1. An XSS vulnerability
2. A weakness to brute-force attacks in the password recovery system
These two weaknesses are dangerous alone, but even more dangerous if used together, as explained in this article: http://ha.ckers.org/deathby1000cuts/
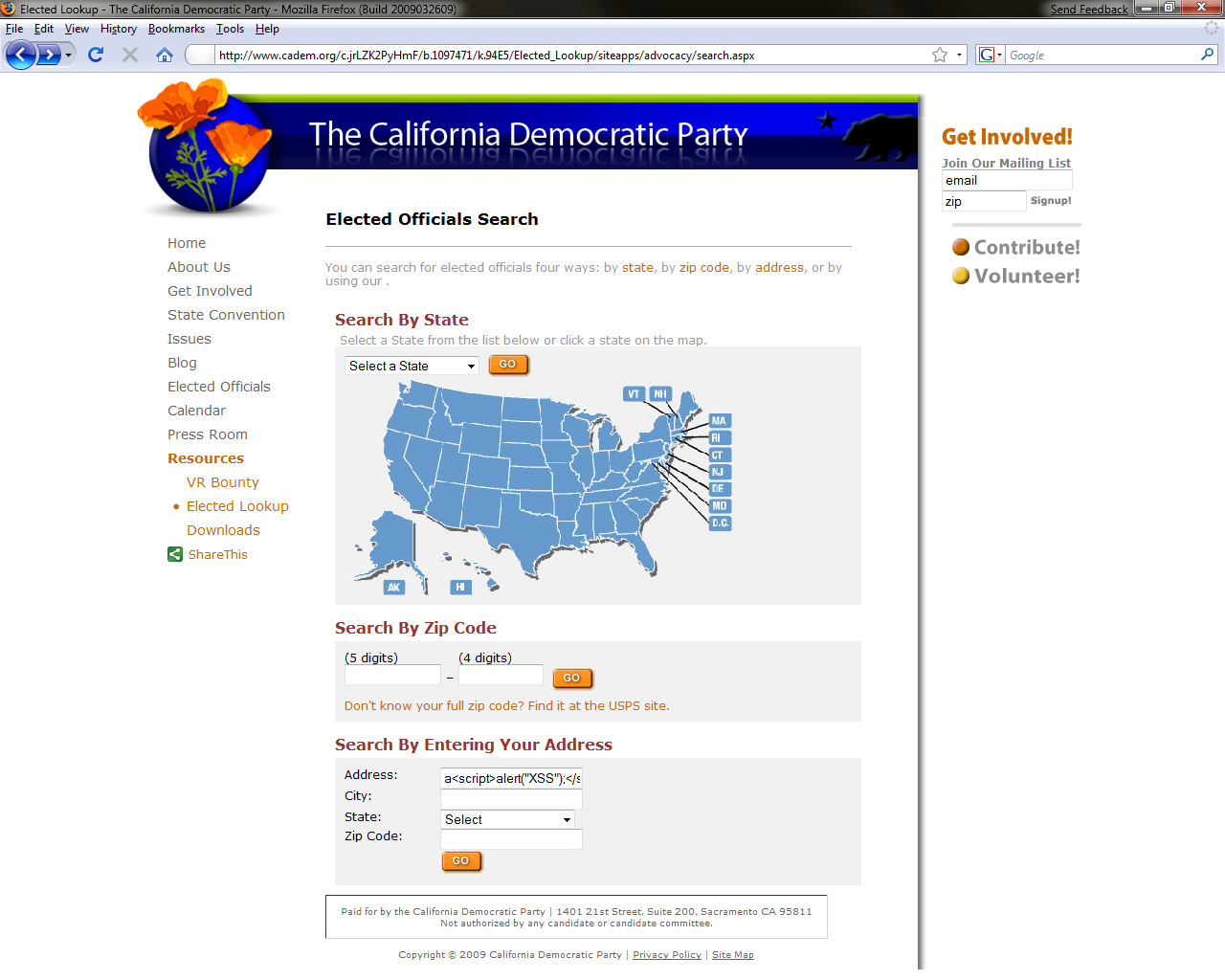
http://www.cadem.org/c.jrLZK2PyHmF/b.1097471/k.94E5/Elected_Lookup/siteapps/advocacy/search.aspx
Search for this address
a<script>alert("XSS");</script>
like this

The result is this
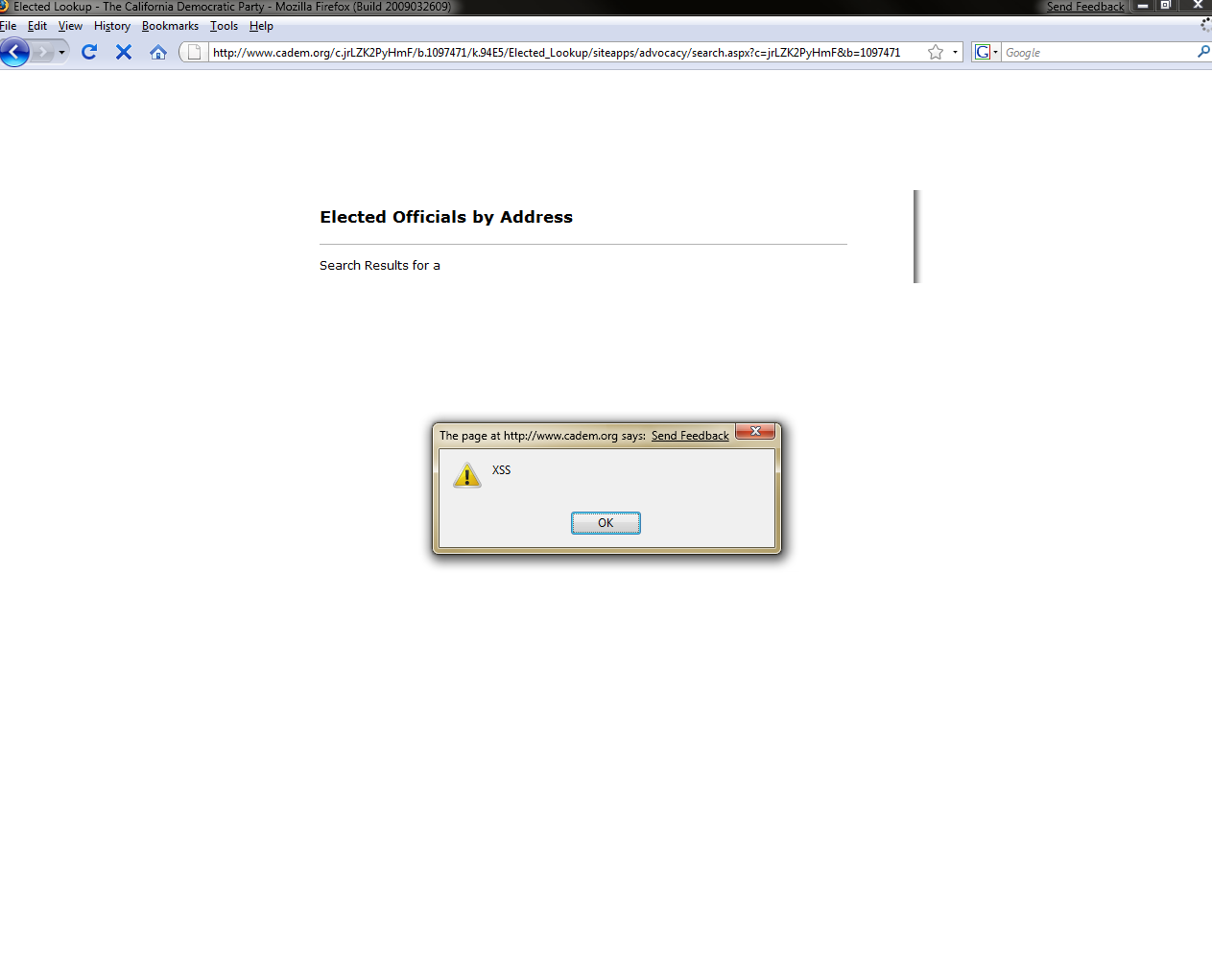
This goes right past NoScript in Firefox. That's pretty evil!
Go to this page:
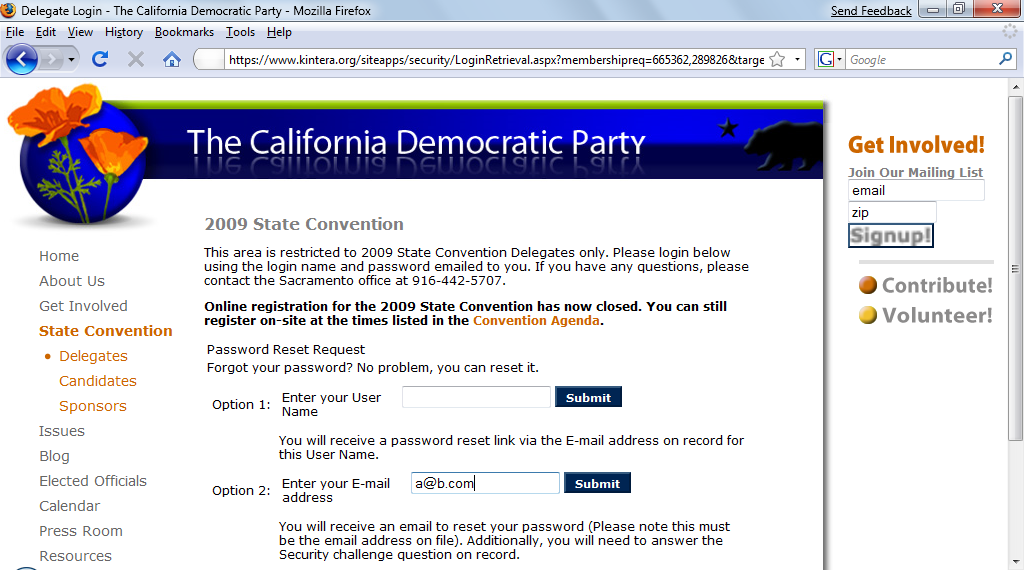
Enter any email address such as a@b.com
The response tells you whether that email is in the system, as shown below:
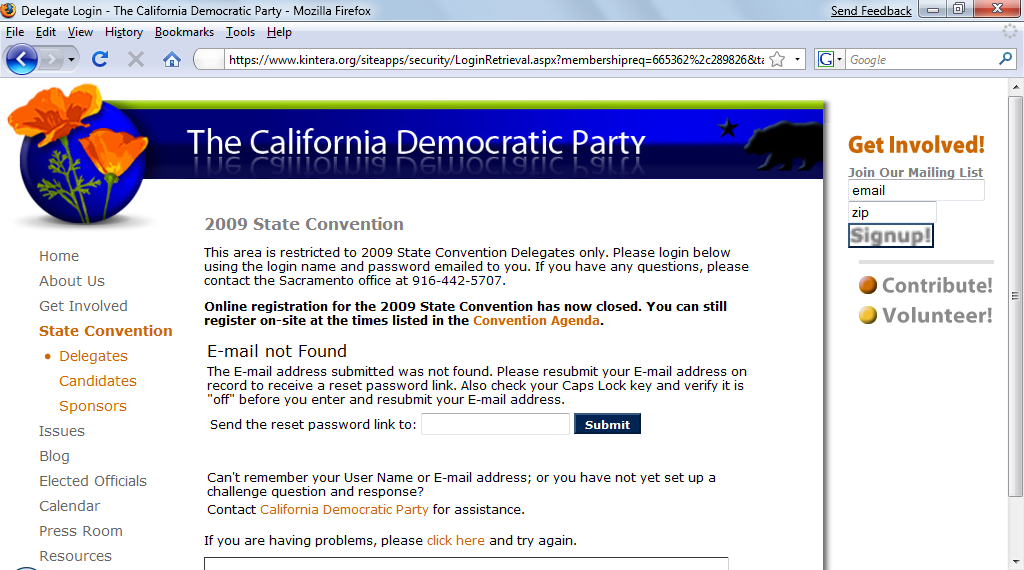
That enables an attacker to find the email accounts that are in the system, and those that are not. Then the attacker can spoof one member's apparent email address and send email to an address that is really in the system, exploiting the XSS vulnerability to hijack that person's session.
I found these on 4-18-09, and reported them to the these addresses on 4-18-09:
abuse@kintera.org
abuse@cadem.org (this bounced)
admin@cadem.org
and on their "contact us" form.
Sam Bowne