Project 2: SQL Injection (10 pts.)
What You Need
- Any computer with a Web browser
Purpose
SQL injection is the most important
vulnerability in the world. Over 90%
of all the stolen data has been stolen with
this attack.
Opening the SQL Hands-On Page
In a Web browser, open this page:
http://attack.samsclass.info/sqlol-raw/search-raw.htm
1. Reset the Database
In section 1 click the Reset button.
2. SQL Database Structure
Read through section 2 to understand
essential SQL concepts.
3. SQL SELECT Queries
SELECT queries find data
in the database and display it.
Try each of the queries shown and see how
they work.
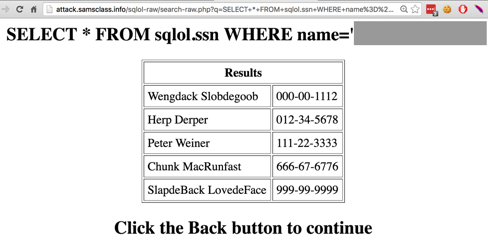
Try all the queries shown, and find one
that reveals social security numbers,
as shown below.
4. Search for Usernames
The form only accepts usernames, but by
using carefully-crafted usernames containing
apostrophes you can use it to perform
SELECT queries.
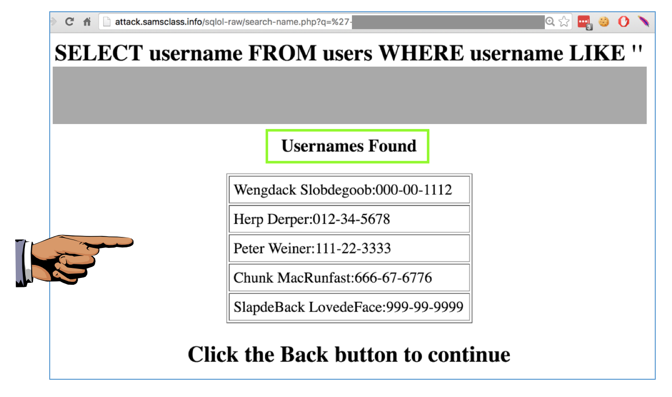
Try all the usernames shown, and find one
that reveals social security numbers,
as shown below.
Saving the Screen Image
Make sure social security numbers are
visible, and that the title of the table
is "Usernames Found",
as shown above.
Save a whole-desktop image
with a filename of "Proj 2 from YOUR NAME".
Turning In Your Project
Email the image to cnit.129s@gmail.com with a subject of
"Project 2 from YOUR NAME".
Last modified 8-14-16


