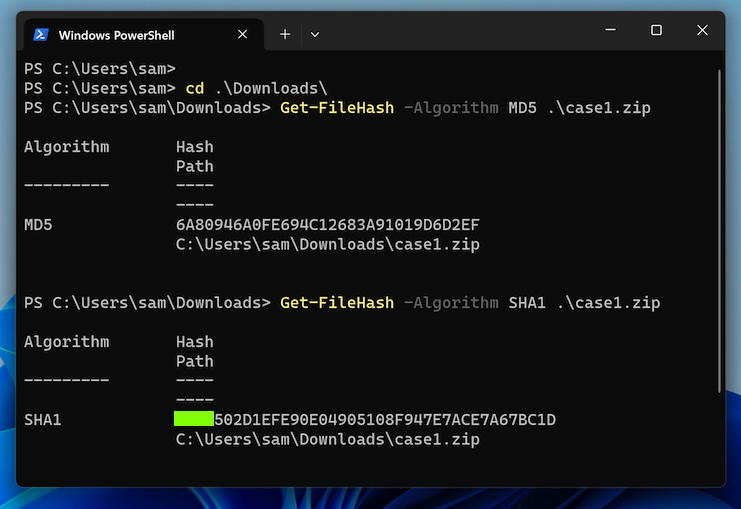
F 201.1: Verifying Hash Values (5 pts)Open a PowerShell window and execute these commands, as shown below.The flag is the first portion of the SHA1 address, covered by a green rectangle in the image below.
|