cd
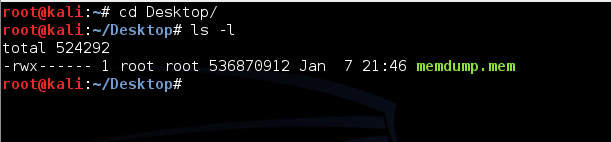
cd Desktop
ls -l
You should see the memdump.mem file, which should be approximately 500 MB in size, as shown below. If you do not, you may need to repeat a previous project to create the memory image again.

volatility -h
The volatility help is long and confusing.
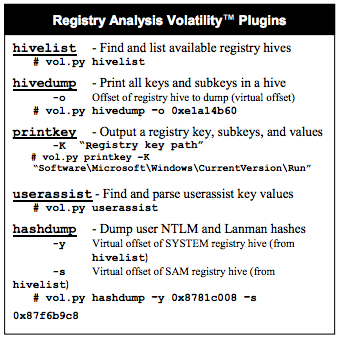
Fortunately, SANS has made a handy one-page cheat sheet which is much friendlier. The part that is important to us is shown below:
volatility imageinfo -f /root/Desktop/memdump.mem
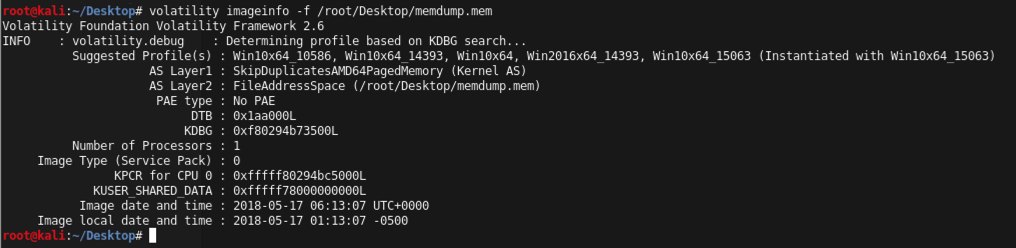
Volatility needs to know what operating system was imaged in order to interpret the memory image correctly. The default profile is WinXPSP2x86, but we used Win2008SP1x86, so we'll have to include that information in all future volatility command-lines.
volatility pslist --profile=Win2016x64_14393 -f /root/Desktop/memdump.mem
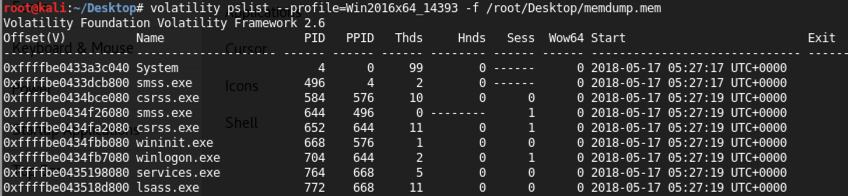
Notice these columns:
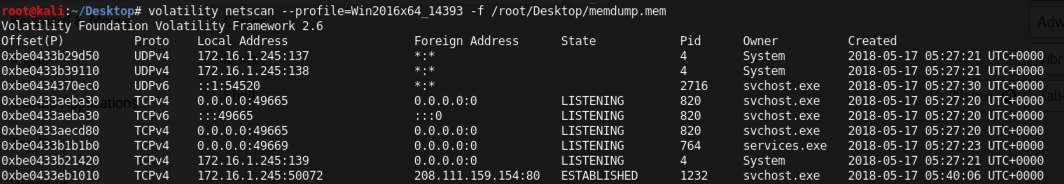
volatility netscan --profile=Win2016x64_14393 -f /root/Desktop/memdump.mem
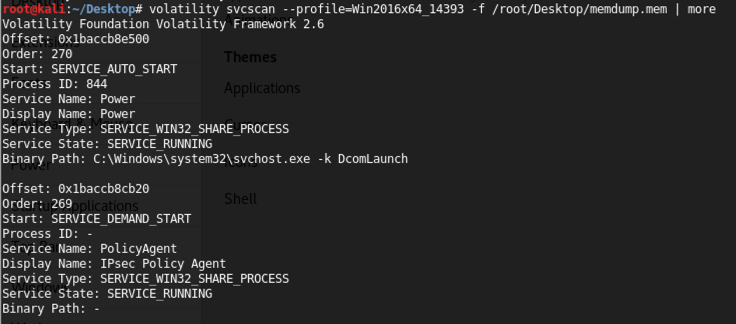
volatility svcscan --profile=Win2016x64_14393 -f /root/Desktop/memdump.mem | more
The file is 130,398,701 bytes in size, and its MD5 hash is 364fed484bcdd1a1f81a3538a4b1cd9a.
To unzip a .7z file in Kali, use "7z x filename"
volatility hivelist --profile=Win2008SP1x86 -f memdump.mem
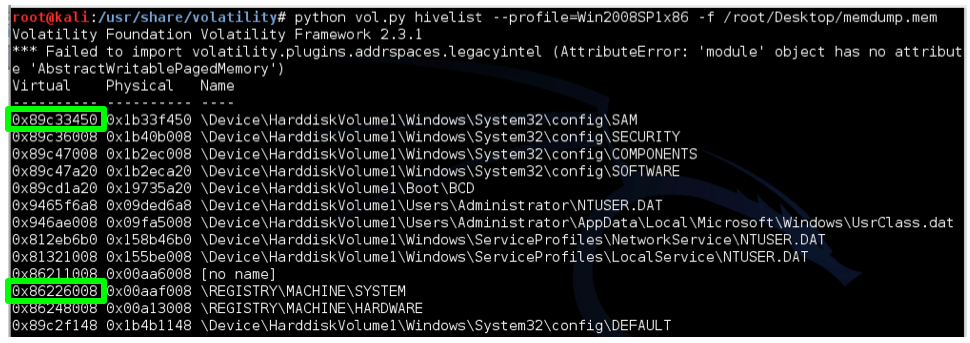
Examine your output and find the two addresses outlined in green above: the virtual addresses of the SAM and SYSTEM hives. Those two hives together contain enough information to extract Windows password hashes.
Notice that the two hexadecimal addresses you found above are used in this format:
-y SYSTEM -s SAM
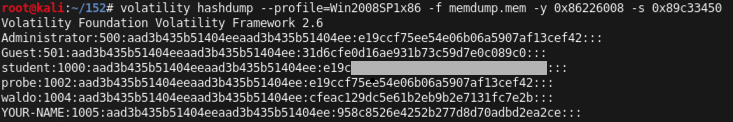
volatility hashdump --profile=Win2008SP1x86 -f memdump.mem -y 0x86226008 -s 0x89c33450
Windows stores two hashes with each password, delimited by colons. The first one is an extremely insecure, obsolete hash using the LANMAN algorithm. Windows operating systems since Vista no longer use LANMAN hashes, so they are filled with a dummy value starting with "aad".
The second hash is the newer NTLM hash, which is much better than LANMAN hashes, but still extremely insecure and much more easily cracked than Linux or Mac OS X hashes.
Use the form below to record your score in Canvas.
If you don't have a Canvas account, see the instructions here.
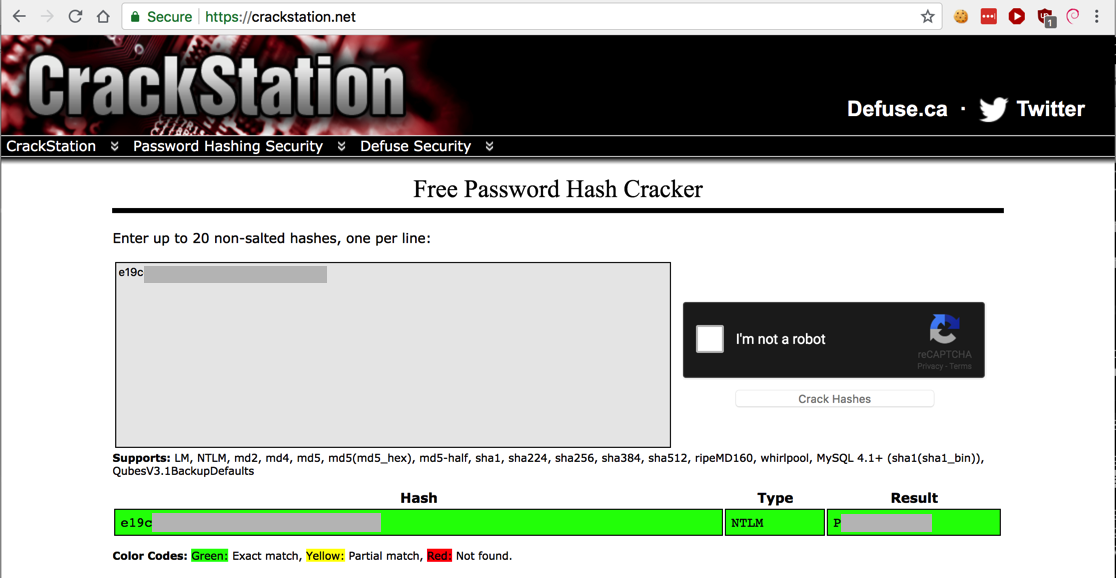
Paste in the hash. On the right side, fill in the CAPTCHA and click the "Crack Hashes" button.
The hash should crack, revealing the plaintext password, as shown below.
If you don't have a Canvas account, see the instructions here.
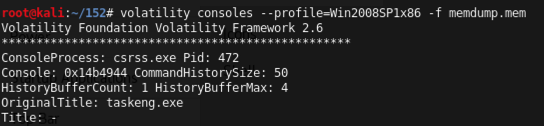
volatility consoles --profile=Win2008SP1x86 -f memdump.mem
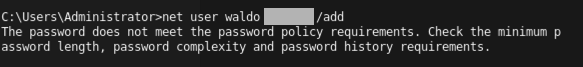
Find the "net user" command shown below, which attempted to set a password on the "waldo" account that violated the complexity requirement.
The password is redacted in the image below.
If you don't have a Canvas account, see the instructions here.
Memory Forensics and Analysis Using Volatility
SANS Memory Forensics Cheat Sheet
Basic Volatility Usage - An advanced memory forensics framework - Google Project Hosting