On the Windows machine, open a Command Prompt window and execute the IPCONFIG command.
Make a note of your IP address for later reference.
On the Windows machine, if Wireshark is running, close it.
scapy
e = Ether()
e.display()

Now we will add the upper layers to the packet.
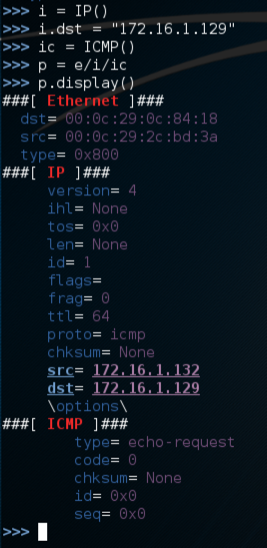
On the Linux machine, in scapy, enter these commands. Use the IP address of your Windows target machine in the second command:
i = IP()
i.dst = "192.168.198.139"
ic = ICMP()
p = e/i/ic
p.display()
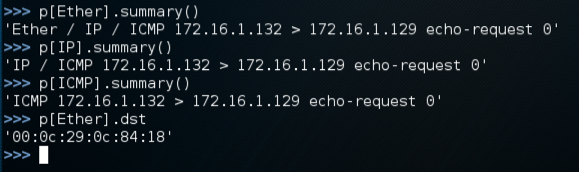
You can reference each layer of the packet named "p" by putting the protocol in square brackets:
On the Linux machine, in scapy, enter these commands:
p[Ether].summary()
p[IP].summary()
p[ICMP].summary()
p[Ether].dst
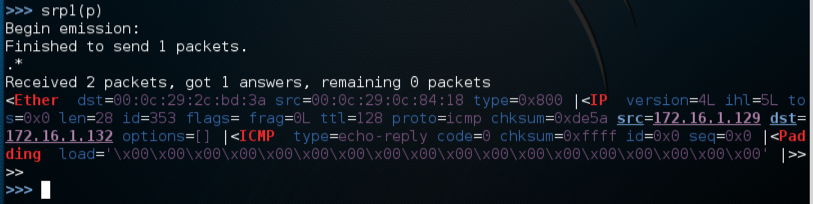
Now we will send the packet, using srp1, which sends at layer 2 and gets one packet in return.
On the Linux machine, in scapy, enter this command:
srp1(p)
On the Linux machine, in scapy, enter these commands. In the second command, use the real MAC address of your Windows machine plus 1:
p[Ether].dst = "00:50:56:24:3b:c1"
srp1(p)
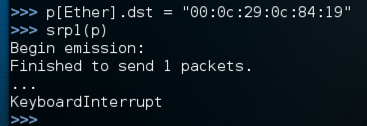
Cancel the waiting process with Ctrl+C.
On the Windows machine, start Wireshark, click Capture, Interfaces and begin capturing packets from the interface that goes to your LAN. This places your NIC in promiscuous mode.
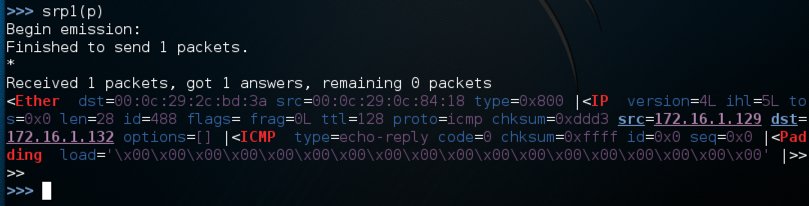
srp1(p)
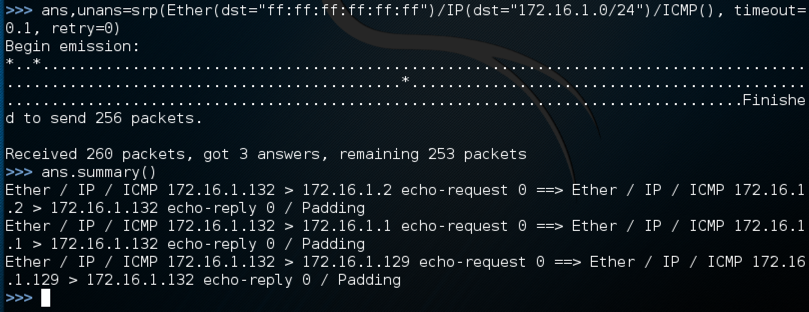
ans,unans=srp(Ether(dst="ff:ff:ff:ff:ff:ff")/IP(dst="192.168.198.0/24")/ICMP(),
timeout=0.1, retry=0)
ans.summary()
The second command shows a summary of the packets in "ans". I had three machines on my LAN: the Kali Linux attacker, the Windows target, and the Mac OS X host. So I got three "echo-reply" packets, as shown below on this page.
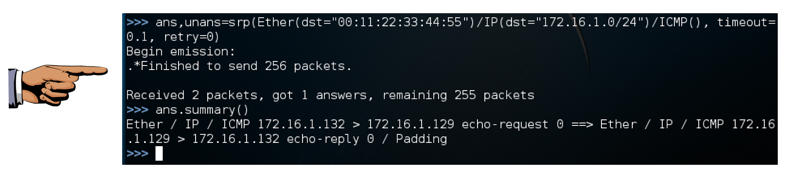
ans,unans=srp(Ether(dst="00:11:22:33:44:55")/IP(dst="192.168.198.0/24")/ICMP(),
timeout=0.1, retry=0)
ans.summary()
Save a screen image with the filename Proj X11 from Your Name.
Email the image to cnit.123@gmail.com with a Subject line of Proj X11 from Your Name.
http://carnal0wnage.blogspot.com/2009/02/quick-scapy-tutorial-for-extending.html
http://www.dirk-loss.de/scapy-doc/Scapy.pdf