New RA Flood Attack
Killing Mavericks
Killing Lion
Windows 8.1 Survives!
Older Contents (2012)
- Killing Mac OS X and Windows Server 2012
- Microsoft's IPv6 Readiness Update
- Wireless: Injuring the iPad 3
- Killing Mac OS X Reliably with a better switch
- Wireless: Freezing the iPad Mini
- BayThreat 3 Talk
- Killing Mac OS X with a Crossover Cable
- Killing Mac OS X on a Wireless LAN
- Notifying Apple
- IPv6 Attack Kills MacBook Air & 3 iPads
- Freezing an Android Phone With an IPv6 Attack
- Google Notified
- Killing the Microsoft Surface with an IPv6 Attack
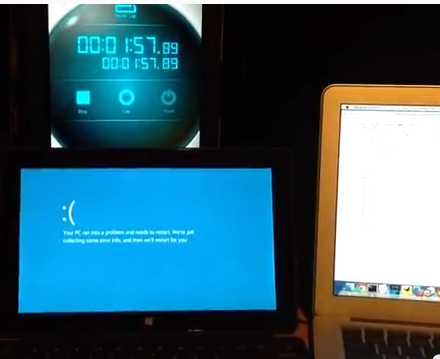
Killing the Microsoft Surface with a Wireless IPv6 Attack
This attack is realistic and practical, although somewhat
sloppy in concept. The attacker is a MacBook Air running
Backtrack in VMware, on a WPA-encrypted 802.11g network. The
target is a Microsoft Surface. Although the Mac is not immune
from this attack, under these conditions the attack does not
kill the Mac, but it kills the Surface.
You can get the attack script at http://pastebin.com/aXUxBXxk
To use it, first download and compile thc-ipv6-2.0.
BE GOOD--don't attack any devices without proper authorization.
Google Notified
I sent
this message to security@android.com:
Hello:
I have been studying IPv6 vulnerabilities for a few years, and they were a large problem for Windows but not for the Mac or Linux.
But with the recent release of thc-ipv6-2.0 that has all changed. The new RA flood tool freezes an Android device, as shown in the videos here:
http://samsclass.info/ipv6/proj/RA_flood2.htm
I think you should be aware of this. It might be good to block excessive RA packets with a firewall, or implement some other countermeasure.
--Sam Bowne
City College San Francisco
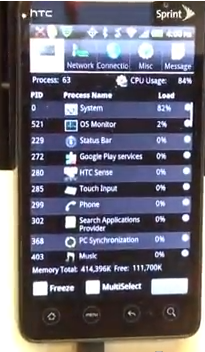
Freezing an Android Phone With an IPv6 Attack
A slightly modified version of the attack, used
on an Android phone. It also kills the Mac and
the iPad 1, all on a 2.4 GHz wireless network.
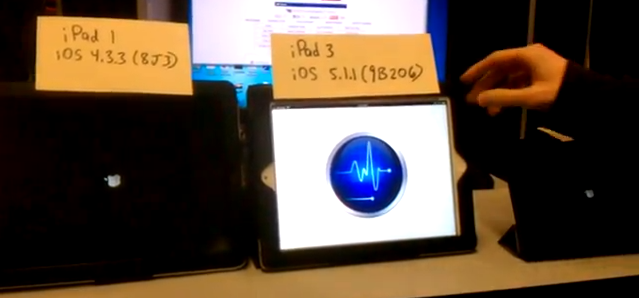
IPv6 Attack Kills MacBook Air & 3 iPads
This is an improved Router Advertisement flood attack: First it simulates ten normal routers, and then sends the new flood_router26 RA flood. That makes it much more effective against all Apple devices we have tried. As the video shows, it can now kill four devices at once via a wireless network.
Notifying Apple
The new version of the attack is powerful enough that
I decided to formally notify Apple. I don't expect them
to care much--Microsoft certainly didn't think this was
important to them, and Windows is much more vulnerable.
But I wanted to make sure they knew, so I sent
this message to product-security@apple.com:
Hello:
I have been studying IPv6 vulnerabilities for a few years, and they were a large problem for Windows but not for the Mac.
But with the recent release of thc-ipv6-2.0 that has all changed. It can bring a Mac down in seconds, as shown in the videos here:
http://samsclass.info/ipv6/proj/RA_flood2.htm
I think you should be aware of this. It might be good to block excessive RA packets with a firewall.
--Sam Bowne
City College San Francisco
Killing Mac OS X on a Wireless LAN
This is even more exciting: a wireless attack
powerful enough to kill the Mac. Just as
in the video below, six simulated routers
are sending router advertisements to the target
at one RA per second, and a seventh process sends
a flood of RAs. The Mac dies in seconds.
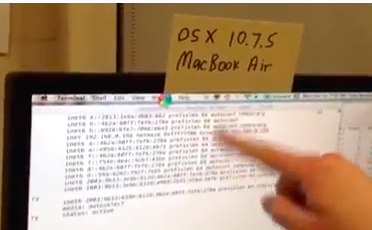
Killing Mac OS X with a Crossover Cable
This is a major advance in the attack: the essential
ingredient is routers on the network, not a fast flood.
With six simulated routers and one process running the
flood, the Mac OS X dies in seconds reliably, even in a
very simple network consisting of a crossover cable.
This makes the attack MUCH more practical than the one
I demonstrated at BayThreat, which required an expensive
and bulky switch and a separate router.
Data Breaches and Password Hashes WITH the New IPv6 RA Flood Attack
This is a talk I gave at BayThreat 3. First I discuss other
issues, then I gave a live demo of the IPv6 attack
killing Mac OS X and Windows 8, which WORKED, thanks
to K. Yang who set it up and was extremely
helpful designing and performing the attack.
The IPv6 attack starts in Part 2.

Videos:
Part 1
Part 2
Part 3
Wireless: Freezing the iPad Mini
The iPad Mini is more vulnerable than the
iPad 1 or the iPad 3, as shown in this
video. But adding a second iPad
to the wireless LAN reduces the attack
effect greatly. This is interesting because
it's the opposite of what we see in a
wired network, where adding a router to the
LAN is necessary to kill the Mac OS X
reliably.

Killing Mac OS X Reliably with a better switch
We used a business-class Gigabit switch, a Vyatta
router on the LAN, and a Gigabit adapter on the Mac OS X.
This kills the Mac OS X reliably, showing a crash of
the Ethernet adapter so it stops configuring addresses,
followed by the whole OS freezing.

Wireless Attack on iPad 3
We finally got a wireless version of the
attack working. It isn't powerful
enough to kill any device we tested
reliably, but it makes the iPad 3 run
slowly and some apps crash, and the
whole OS crashes sometimes.
The other devices we tested were
Windows 8, iPad 1, and MacBook Air.
They all slowed down during the attack,
but remained usable. The iPad 1 was
the most resistant to this attack,
all it did was consume about 10% - 20%
of the CPU, making no significant difference
in its performance.
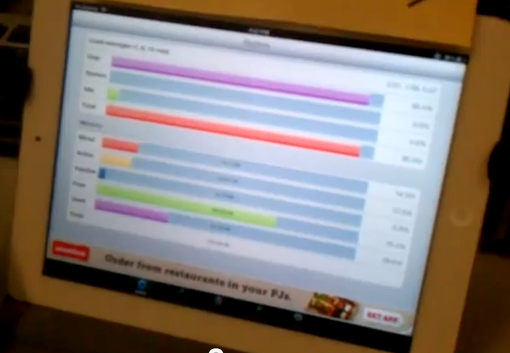
Posted 11-30-12
Microsoft's IPv6 Readiness Update
Microsoft's IPv6 Readiness Update greatly
alleviates this vulnerability:
http://support.microsoft.com/kb/2750841
However, it's only available for Win 7 and Win Server 2008 R2.
In addition, it only provides partial protection:
a patched machine freezes totally during the attack,
but recovers quickly when it stops. It is possible
to do better--Ubuntu Linux completely shrugs off the
attack, adding a few new IPv6 addresses
and showing no deleterious effect at all.
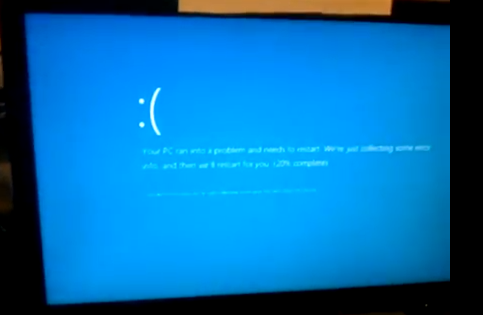
Here's a video showing the attack killing
Windows 8, Server 2008, and Mac OS X:
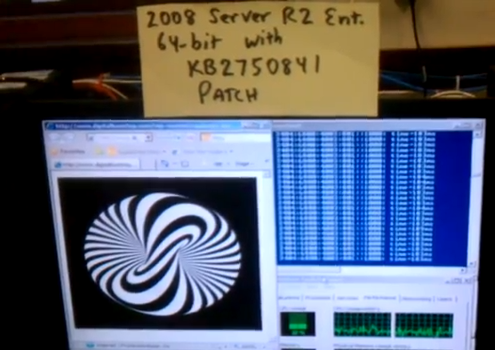
Here's a video showing the extent to which
the Microsoft IPv6 Readiness Update
protects Windows 7 and Server 2008 R2.
It also shows the attack's effect on Windows
XP and Ubuntu Linux.
Details of an earlier test using virtual machines are
here.
Killing Mac OS X and Server 2012
We tested the new attack from Marc Hause,
and it is MUCH more powerful. It kills
Mac OS X and Server 2012 in a few seconds,
as shown in the video below:
How it Works
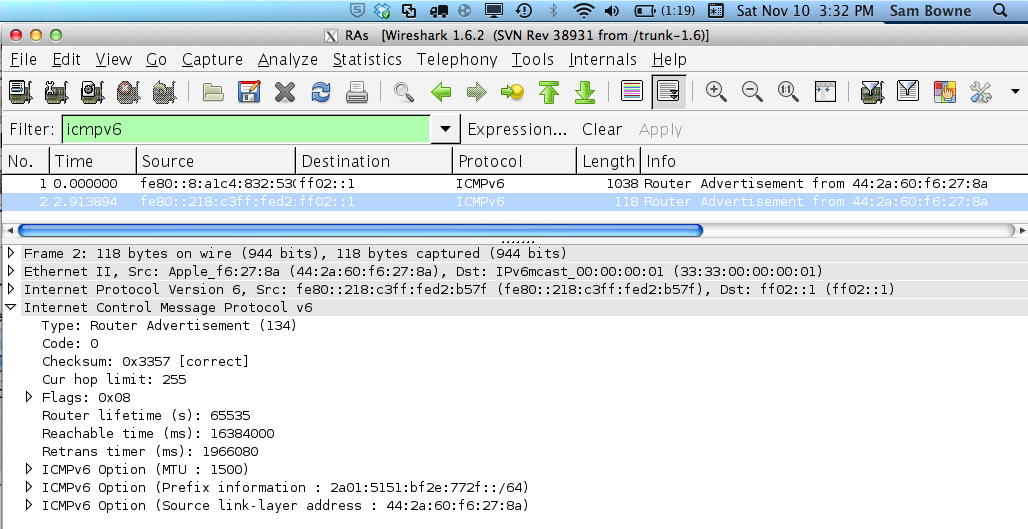
Here is a captured
packet from the previous, weaker attack
that the flood_router6 tool uses.
It's a normal RA, with these ICMPv6
Options:
- MTU
- Prefix Information
- Source link-layer address
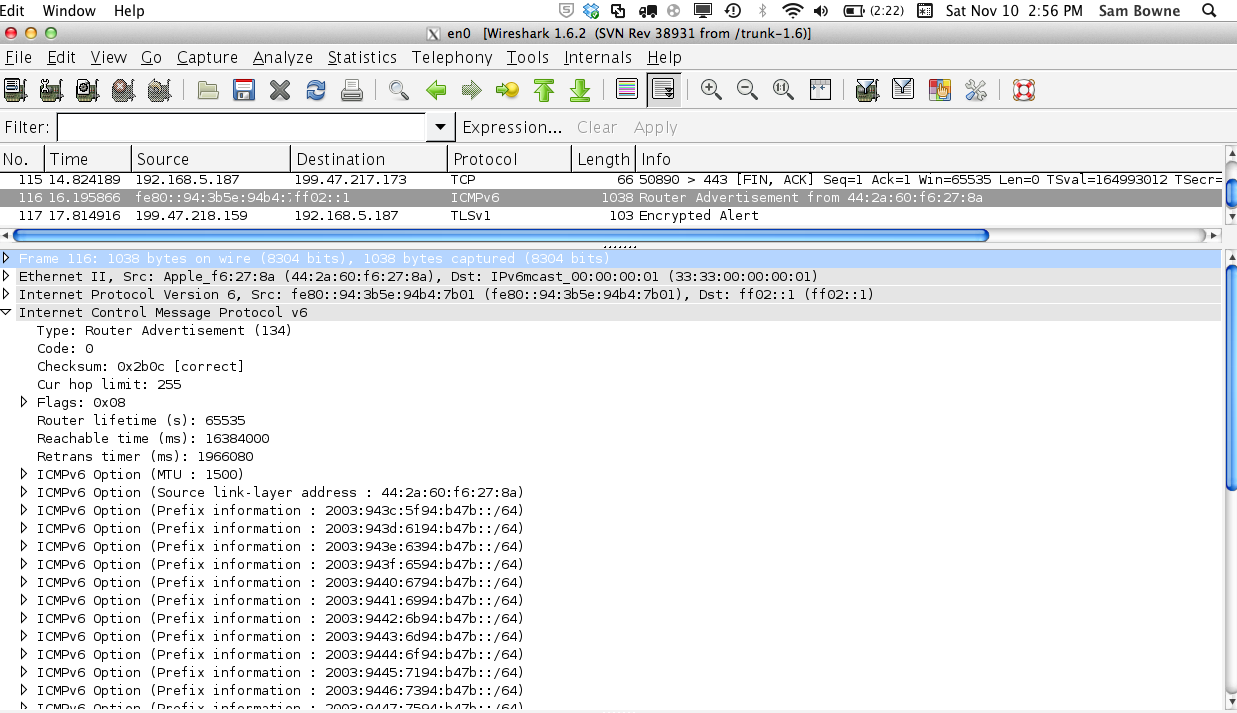
Here's a captured packet from the newer
attack, shown in two images because
it's too big to fit in one.
It's a normal RA, with these ICMPv6
Options:
- 17 Route Information sections
- 18 Prefix Information sections
- 1 Source link-layer address
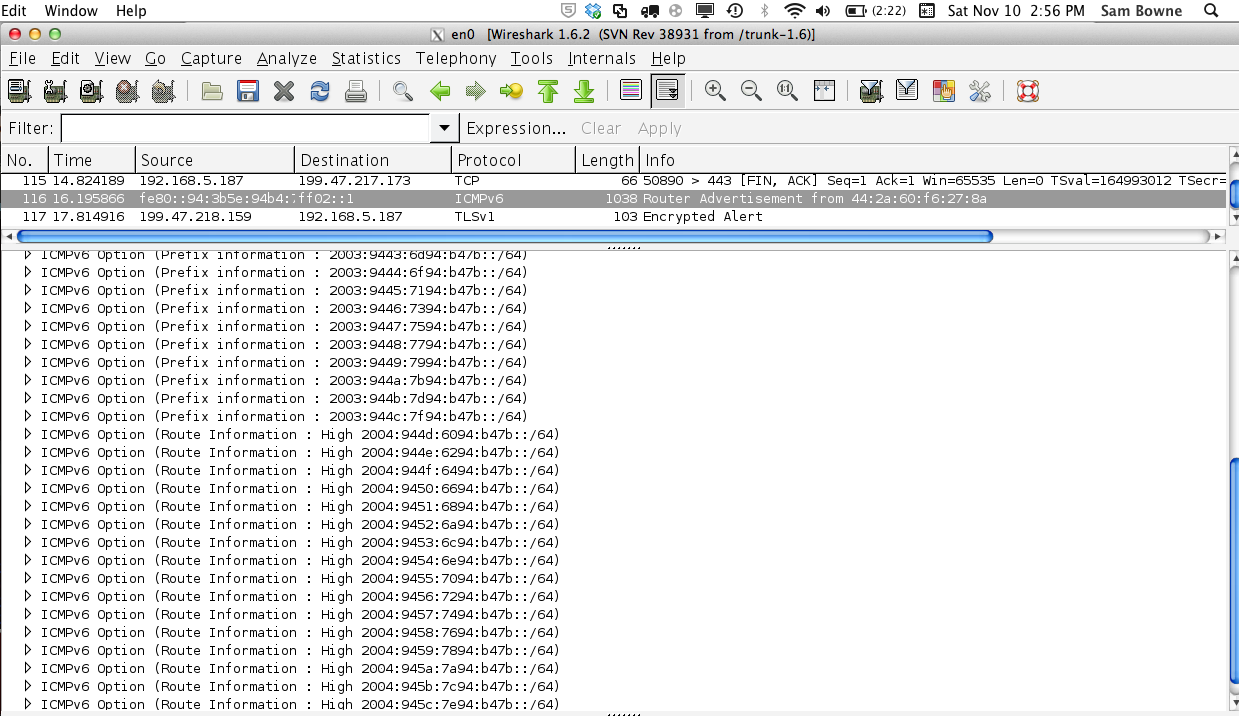
So each packet burdens the recipients a lot
more.
I think Microsoft and Apple need to pay attention
this time, because this one crashes the Mac, and it makes Server 2012 restart, which makes me suspect it could be exploited further, perhaps into a remote code execution attack.
Packet Captures
Here is a PCAP file with one new RA and one
of the old type:
RAs.pcap
References
My previous page about the old attack, with mitigation recommendations:
http://samsclass.info/ipv6/proj/flood-router6a.htm
Marc Hause's slides presenting thc-ipv6 version 2
http://conference.hitb.org/hitbsecconf2012kul/materials/D1T2%20-%20Marc%20Heuse%20-%20IPv6%20Insecurity%20Revolutions.pdf
Step-by-step instructions for testing the older tool
http://samsclass.info/ipv6/proj/projL9-flood-router.htm
First posted: 7:30 am 11-20-12 by Sam Bowne
Page reorganized with Contents section 11-30-12 10:36 am
New videos 4 and 5 added 12-5-12
BayThreat Videos added 12-8-12 11:19 pm
Attacks on the Mac OS X with simulated routers added 7:45 pm, 12-10-12.
Apple notified 12-11-12
3 iPads video added 11:37 PM 12-11-12
Android attack and Google notification added 4:36 PM 12-12-12
Microsoft Surface attack added 7 am 12-15-12
Mavericks & Win 8.1 added 11-12-13



