
https://visualstudio.microsoft.com/visual-cpp-build-tools/
Click the "Download Build Tools" button, as shown below.

On the next page, in the "Build Tools for Visual Studio 2017" section, click the Download button, as shown below.
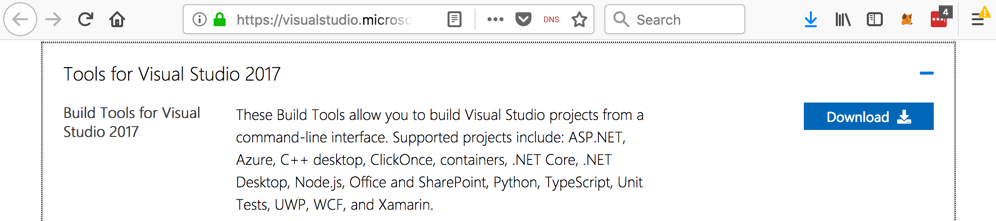
Save the vs_buildtools__935747363.1537797301.exe file in your Downloads folder.
Double-click the the vs_buildtools__935747363.1537797301.exe file.
A box pops up, as shown below.
Click Continue.
Wait while software downloads and installs, as shown below.
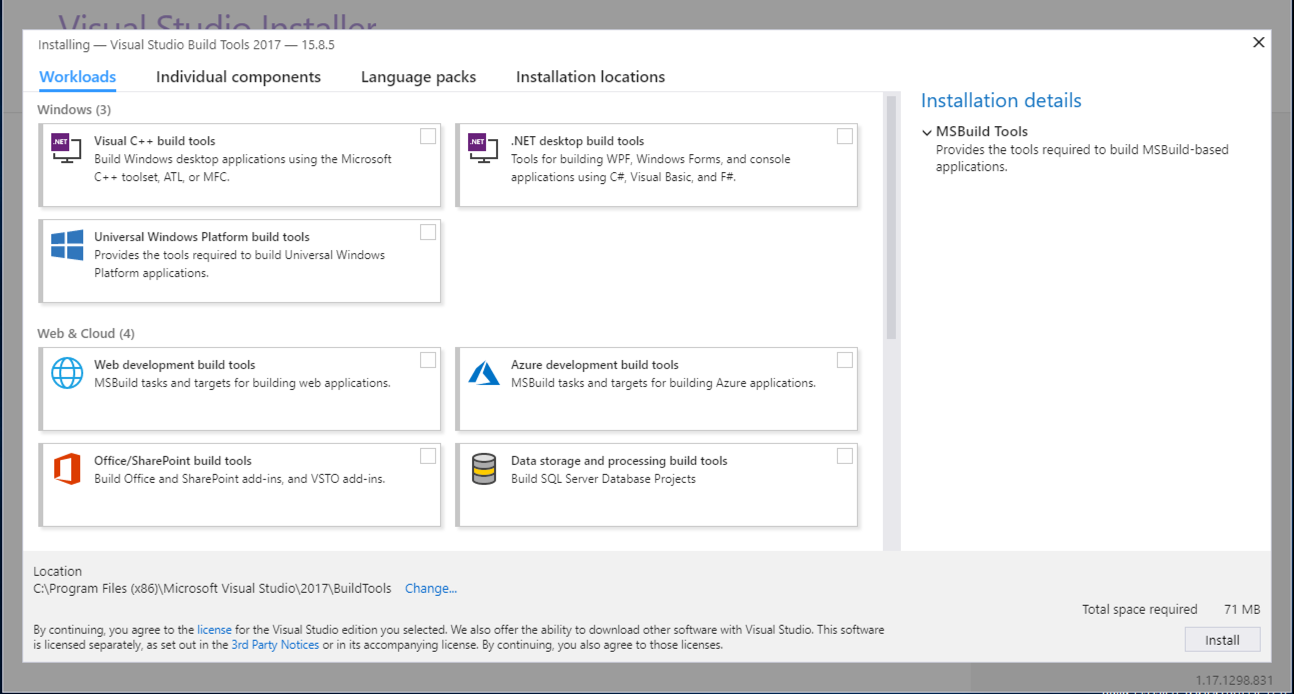
A large window appears, as shown below.
At the top left, click "Visual C++ build tools".
Click the Install button.
Wait while software downloads and installs., as shown below. When I did it on the Google cloud, it took about ten minutes.
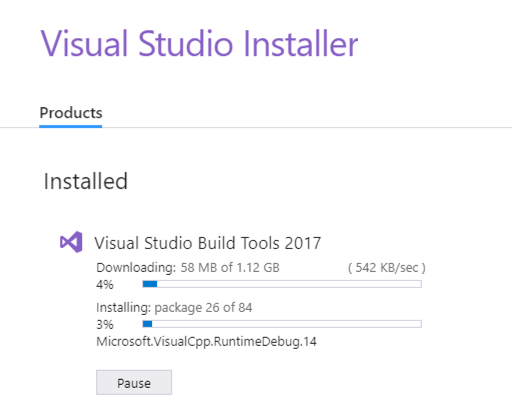
When the installation completes, you should see the screen shown below.
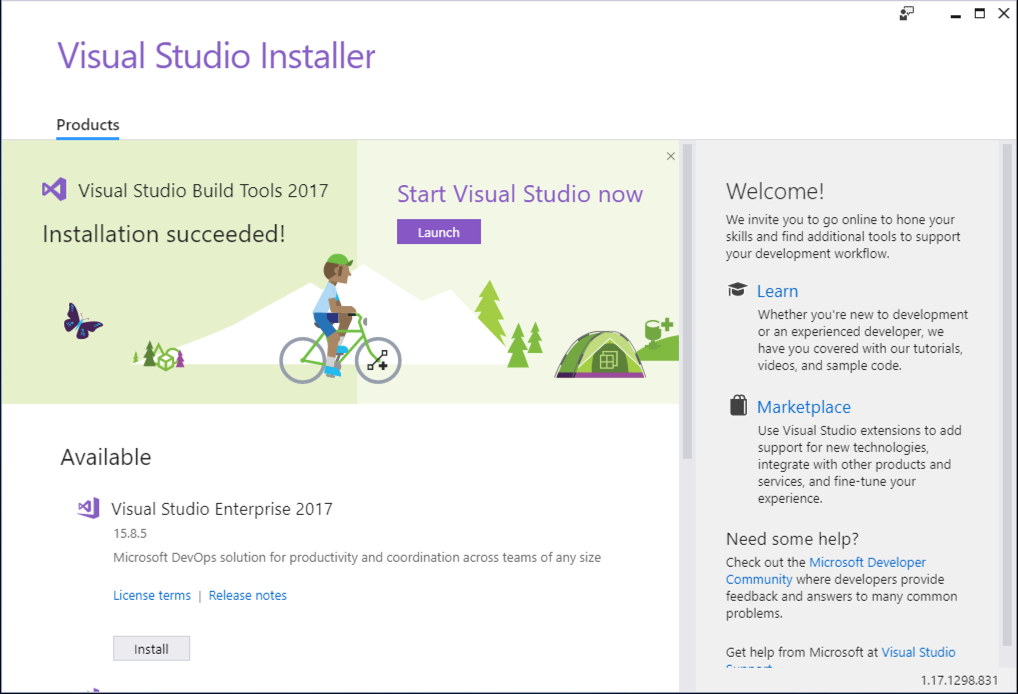
In the upper center of the window, click the purple Launch button. A Developer Command Prompt window opens, as shown below.
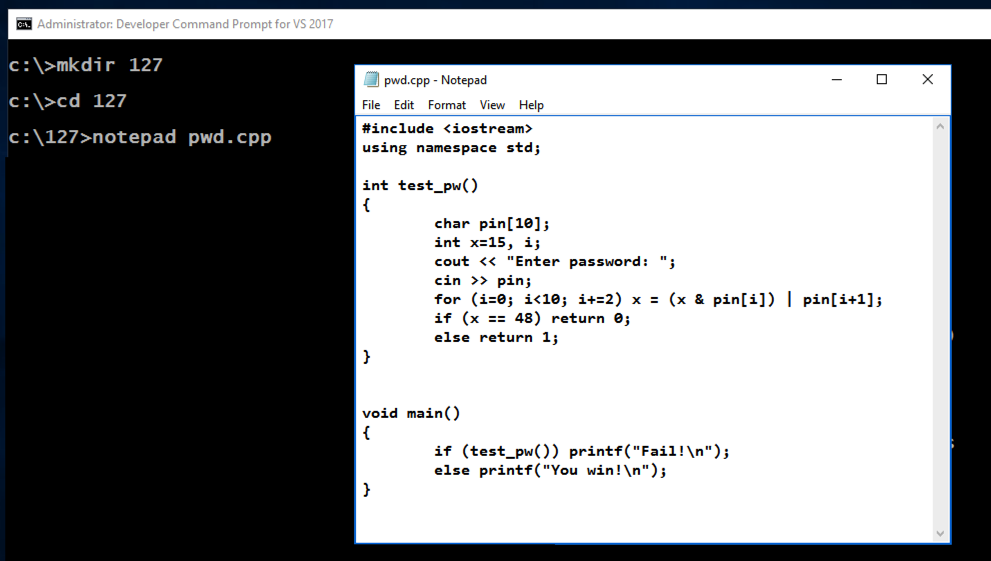
mkdir c:\127
cd c:\127
notepad pwd.cpp
Enter this code, as shown below:
#include <iostream>
using namespace std;
int test_pw()
{
char pin[10];
int x=15, i;
cout << "Enter password: ";
cin >> pin;
for (i=0; i<10; i+=2) x = (x & pin[i]) | pin[i+1];
if (x == 48) return 0;
else return 1;
}
void main()
{
if (test_pw()) printf("Fail!\n");
else printf("You win!\n");
}
In Notepad, click File, Save.
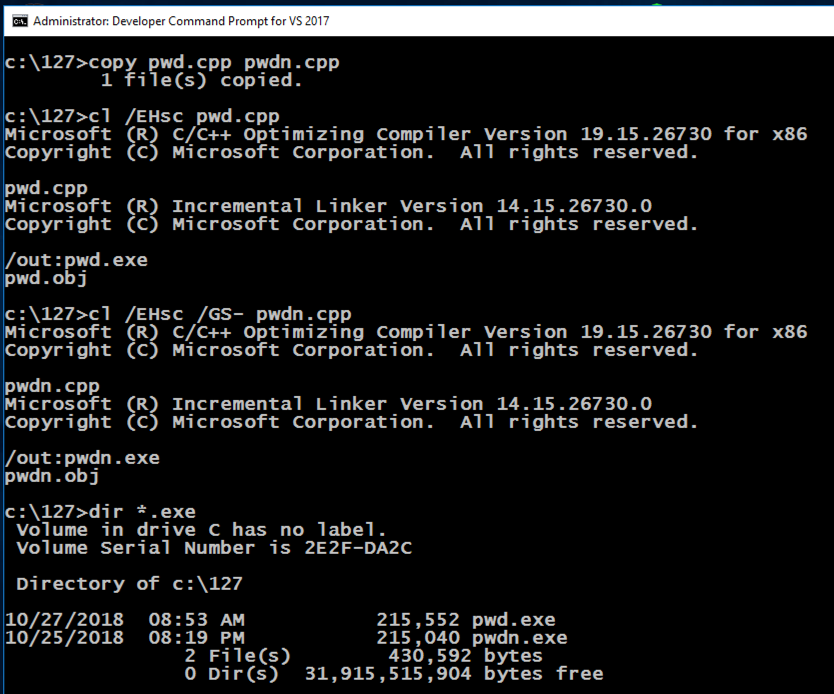
In the Developer Command Prompt window, execute these commands:
copy pwd.cpp pwdn.cpp
cl /EHsc pwd.cpp
cl /EHsc /GS- pwdn.cpp
dir *.exe
https://www.hex-rays.com/products/ida/support/download_freeware.shtml
Click the "IDA Freeware for Windows" link, as shown below.
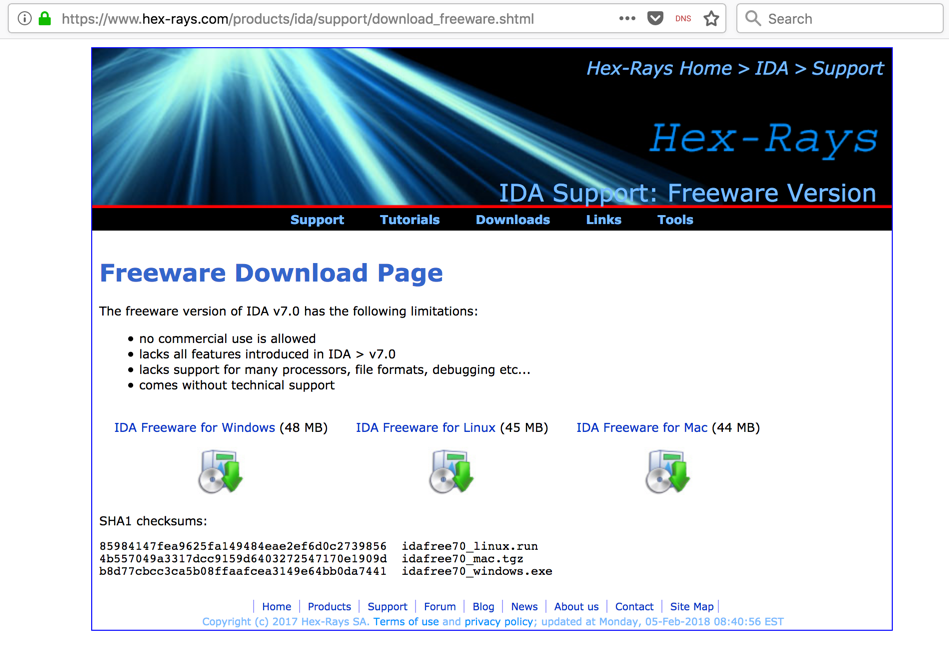
Install the software with the default options.
In the "IDA License" window, click the "I Agree" button.
In the "IDA: Quick start" box, click New, as shown below.

Navigate to the C:\127\pwd.exe file and double-click it.
In the "Load a new file" box, click OK.
IDA opens, showing some assembly code, as shown below.
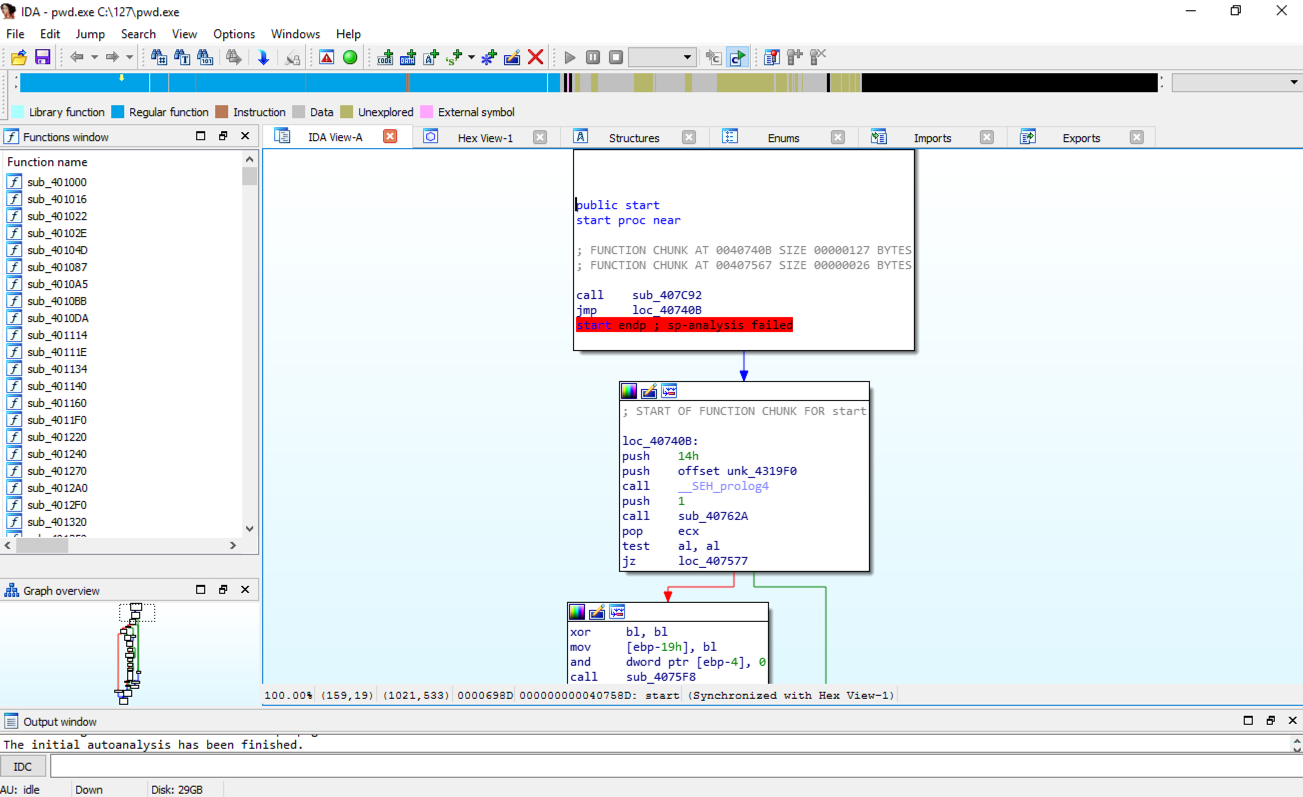
From the IDA menu, click View, "Open subviews", Strings.
Double-click "Enter password", as shown below.
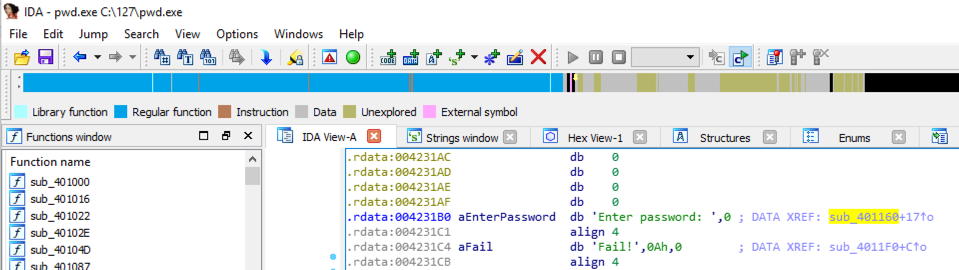
The .rdata section appears, showing stored strings. On the line containing "Enter password", find "DATA XREF". Point to the address after the "DATA XREF" marker, as highlighted in yellow in the image below, and double-click it.
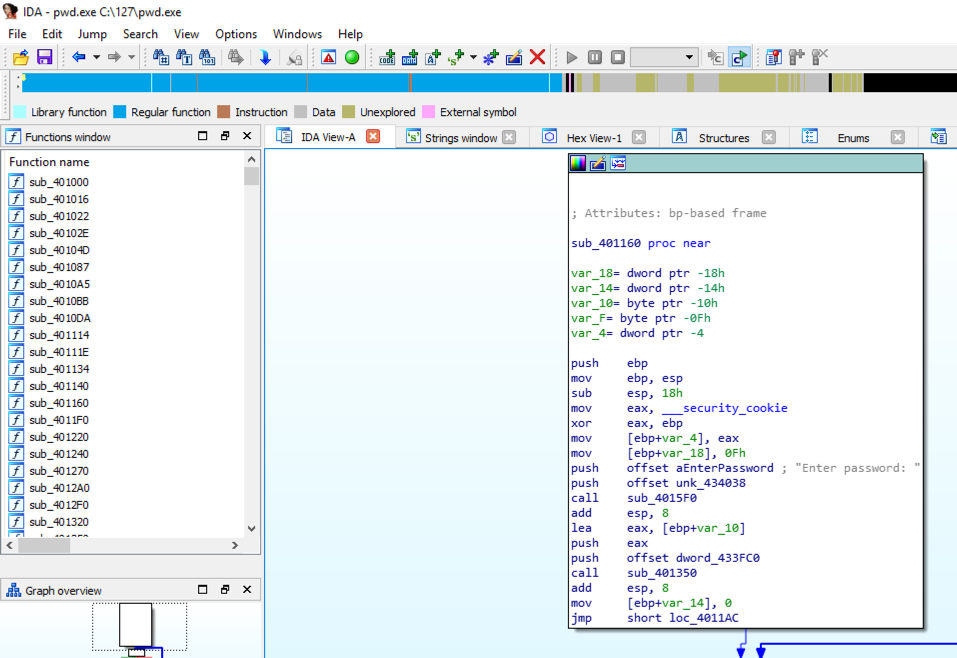
The function prologue appears, with a line containing "security_cookie", as shown below.
The security_cookie is placed on the stack to prevent buffer overflow attacks.
In the "Save database" box, click "DON'T SAVE the database", as shown below. Click OK.

In the "Select a file to disassemble" box, double-click pwdn.
In the "Load a new file" box, click OK.
IDA opens, showing some assembly code.
From the IDA menu, click View, "Open subviews", Strings.
Double-click "Enter password".
The .rdata section appears, showing stored strings. On the line containing "Enter password", find "DATA XREF". Point to the address after the "DATA XREF" marker, and double-click it.
The function prologue appears.
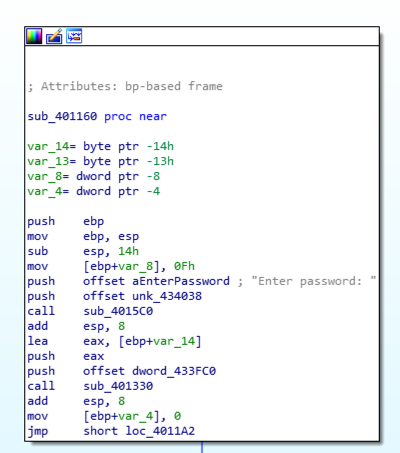
The "security_cookie" line is gone, as shown below. This executable was compiled without stack protectors.
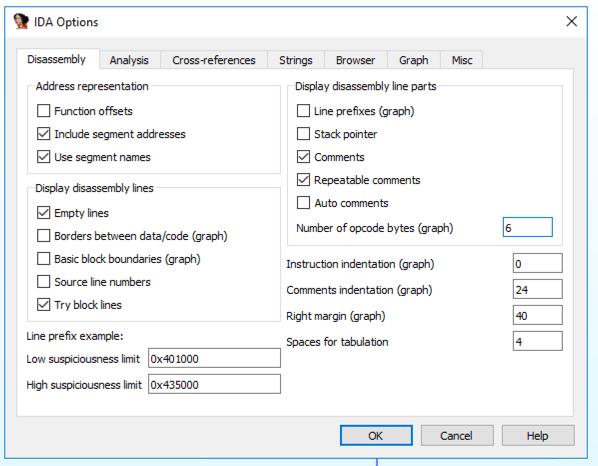
Enter a "Number of opcode bytes" of 6 as shown below. Then click OK.
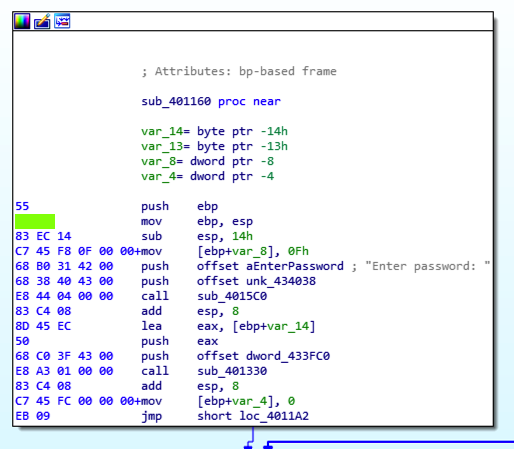
Find the hexadecimal values covered by a green box in the image below. Enter them into the form below to record your success.
Posted: 12-31-18