Here's what I found: dozens of text files containing medical patient data.
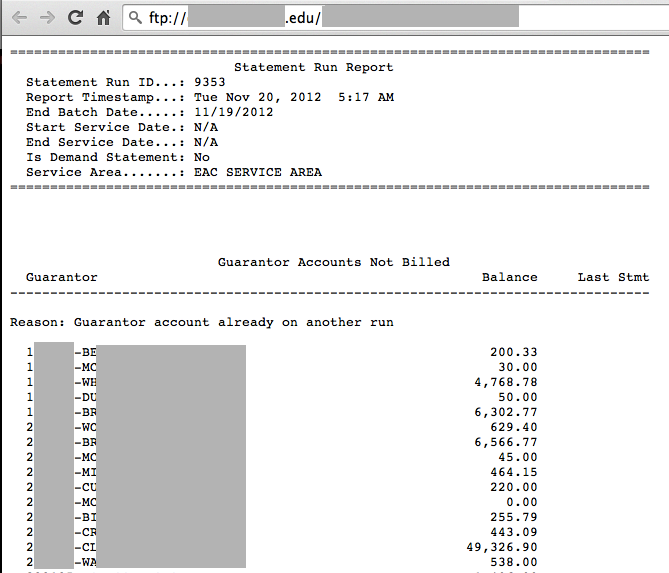
Here's a redacted screen shot of a text file I opened containing more than 2000 patient names with dollar amounts:

Here's another file I found with three complete patient addresses:
So I sent this email to three addresses: the webmaster, the chancellor, and the HIPAA compliance officer:
To: webmaster@redacted.edu, nocompliance@redacted.edu, chancellor@redacted.edu
Exposed patient data on public server
Hello:
I am Sam Bowne, an instructor at City College San Francisco, and I found two security problems on your server with a Google search.
Your FTP server has been compromised, and some files named "w0000000t" were added to it.
However, that's very minor compared to the fact that you have dozens of files publicly exposed on that server containing medical data about thousands of patients and medical insurance claims.
Here's the server root:
ftp://redacted.edu/
Here's an example file showing approximately 2000 of what appear to be patient names:
ftp://redacted.edu/redacted.txt
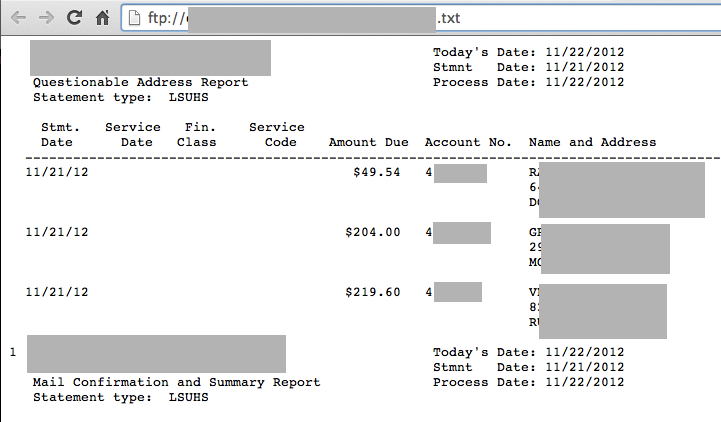
Here are some patient addresses:
ftp://redacted.edu/redacted.txt
There are many more files there--I think you have a serious violation of HIPAA regulations here.
These files have apparently been exposed for at least a year, and have already been copied to other servers by FTP search engines:
Redacted link to FTP archive site
The "w0000000t" file is apparently part of a mass compromise of Microsoft FTP servers, which was found but not explained by a French security company named QuarkLabs in this slide:
http://samsclass.info/lulz/w00t-ftp.png
Full presentation here:
http://www.quarkslab.com/dl/D2T1-Why-Port-Scans-are-for-Pussies.pdf
Please alert your technical and legal staff. I think there is a lot of work to be done here.
I am happy to answer any questions you may have.
Sam Bowne
sbowne@ccsf.edu
When I checked at 4:48 pm, the FTP site was gone; no longer accessible from the Internet at all, which was certainly the correct thing to do.
I hope they will follow through with whatever other actions are now required, like reporting the breach to oversight agencies, notifying affected patients, paying fines, etc.
But I applaud their fast action in doing the first thing quickly and correctly!