However, I did not believe that, and I did it anyway. Everything was fine. The high-profile companies, universities, and government agencies I contacted were polite and thankful.
My students and I have also contacted hundreds of small businesses to warn them of SQL injection vulnerabilities, and although most of them ignore the notifications, all the replies we got were friendly and grateful.
But last week my luck ran out.
"Web Site by Websmart Inc."I wondered if the other sites from this developer were also vulnerable, and indeed they are--more than 100,000 of them.
So I sent this notification to the administrators of eleven vulnerable sites, and to the developer.
To: info@websmartconsulting.com, kincardine@sunsets.com, farm@hiberryfarm.com, info@bruceanchor.com, clerk@town.southbruce.on.ca, office@shorelinechurch.ca, bill.walkerco@pc.ola.org, pemc@bmts.com, office@ebelquarries.comPosted via comment form to:
http://www.560cfos.ca/contact.php
http://www.oceanfrontier.com/contact.php
http://bruceanchorcruises.com/contact.php
Re: Insecurity of Websites from Websmart, Inc.
Hello:
I am Sam Bowne, an instructor in Computer Networking and Information Technology at City College San Francisco.
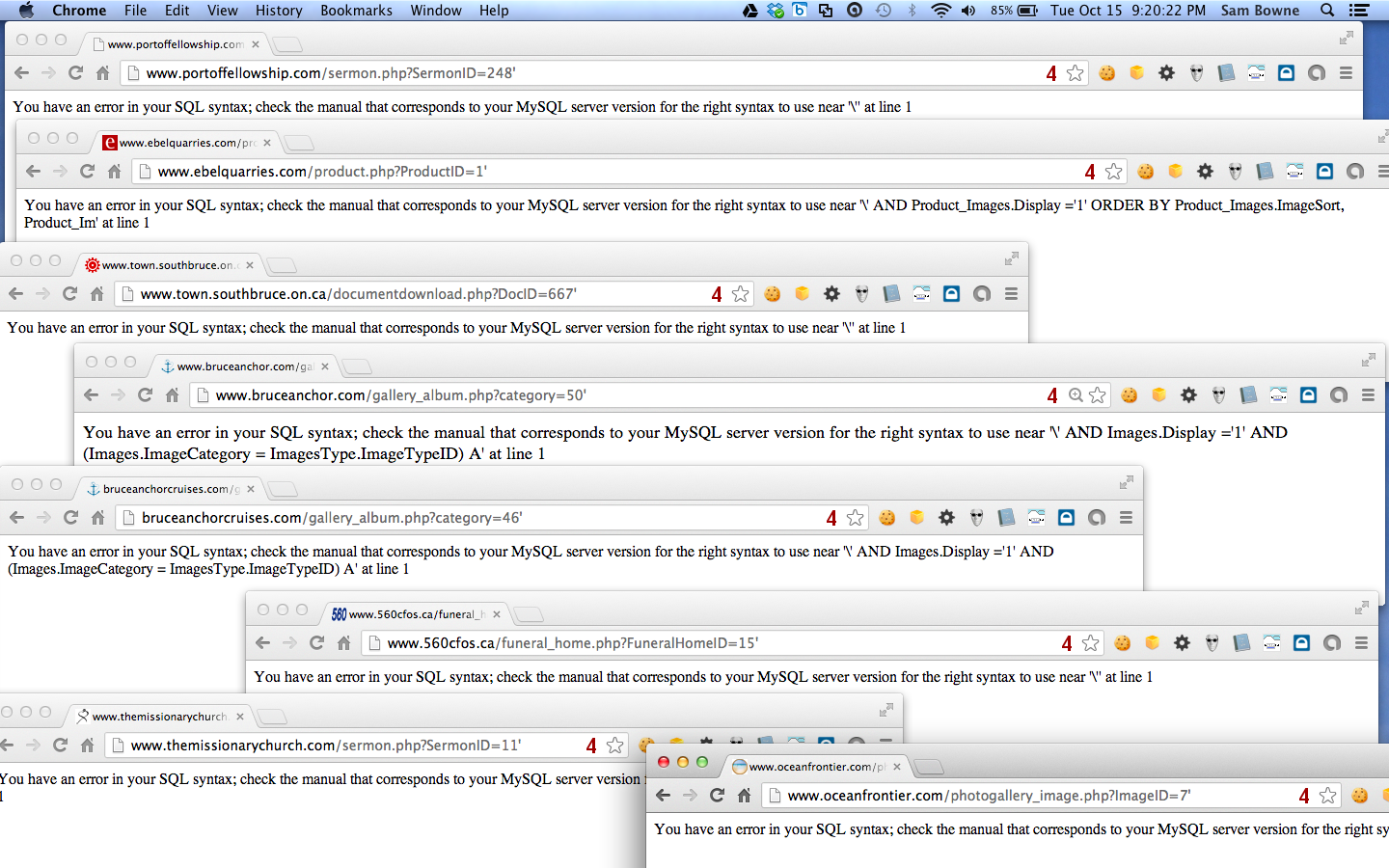
I am writing this to inform Websmart, Inc. and several of its customers, of a critical security vulnerability in many of Websmart's websites. In particular, all these sites are vulnerable to SQL injection:
http://www.sunsets.com/kincardine/picture.php?ID=69'
http://www.hiberryfarm.com/recipe.php?RecipeID=11'
http://www.bruceanchor.com/gallery_album.php?category=50'
http://www.560cfos.ca/funeral_home.php?FuneralHomeID=15'
http://www.town.southbruce.on.ca/documentdownload.php?DocID=667'
http://www.portoffellowship.com/sermon.php?SermonID=248'
http://www.oceanfrontier.com/photogallery_image.php?ImageID=7'
http://billwalkermpp.com/gallery_album.php?category=51'
http://bruceanchorcruises.com/gallery_album.php?category=46'
http://www.ebelquarries.com/product.php?ProductID=1'
http://www.themissionarychurch.com/sermon.php?SermonID=11'
I tested 14 Websmart websites, and 11 of them were vulnerable.
Google found over 100,000 pages made by Websmart, Inc., so this is an enormous problem affecting many businesses and customers.
These are all SQL Injection vulnerabilities, which make it trivial for any amateur hacker to steal your data, and often allow a hacker complete control of your servers.
Because of the number of websites affected, I don't think I can ignore this. This is by far the most important security problem I have ever discovered. So, please reply to this message and let me know what you intend to do. If I get no reply by October 12, 2013, I will pursue more drastic remedies, such as contacting news media.
The technical details of the problem, suggested fixes, and the method I used to find it are in the Appendix.
Please contact me to let me know what you intend to do about this. If you have any questions, I would be happy to address them.
Thank you,
Sam Bowne
sbowne@ccsf.edu
Website: samsclass.info
------------------
APPENDIX:
Today I saw this document on Pastebin, listing vulnerable websites:
http://pastebin.com/AWixyyNs
The first website on that list is indeed vulnerable:
http://www.sunsets.com/kincardine/picture.php?ID=69'
I saw the message at the bottom saying "Web Site by Websmart Inc.", so I searched for sites with that label and Google found 116,000 hits:
https://www.google.com/search?q=Web+Site+by+Websmart+Inc.#q=%22Web+Site+by+Websmart+Inc.%22
I examined the first 20 hits with these results:
11 vulnerable
3 not vulnerable
6 duplicates
It is very simple to patch this flaw. Even a single statement like this helps a lot:
$q = mysql_real_escape_string($q);
Here is the homework assignment I give my students explaining the vulnerability, an attack tool, and the easiest patch:
http://samsclass.info/124/proj11/p20-123-Havij-fix.html
A better fix is to use parameterized queries, as explained here:
http://samsclass.info/124/proj11/pSQL-X4-123-pq.htm
owen@websmart.ca via srs.bis6.us.blackberry.com 9:06 PM (11 hours ago)
to meMr Bowne
I appreciate your observations and information, and we will look into this. Thank you for bringing this to our attention. Of course this is something we are concerned about.
I do not appreciate you taking the liberty of contacting my clients directly. This is highly unprofessional. I do not appreciate your 'ultimatum" - nor your scare tactics that no doubt will have an impact our customers. I am very tempted to notify your superiors of this misconduct.... you have no right or authority here. You could very well damage my business with this . If that happens you will be hearing from our lawyer.
Any further correspondence on this matter may be directed to me and me alone. Like I said, I appreciate your information.... I really do, but contacting my customers directly is way out of line and I believe well outside of your mandate with your employer.
Thank you.
Owen Smart
President
Websmart Inc.
So I sent this to a Canadian reporter and two American reporters, thinking that they might contact Owen Smart and put pressure on him to fix his defective products, or to notify his customers. But two of the reporters completely ignored my notice, and the third one said I was morally wrong for not practicing responsible disclosure and working with the vendor.
I was amazed at that accusation, and decided to seek advice from some respected infosec professionals.
One of them forwarded my query to a huge corporation's security division, and they recommended that I try to sweet-talk the vendor into being nice and working with me.
Although I had grave doubts that this would work, I sent this message, following that advice.
Sam Bowne <sam.bowne@gmail.com>
to: owen@websmart.ca
date: Thu, Oct 10, 2013 at 9:18 AM
subject: Re: Insecurity of Websites from Websmart, Inc.
mailed-by: gmail.com
Mr. Smart:
I'm happy that you responded so quickly to my vulnerability report, and I'm sorry if I came across as threatening in any way -- it was not my intention. However, I think we got off on the wrong foot and I'd like to move forward with what we both want, which is to get these issues addressed as quickly as possible.
As far as informing your customers, I felt it was reasonable, given the fact that they have active vulnerabilities that could be impacting their own businesses and were in more direct risk of attack than your company.
Let's move forward cooperatively and work to get these issues resolved. As I mentioned, I'm happy to answer any questions you have about the vulnerabilities, and I'd be willing to test the fixes if that would help.
Looking forward to working with you cooperatively.
--Sam
Owen Smart <owen@websmart.ca> via ccsf.edu
to: Samuel Bowne <sbowne@ccsf.edu>
date: Thu, Oct 10, 2013 at 12:17 PM
subject: Fwd: Re: Insecurity of Websites from Websmart, Inc.
mailed-by: ccsf.edu
: Important mainly because of your interaction with messages in the conversation.
Dear Mr Bowne
Someone has been emailing my clients and myself, essentially interfering in my business - claiming to be you. Please see the email below.
I want to confirm whether this is legitimate and if this is really coming from you Sam Bowne. As this has been highly unprofessional, I sincerely hope it is just a bad prank.
Please advise.
Thank you
Owen R. Smart
President, Websmart Inc.
From: Owen Smart <owen@websmart.ca>
Date: Thu, Oct 10, 2013 at 2:47 PM
Subject: Sam Bowne
To: REDACTED
Hello REDACTEDI understand you are the Department Chair for COMPUTER NETWORKING AND INFORMATION TECHNOLOGY DEPARTMENT at City College of San Francisco?
Would you be the supervisor or authority for Mr. Sam Bowne?
I need to speak/email someone at the college to file a complaint regarding Mr. Bowne's conduct as it pertains to our business, since he is using the college's name as part of his activities.
Please advise.
Thank you
Owen Smart
---------------------------------------------------------------------------
Owen R. Smart
President, Websmart Inc
www.websmartconsulting.com
************************ NEW CONTACT INFORMATION *****************************
Websmart Inc.
P.O. Box 936
CARONPORT, SK S0H 0S0
1-888-388-3982 1-306-690-1069
*****************************************************************************
Can Owen Smart possibly think that I need his permission to send emails to his customers, or to anyone else I want to? Does he think he has any conceivable case against me in court? Does he imagine that I am subject to Canadian law anyway?
My working hypothesis is that bullies do actually believe this stuff, because they have been demanding unreasonable things for so long, they have hypnotized themselves into imagining that their delusions of power and rightousness are based in fact.
In any case, it is clear that the advice I got was incorrect. This man is a thug, and nice treatment just indicates weakness and results in further abuse, as I originally thought.
But what is the correct next step? I could just post the whole thing on my website, but that would reveal this problem to criminals who would might hack these 100,000 clueless customers. Full disclosure, I thought, could create the very disaster I wanted to avoid.
A better plan would be to email more of his customers. That would alert the people who are at risk without informing the criminals who might hack them.
My first email disclosure did have some effect--three of the eleven sites were fixed within a few days, although the remaining eight are still vulnerable as of Oct 15, 2013. That's consistent with my previous experience--a small fraction of sites notified about SQL injections do fix them, and very few of them reply to the notice.
I have never attempted to send 100,000 emails. But I have sent 100 or 200 at a time through Gmail, and I could script it. But would it really do any good? And would I be guilty of an offense under the CAN-SPAM act?
I had another idea--to try to mine the list of 100,000 victims and find government sites or colleges, who might be more responsive.
So I did several more Google searches, trying to find the best people to contact. And this is what I found.
According to this page, it was posted on 2010-07-08: http://inj3ct0rs.com/1337day-2010-13244
Material's title: Websmart XSS/SQL Injection Vulnerability
Category: web applications
Platform: php
======================================== Websmart XSS/SQL Injection Vulnerability ======================================== __ __ .----..--.--.| |--..-----..----.| |.-----..-----. | __|| | || _ || -__|| _|| || _ || _ | |____||___ ||_____||_____||__| |__||_____||___ | |_____| |_____| #################################################### # websmart SQL Injection Vulnerability [ Multiple Vulnerabilities ] #################################################### # Vendor: http://www.websmartconsulting.com/ # Discovered by : cyberlog # Site : Sekuritionline.net # Channel : #SekuritiOnline [ Now Just My Bot ] # Dork : " Web Site by Websmart Inc Or Visit http://www.websmartconsulting.com/portfolio.php " # Exploit : [site]/page.php?PageID= [SQL Injection] [site]/news_item.php?NewsID= [SQL Injection] [site]/display.php?PhotoID= [SQL Injection] [site]/portfolio_profile.php?ClientID= [SQL Injection] [site]/news_item.php?NewsID= [SQL Injection] [site]/photogallery_full.php?ImageTypeID= [SQL Injection] [site]/gallery_album.php?category= [SQL Injection] # XSS/HTML Injection : [site]/page.php?PageID= # Thanks : r0073r,adhietslank, k1n9k0ng, cr4wl3r,cah_gemblunkz, jayoes,thesims,setiawan,irvian,EA_Angel,BlueSpy,SoEy,A-technique,Jantap,KiLL,blindboy,sukam, SarifJedul,wiro gendeng,Letjen,ridho_bugs,Ryan Kabrutz,Mathews,aurel666,Inoef,dbanie, # special to Mama Sri Rahayu, Member& Staff Sekuritonline, C0li a.k.a antisecurity [ pinjem script perl-na ] , # Hiroyuki Doni thanks to create New design SO T-shirt P # Inj3ct0r Now Brothers with Sekuritionline #################################################### # Demo: # http://localhost/display.php?PhotoID=[SQL Injection] # http://localhost/display.php?PhotoID= #################################################### We never die !!!! indonesian Underground Community !!!!! anjing buat oknum Pemerintah yang suka nilep uang rakyat !!! !!!!! anjing juga buat admin site indon3sia yang merasa sok h3bat, dikasih tahu ada hole malah nyolot !!!!! KacrUt I h@te U [ jika kau tidak mau aku katakan LOv3 ] Give me NOCAN Brothers am nt hacker just Lik3 Syst3m S3curity .-----..-----.| |--..--.--..----.|__|| |_ |__|.-----..-----.| ||__|.-----..-----. |__ --|| -__|| < | | || _|| || _|| || _ || || || || || -__| |_____||_____||__|__||_____||__| |__||____||__||_____||__|__||__||__||__|__||_____| # 1337day.com @ http://1337day.com/
http://www.securityhome.eu/exploits/exploit_pdf.php?eid=16497725684c3604584c7c67.88077932Another from June, 2012
http://pastebin.com/c5WEysGz
And telling the truth is legal in the USA, anyway.
Here are some things I have observed so far.
Perhaps they are of such low value that no criminal cares, but I'd have thought someone would use them for political propaganda, or to add them to botnets, or to send spam, at least. And I still think that is their inevitable fate, but it is strangely slow in coming.
But the people I contact are small businesses, apparently clueless about security, and I am just an unwelcome pest to them. I am just a meddling do-gooder, and they naturally wish I would just shut up and go away.
My own experience in judging the significance of the reactions I get seems more accurate than the wisdom of professionals, because what I am doing is different.
And the press doesn't care. This is not a new, sexy exploit; just an old stupid problem no one has bothered to clean up yet, like gum on the sidewalk.
It would be really nice to decrease the number of vulnerable pages on the Internet. I may notify more of WebSmart's victims--if I do, I will update this page.
If anyone has helpful ideas, please tell me:
Twitter: @sambowne
Email: sam.bowne@gmail.com
To: info@977thebeach.ca info@bruceanchor.com info@greycountyrealestate.com info@saugeenrailtrail.com info@sunshine89.ca sales@chatsworthmotors.ca office@ackertconstruction.com office@debtontario.com office@frontierloghomes.ca office@kingstonwestfmc.ca office@broughandwhicher.com office@debtontario.com inquiry@ackertinsurance.ca rentals@amethystcottages.com thebeach@1049thebeach.ca tcumming@abca.on.ca lhcrstaff@hurontel.on.ca publicinfo@svca.on.ca hernandezo@saugeenshores.ca publicinfo@svca.on.ca terryarnold@casualtycare.com gplantphoto@yahoo.com saugeenmetis@bmts.com reservations@edelweissmotel.com contactadmin@saugeenfirstnation.ca saugeenmetis@bmts.com terrybestartist@hotmail.ca sandra_mielhausen@bwdsb.on.ca saugeenshorespolice@bmts.comSubject: Security Vulnerability on WebSmart Websites
I am Sam Bowne, an instructor in Computer Networking and Information Technology at City College San Francisco.
I am writing this to inform several Websmart, Inc. customers of a critical security vulnerability in Websmart's websites: the sites listed below are vulnerable to SQL injection, which makes it very easy to hack them.
This is a serious security defect. It is easy to fix, but Websmart has made it clear that they have no intention of fixing it.
If you have questions, or would like help fixing your website, feel free to contact me.
http://www.977thebeach.ca/calendar_details.php?EventID=6121'
http://www.bruceanchor.com/gallery_album.php?category=54%27
http://www.greycountyrealestate.com/listing_images.php?PropertyID=796%27
http://www.saugeenrailtrail.com/newsfull.php?NewsID=27%27
http://www.sunshine89.ca/calendar_details.php?EventID=2233'
http://www.chatsworthmotors.com/vehicle.php?VehicleID=319%27
http://www.ackertconstruction.com/photogallery_image.php?ImageID=
http://www.debtontario.com/article.php?ArticleID=9%27
http://www.frontierloghomes.ca/showcase_album.php?category=19%27
http://www.kingstonwestfmc.ca/sermon.php?SermonID=42%27
http://broughandwhicher.com/product.php?ProductID=3%27
http://debtontario.com/article.php?ArticleID=10%27
http://www.ackertinsurance.ca/staff-profile.php?StaffID=31%27
http://www.amethystcottages.com/cottage.php?CottageGroup=1%27
http://www.1049thebeach.ca/calendar_details.php?EventID=6175%27
http://abca.on.ca/publications_section.php?Category=8%27
http://www.lakehuroncottagerentals.com/cottage1.php?recordID=173'
http://www.saugeenconservation.com/publications_section.php?Category=1%27
http://www.saugeenshores.ca/photogallery_album.php?category=51%27
http://www.svca.on.ca/contact_card.php?ContactID=4%27
http://www.casualtycare.com/newsfull.php?NewsID=35%27
http://www.georgeplantphotography.com/photogallery_album.php?category=1%27
http://saugeenmetis.com/news_item.php?NewsID=173%27
http://edelweissmotel.com/photogallery_image.php?ImageID=10%27
http://www.saugeenfirstnation.ca/gallery_album.php?category=18%27
http://www.saugeenmetis.com/gallery_album.php?category=47%27
http://www.terrybest.com/gallery_album.php?category=21%27
http://www.bluewater-edfoundation.org/photogallery_album.php?category=19'
http://sspspolice.com/photogallery_image.php?ImageID=5%27
Details of previous correspondence with WebSmart are here:
http://samsclass.info/125/ethics/smart-websites.htm