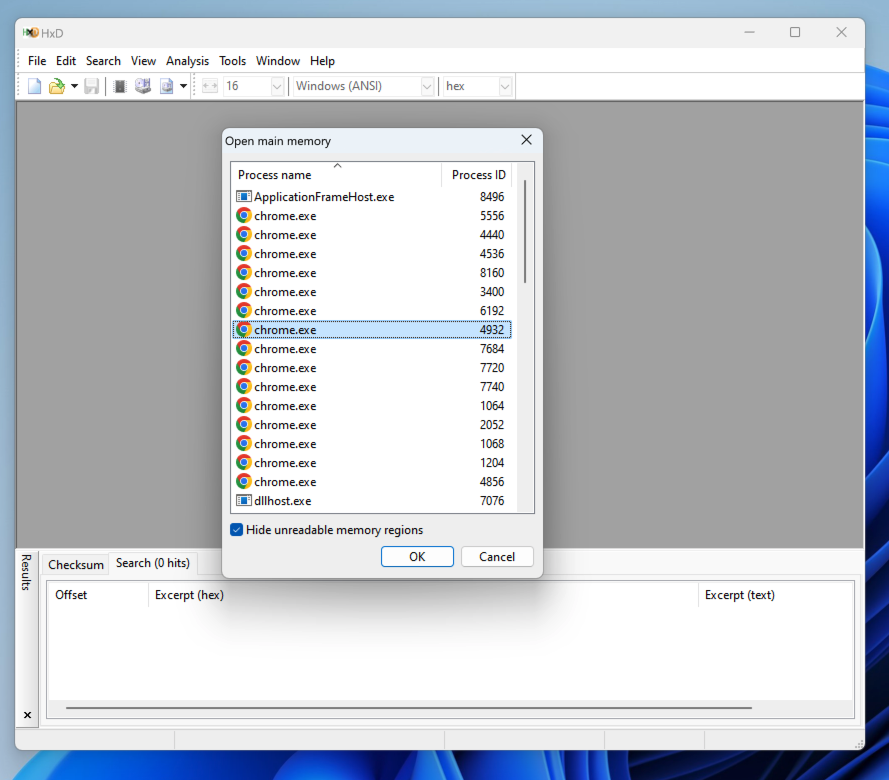
From the menu bar, click Tools, "Open main memory...".
Find the Process ID of the process containing the LastPass extension, as shown below, and double-click it.
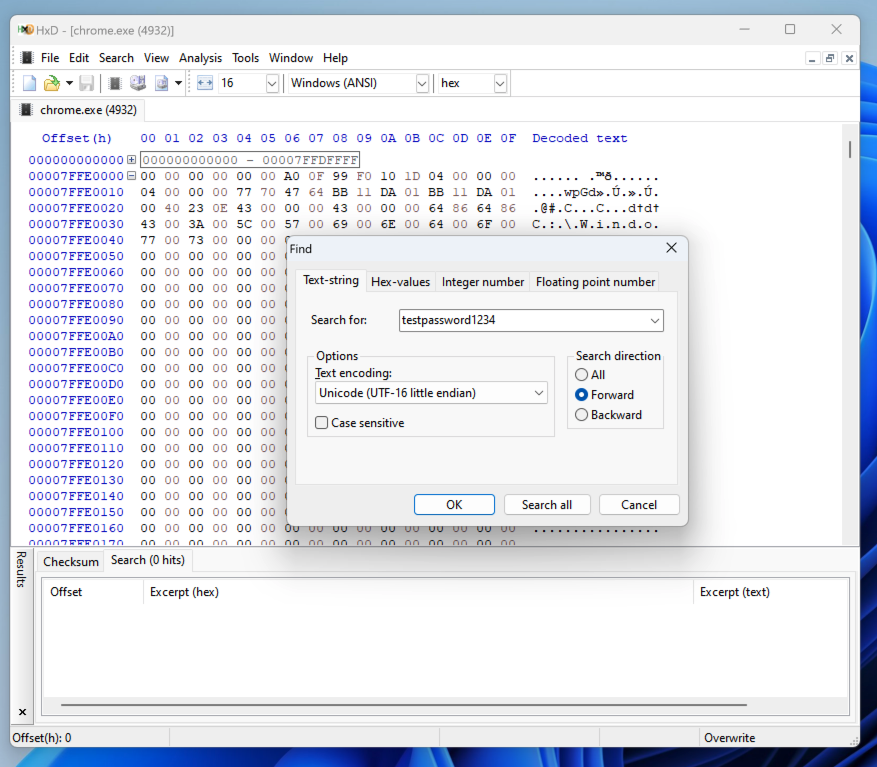
In the "Search for" field, enter testpassword1234
Set the Text Encoding to "unicode (UTF-16 little-endian)", as shown below.
F 211.1: Password Label (15 pts)
The flag appears at the lower right, covered by a green rectangle in the image below.
https://getfirefox.com
https://www.keepersecurity.comAt the top right, click "Try it Free for 10 Days".
Click "Personal and Family".
Enter a disposable email address ending in mailinator.com and click "Try it Free Now".
Create an account and log in.
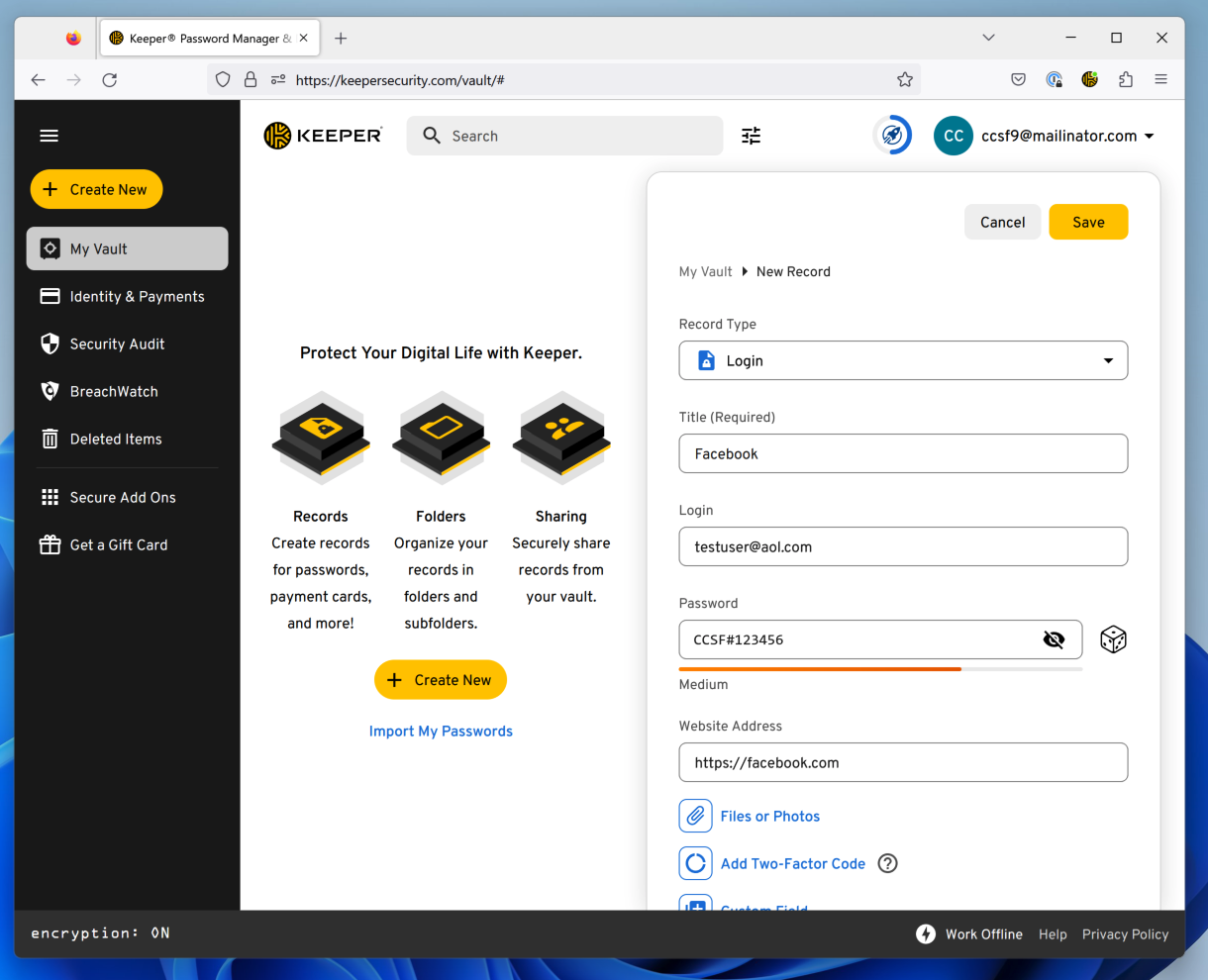
Click the "Create New" button.
Click Record.
Create a "Login" record with any name and a password containing the string CCSF#, as shown below.
Install the KeeperFill Browser Extension.
F 211.2: Finding the Process Containing Private Data (10 pts)
It's difficult to find the correct Firefox process. You don't always see the same indicator.In Process Explorer, click View, "Show Lower Pane".
Click View, "Lower Pane View", DLLs.
Look for one of these clues:
In HxD, search that Firefox process for the string "CCSF#" in Unicode, as shown below.
- A DLL with a name containing "keepersecurity" or "formautofill"
- A handle to File \Device\KsecDD (You'll need to change the lower pane view)
The flag is covered by a green rectangle in the image below.
Posted 10-23-2021
Keeper added 11-3-22
Lastpass link fixed 11-29-22
Flag 2 changed 12-3-22
Flag 1 changed and video added 4-24-23
Flag 2 changed 5-4-23
Instructions for LastPass updated 11-7-23
--extension-process figure fixed 7-17-24